Error Code 0x80070652 – What is it?
Error code 0x80070652 occurs when Windows users attempt to upgrade their operating system while another program is in the process of being downloaded. It may also occur due to problems related to previously failed update attempts within Window Update. When this Windows 10 upgrade occurs, Windows users fail to access the version of Windows they are attempting to download. Instead, a message box occurs stating that error code 0x80070652 has occurred on the device. If this error message is not rectified, it could give birth to other Windows 10 errors such as error code 0x80072EE2.
Solution
 Error Causes
Error Causes
Error code 0x80070652 may result from Windows 10 users attempting to download another program while upgrading their operating system. It may also be caused by an issue related to previous installations of updates. For instance, in some cases, your previous installation of the Windows process may have been interrupted or it was simply not completed properly. This causes any other upgrade process that follows to result in error code 0x80070652.
Further Information and Manual Repair
But what can be done in such a situation to resolve the error code? Windows users have several options available. For instance, they can wait on any additional program that may be in the process of downloading to complete the process before attempting to upgrade Windows. They may also troubleshoot problems related to any failed updates or select a system restore point in which the error code was not present.
The manual repair methods Windows 10 users choose may involve any of the solutions mentioned previously. The choice is largely dependent on the user and his determination to fix the error code. However, note that automated tools or Windows repair technicians may also provide solutions to PC issues like error code 0x80070652.
Method One: Verify and Troubleshoot Failed Upgrades
Since previously failed updates within Windows Update can lead to the occurrence of error code 0x80070652, Windows 10 users will need to verify which of these failed updates occurred by checking the history section of the Windows Update tool. Once you’ve been able to verify that failed updates have occurred in the recent past, you’ll need to troubleshoot these problems to rectify the error code. Follow the instructions below to check for updates that have failed to install properly via Windows Update.
- Step one: Type Windows Update in the Search box near Start Menu
- Step two: Select Windows Update settings
- Step three: Select Update history
- Step four: Review updates from the most recent to least recent to see which updates have failed
- Step five: Click failed updates for more details and troubleshoot accordingly.
Once you’ve completed the troubleshooting of any updates which failed, proceed by rebooting your device. You may then reattempt to upgrade to the latest version of Windows 10 once no other program is in the process of being downloaded.
If the problem causing error code 0x80070652 was related to failed updates of the past, these issues will likely be resolved once you successfully troubleshoot them. However, if the error code reoccurs, apply the next manual repair solution mentioned in this article.
Method Two: Download Updates Manually via Microsoft Download Center
Another option available to users is simply downloading updates manually by visiting the official Microsoft website, specifically the Windows section which provides downloads. To successfully complete this process, ensure you look for stand-alone packages of these downloads available on the website. You will need to know the Microsoft Knowledge Base (KB) article number related to the specific update(s) which failed.
Once a Windows user has verified the KB article number of the specific update, download it from the Microsoft website, then select Run to install the update. Reboot your PC, then check Windows Update to see if you are able to successfully complete the Windows 10 upgrade.
If the upgrade fails, you may need to implement the next manual repair method as is mentioned below.
Method Three: Use Windows System Restore
One of the best options for Windows 10 users facing certain PC problems is to apply System Restore. This allows them to reset their machine for a period of time in which the problem was not present. This is known as the restore point. To apply this manual repair method, follow the steps below.
- Step one: In the search box beside the Start Menu, type System Restore
- Step two: Select Create a restore point
- Step three: Select the System Protection tab then Configure or Create
- Step four: Provide details regarding a system restore point of your choice
- Step five: Select Create, then OK.
Method Four: Download an Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.

































