RadioRage is a potentially unwanted application developed by Mindspark Inc. This browser add-on is compatible with Mozilla Firefox, Internet Explorer and Google Chrome and claims to enhance the Internet browsing experience by allowing users to listen to their favorite music via the installed toolbar.
RadioRage Toolbar is categorized as adware since it infiltrates computers and after successful installation, this browser extension redirects browsers to home.tb.ask.com. And changes your default search engine to myway.com.
While active on your computer RadioRage collects user information such as browsing data, website clicks, and sometimes even sensitive user information, that it later sells / forwards to its ad distributors.
About Browser Hijackers
Browser hijacking is regarded as the internet’s constant risk that targets web browsers. It’s a type of malicious software that modifies your internet browser’s settings so that you are redirected to websites or pages that you had no intention of checking out. They are made to interfere with browser programs for many different reasons. These are typically used to force visitors to a specific website, manipulating web traffic to generate ad revenue. Most people assume that the browser hijacker is just a harmless website but that is not the case. Nearly all browser hijackers pose an actual threat to your online safety and it is necessary to classify them under privacy dangers. In a much worst case, your browser can be hijacked to download malicious software that will do a great deal of damage to your PC.
Key signs that your web browser has been hijacked
The typical signs that signify having this malicious software on your computer are:
1. your web browser’s home page is suddenly different
2. you get re-directed to internet sites you never intended to visit
3. The default search page of the browser is modified
4. you see multiple toolbars on the web browser
5. you might notice many pop-up ads on your screen
6. web pages load slowly and sometimes incomplete
7. you cannot go to specific sites such as home pages of security software.
So how does a browser hijacker infect a PC
There are many ways your computer could become infected with a browser hijacker. They typically arrive by way of spam email, via file-sharing websites, or by a drive-by download. They may also be deployed through the installation of a web browser toolbar, add-on, or extension. Some internet browser hijackers spread in user’s computers by using a deceptive software distribution method known as “bundling” (often through freeware and shareware). Well-known examples of browser hijackers include Conduit, CoolWebSearch, Coupon Server, OneWebSearch, RocketTab, Searchult.com, Snap.do, and Delta Search.
Browser hijackers might record user keystrokes to collect potentially valuable information leading to privacy concerns, cause instability on systems, drastically disrupt the user experience, and finally slow down the computer to a point where it becomes unusable.
Browser hijacker removal methods
One thing you can try to eliminate a browser hijacker is to locate the malware within the “Add or Remove Programs” list of the Windows Control Panel. It might or might not be there. When it is, try to uninstall it. But, the majority of hijackers are really tenacious and require specialized tools to get rid of them. Inexperienced PC users should never attempt the manual form of removal, as it demands detailed system knowledge to carry out repairs on the computer registry and HOSTS file.
What To Do If You Cannot Install Any Anti-virus?
Every malware is detrimental and the effects of the damage will vary based on the specific kind of malware. Some malware is meant to restrict or prevent things that you wish to do on your computer system. It may well not permit you to download anything from the internet or it will prevent you from accessing a few or all websites, especially the anti-virus sites. So what should you do if malware keeps you from downloading or installing Anti-Malware? Refer to the instructions below to eliminate malware through alternate methods.
Use Safe Mode to resolve the issue
If the malware is set to run at Windows start-up, then booting in Safe Mode should avoid it. Only the bare minimum required applications and services are loaded when you boot your computer or laptop into Safe Mode. Listed below are the steps you need to follow to eliminate viruses in Safemode.
1) At power on, hit the F8 key before the Windows splash screen begins to load. This will bring up the Advanced Boot Options menu.
2) Select Safe Mode with Networking with arrow keys and press ENTER.
3) As soon as this mode loads, you will have an internet connection. Now, get the malware removal software you want by utilizing the browser. To install the application, follow the guidelines in the installation wizard.
4) As soon as the software is installed, allow the scan run to eliminate viruses and other threats automatically.
Switch over to some other web browser
Certain viruses might target vulnerabilities of a particular browser that block the downloading process. When you suspect that your Internet Explorer happens to be hijacked by malware or otherwise compromised by online hackers, the ideal plan of action is to switch over to a different web browser such as Firefox, Chrome, or Safari to download your favorite computer security application – Safebytes Anti-Malware.
Run anti-malware from a pen drive
Another approach is to download and transfer an antivirus program from a clean PC to run a virus scan on the infected system. Follow these steps to employ a flash drive to fix your infected system.
1) Make use of another virus-free computer system to download Safebytes Anti-Malware.
2) Insert the pen drive onto the same computer.
3) Run the setup program by double-clicking the executable file of the downloaded software, with a .exe file format.
