Hello and welcome to our Business Email Etiquette. Most people have experience in writing emails at some point before in their lives. However, the emails an average person writes are probably personal emails and not mails for work purposes.
Emails you send to friends are incredibly different in content and context to business emails you would send to customers or employers or even other colleagues in your workforce.
So, if you have a job that involves you writing emails to people in business style, learning business email etiquette is an absolute must for you.
1. Heading layouts
When you are sending emails to friends, you generally lay them out like a memo. This means there is very little detail in the layout besides basic greetings and paragraphs, usually starting with the greetings.
However, with a business email, it is best to lay it out exactly like you would lay out a formal letter. You need to put the company’s address in the right-hand corner and the date as well. Only then must you go on to the greetings.
This will make your email look more formal, making you seem like a professional who knows what they are doing as opposed to someone who just couldn’t be bothered spending the extra time to get the layout right.
2. Proper greetings
When you are sending an email to a friend, you usually greet them informally. If their name was Mary Johnson, you’d probably start your letter with a ‘Hey Mary’ or a ‘Hello Mary.’
However, this is not considered a professional way to write an email to a customer or other important person in your business. Again, you must use the proper method that you would greet someone with were you writing them a formal letter instead.
If your customer is Mary Johnson again, you should greet her with respect. ‘Dear Ms. Johnson’ would be the most appropriate way to start off your letter’s actual body in this case. If you do not know the recipient’s name, then you should start with a simple ‘Dear Sir or Madam.’
Politeness will always get you incredibly far, no matter what line of work you are in.
3. Informal language
You should get straight to the point with your email. Don’t dawdle on with it like you would if chatting to a friend and don’t write it how you would speak either.
You use language that sounds impressive and smart while not using such obscure language that your recipient doesn’t know what you are saying. All the time, you must keep it informal where possible, possibly even impersonal as well.
It will make you seem very professional in the long run.
4. Signing off
When you are sending your email, you must end it as you would with a letter also. Don’t just say ‘Bye’ and your first name; that is too personal.
You need to say ‘yours sincerely if you know the name of the recipient and ‘yours faithfully’ if you do not. Then you should end with your full name and whatever position you have at the company. (CEO, technical staff etc.)
So there you have it! All you need to do now is to show your boss that you can handle the emails from now on!

 Once File Explorer is up and running right-click on the hard drive you wish to run disk cleanup on and click on properties.
Once File Explorer is up and running right-click on the hard drive you wish to run disk cleanup on and click on properties.
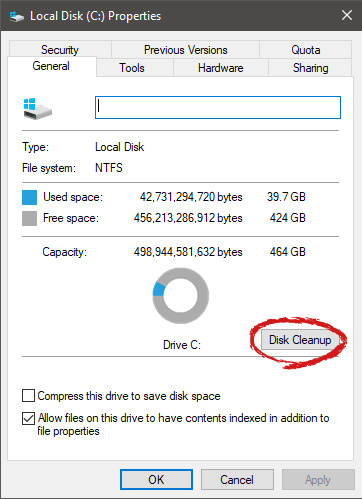
 Properties Windows will open on the general tab, on that tab you have disk cleanup on the lower right part of properties, click on it.
Properties Windows will open on the general tab, on that tab you have disk cleanup on the lower right part of properties, click on it.
 Wait for Windows to gather information about your hard drive and files on it. After it is finished you will be greeted with the next screen:
Wait for Windows to gather information about your hard drive and files on it. After it is finished you will be greeted with the next screen:
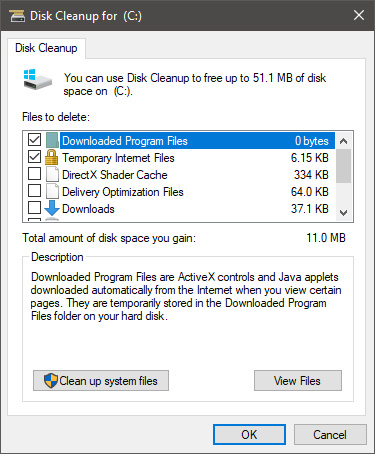 Here you can thick and mark which items you would like to get rid of and which ones you would like to keep. Note that you can freely tick all of them and remove them since removing these files will not break WIndows in any way. make your choices and click on ok. You can also click on Clean up system files to run system files cleaner and get rid of junk there, you will not be able to choose any options there, Windows will alone clean up what is not needed.
