Sadooma is a Browser Extension for Google Chrome. This extension offers users the ability to search for any trending news on the web.
This extension changes your default search engine to Yahoo, and while active it changes the displayed ads on your browser, allowing it to make revenue on every ad you click. While this is not inherently malicious, the extension redirects your search to its servers first before forwarding it to yahoo and displaying search results. The information that is sent back to the servers contains your browsing data & visited web pages. As this represents a security and privacy risk, Sadooma is classified as a browser hijacker for its potentially unwanted functions and poor user experience.
From the Author:
We’ve got what you need!
If you are like us, addicted to interesting viral content, you’ve reached the best place for this.
Sadooma will help you to find what is trending right now on the internet in an easy and immediate way.
Privacy – We don’t share your information with others.
Trending Content – New viral content every day
Up to Date – We update sources to keep things fresh.
Made with Love – Our content is safe and suitable for all ages.
About Browser Hijackers
Browser hijacking is a type of unwanted software, commonly a browser add-on or extension, which then causes modifications in the web browser’s settings. Browser hijackers can do more than simply modifying home pages. It redirects you to the sponsored sites and inserts advertisements on the internet browser that helps its creator generate earnings. A lot of people think that these types of sites are legitimate and harmless but that is not true. Nearly all browser hijackers pose an existent threat to your online safety and it is vital to classify them under privacy dangers. In a much worst case, your web browser could be hijacked to download malicious software that will do a lot of damage to your computer.
Indications of browser hijack
There are many symptoms that point to a browser hijacking: you see unauthorized modifications to your web browser’s homepage; you get re-directed to sites you never intended to visit; default web engine is modified; you’re getting browser toolbars you haven’t noticed before; your internet browser will display constant pop-up windows; your web browser starts running slowly or presents frequent errors; You can’t access certain websites, particularly anti-virus websites.
How they get into your computer or laptop
Browser hijackers infect computers via malicious email attachments, downloaded infected computer files, or by visiting infected sites. Many web browser hijackings originate from add-on software, i.e., browser helper objects (BHO), toolbars, or extensions added to web browsers to give them extra features. Browser hijackers sneak to your computer along with free software application downloads that you unknowingly install alongside the original. An example of some well-known browser hijacker includes Conduit, Anyprotect, Babylon, SweetPage, DefaultTab, RocketTab, and Delta Search, but the names are regularly changing.
Removal
Certain browser hijacking could be quite easily stopped by finding and removing the corresponding malware application from your control panel. But, the majority of hijackers are really tenacious and require specialized applications to remove them. You should think about undertaking manual repairs only if you’re a tech-savvy individual, as potential risks are associated with fiddling with the system registry and HOSTS file.
You might opt for automatic browser hijacker removal methods by simply installing and running a reliable anti-malware application. One of the top tools for correcting browser hijacker malware is SafeBytes Anti-Malware. It can help you remove any pre-existing malware in your computer and gives you real-time monitoring and protection from the latest internet threats. Together with the anti-malware tool, a system optimizer will help you in removing all linked files and modifications in the computer registry automatically.
What To Do When You Cannot Install Any Antivirus?
All malware is inherently dangerous, but certain kinds of malware do a lot more damage to your computer than others. Some malware variants modify internet browser settings by including a proxy server or change the computer’s DNS configurations. In such cases, you’ll be unable to visit some or all websites, and thus unable to download or install the required security software to clear out the computer virus. If you are reading this, you may have infected by a virus that prevents you from downloading computer security software like Safebytes Anti-Malware. Although this sort of issue will be difficult to circumvent, there are some steps you can take.
Make use of Safe Mode to resolve the problem
In Safe Mode, you could adjust Windows settings, un-install or install some programs, and eliminate hard-to-delete malware. If the malicious software is set to load immediately when the computer starts, switching into this mode may well prevent it from doing so. In order to enter into Safe Mode or Safe Mode with Networking, press the F8 key while the computer is starting up or run MSCONFIG and locate the “Safe Boot” options under the “Boot” tab. Once you are in safe mode, you can try to download and install your anti-malware software program without the hindrance of malicious software. After installation, run the malware scanner to eliminate most standard infections.
Switch to some other browser
Malicious code may exploit vulnerabilities on a specific internet browser and block access to all anti-virus software websites. When you suspect that your Internet Explorer happens to be hijacked by a computer virus or otherwise compromised by hackers, the best plan of action is to switch to a different internet browser such as Google Chrome, Mozilla Firefox, or Apple Safari to download your chosen security application – Safebytes Anti-Malware.