4) Select the USB flash drive as the destination for saving the file. Follow activation instructions.
5) Now, transfer the flash drive to the infected computer.
6) Double click the Safebytes Anti-malware icon on the pen drive to run the software.
7) Hit the “Scan” button to run a full computer scan and remove viruses automatically.
Let's Talk About SafeBytes Security Suite!
These days, anti-malware software can protect your laptop or computer from various forms of online threats. But wait, how to select the right one amongst several malware protection software that’s available in the market? Perhaps you might be aware, there are many anti-malware companies and tools for you to consider. Some are really worth your money, but many aren’t. When looking for anti-malware software, purchase one which gives solid, efficient, and complete protection against all known computer viruses and malware. One of the recommended software programs is SafeBytes AntiMalware. SafeBytes carries a really good reputation for top-quality service, and clients seem to be very happy with it.
SafeBytes anti-malware is a highly effective and user-friendly protection tool that is designed for end-users of all levels of computer literacy. This application could easily detect, remove, and protect your personal computer from the most advanced malware attacks including spyware, adware, trojan horses, ransomware, PUPs, worms, parasites as well as other possibly damaging software programs.
There are numerous amazing features you’ll get with this particular security product. Listed below are a few of the great ones:
Real-time Protection: SafeBytes gives you round-the-clock protection for your computer limiting malware intrusions in real-time. It’ll continuously monitor your laptop or computer for hacker activity and also gives end-users sophisticated firewall protection.
Antimalware Protection: Built upon a greatly acclaimed antivirus engine, this malware removal application is able to find and remove several obstinate malware threats such as browser hijackers, PUPs, and ransomware that other common anti-virus applications will miss.
Web protection: SafeBytes checks and gives a unique safety ranking to every site you visit and block access to webpages considered to be phishing sites, thus protecting you from identity theft, or known to contain malicious software.
Light-weight: This application is not “heavy” on the computer’s resources, so you’ll not find any performance problems when SafeBytes is working in the background.