After disk cleanup is finished least thing you will have is more free disk space, but like mentioned, keeping your Windows and computer healthy goes a long way in its usability, speed, and performance.
Here you can thick and mark which items you would like to get rid of and which ones you would like to keep. Note that you can freely tick all of them and remove them since removing these files will not break WIndows in any way. make your choices and click on ok. You can also click on Clean up system files to run system files cleaner and get rid of junk there, you will not be able to choose any options there, Windows will alone clean up what is not needed.
After disk cleanup is finished least thing you will have is more free disk space, but like mentioned, keeping your Windows and computer healthy goes a long way in its usability, speed, and performance.  Today most people have Facebook accounts where they keep in touch with friends and family. But large Facebook network of users is also very interesting to another party as well, hackers.
There are many ways hackers can steal your data via direct hacks, trickery, and social engineering in order to get your credentials, emails, and many other things using them to wreak further havoc.
Once a hacker has needed information it is very difficult to minimize impact and all of your information could be compromised from a list of friends to credit card numbers. Keep on reading to learn how can you protect yourself against these attacks and learn about common practices that hackers use in order to steal your data.
Today most people have Facebook accounts where they keep in touch with friends and family. But large Facebook network of users is also very interesting to another party as well, hackers.
There are many ways hackers can steal your data via direct hacks, trickery, and social engineering in order to get your credentials, emails, and many other things using them to wreak further havoc.
Once a hacker has needed information it is very difficult to minimize impact and all of your information could be compromised from a list of friends to credit card numbers. Keep on reading to learn how can you protect yourself against these attacks and learn about common practices that hackers use in order to steal your data.
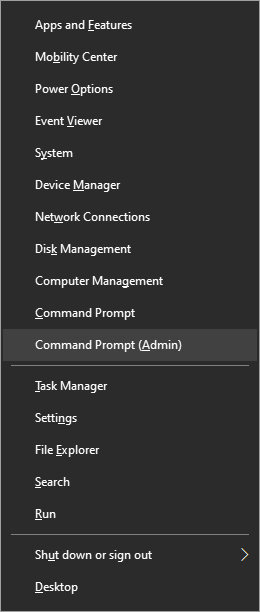
 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
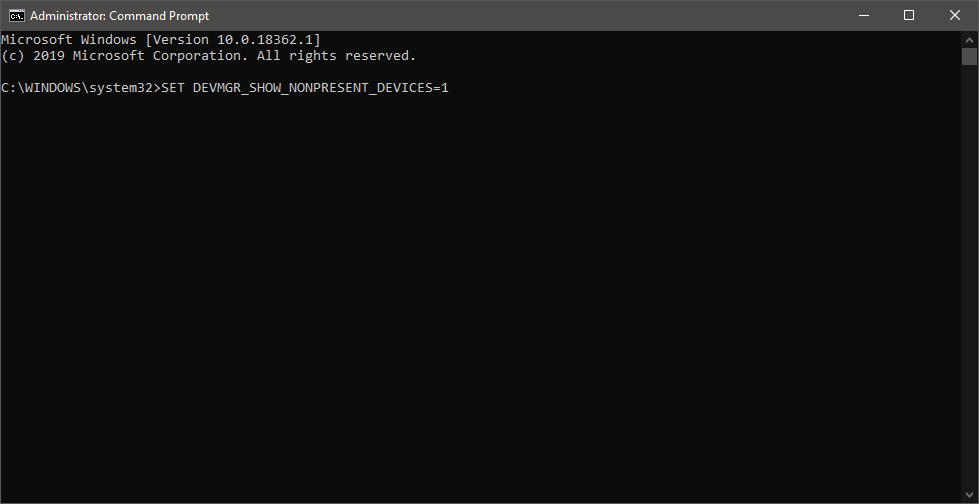 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
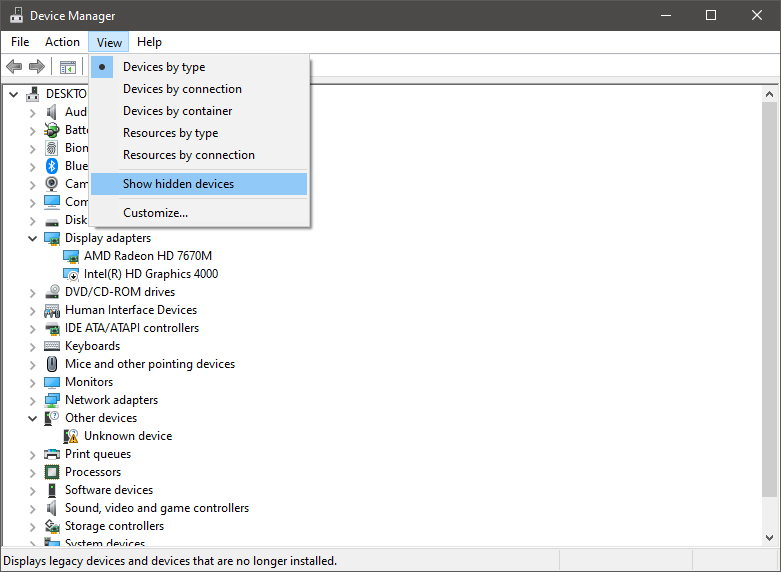
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
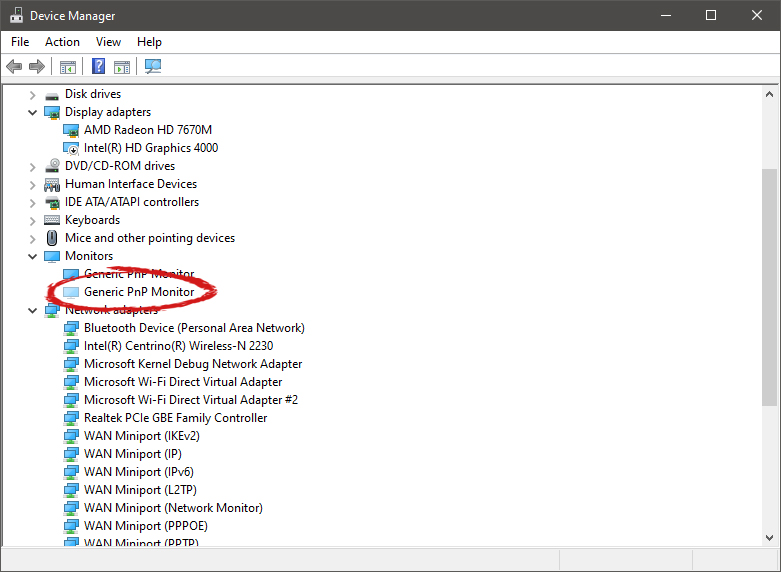 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
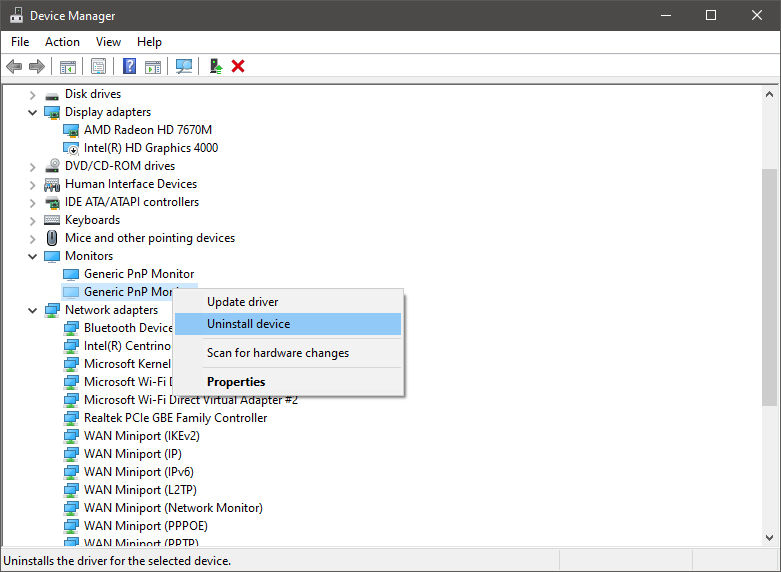 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 