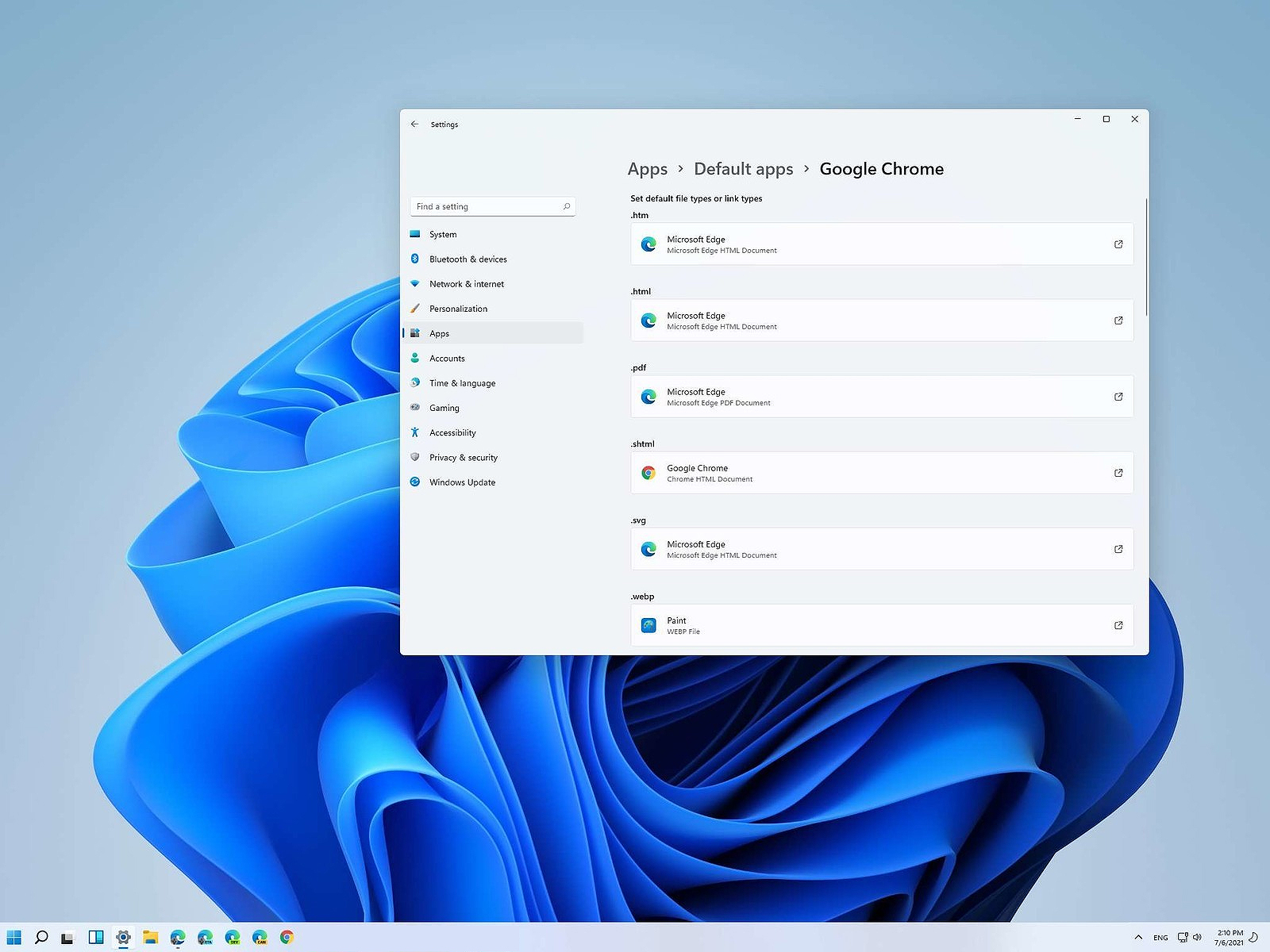 Same as in previous Windows versions, Windows 11 will also use certain applications as default ones for opening certain file types and file extensions. And yes, same as in previous versions it will come preconfigured for certain file types and associated applications like for example photos for pictures.
Of course, users usually have their own favorite applications for certain file types and much more prefer to open them inside the application of their choice instead of the default one.
We can change the default application like in previous Windows versions but this time there are two ways and overall more control of this process. Windows 11 has settings for choosing default file type applications and default file extension applications giving you more control of this process.
Same as in previous Windows versions, Windows 11 will also use certain applications as default ones for opening certain file types and file extensions. And yes, same as in previous versions it will come preconfigured for certain file types and associated applications like for example photos for pictures.