24/7 On-line Tech Support: Support service is accessible 24 x 7 x 365 days via email and chats to answer your questions.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove RadioRage without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by RadioRage
Files:
C:Program FilesRadioRage_4jEIInstallr.binNP4jEISb.dl_
C:Program FilesRadioRage_4jEIInstallr.binNP4jEISb.dll
C:Program FilesRadioRage_4jEIInstallr.binjEIPlug.dl_
C:Program FilesRadioRage_4jEIInstallr.binjEIPlug.dll
C:Program FilesRadioRage_4jEIInstallr.binjEZSETP.dl_
C:Program FilesRadioRage_4jEIInstallr.binjEZSETP.dll
C:Program FilesRadioRage_4jEIInstallr.binjEZSETP.dll
C:Program FilesRadioRage_4jEIInstallr.binNP4jEISb.dl_
C:Program FilesRadioRage_4jEIInstallr.binNP4jEISb.dll
C:Program FilesRadioRage_4jEIInstallr.binjEIPlug.dl_
C:Program FilesRadioRage_4jEIInstallr.binjEIPlug.dll
C:Program FilesRadioRage_4jEIInstallr.binjEZSETP.dl_
C:PROGRA1RADIOR1Installr.binjEZSETP.dl_
C:Program FilesRadioRage_4jEIInstallr.binjEZSETP.dll
C:WINDOWSsystem32rundll32.exe
Registry:
Key HKLMSYSTEMCurrentControlSetServicesRadioRage_4jService
Key HKLMSYSTEMControlSet001ServicesRadioRage_4jService
Key HKLMSOFTWAREMozillaPlugins@RadioRage_4j.com/Plugin
Key HKLMSOFTWARERadioRage_4j
Key HKLMSOFTWAREMicrosoftWindowsCurrentVersionUninstallRadioRage_4jbar Uninstall Internet Explorer
Key HKLMSOFTWAREMicrosoftWindowsCurrentVersionUninstallRadioRage_4jbar Uninstall Firefox
Key HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects5848763c-2668-44ca-adbe-2999a6ee2858
Key HKLMSOFTWAREMicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects48909954-14fb-4971-a7b3-47e7af10b38a
Key HKLMSOFTWAREClassesRadioRage_4j.XMLSessionPlugin.1
Key HKLMSOFTWAREClassesRadioRage_4j.XMLSessionPlugin
Key HKLMSOFTWAREClassesRadioRage_4j.UrlAlertButton.1
Key HKLMSOFTWAREClassesRadioRage_4j.UrlAlertButton
Key HKLMSOFTWAREClassesRadioRage_4j.ToolbarProtector.1
Key HKLMSOFTWAREClassesRadioRage_4j.ToolbarProtector
Key HKLMSOFTWAREClassesRadioRage_4j.ThirdPartyInstaller.1
Key HKLMSOFTWAREClassesRadioRage_4j.ThirdPartyInstaller
Key HKLMSOFTWAREClassesRadioRage_4j.SkinLauncherSettings.1
Key HKLMSOFTWAREClassesRadioRage_4j.SkinLauncherSettings
Key HKLMSOFTWAREClassesRadioRage_4j.SkinLauncher.1
Key HKLMSOFTWAREClassesRadioRage_4j.SkinLauncher
Key HKLMSOFTWAREClassesRadioRage_4j.SettingsPlugin.1
Key HKLMSOFTWAREClassesRadioRage_4j.SettingsPlugin
Key HKLMSOFTWAREClassesRadioRage_4j.ScriptButton.1
Key HKLMSOFTWAREClassesRadioRage_4j.ScriptButton
Key HKLMSOFTWAREClassesRadioRage_4j.RadioSettings.1
