It is no longer a secret that websites, social media, and other various places on WEB are tracking you and your messages and emails for keywords that they will later use to promote and serve your specific ads linked to those keywords. Altho the process is fully automated it does feel a little forced and uneasy.
That is why we are bringing you this article in which we will show you how to stop website tracking in the most popular and used browsers.
SAFARI
Apple’s Safari browser gives you the option to block cross-site tracking. It also has a Privacy Report that displays all the sites and agencies that are gathering information about you.
Before blocking these trackers, you may want to review exactly which sites are tracking you online and gathering information about you. Armed with this information, you may decide that cross-site tracking isn’t a huge issue for your particular browsing habits, or you may decide to avoid certain websites entirely.
To access Safari’s Privacy Report:
- Launch the Safari web browser.
- In the toolbar, select Safari > Privacy Report.
- Select the Websites tab. This will display information about all the websites that are profiling you.
- Select the Trackers tab. This displays a list of all the trackers that are gathering information about you. This includes the companies that created these trackers and the number of times Safari detected these trackers during your browsing sessions.
You can also check how intrusive a particular website is by navigating to the website in question and then selecting the shield icon that appears alongside Safari’s address bar. You can then select
Trackers on This Web Page, and Safari will display a list of all the trackers that are active on this particular webpage.
Once you’ve seen all the websites and agencies who are tracking you, if you want to block these trackers:
- In the Safari toolbar, select Safari > Preferences …
- Select the Privacy tab.
- Select the following checkbox: Prevent Cross-Site Tracking.
Safari will now prevent these trackers from following you across the World Wide Web.
CHROME
As you’re browsing the web, Chrome can send a request for websites not to collect or track your browsing data.
It’s important to note that this is a request, so there’s no guarantee that every website will honor the request. Frustratingly, Chrome doesn’t provide information about the websites that are tracking you online. However, we still recommend enabling this feature, as it can help minimize the number of websites that are tracking your online movements:
- In Chrome’s upper-right corner, select the three-dot menu icon, then Settings.
- In the menu on the left, select Privacy and security.
- Click Cookies and other site data.
- Find the Do not track slider and push it into the On position.
Now Chrome will send a
Do Not Track request to every website you visit. Since this is only a request, you may want to take additional steps to protect your online privacy.
Ghostery is a Chrome extension that enables you to view and block online trackers. After installing Ghostery, you can view all the trackers that are active on a particular website:
- Head to the site in question.
- Click the Extensions icon in the Chrome toolbar.
- Select Ghostery to see a list of all the trackers this extension has detected.
- You can block all of these trackers by selecting the Detailed tab and then clicking Restrict site.
Repeat this process for every site you visit.
MOZILLA FIREFOX
Firefox has an Enhanced Tracking Protection feature that can block all the cross-site trackers identified by
Disconnect. This feature can also preserve your online privacy by blocking social media trackers, fingerprints, and crypto miners, making this a great all-arounder for the security-conscious Internet user.
Enhanced Tracking Protection should be enabled by default. However, you can verify whether it’s active for your particular Firefox installation by navigating to any website. Next, click the little shield icon that appears alongside Firefox’s address bar and you should see a message confirming that Enhanced Tracking Protection is enabled.
If Enhanced Tracking Protection isn’t enabled, we recommend activating it:
- In Firefox’s upper-right corner, select the three-line icon, then Preferences.
- In the menu on the left, select Privacy & Security.
- You can now select either Standard or Strict. Note that Strict may affect the functionality of certain websites, so it’s recommended you opt for Standard unless you specifically require a greater level of protection.
Similar to Chrome, Firefox can send a
Do Not Track request. While you’re in the
Privacy & Security menu, you may want to consider activating Mozilla’s Do Not Track feature.
OPERA
When you first installed Opera, it gave you the option to block trackers. If you didn’t take Opera up on the offer then, you can start blocking trackers now:
- Along the left side of the Opera browser, click the cog icon. This opens Opera’s settings.
- In the menu on the left, select Basic.
- Find the Block Trackers slider and push it into the On position.
- Blocking trackers can impact the functionality of certain websites. If you start noticing strange behavior on a particular website, you may want to add that site to your Exceptions list. By allowing this site to use trackers, you should be able to resolve any issues you’re experiencing.
To make an exception for one or more websites:
- Launch Opera’s settings by clicking the little cog icon.
- Navigate to Basic > Manage Exceptions.
- Click Add and then type the address of the site where you want to permit trackers.
Repeat for all the sites that you want to add to your exceptions list.

