Error Code 0x80073afc - What is it?
Error code 0x80073afc deals with an antivirus program first built into Windows 8/8.1 This error occurs when Windows Defender, the built-in anti-virus software in Windows 8/8.1 and higher, does not start automatically and users attempt to manually start the program. During the initialization period of the program start-up, something goes wrong and users get a 0x80073afc Error message. The error message states there was a problem with the initialization of the program. Windows Defender provides protection of your computer and it is advised by the Microsoft Corporation that you ensure it starts up automatically on every start-up.
Solution
 Further Information and Manual Repair
Further Information and Manual Repair
Users have found several manual repairs that have fixed the problem without needing to contact technicians for extra help. While the methods below should solve your problem easily, if this is the first time you have encountered the issue you may want to do a simple restart. This has fixed the problem for some users and is the easiest first troubleshooting move. If it doesn’t work move on to the methods listed below, which are easily completed without extra help.
Before trying any of these methods, please make sure that you are logged into a profile that is listed as the administrator of the computer of his administrative powers enabled. If this is not the case you will not be able to complete the following methods. Please log out and log back in on the administrator profile.
Method 1:
First, check to see if you have a third-party anti-virus program installed on your computer. Some users believe that the built-in Windows Defender program is not powerful enough to handle the safety of their computer so they usually download a third-party program. However, that program may have caused a conflict with Windows Defender and may not allow it to open. If you do have a third-party program installed, try uninstalling it then manually starting Windows Defender.
Method 2:
If method one does not work, you may be infected by malware or a virus that has tampered with the settings on your computer and will not allow Windows Defender to start automatically or manually.
First, open Run by holding the “Win” key and pressing the “R” key. Then type “Regedit”. The program will ask for permission to follow through with this action. Click on “Yes” and the Open Registry Editor will open.
Find the HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionImage File Execution Option and check to see if there are any files similar to MSASCui.exe or MpCmdRun.exe. If there are any file entries that resemble that, you will want to right-click on them before selecting the “Delete” option. If you do not see any entries that match, this is not the issue with your Windows Defender and you will want to try another method.
The Registry on your computer is very important. It helps tell your computer what programs are safe to run, what programs should be run, and what programs should not be run. If it is tampered with by a virus or Malware, multiple system operations can be affected.
However, if you did find similar file names, and you deleted them, try to start Windows Defender manually. If it does not work again, move on to the next method.
Method 3:
If the first two methods do not work for your issue, and you are still receiving error code 0x80073afc when attempting to start Windows Defender, this step should solve the problem if you have Restore Point installed on your computer, which you most likely do.
For this method, we will be restoring your computer to a previous Restore Point. First, just like in method two, hold the “Win” key and press the “R” key. This will open run. Next type “Rstrui.exe” and click “ok”. After some time, you will see System Restore Windows. Click “Next” and select the restore point that you would like to go back to. After your computer has restored to the point you selected, check to ensure that Windows Defender has started correctly.
If the above methods aren't able to rectify the issue, you might have to download and install a powerful automated tool to get the job done.

 To personalize the lock screen do:
To personalize the lock screen do: With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
 Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
 The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
 HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
 HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price.
HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price. 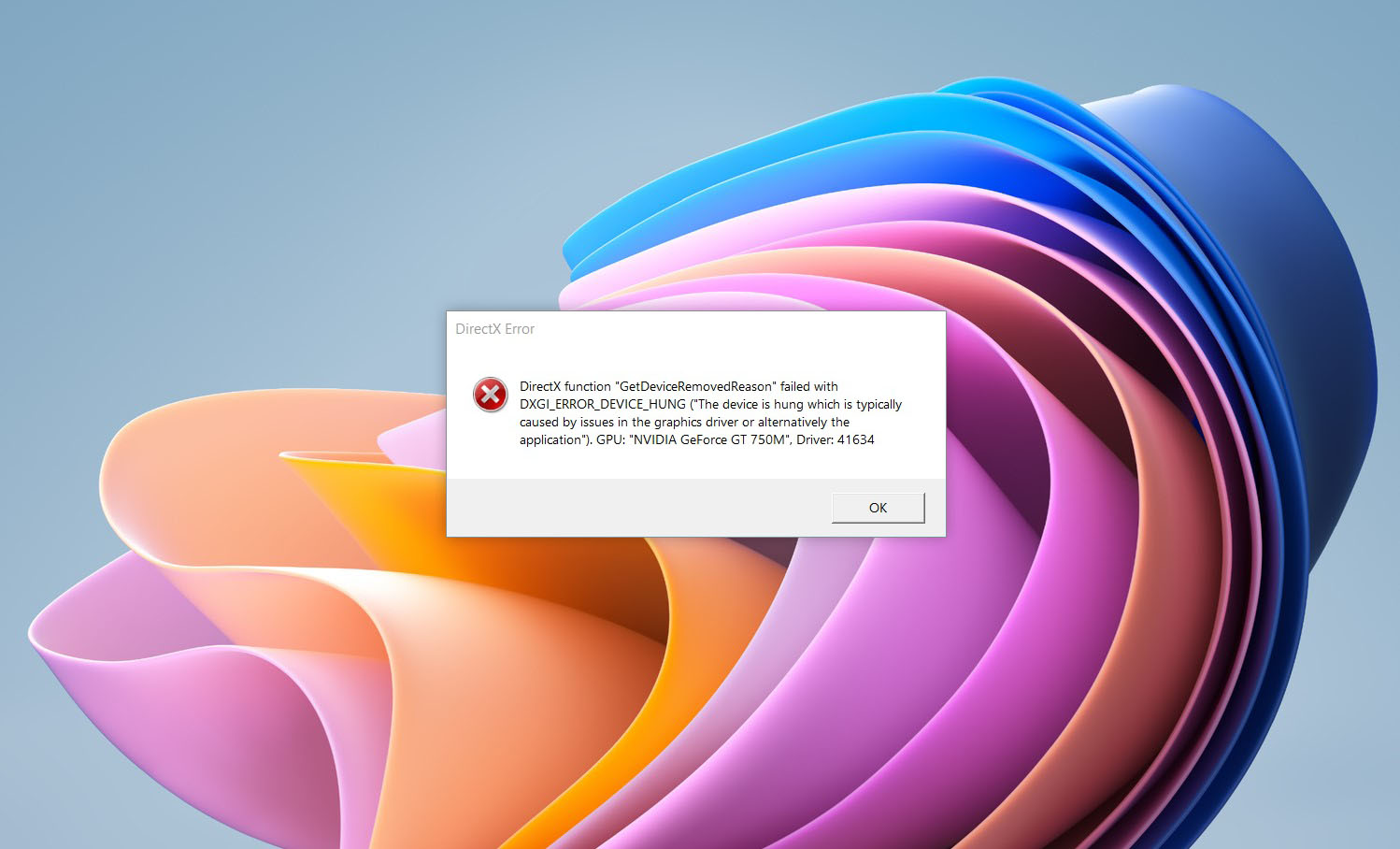 If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
 In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
 Fear not because we had this issue and tried several things in order to overcome the problem and after some time here is a list of what can you do if you are facing this exact issue. The list is written from most simple solutions to more complex ones and it is advisable to follow it as presented. That being said, let's dive into solving the problem.
Fear not because we had this issue and tried several things in order to overcome the problem and after some time here is a list of what can you do if you are facing this exact issue. The list is written from most simple solutions to more complex ones and it is advisable to follow it as presented. That being said, let's dive into solving the problem.