Key HKLMSOFTWAREClassesRadioRage_4j.RadioSettings
Key HKLMSOFTWAREClassesRadioRage_4j.Radio.1
Key HKLMSOFTWAREClassesRadioRage_4j.Radio
Key HKLMSOFTWAREClassesRadioRage_4j.PseudoTransparentPlugin.1
Key HKLMSOFTWAREClassesRadioRage_4j.PseudoTransparentPlugin
Key HKLMSOFTWAREClassesRadioRage_4j.MultipleButton.1
Key HKLMSOFTWAREClassesRadioRage_4j.MultipleButton
Key HKLMSOFTWAREClassesRadioRage_4j.HTMLPanel.1
Key HKLMSOFTWAREClassesRadioRage_4j.HTMLMenu.1
Key HKLMSOFTWAREClassesRadioRage_4j.HTMLPanel
Key HKLMSOFTWAREClassesRadioRage_4j.HTMLMenu
Key HKLMSOFTWAREClassesRadioRage_4j.FeedManager
Key HKLMSOFTWAREClassesRadioRage_4j.FeedManager.1
Key HKLMSOFTWAREClassesRadioRage_4j.DynamicBarButton.1
Key HKLMSOFTWAREClassesRadioRage_4j.DynamicBarButton
 Error Causes
Error Causes Microsoft office has two major packages, an online one, and an offline version. The online version of the course is Office 365 that requires a monthly subscription and it is always regularly updated and maintained. Another version is more of a typical old school application, install it and use it, no constant internet connection is required and no monthly subscription is required, buy once and use it.
Microsoft office has two major packages, an online one, and an offline version. The online version of the course is Office 365 that requires a monthly subscription and it is always regularly updated and maintained. Another version is more of a typical old school application, install it and use it, no constant internet connection is required and no monthly subscription is required, buy once and use it.
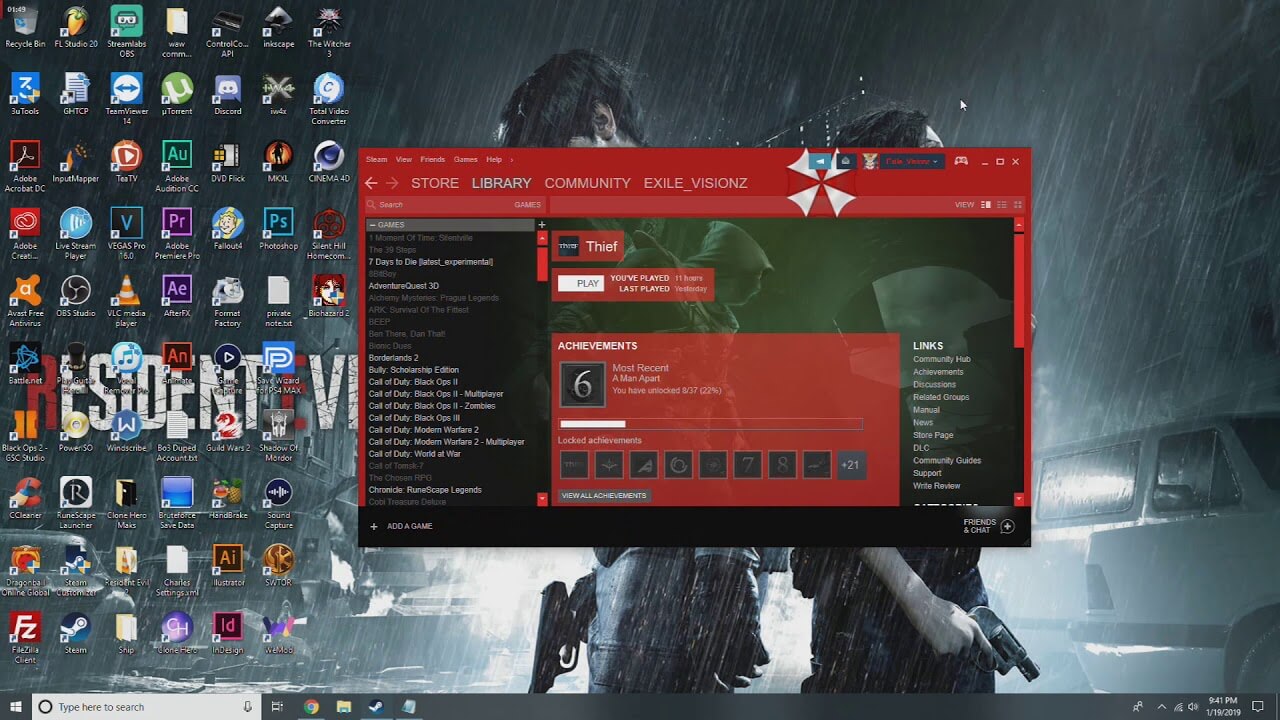 Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend
Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend 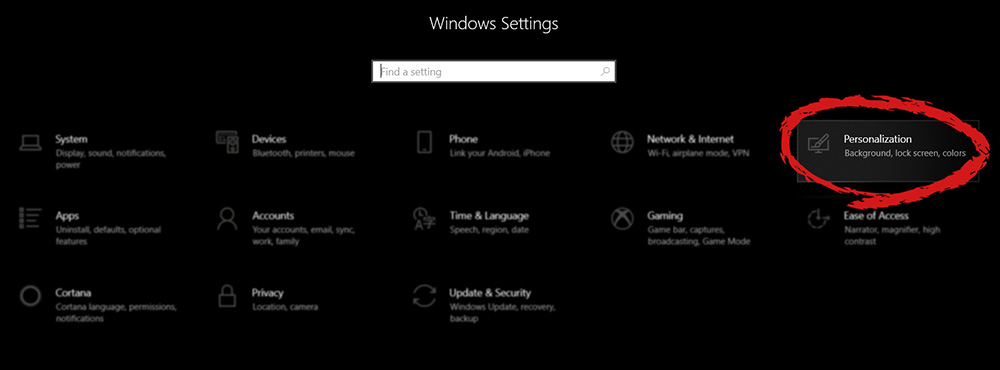 When the personalization setting opens go-to color tab on left and scroll down until you find 2 checkboxes under "show accent color on the following surfaces:"
When the personalization setting opens go-to color tab on left and scroll down until you find 2 checkboxes under "show accent color on the following surfaces:"
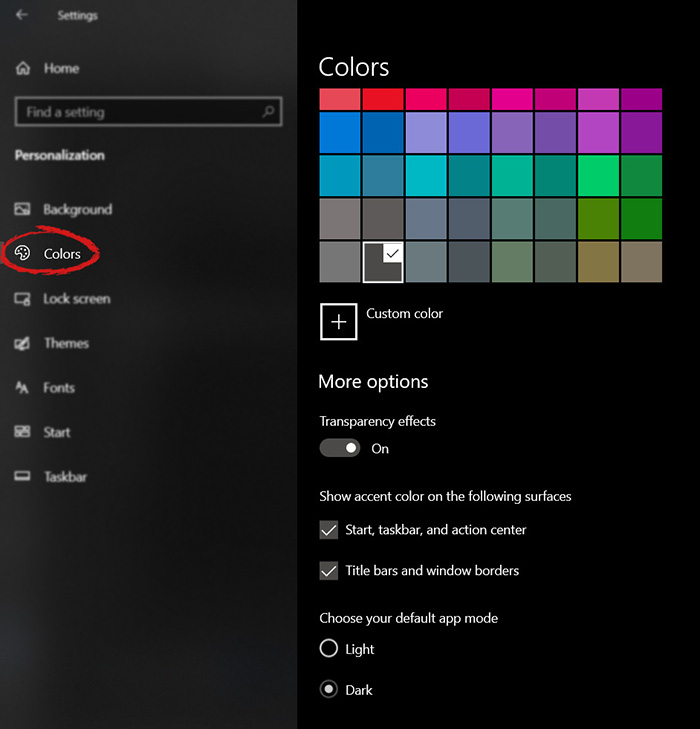 check ones you wish to apply the effect to and you are done. Now your START menu and/or title bars are using the color scheme of your choice.
check ones you wish to apply the effect to and you are done. Now your START menu and/or title bars are using the color scheme of your choice. 
 Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process:
Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process:
