FlightSearchApp is a browser extension for Google Chrome. This extension claims to be a simple tool to provide updates regarding flight arrivals, flight departures, flight tracking, and access to time zone converters. However, it is a potentially unwanted program which is also known as a browser hijacker.
This extension hijacks your browser home page and search engine changing it to MyWay. While this extension is active you will see additional ads, sponsored links, and sometimes even pop-up ads appearing through your browsing sessions. It also keeps track of your browsing data, recording your browsing activity, website visits, clicks, and potentially personal information. It also adds a toolbar to the browser header which can lag the browser while also reducing usable screen size.
Several anti-virus scanners have marked this extension as a Browser Hijacker, and is therefore not recommended to keep on your computer.
About Browser Hijackers
Browser hijacking is regarded as the internet’s constant risk that targets web browsers. It is a kind of malicious software that alters your web browser’s configuration settings so that you are redirected to websites or webpages that you had no intention of visiting. Basically, nearly all browser hijackers are made for marketing or advertising purposes. The idea would be to force users to visit particular websites which are looking to improve their visitor traffic and produce higher ad earnings. It might appear naive, but the majority of such sites are not legitimate and will pose a serious threat to your on-line safety. Some browser hijackers are designed to make certain modifications beyond the web browsers, like changing entries in the computer registry and allowing other malware to further damage your PC.
How one can know whether the browser is hijacked?
Symptoms that your browser is hi-jacked include:
1. the browser’s homepage is changed
2. you see new unwanted favorites or bookmarks added, typically directed to ad-filled or pornography websites
3. The default search page of your web browser is altered
4. unsolicited new toolbars are added to your web browser
5. many pop-up ads show up and/or your browser pop-up blocker is disabled
6. your web browser has become unstable or starts running slowly
7. You can’t access particular websites, in particular anti-virus sites.
How it infects your PC
Browser hijackers can get into a computer by some means or other, for instance via file sharing, downloads, and email too. They are generally included with toolbars, add-ons, BHO, plugins or browser extensions. Some browser hijackers spread in user’s computer systems using a deceptive software distribution technique known as “bundling” (usually through freeware and shareware).
Browser hijackers may record user keystrokes to collect potentially valuable information that leads to privacy issues, cause instability on computers, significantly disrupt user’s browsing experience, and finally slow down the computer to a point where it will become unusable.
Browser hijacker removal tips
Some types of browser hijackers can be quickly removed from your PC by uninstalling malicious programs or any other recently installed freeware. At times, it can be a challenging task to identify and eliminate the malicious component since the associated file could be running as part of the operating system process. On top of that, manual removal expects you to execute many time-consuming and intricate procedures that are very hard to carry out for new computer users.
You might opt for automatic browser hijacker removal methods by just installing and running an efficient anti-malware program. One of the recommended tools for fixing browser hijacker infections is SafeBytes Anti-Malware. It assists you eliminate any pre-existing malicious software on your system and provides you real-time monitoring and protection against new threats. Utilize a system optimizer along with your anti-malware to fix various registry issues, remove computer vulnerabilities, and enhance your computer's overall performance.
Virus Blocking Internet And All Anti-Malware Software? Do This!
Every malware is bad and the degree of the damage will differ greatly with regards to the type of infection. Some malware is meant to interfere with or prevent things that you wish to do on your personal computer. It may not allow you to download anything from the net or prevent you from accessing a few or all of the websites, particularly the anti-malware websites. If you’re reading this now, you have perhaps realized that a malware infection is the real cause of your blocked internet traffic. So how to proceed if you want to download and install an anti-malware program like Safebytes? There are some solutions you could try to get around with this issue.
Download the application in Safe Mode with Networking
Safe Mode is a unique, simplified version of Windows in which just bare minimum services are loaded to prevent malware and other troublesome applications from loading. If the malware is set to load immediately when PC starts, switching into this mode can prevent it from doing so. To start the computer into Safe Mode, hit the “F8” key on your keyboard just before the Windows boot screen shows up; Or after normal Windows boot up, run MSConfig, check “Safe Boot” under Boot tab, and click Apply. Once you are in Safe Mode, you can attempt to download and install your antivirus program without the hindrance of the virus. After installation, run the malware scanner to remove standard infections.
Utilize an alternate web browser to download an anti-malware program
Some malware mainly targets specific browsers. If this is your situation, use another internet browser as it could circumvent the malware. The ideal solution to overcome this issue is to opt for a browser that is well known for its security measures. Firefox contains built-in Phishing and Malware Protection to help keep you secure online.
Run anti-virus from your pen drive
Another solution is to save and run an antivirus software program completely from a USB drive. Follow these steps to run the antivirus on the affected computer system.
1) Download the anti-malware software on a virus-free PC.
2) Plug the Thumb drive into the uninfected computer.
3) Double click on the downloaded file to open the installation wizard.
4) Select the USB stick as the location for saving the software file. Do as instructed on the computer screen to finish off the installation process.
5) Transfer the flash drive from the clean PC to the infected PC.
6) Double-click the anti-malware software EXE file on the USB flash drive.
7) Hit the “Scan” button to run a full system scan and remove malware automatically.
Features and Benefits of SafeBytes Anti-Malware
In order to protect your computer or laptop from many different internet-based threats, it is important to install anti-malware software on your computer. But with countless numbers of anti-malware companies out there, these days it is tough to decide which one you should buy for your PC. Some of them do a good job in getting rid of malware threats while some will damage your PC by themselves. When looking for an anti-malware tool, purchase one which gives dependable, efficient, and comprehensive protection against all known viruses and malware. Among few good programs, SafeBytes Anti-Malware is the highly recommended software program for the security-conscious user.
SafeBytes anti-malware is a trustworthy tool that not only secures your system permanently but is also extremely easy to use for people of all ability levels. Through its cutting-edge technology, this software protects your personal computer against infections caused by different kinds of malware and other threats, including spyware, adware, viruses, worms, trojans, keyloggers, potentially unwanted programs (PUPs), and ransomware.
SafeBytes anti-malware provides an array of enhanced features that sets it aside from all others. The following are a few of the great ones:
World-class AntiMalware Protection: This deep-cleaning anti-malware application goes much deeper than most antivirus tools to clean out your PC. Its critically acclaimed virus engine finds and disables hard-to-remove malware that hides deep inside your computer.
Real-time Threat Response: SafeBytes offers completely hands-free real-time protection and is set to check, block and get rid of all computer threats at its first encounter. It will regularly monitor your pc for hacker activity and also gives end-users sophisticated firewall protection.
Safe Web Browsing: SafeBytes checks the links present on a webpage for possible threats and informs you whether the site is safe to visit or not, through its unique safety rating system.
“Fast Scan” Features: Safebytes AntiMalware, with its advanced scanning engine, gives ultra fast scanning which can quickly target any active online threat.
Minimal CPU Usage: SafeBytes is really a lightweight application. It use up a very small amount of processing power as it operates in the background so you are free to use your Windows-based PC the way you really want.
24/7 Online Support: You may get absolutely free 24/7 technical support from their IT experts on any product queries or computer security concerns.
All in all, SafeBytes Anti-Malware is a solid program since it has plenty of features and can identify and eliminate any potential threats. Once you’ve downloaded and installed SafeBytes Anti-Malware, you no longer have to bother about malware or any other security concerns. If you’re searching for the absolute best malware removal application out there, and if you don’t mind spending some money for it, opt for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you want to manually get rid of FlightSearchApp without using an automated tool, it may be possible to do so by deleting the application from the Microsoft Windows Add/Remove Programs menu, or in cases of web browser plug-ins, going to the browser’s AddOn/Extension manager and uninstalling it. You may even want to reset your home page and search providers, as well as delete temporary files, browsing history, and cookies.
Lastly, check your hard disk for all of the following and clean your computer registry manually to get rid of leftover application entries after uninstalls. Please remember that only experienced computer users should try to manually edit the registry because incorrect file removal results in a serious problem or even a PC crash. In addition, some malware is capable of replicating itself or preventing deletion. Doing this in Safe Mode is advised.
Files:
%PROGRAMFILES(x86)%\FlightSearch_fo
%PROGRAMFILES%\FlightSearch_fo
%UserProfile%\Local Settings\Application Data\FlightSearchTooltab
%LOCALAPPDATA%\FlightSearchTooltab
Registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe Debugger = svchost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe Debugger = svchost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\free.flightsearchapp.com
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings WarnOnHTTPSToHTTPRedirect = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings WarnOnHTTPSToHTTPRedirect = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore DisableSR = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe Debugger = svchost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe Debugger = svchost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run 3948550101
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run xas
HKEY_CURRENT_USER\Software\free.flightsearchapp.com
 Microsoft just released Windows 11 ISo file, based on the latest Insider Preview Build 22000.132. Inside build, you can try all-new features like clock updated app, snip tool, and everything releases so far via various patches. You can also use Windows 11 ISO file to do a clean install on your computer, but if you go with this option all of your existing files will be deleted.
Microsoft just released Windows 11 ISo file, based on the latest Insider Preview Build 22000.132. Inside build, you can try all-new features like clock updated app, snip tool, and everything releases so far via various patches. You can also use Windows 11 ISO file to do a clean install on your computer, but if you go with this option all of your existing files will be deleted.

 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
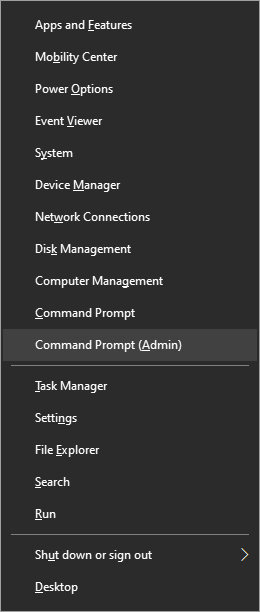 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
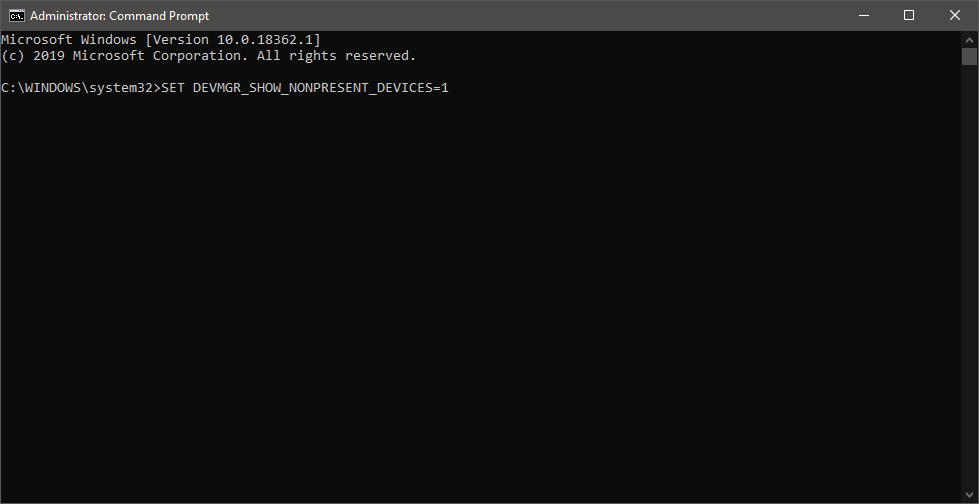 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
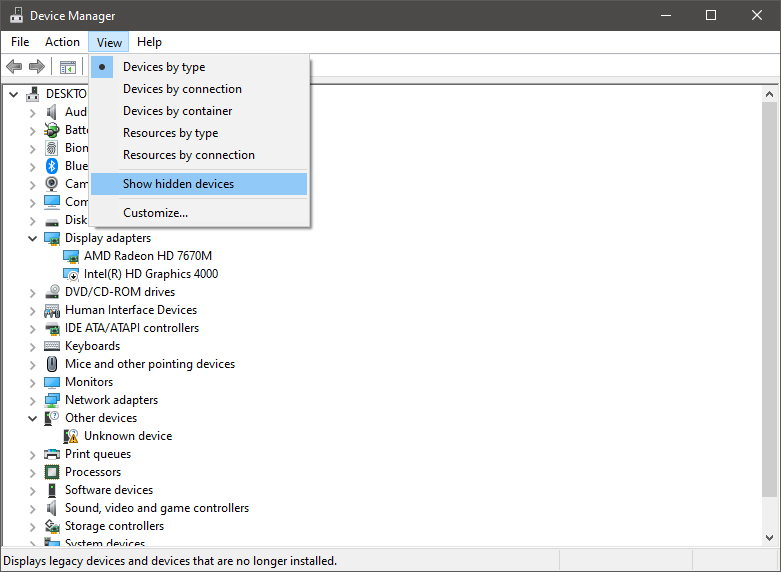
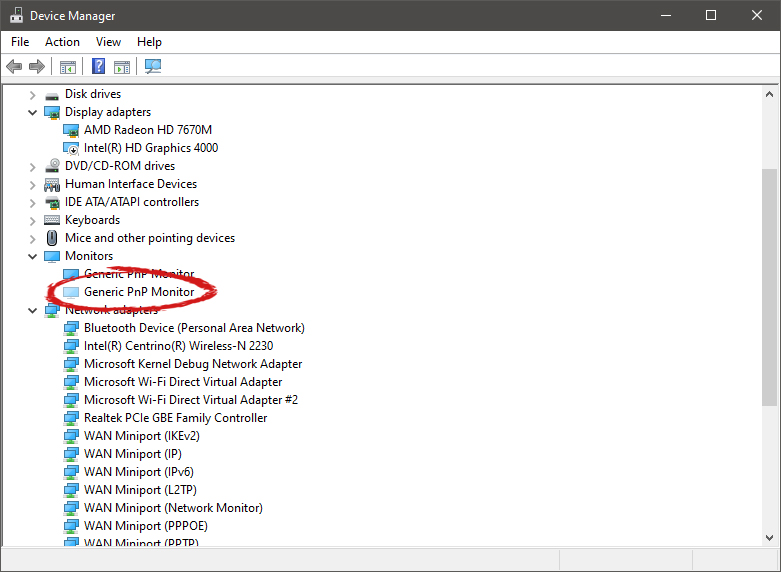 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
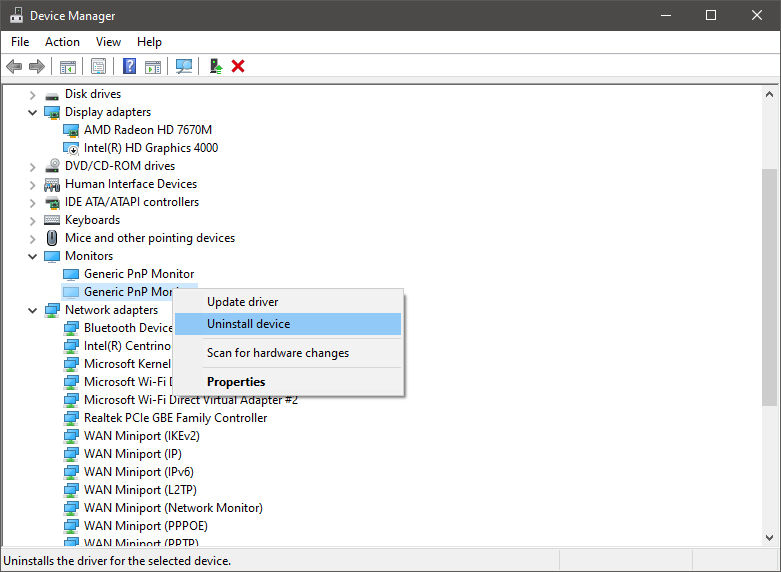 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 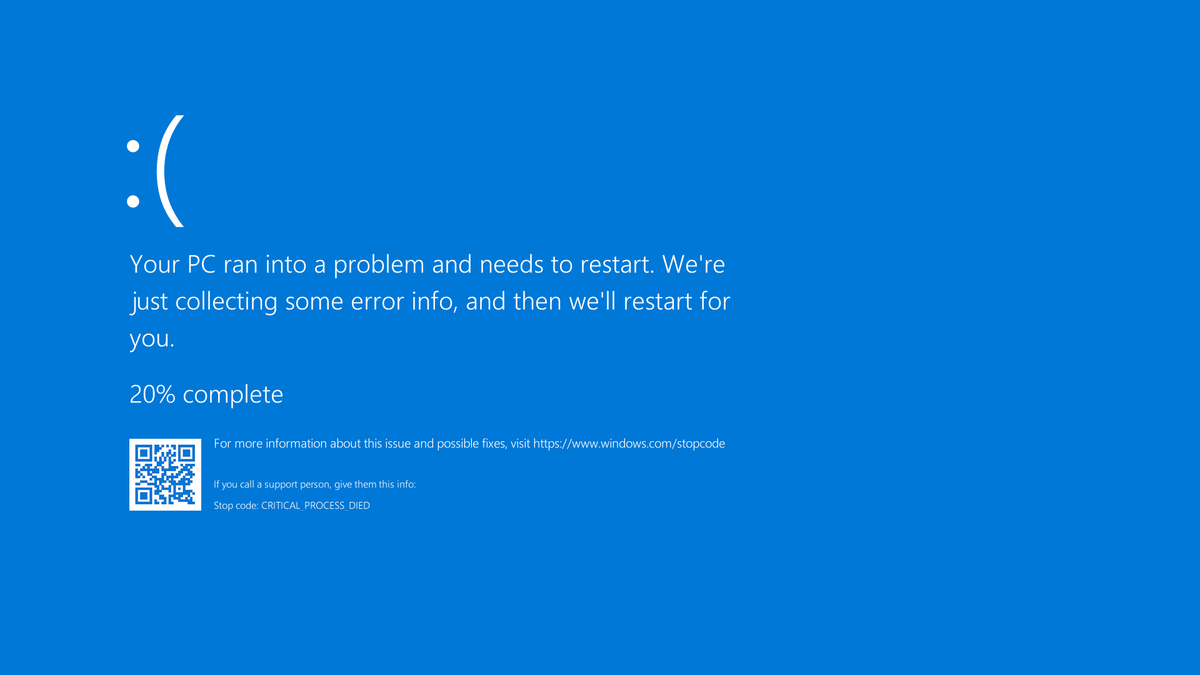 A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
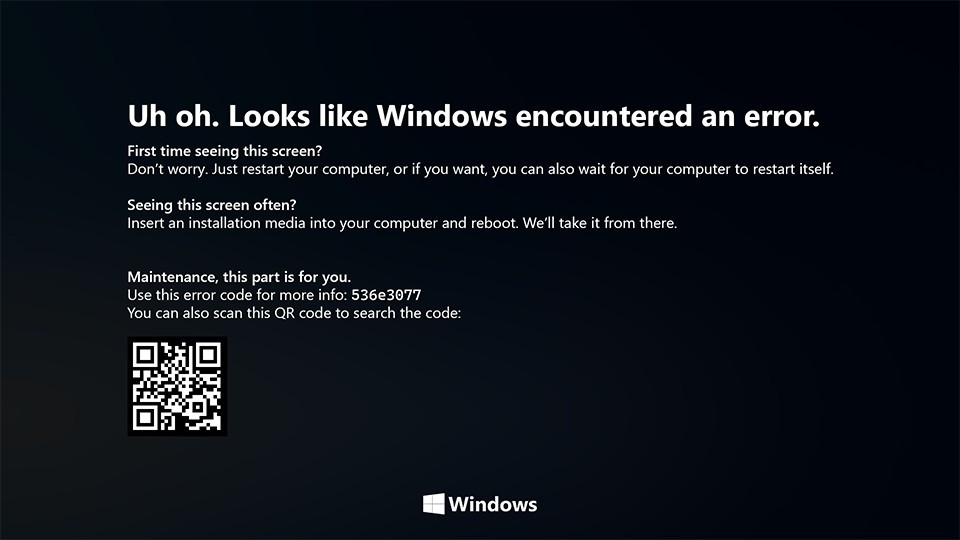 On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update.
