What is Ammyy Admin
AmmyyAdmin is a software developed by Ammy. This software allows you to manage network computers and servers remotely without complicated NAT settings adjustments or Firewall problems. The program is similar in marketed function to TeamViewer or LogMeIn. This software does not require installation and it lets you control other computers or share files over the software. It usually comes bundled with other software.
This software copes files into your computer and sometimes creates new startup keys that allow it to start each time your computer is restarted. AmmyAdmin might display additional ads in your browser as well as pop-up ads. Due to its ability to silently install and run remote administration, it could be used maliciously by those who intend to damage your computer or steal data. AmmyyAdmin is flagged for optional removal, and if you did not intentionally install it, removal is highly recommended
What is a Potentially Unwanted Program (PUP)?
If you’ve ever downloaded freeware or shareware, odds are high that your computer can get installed with a bunch of unwanted programs. A PUA / PUP (potentially unwanted application / potentially unwanted program) is a software program that comes bundled with freeware/shareware and you agree to install it on your computer system. These are programs you definitely don’t want on your system simply because it does not give any beneficial service.
PUP doesn’t involve malware in the traditional sense. One simple difference between malware and PUP is distribution. Malware is typically dropped through vulnerability exploitation and in contrast, PUP gets installed with the consent of the end-user, who consciously or unknowingly authorizes the PUP installation on their computer. A PUP might not be viewed as malicious or harmful but nonetheless, it is a common cause of clunky operating systems; some PUPs are a lot more aggressive by deliberately slowing down your PC.
How PUPs affect you?
Potentially Unwanted Programs appear in different forms and varieties, but most times, they are adware programs that exhibit irritating pop-up adverts and advertisements on web pages you explore. In addition, most free software nowadays comes with quite a few unwanted add-ons; in many instances a web browser toolbar or browser modification like a homepage hijacker. They’ll modify browser settings, change default search provider, substitute the default home page with their very own websites, decelerate internet speed, and will damage your computer as well.
They could look harmless but PUPs are usually spyware. Some might carry dialers, keyloggers, web browser hijackers, and tracking components that will collect system details, or tracks customer habits and relays these records to third-party organizations. Because of this unwanted program, your application might freeze, your security protections could get disabled which may leave the computer susceptible, your system may get damaged, and the list goes on and on.
Tips on protecting yourself from unwanted software
• When installing anything on your PC, always read the fine print, including the EULA. Do not accept terms of use that are for bundled programs.
• Select the “custom” install whenever downloading a software program. Particularly, pay attention to those small boxes which have been checked as default, where you might ‘agree’ to receive advertisements or install software bundlers.
• Use anti-PUP software. Security applications like Safebytes Anti-Malware offer the very best real-time protection from PUPs and also other malware.
• Be alert if you download and install freeware, open-source programs, or shareware. Avoid downloading and installing browser extensions and programs you are not knowledgeable about.
• Use only official product sites for downloading applications. Avoid download websites completely since the majority of websites force users to download the software using their own download manager, which is often bundled with some kind of unwanted program.
Safebytes Anti-Malware scans and detects malware for free. To complete removal, and ensure full PC protections, a paid license key is required.
Malware could potentially cause a lot of damage to your computer. Some malware sits in between the computer and the net connection and blocks a few or all internet sites that you would like to check out. It could also block you from installing anything on your computer, particularly anti-virus programs. If you are reading this article now, you’ve perhaps recognized that a malware infection is a reason behind your blocked net connectivity. So what do if you need to download and install an anti-virus application like Safebytes? There are a few solutions you can attempt to get around with this issue.
Boot Windows in Safe Mode
The Windows-based PC includes a special mode called “Safe Mode” where only the minimum required programs and services are loaded. In the event the malware is blocking internet connection and affecting your PC, running it in Safe Mode enables you to download antivirus and run a scan while limiting potential damage. To enter into Safe Mode or Safe Mode with Networking, press F8 while the system is booting up or run MSCONFIG and locate the “Safe Boot” options in the “Boot” tab. Once you’re in Safe Mode, you can try to download and install your anti-malware software program without the hindrance of the malicious software. Following installation, run the malware scanner to eliminate most standard infections.