Install and run anti-virus from your Thumb drive
Another solution is to save and run an antivirus program entirely from a USB drive. Try these simple actions to clear up your infected PC using a portable antivirus.
1) Make use of another virus-free PC to download Safebytes Anti-Malware.
2) Plug the Flash drive into the clean computer.
3) Double-click the Setup icon of the antivirus software to run the Installation Wizard.
4) Select the drive letter of the flash drive as the location when the wizard asks you where you would like to install the anti-virus. Follow the on-screen instructions to finish the installation process.
5) Remove the pen drive. You may now use this portable anti-malware on the infected computer.
6) Double click the Safebytes Anti-malware icon on the flash drive to run the program.
7) Run Full System Scan to identify and get rid of all kinds of malware.
Let's Talk About SafeBytes Anti-Malware!
If you are looking to download the anti-malware program for your computer, there are several tools in the market to consider however, you cannot trust blindly anyone, no matter whether it is paid or free program. Some of them do a great job in getting rid of malware threats while some will affect your PC themselves. You have to purchase a tool that has got a good reputation and detects not just viruses but other sorts of malware as well. One of the recommended tools by industry analysts is SafeBytes Anti-Malware, the safest program for Microsoft Windows.
SafeBytes anti-malware is a powerful, very effective protection software made to assist users of all levels of IT literacy in finding and removing malicious threats out of their personal computers. Using its cutting-edge technology, this application will help you get rid of several types of malware including computer viruses, PUPs, trojans, worms, ransomware, adware, and browser hijackers.
There are many great features you’ll get with this security product. Below are some of the highlighted features included in the tool.
Real-time Threat Response: SafeBytes provides round-the-clock protection for your PC restricting malware intrusions instantly. It will regularly monitor your laptop or computer for hacker activity and also provides users with advanced firewall protection.
World-class AntiMalware Protection: Safebytes is made on the best virus engine in the industry. These engines will find and get rid of threats even during the early phases of a malware outbreak.
Faster Scanning: This software has got one of the quickest and most effective virus scanning engines in the industry. The scans are very accurate and take a short amount of time to complete.
Safe Web Browsing: SafeBytes provides an instant safety rating on the web pages you are about to check out, automatically blocking unsafe sites and make sure that you’re certain of your online safety while browsing the net.
Lightweight Tool: SafeBytes is a lightweight and user-friendly anti-virus and antimalware solution. Since it uses minimal computer resources, this application leaves the computer’s power exactly where it belongs to: with you actually.
24/7 Online Technical Support: You could get high levels of support round the clock if you’re using their paid software.
To sum it up, SafeBytes Anti-Malware is pretty great for securing your laptop or computer against all sorts of malware threats. There is no doubt that your computer will be protected in real-time as soon as you put this software to use. So if you’re trying to find a comprehensive antivirus program that’s still simple enough to use, SafeBytes Anti-Malware is exactly what you will need!
Technical Details and Manual Removal (Advanced Users)
If you don’t want to use malware removal software and prefer to eliminate Sadooma manually, you could do so by going to the Add/Remove Programs menu in the Control Panel and removing the offending software; in cases of browser add-ons, you may uninstall it by visiting the browser’s Add-on/Extension manager. You might even want to reset your browser settings, as well as clear your web browser cache and cookies.
In order to ensure the complete removal, manually examine your hard disk and registry for all the following and eliminate or reset the values as needed. However, editing the Windows registry is actually a complicated job that only advanced users and professionals should try to fix it. In addition, certain malicious programs have the capability to defend against its deletion. You are encouraged to do this procedure in Safe Mode.
Files:
%USERPROFILE%\AppData\Local\Google\
Registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
 I going to admit right here that I am a big fan of Cooler Master PC cases, I like them and they are always one of the things that I consider when building a new PC, overall I like their ideas and quality so personal for me it was quite a surprise to see that they are one that is making a new generation gaming chair.
Now truth to be told Orb X is not your typical gaming chair as you can clearly see from the pictures. The chair itself will come in two colors: white or black and RGB lighting looks to be prominently featured throughout.
I going to admit right here that I am a big fan of Cooler Master PC cases, I like them and they are always one of the things that I consider when building a new PC, overall I like their ideas and quality so personal for me it was quite a surprise to see that they are one that is making a new generation gaming chair.
Now truth to be told Orb X is not your typical gaming chair as you can clearly see from the pictures. The chair itself will come in two colors: white or black and RGB lighting looks to be prominently featured throughout.
 The chair itself is advertised as both meant and aimed for professional and gaming crowds but I believe the gaming crowd is in general more interested in this hardware piece.
Hardware is enclosed in a fully motorized shuttle dome which aims to maximize your privacy, it supports a single 49inch display or three 27inch monitors along with surround speakers if you do not wish to use headphones.
The chair itself is advertised as both meant and aimed for professional and gaming crowds but I believe the gaming crowd is in general more interested in this hardware piece.
Hardware is enclosed in a fully motorized shuttle dome which aims to maximize your privacy, it supports a single 49inch display or three 27inch monitors along with surround speakers if you do not wish to use headphones.
 It offers an adjustable headrest, lumbar support, and footrest so you can spend some time in it and be comfortable. Controls on the chair itself allow you to raise or lower the dome for easier getting in and out of it.
Orb X also has a compartment in its backside, it folds out and has a sliding tray designed to hold your PC or console. Everything is enclosed so wiring is not the issue.
Overall Orb X seems really like the computer chair of the future, Cooler Master expects to release the Orb X by December 2021, priced around $12,000-$14,000.
It offers an adjustable headrest, lumbar support, and footrest so you can spend some time in it and be comfortable. Controls on the chair itself allow you to raise or lower the dome for easier getting in and out of it.
Orb X also has a compartment in its backside, it folds out and has a sliding tray designed to hold your PC or console. Everything is enclosed so wiring is not the issue.
Overall Orb X seems really like the computer chair of the future, Cooler Master expects to release the Orb X by December 2021, priced around $12,000-$14,000. 

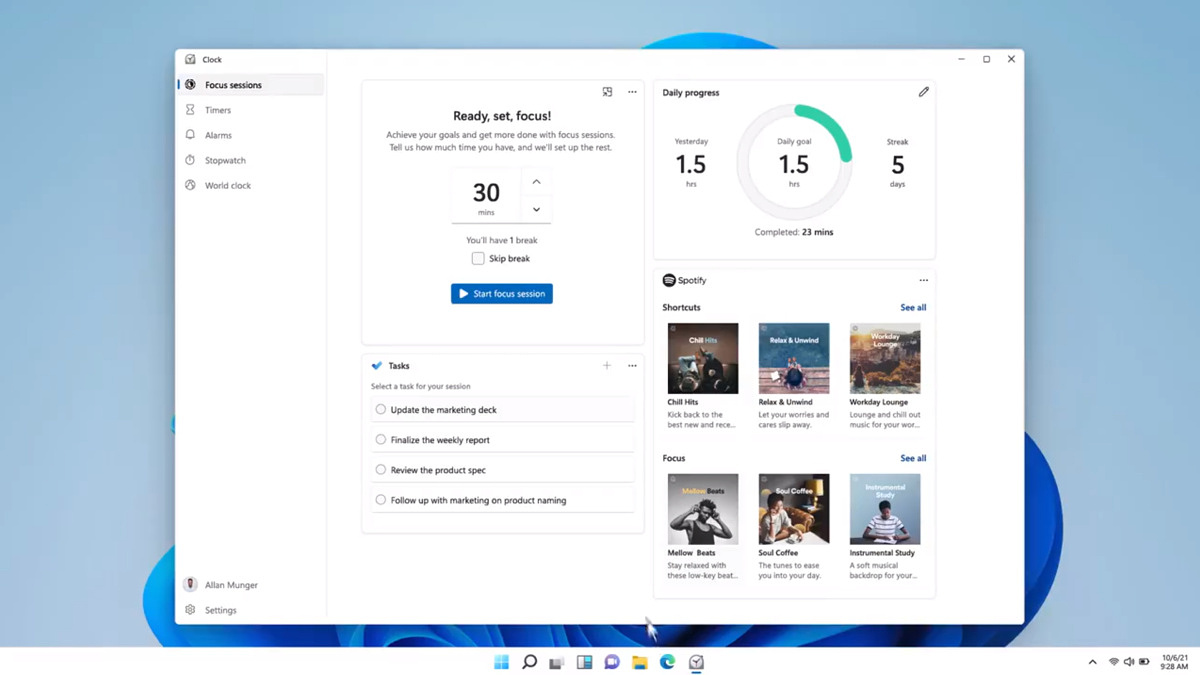 Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.

