
A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested:
https://errortools.com/windows/what-is-deep-and-dark-web/
Now at this point in time, we want to present you with 15 great Deep WEB sites that could offer you some information not found anywhere else, that could offer you some privacy, or simply to have some fun and safely explore how it is like to be part of deep WEB.
Take notice that for successful visiting of given sites you will need to have installed TOR browser. More about Tor browser itself can be found here:
https://errortools.com/blog/software-review-series-tor-browser/ and its official website for download here:
https://www.torproject.org/download/
Make sure that you copy the onion link and paste it into your TOR browser in order to access the site. That being said, let’s begin.
Mail2Tor
http://mail2tor2zyjdctd.onion/
If you want secure and private ways of sending your emails then look no further. Mail2Tor uses a webmail client and encrypts each email received or sent, combine that for not storing IP addresses and you have a private and safe environment for your emails.
The Hidden Wiki
http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page
The Hidden Wiki is the go-to site if you want to explore more of deep WEB since it is the site of collected .onion sites. Think of it as a registry of onion sites that want to be accessed publicly but offer anonymity.
TorLinks
http://torlinksd6pdnihy.onion/
TorLinks is another site focusing on .onion site listings. Site themselves are divided into categories and are easy to find. Take note that .onion sites come and go so make sure to visit frequently both The Hidden Wiki and TorLinks in order to be updated.
Torch Search Engine
ttp://xmh57jrzrnw6insl.onion/
Torch is the oldest and most well-known search engine for dark web links, with its database of over a million .onion websites there is a chance that you will find what you are looking for on it.
DuckDuckGo
http://3g2upl4pq6kufc4m.onion/
Integrated into TOR itself as a default search engine DucDuckGo has proven itself to be a great competitor and challenger to Google. But unlike Google, DuckDuckGo will not track you nor store your search activities making it a great general private search engine.
Facebook
https://www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion/
Yup, Facebook has its own .onion version of its popular platform. Now since Facebook itself is a social media platform anonymity is out of the question but with .onion routing, you can have and maintain a Facebook account from locations where you normally could not like in some countries where Facebook.com is banned.
Galaxy3
http://galaxy3bhpzxecbywoa2j4tg43muepnhfalars4cce3fcx46qlc6t3id.onion/
Galaxy3 is also a social platform, the site is mostly populated with code experts and other individuals posting all kinds of stuff.
The Dark Lair
http://vrimutd6so6a565x.onion/index.php/Board
Dark Lair was the first image exchange website that evolved into a social network. One difference from the other two mentioned is that you can engage in the website without registration as an anonymous user.
Pro Publica
https://www.propub3r6espa33w.onion/
The aim of the five-time Pulitzer Prize winner ProPublica is “To expose abuses of power and betrayals of the public trust by government, business, and other institutions, using the moral force of investigative journalism to spur reform through the sustained spotlighting of wrongdoing.”
It’s the first major online publication to have a .onion address. The non-profit newsroom is funded by organizations such as the Sandler Foundation and has made countless contributions to the fight for free speech and privacy.
Soylent News
http://7rmath4ro2of2a42.onion/
Soylent news is an onion site that well brings news. The difference from other sites of the same content is that Soylent news is community moderated without any big names involved so it is authentic in its content.
CIA
ttp://ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion/
Tor’s history is an unlikely tale. It was created by the U.S Navy with the purpose of helping informants in foreign nations to communicate safely over the Internet. The Central Intelligence Agency (CIA), in that spirit, released a .onion site so that people from across the globe can browse their resources securely and anonymously.
Secure drop
https://secrdrop5wyphb5x.onion/
Secure drop is a platform for changing leaked information and for journalists to communicate with their leads in private. It is used by Washington Post, Pro Publica, and The Guardian.
Hidden Answers
http://answerszuvs3gg2l64e6hmnryudl5zgrmwm3vh65hzszdghblddvfiqd.onion/
Hidden Answers is Reddit or Quora of the dark web but as in the spirit of the dark web, all discussed topics and stories are in total anonymity.
SCI-HUB
http://scihub22266oqcxt.onion/
With over 50 million research papers in the domain of science shared freely, Sci-Hub eliminates all barriers of free knowledge and offers a unique approach to education and scientific information.
Smartmixer.IO
http://smrtmxdxognxhv64.onion/
Smartmixer is a bitcoin mixer. The service scrambles your bitcoin with other users making your purchases completely anonymous.
And that's it. 15 dark WEB onion sites you need to visit. I hope that you enjoyed the list and found something useful in it. Also, note that onion links can change overnight so if any of provided links do not work just go to DuckDuckGo and search for the site with the onion at the end.
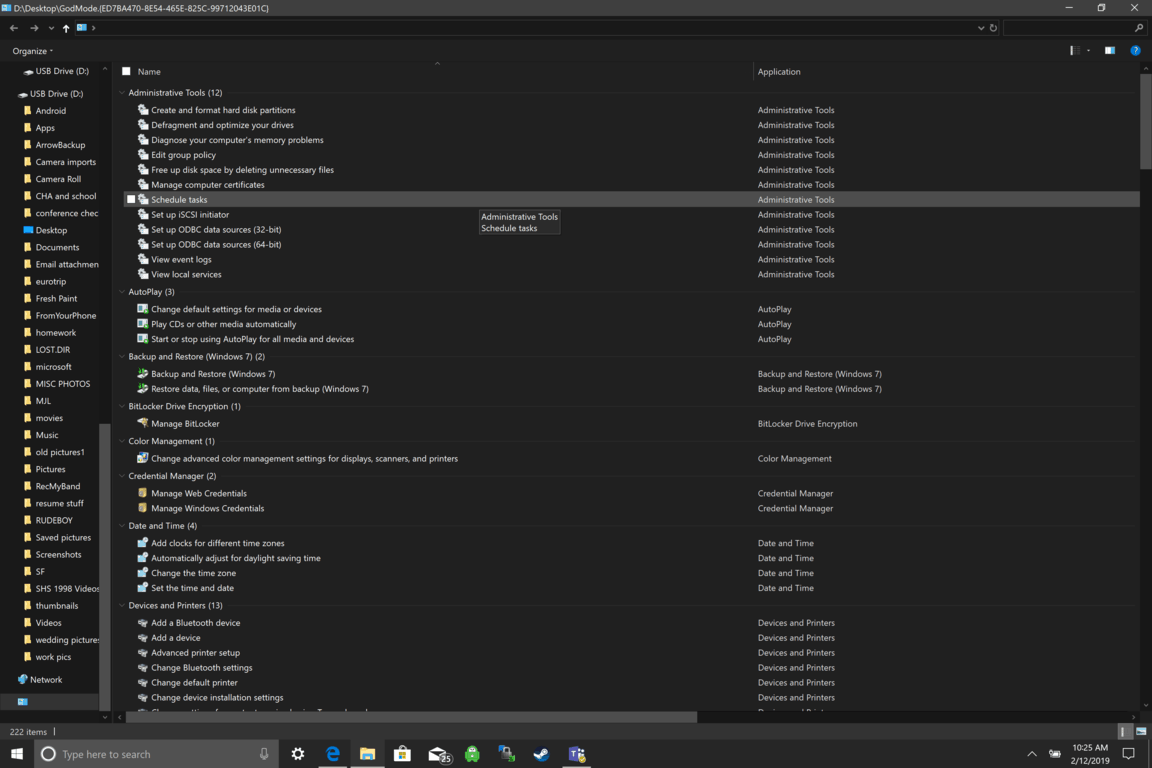 Like in Windows 10, Windows 11 will also support God mode to be enabled and used. For those readers that do know what God mode is, let me explain it in simple terms. God mode is the icon on the desktop that once clicked will open and let you adjust every option in the control panel and some hidden features for Windows inside one application.
Like in Windows 10, Windows 11 will also support God mode to be enabled and used. For those readers that do know what God mode is, let me explain it in simple terms. God mode is the icon on the desktop that once clicked will open and let you adjust every option in the control panel and some hidden features for Windows inside one application.

 A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested:
A not long time ago we had an article about the deep WEB and dark WEB here on errortools.com explaining its origins and its purpose. The article can be found here if you are interested:  Following a two-year investigation by the California Department of Fair Employment and Housing, the state has filed a lawsuit against Activision Blizzard for fostering a "frat boy" culture in which female employees are allegedly subjected to unequal pay and sexual harassment.
As reported by Bloomberg, Activision Blizzard is being accused by the state of California of discriminating against female employees at nearly all levels of employment, including in regards to compensation, promotion, assignments, and termination. The state alleges Activision Blizzard’s leadership has failed to address any of these outstanding issues or prevent them from occurring within the workplace. You can read the full details of the lawsuit here.
The suit, filed Tuesday in the Los Angeles Superior Court, says Activision Blizzard, which is made up of about 20 percent women, assigns women, and women of color, to "lower paid and lower opportunity levels" with lower starting pay for similar work as their male counterparts.
The documents also accuse Activision Blizzard of fostering a "pervasive 'frat boy' workplace culture in the office. Male employees are said to drink "copious amounts of alcohol" as they make their way through cubicles and "often engage in inappropriate behavior toward female employees."
Male employees are said to come to work hungover, play video games during work "while delegating their responsibilities to female employees, engage in banter about their sexual encounters, talk openly about female bodies, and joke about rape."
The lawsuit also cites one particular incident where a female employee, who was already subjected to intense sexual harassment at the company, committed suicide during a work trip with a male supervisor who allegedly brought inappropriate, sexual items with him on the trip.
The lawsuit is asking for an injunction that will force Activision Blizzard to comply with workplace protections, as well as deliver unpaid wages, pay adjustments, back pay, and lost wages and benefits for female employees.
Following a two-year investigation by the California Department of Fair Employment and Housing, the state has filed a lawsuit against Activision Blizzard for fostering a "frat boy" culture in which female employees are allegedly subjected to unequal pay and sexual harassment.
As reported by Bloomberg, Activision Blizzard is being accused by the state of California of discriminating against female employees at nearly all levels of employment, including in regards to compensation, promotion, assignments, and termination. The state alleges Activision Blizzard’s leadership has failed to address any of these outstanding issues or prevent them from occurring within the workplace. You can read the full details of the lawsuit here.
The suit, filed Tuesday in the Los Angeles Superior Court, says Activision Blizzard, which is made up of about 20 percent women, assigns women, and women of color, to "lower paid and lower opportunity levels" with lower starting pay for similar work as their male counterparts.
The documents also accuse Activision Blizzard of fostering a "pervasive 'frat boy' workplace culture in the office. Male employees are said to drink "copious amounts of alcohol" as they make their way through cubicles and "often engage in inappropriate behavior toward female employees."
Male employees are said to come to work hungover, play video games during work "while delegating their responsibilities to female employees, engage in banter about their sexual encounters, talk openly about female bodies, and joke about rape."
The lawsuit also cites one particular incident where a female employee, who was already subjected to intense sexual harassment at the company, committed suicide during a work trip with a male supervisor who allegedly brought inappropriate, sexual items with him on the trip.
The lawsuit is asking for an injunction that will force Activision Blizzard to comply with workplace protections, as well as deliver unpaid wages, pay adjustments, back pay, and lost wages and benefits for female employees.
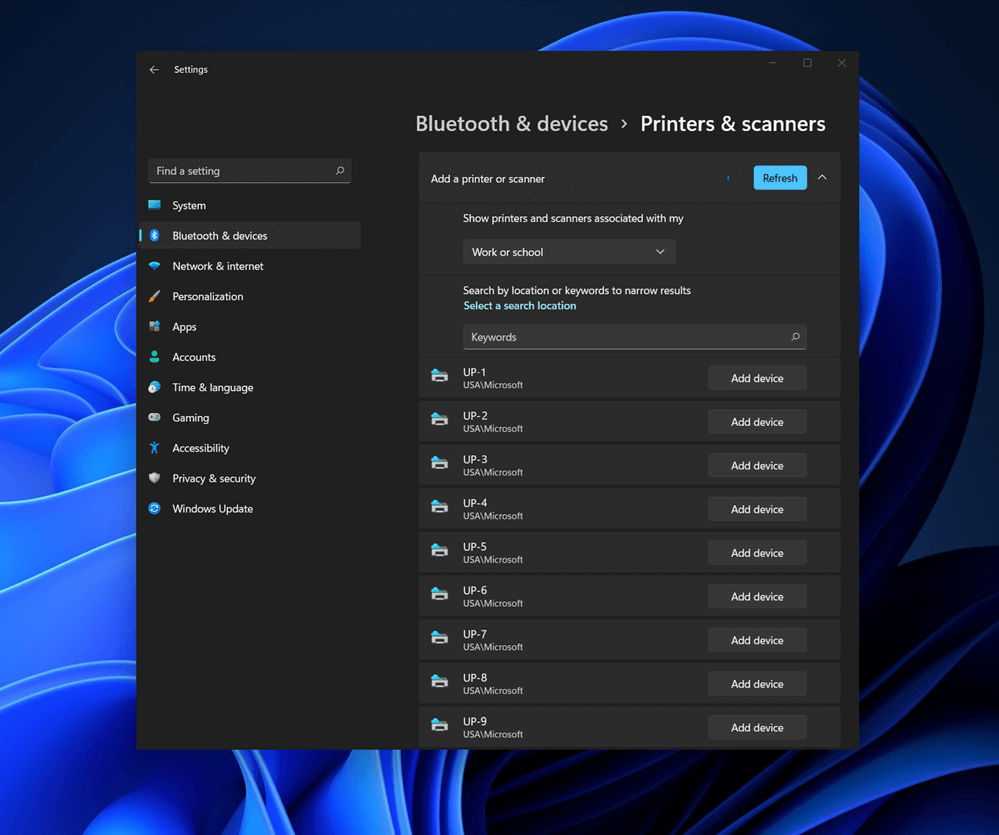 Bluetooth perhaps is slowly becoming an outdated feature but sometimes you can really used it and need it.
By default, in Windows 11 Bluetooth is turned OFF so if you need it, you will need to turn it ON first. Luckily turning it ON is easy and we will guide you through the process
Bluetooth perhaps is slowly becoming an outdated feature but sometimes you can really used it and need it.
By default, in Windows 11 Bluetooth is turned OFF so if you need it, you will need to turn it ON first. Luckily turning it ON is easy and we will guide you through the process
