InternetSpeedTracker is a browser extension developed by MindSpark Inc. This browser add-on offer uses tips on how to boost their “bad” internet connection speed. It displays false internet speed in order to get you to open the sponsored links listed in the toolbar.
This extension also hijacks your browser home page and replaces your default search engine with MyWay. While browsing the internet you will see additional unwanted sponsored ads and links throughout your search results, and sometimes even pop-up ads might appear. While active this extension gathers personal information, website visits, links, and clicks and uses this data to serve ads.
InternetSpeedTracker has been flagged as a Browser Hijacker by several anti-virus scanners, and due to its data mining behavior, it is not recommended to keep it on your computer, especially because it gives false data about your internet speed.
About Browser Hijackers
Browser hijack is a very common type of online fraud where your internet browser settings are modified to allow it to carry out things you don’t intend. They’re created to disrupt browser functions for several purposes. It redirects you to the sponsored sites and inserts ads on the web browser which helps its developer generate earnings. Nevertheless, it’s not that naive. Your web safety is jeopardized and it is also extremely irritating. They don’t just ruin your web browsers, but browser hijackers could also modify the computer registry, making your PC vulnerable to other attacks.
How one can know if your web browser is hijacked
Signs that an internet browser is a hi-jacked include: the browser’s home-page is modified; you find yourself regularly directed to a different site than the one you meant; the default search engine is changed; unwanted new toolbars are added to your web browser; never-ending pop-up ads show up and/or your browser pop-up blocker is disabled; your web browser starts running sluggishly or displays frequent glitches; You simply can’t access specific sites, particularly anti-virus sites.
How they infect PCs
A browser hijacker can be installed on your computer when you check out an infected website, click an e-mail attachment, or download something from a file-sharing website. They are usually included with toolbars, BHO, add-ons, plugins, or browser extensions. A browser hijacker could also be installed as a part of freeware, shareware, demoware, and fake programs. A good example of a notorious browser hijacker is the most recent Chinese malware known as “Fireball”, which has attacked 250 million computer systems worldwide. It acts as a hijacker but can be turned into a fully functioning malware downloader afterward.
Browser hijackers could affect the user’s browsing experience greatly, keep track of the websites visited by users and steal private information, cause difficulty in connecting to the internet, and ultimately create stability issues, making software programs and systems freeze.
How to repair a browser hijack
Some hijackers could be removed by uninstalling the freeware they came with or by eliminating any extension you have recently added to your system. But, many hijackers are hard to get rid of manually. No matter how much you attempt to eliminate it, it can keep coming back over and over again. And there’s no denying the fact that the manual fixes and removal methods can be quite a complicated job for a rookie PC user. Furthermore, there are several risks connected with fiddling around with the system registry files.
What you can do if Virus Stops You From Downloading Anything?
Malware could cause all kinds of damage after they invade your system, ranging from stealing your private information to deleting data files on your computer system. Certain malware variants modify web browser settings by adding a proxy server or modify the computer’s DNS configuration settings. In such cases, you’ll be unable to visit some or all of the websites, and thus not able to download or install the necessary security software to remove the infection. If you’re reading this article, chances are you’re stuck with a virus infection that is preventing you to download or install the Safebytes Anti-Malware program on your PC. There are some fixes you can try to get around with this issue.
Install antivirus in Safe Mode with Networking
If the malware is set to load at Windows startup, then booting in Safe Mode should prevent it. Since only the minimal programs and services start-up in safe mode, there are rarely any reasons for issues to take place. Listed below are the steps you should follow to start your computer into the Safe Mode of your Windows XP, Vista, or 7 computers (visit Microsoft site for instructions on Windows 8 and 10 PCs).
1) At power on/start-up, tap the F8 key in one-second intervals. This will bring up the Advanced Boot Options menu.
2) Select Safe Mode with Networking with arrow keys and hit Enter.
3) As soon as this mode loads, you will have an internet connection. Now, utilize your web browser normally and navigate to https://safebytes.com/products/anti-malware/ to download and install Safebytes Anti-Malware.
4) Right after the software program is installed, let the diagnostic scan run to remove trojans and other malware automatically.
Switch to an alternate web browser
Web-based viruses can be environment-specific, aiming for a particular internet browser or attacking specific versions of the browser. The best solution to avoid this issue is to opt for a browser that is known for its security features. Firefox comprises built-in Phishing and Malware Protection to keep you safe online.
Run anti-virus from a pen drive
Another technique is to download and transfer an anti-malware application from a clean PC to run a scan on the affected computer. Follow these steps to use a flash drive to clean your infected system.
1) Download Safebytes Anti-Malware or Microsoft Windows Defender Offline onto a clean PC.