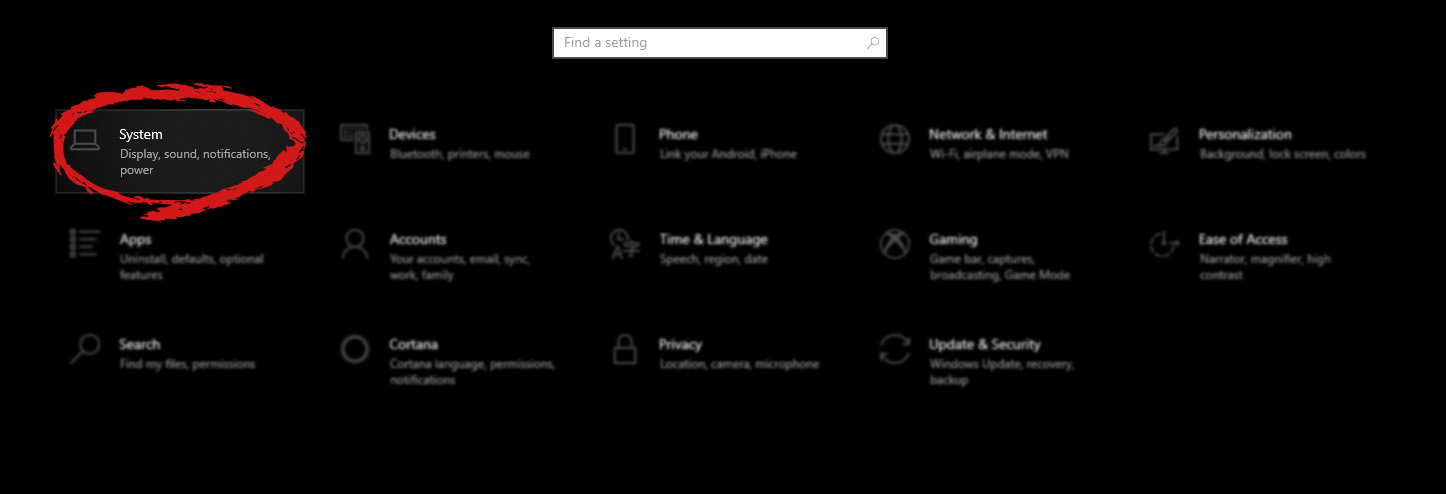 in system dialog click on the clipboard and on the right screen turn ON CLipboard history.
in system dialog click on the clipboard and on the right screen turn ON CLipboard history.
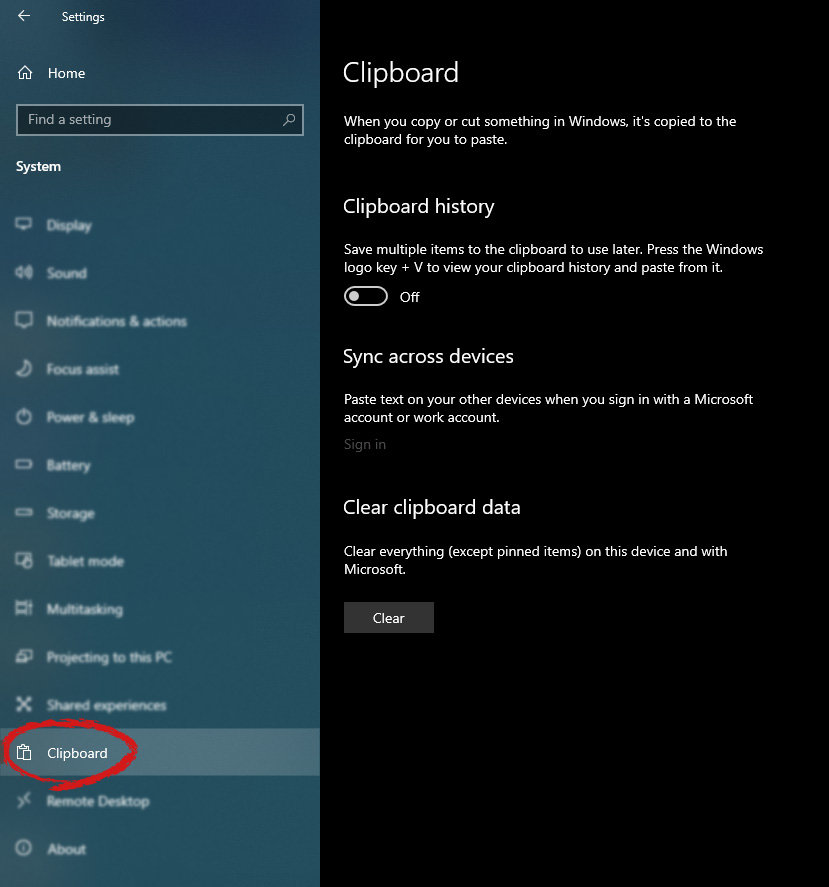
 From the menu choose command prompt (admin)