On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
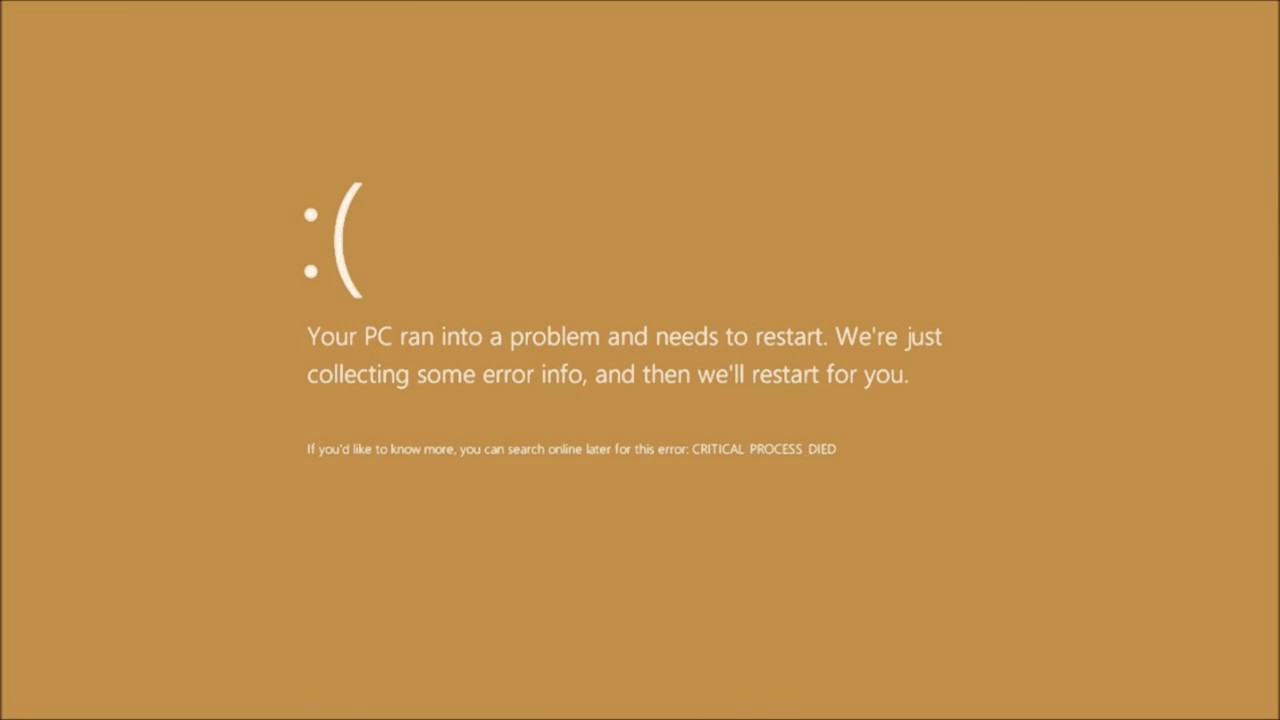 The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers). It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
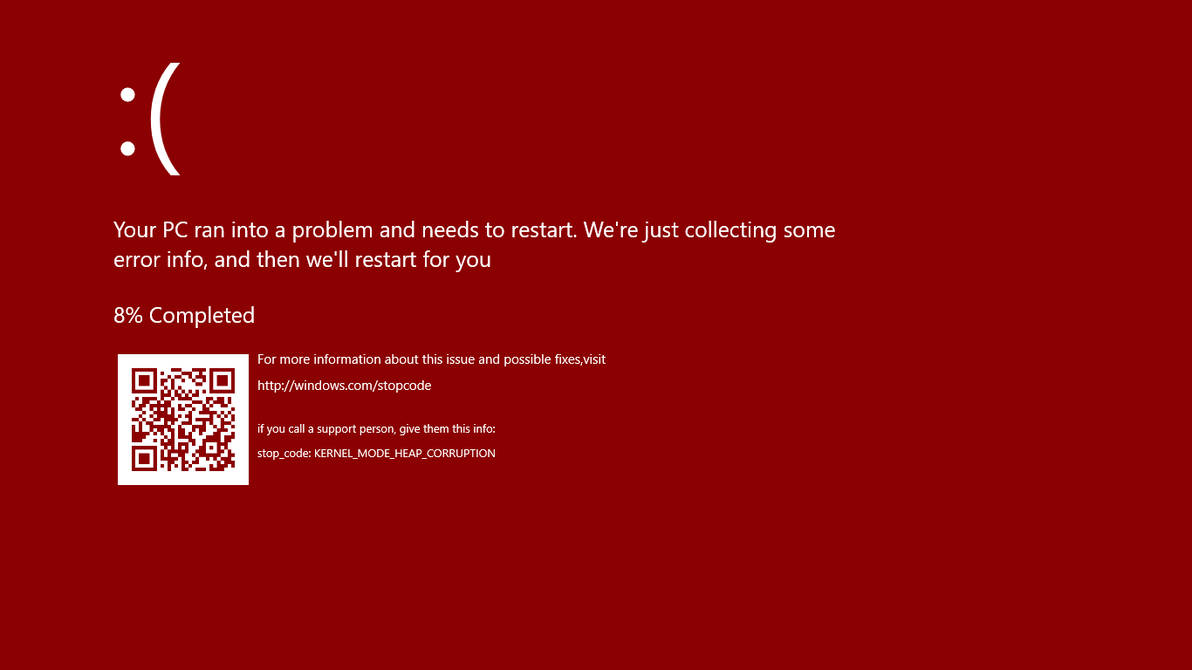 Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.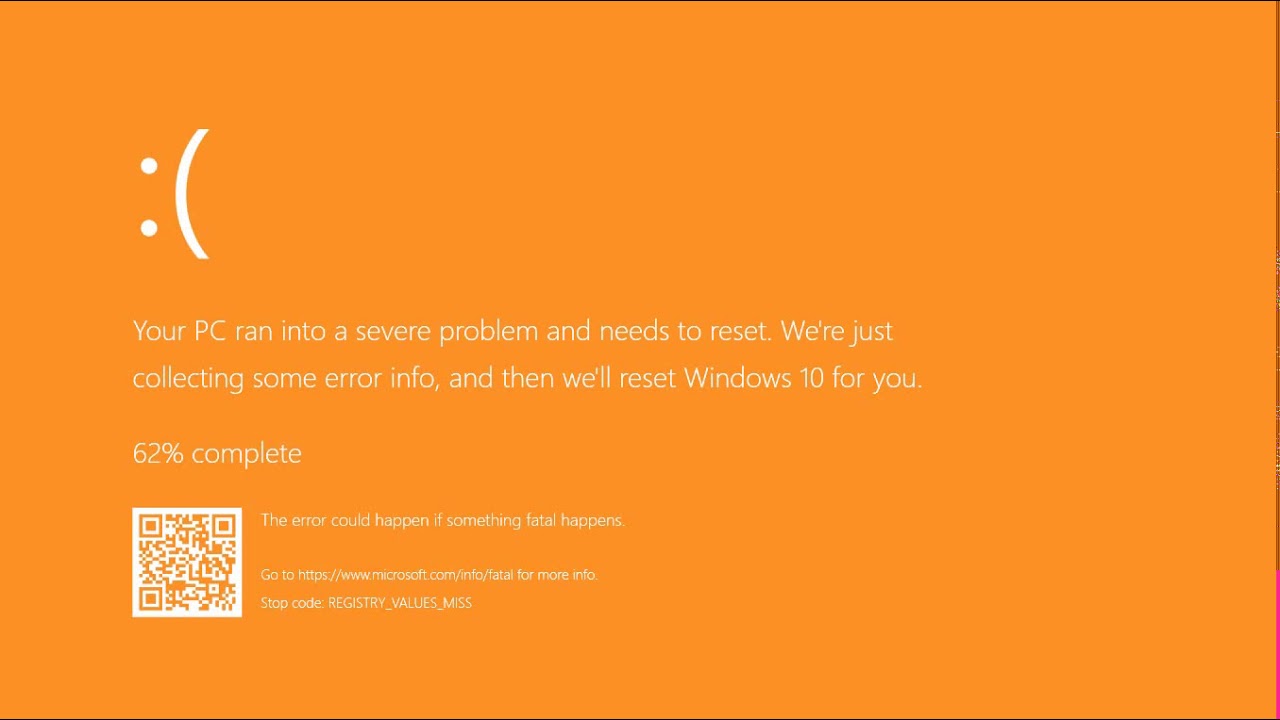 The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
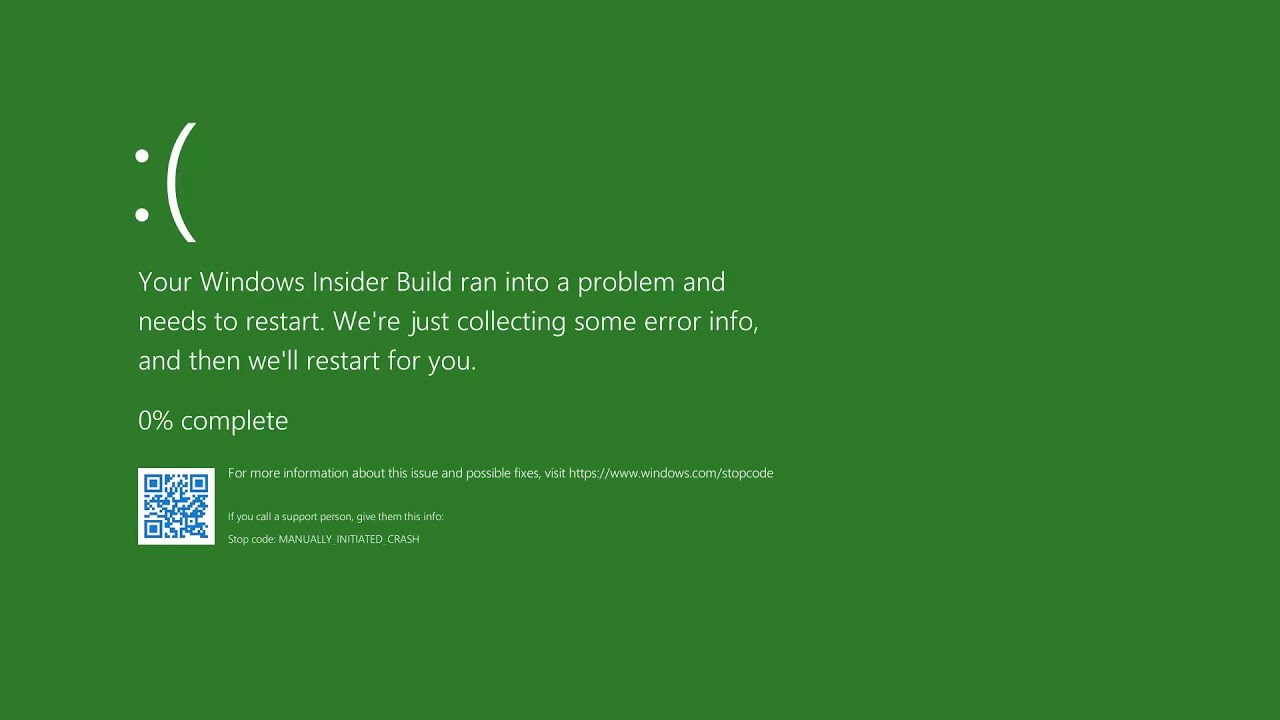 The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10. The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.
The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.