2) Insert the pen drive on the same system.
3) Double-click the Setup icon of the anti-malware software package to run the Installation Wizard.
4) Pick a USB flash drive as the place when the wizard asks you exactly where you would like to install the application. Follow the instructions on the computer screen to complete the installation process.
5) Now, transfer the pen drive to the infected computer.
6) Run the Safebytes Anti-malware directly from the thumb drive by double-clicking the icon.
7) Click the “Scan” button to run a full system scan and remove malware automatically.
Let's Talk About SafeBytes Anti-Malware!
Want to install the best anti-malware application for your laptop or computer? There are many applications available in the market which comes in free and paid versions for Windows computers. Some of them are great and some are scamware applications that pretend as legitimate anti-malware programs waiting to wreak havoc on your PC. When looking for an antimalware program, pick one which gives reliable, efficient, and total protection against all known viruses and malware. One of the recommended tools by industry leaders is SafeBytes Anti-Malware, the most dependable program for Windows computers.
SafeBytes anti-malware is a reliable tool that not only secures your system permanently but is also quite user-friendly for people of all ability levels. This application could easily identify, remove, and protect your personal computer from the most advanced malware attacks such as spyware, adware, trojan horses, ransomware, worms, PUPs, and other possibly damaging software applications.
SafeBytes has excellent features when compared to other anti-malware programs. Below are a few of the great ones:
World-class AntiMalware Protection: Built upon a greatly acclaimed anti-virus engine, this malware removal application can identify and remove numerous obstinate malware threats such as browser hijackers, PUPs, and ransomware that other common antivirus applications will miss.
Live Protection: SafeBytes gives real-time active supervision and protection from all known viruses and malware. They’re very effective in screening and eliminating different threats because they are regularly improved with new updates and alerts.
Web Security: SafeBytes provides an instant safety rating on the web pages you are going to visit, automatically blocking risky sites and making sure that you are certain of your safety while browsing the internet.
Very Low CPU and Memory Usage: SafeBytes provides complete protection from online threats at a fraction of the CPU load due to its enhanced detection engine and algorithms.
Premium Support: SafeBytes provides 24/7 technical support, automatic maintenance, and updates for the best user experience.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove InternetSpeedTracker without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by InternetSpeedTracker



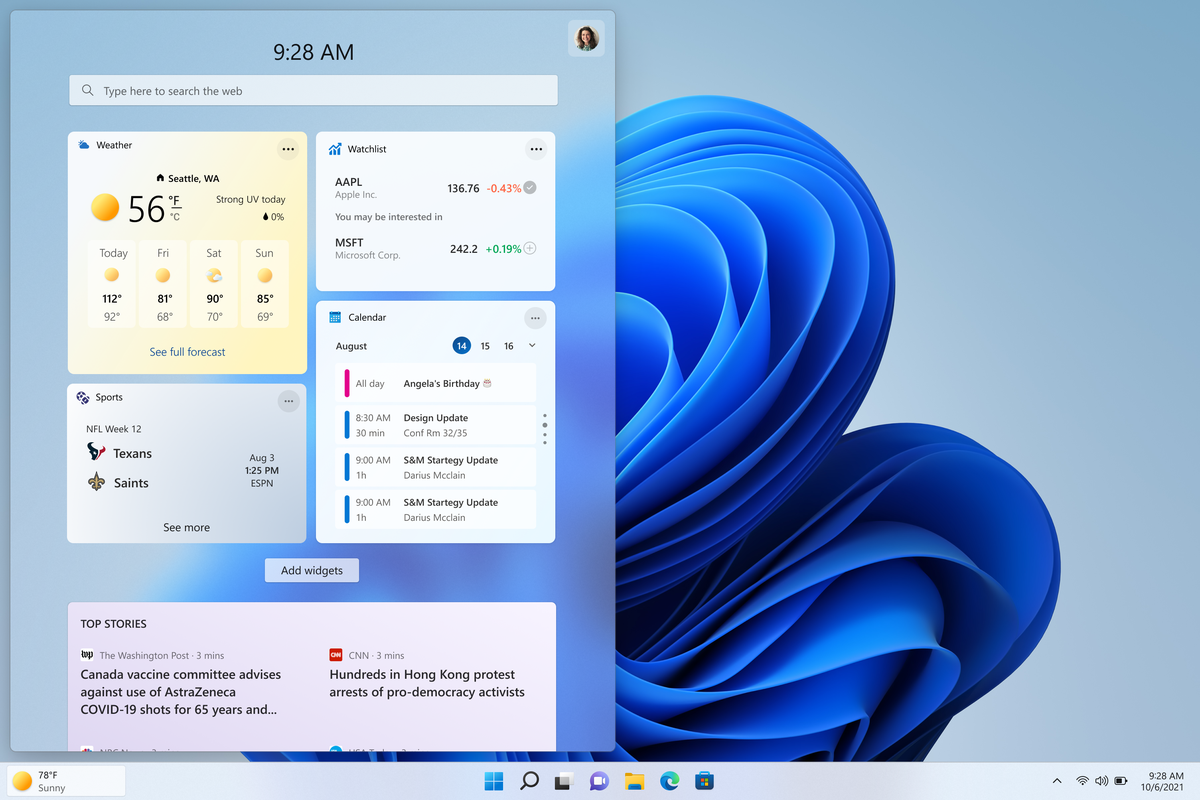 The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it.
The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it. 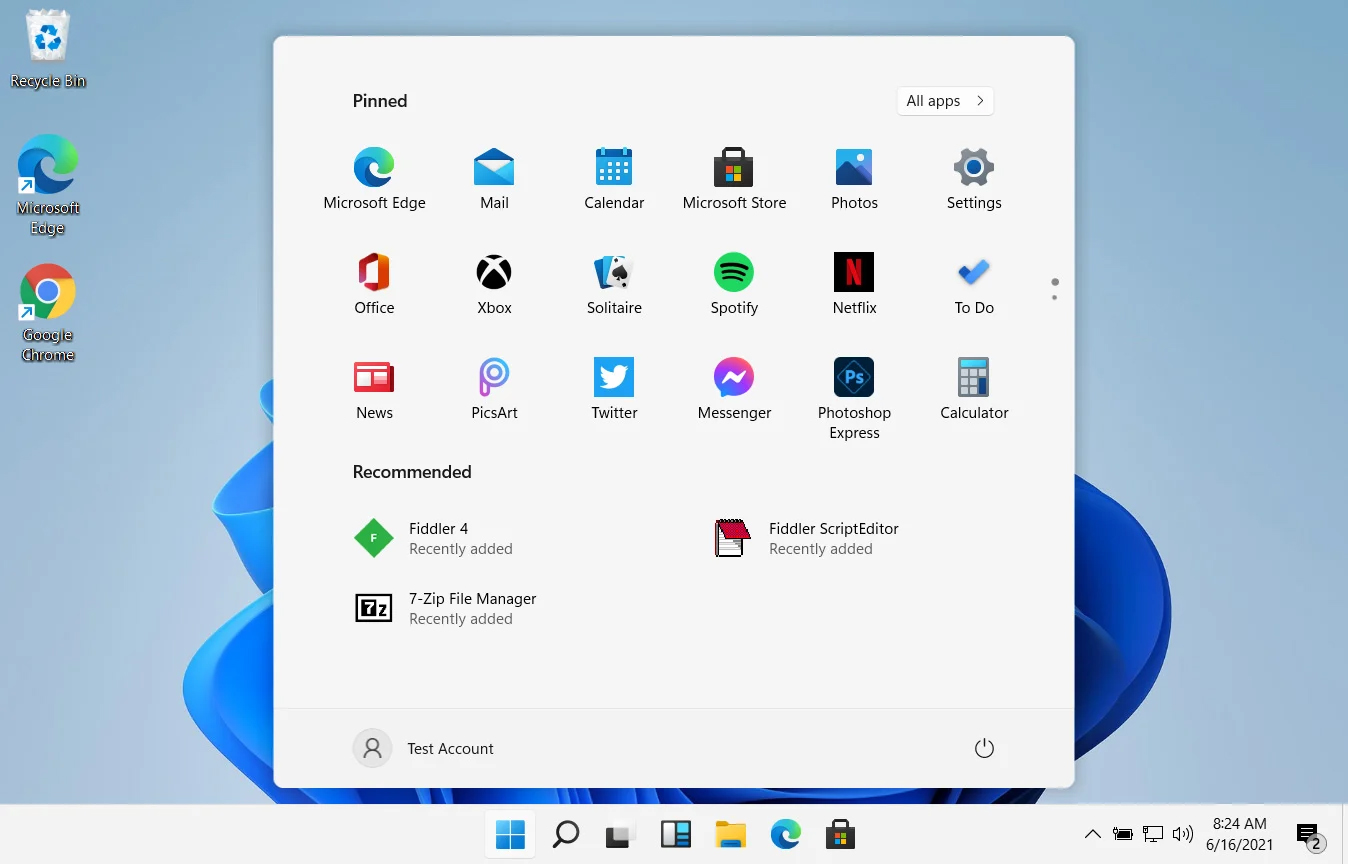 In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