From the menu choose command prompt (admin)
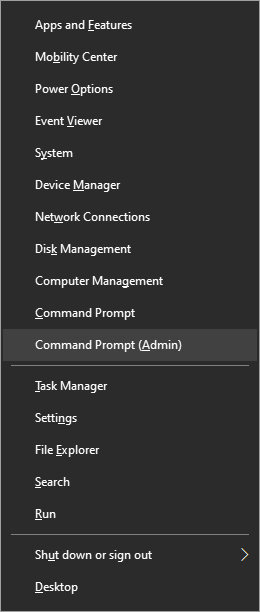 In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer
In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer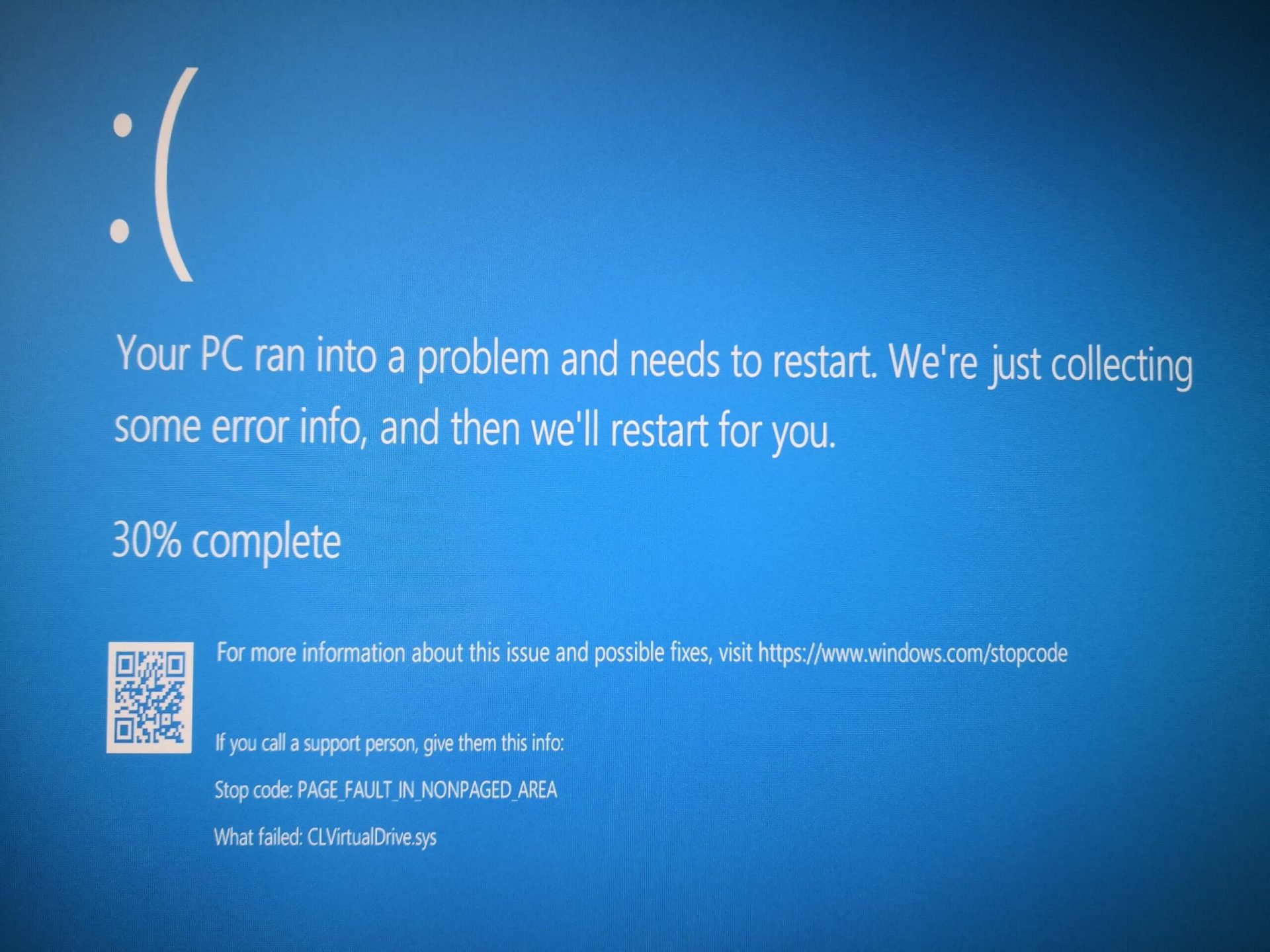 Rollback using system restore
Rollback using system restore