Of course, users usually have their own favorite applications for certain file types and much more prefer to open them inside the application of their choice instead of the default one.
We can change the default application like in previous Windows versions but this time there are two ways and overall more control of this process. Windows 11 has settings for choosing default file type applications and default file extension applications giving you more control of this process.

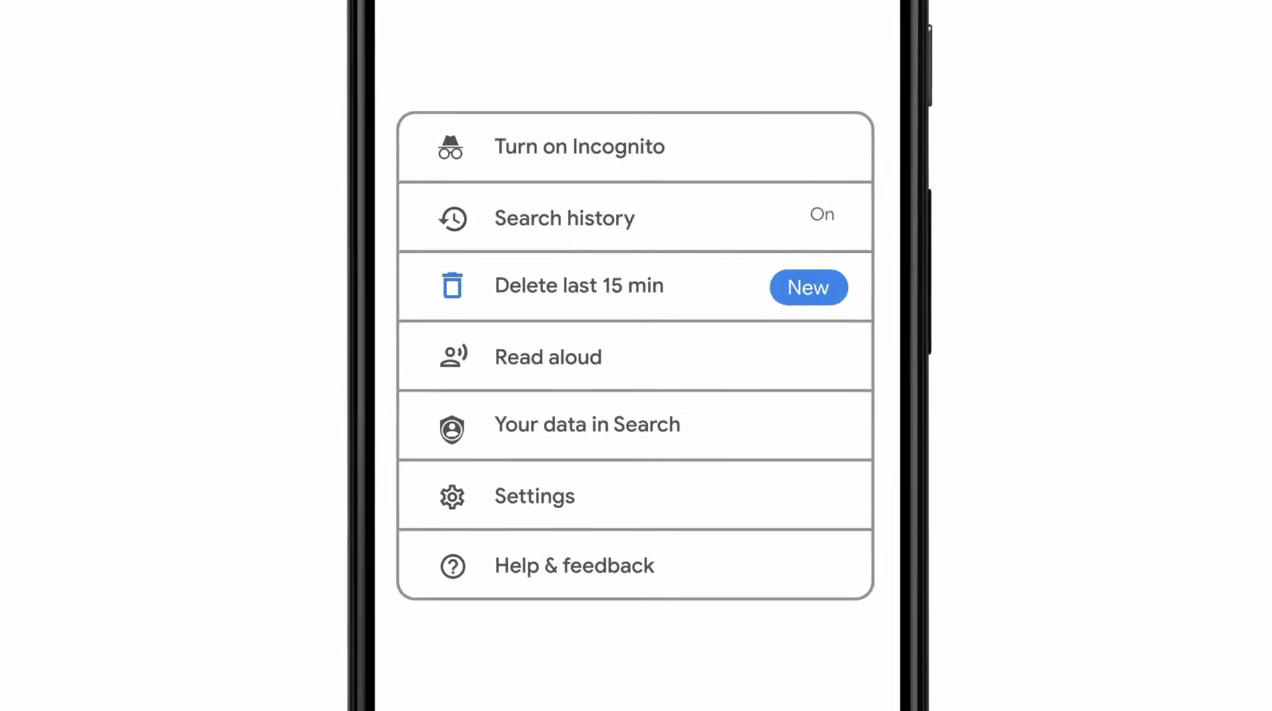 As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes."
As previously announced by Google feature to quickly delete the last 15min of browsing history via one button is rolling out now.
For now, only Apple users will be available to use this feature but the Android update is scheduled for later this year, a strange move by Google but it is what it is.
For anyone who is unfamiliar with this feature, basically, Google wants a quick way to remove the last 15min of browsing history as a supposedly stated request to make deleting browsing history much easier.
Google came up with this idea so you can keep the previous history intact but remove just 15min time frame, no additional explanation was given on why 15 but I presume it is some round number that came up as the middle one with research, read telemetry info.
Using quick delete requires being signed into Search with a Google account. Users can access the option by simply tapping on the avatar icon to access the settings then choosing "Delete last 15 minutes." 