Obtain the security program in an alternate web browser
Certain malware may target vulnerabilities of a specific web browser that obstruct the downloading process. If you seem to have a virus attached to Internet Explorer, then switch over to an alternate browser with built-in security features, such as Firefox or Chrome, to download your favorite antivirus program – Safebytes.
Create a portable anti-malware for removing malware
Here’s another solution which is utilizing a portable USB antivirus software that can check your system for malicious software without the need for installation. Adopt these measures to run the anti-malware on the infected computer system.
1) On a clean computer, install Safebytes Anti-Malware.
2) Plug the Thumb drive into the uninfected computer.
3) Double-click the exe file to run the installation wizard.
4) Pick a USB flash drive as the location when the wizard asks you where you want to install the program. Follow the on-screen instructions to finish the installation process.
5) Remove the flash drive. Now you can utilize this portable anti-virus on the affected computer system.
6) Double-click the anti-malware program EXE file on the flash drive.
7) Run Full System Scan to identify and clean-up up all sorts of malware.
These days, an anti-malware program can protect your computer from different forms of online threats. But how to select the right one amongst countless malware protection software that is available in the market? As you might be aware, there are numerous anti-malware companies and products for you to consider. Some of them are great, some are ok types, while some will ruin your computer themselves! You have to choose one that is reliable, practical, and has a strong reputation for its malware source protection. One of the strongly recommended software is SafeBytes AntiMalware. SafeBytes has a superb reputation for quality service, and customers appear to be very happy with it.
SafeBytes can be described as a highly effective, real-time anti-malware application that is created to assist everyday computer users in safeguarding their computers from malicious internet threats. Using its cutting-edge technology, this application will assist you to eradicate multiples types of malware like computer viruses, PUPs, trojans, worms, ransomware, adware, and browser hijackers.
There are many wonderful features you will get with this security product. Below are some typical features found in this software:
Robust, Anti-malware Protection: Built on a highly acclaimed anti-virus engine, this malware removal application has the capacity to find and get rid of various obstinate malware threats like browser hijackers, PUPs, and ransomware that other common antivirus software will miss.
Real-time Protection: Malware programs attempting to get into the system are identified and stopped as and when detected by the SafeBytes active protection shields. They are very effective in screening and eliminating different threats because they’re constantly improved with the latest updates and alerts.
Internet Security: Safebytes assigns all sites a unique safety score that helps you to get an idea of whether the webpage you’re going to visit is safe to browse or known to be a phishing site.
Light-weight: This software program is not “heavy” on the computer’s resources, so you’ll not notice any performance problems when SafeBytes is working in the background.
24/7 Online Support: Skilled technicians are at your disposal 24/7! They will promptly resolve any technical issues you might be experiencing with your security software.
SafeBytes has come up with a wonderful anti-malware solution that can help you conquer the latest malware threats and virus attacks. Once you’ve installed SafeBytes Anti-Malware, you will no longer need to bother about malware or other security worries. To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
Files:
%APPDATA%AMMYY
C:%DOCUMENTS%%%USER%%LocalTemp$inst.tmp
C:%DOCUMENTS%%%USER%%LocalTemp$insttemp_0.tmp
C:%DOCUMENTS%%%USER%%LocalTempAA_v3.exe
C:%DOCUMENTS%%%USER%%LocalTempencrypted.exe
C:Documents and Settings%USER%Application DataCasablanca
C:Documents and Settings%USER%Application DataBl 430 493 557.ADO
C:Documents and Settings%USER%Application DataDakar
C:Documents and Settings%USER%Application DataMegaloblast.a
C:Documents and Settings%USER%Application DataCrypto.dll
C:%DOCUMENTS%%%USER%%LocalTempnsh2.tmpSystem.dll
Key: HKUS-1-5-21-1801674531-413027322-2147225017-500SoftwareAmmyy
Key: HKLMSOFTWAREAmmyy
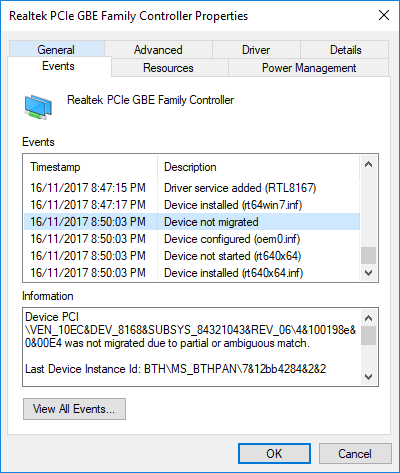
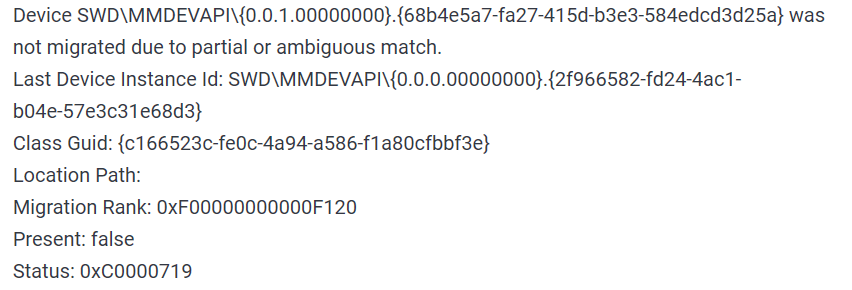 The first thing that would pop into my mind is that I have lost tons of work and that something in my hardware has gone very wrong and it is dead. Luckily that is not the case and this error means that due to Windows update drivers were not properly transferred due to some compatibility issues, maybe it was a corrupt update file, etc. Of course, the reason could be hardware malfunction as well, but if everything was working fine before the update, it is a software issue, and I must say it is a common one and fixable. Please keep reading this guide in order to fix the Device not migrated error.
The first thing that would pop into my mind is that I have lost tons of work and that something in my hardware has gone very wrong and it is dead. Luckily that is not the case and this error means that due to Windows update drivers were not properly transferred due to some compatibility issues, maybe it was a corrupt update file, etc. Of course, the reason could be hardware malfunction as well, but if everything was working fine before the update, it is a software issue, and I must say it is a common one and fixable. Please keep reading this guide in order to fix the Device not migrated error.
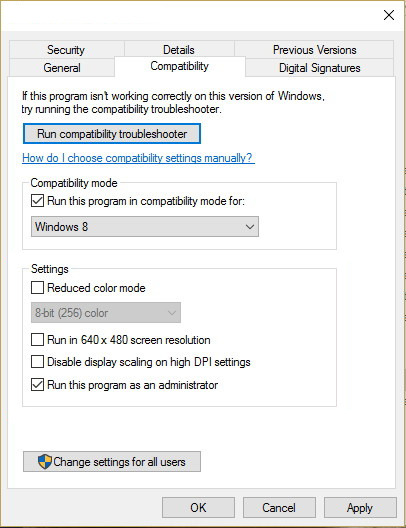 Reboot your system after this step.
Reboot your system after this step.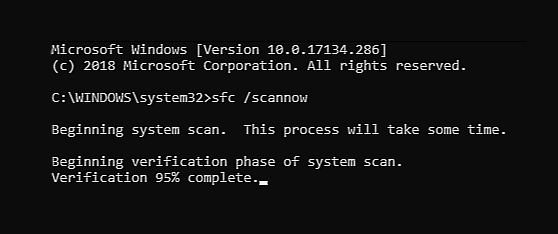


 Windows 11 comes with glass and transparency effects by default once it is installed. The transparency effect looks really good but if in any case, you do not like them, you can easily turn them off very easily
Windows 11 comes with glass and transparency effects by default once it is installed. The transparency effect looks really good but if in any case, you do not like them, you can easily turn them off very easily
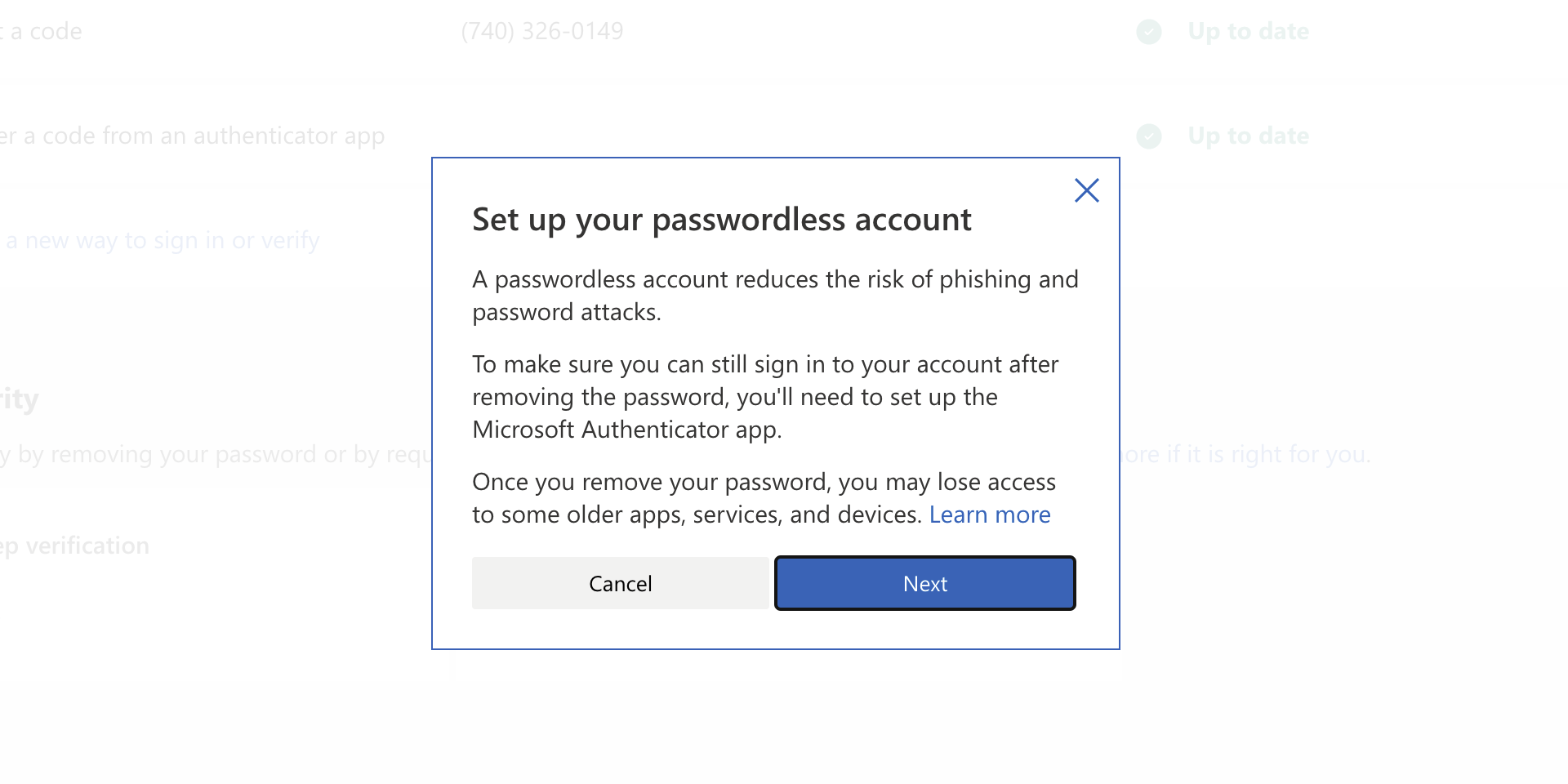 As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.

 Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process:
Same as Windows 10, Windows 11 also keeps track of date and time using an internet time server. But in a case that you need to change the date or time for any kind of reason here is a guide for that process:
