The DailyProductivityTools Toolbar is packed as a browser extension that claims to increase your productivity with access to free online tools and developed by Mindspark Inc. This extension may seem handy at first, however, while browsing the internet with it active you will experience additional ads, sponsored content, and pop-up ads throughout your browsing sessions and search results.
When installed DailyProductivityTools changed your default new tab page to Search.MyWay.com disguising as a ‘Enhanced Google Search Engine’. This extension monitors your browsing activity, visited websites and links, then uses this information to better target Ads.
DailyProductivityTools has been marked as a Potentially Unwanted Program, and is recommended for removal by many anti-virus applications.
About Browser Hijackers
Browser hijacking is a type of unwanted software, often a web browser add-on or extension, which causes modifications in the browser’s settings. Browser hijacker malware is designed for a variety of reasons. Generally, the idea is to force users visit certain sites that are aiming to increase their site visitor traffic and produce higher ad revenue. Many people believe that the browser hijacker is only a harmless website but that is incorrect. Almost every browser hijacker pose an actual threat to your on-line safety and it is important to classify them under privacy risks. What’s more, hijackers can make the entire infected system vulnerable – other harmful malware and viruses will grab these opportunities to intrude into your computer system very easily.
How one can identify a browser hijack
The following are some symptoms that suggest you have been hijacked: you find unauthorized modifications to your internet browser’s homepage; your internet browser is constantly being redirected to adult sites; the default web browser configurations have been modified and/or your default search engine is altered; you find many toolbars on the web browser; you see lots of pop-ups on your computer screen; your browser has become unstable or starts running slowly; you’re blocked to access those sites of antivirus solution providers.
So how does a PC get infected with a browser hijacker?
A browser hijacker can be installed on your computer if you check out an infected site, click on an email attachment, or download something from a file-sharing site. They could also come from add-on programs, also known as browser helper objects (BHO), browser plug-ins, or toolbars. Browser hijackers sneak into your pc along with free software downloads also that you unwittingly install alongside the original. Examples of popular browser hijackers are Fireball, Ask Toolbar, GoSave, CoolWebSearch, RocketTab and Babylon Toolbar.
Browser hijacking can lead to severe privacy problems and even identity theft, disrupt your browsing experience by taking control of outbound traffic, considerably slows down your PC by consuming lots of resources, and lead to system instability also.
Browser Hijacker Malware – Removal
Certain browser hijacking can be easily corrected by finding and removing the corresponding malware program through your control panel. But, many hijackers will be more difficult to locate or remove since it might get itself connected with certain important computer files that enable it to operate as a necessary operating system process. Novice PC users shouldn’t ever attempt for the manual form of removal, as it demands comprehensive system knowledge to do repairs on the system registry and HOSTS file.
Professionals always recommend users remove any malicious software including browser hijacker by using an automatic malware removal tool, which is better, safer, and faster than the manual removal method. Among the best tools for repairing browser hijacker malware is SafeBytes Anti-Malware. It can help you eliminate any pre-existing malware on your computer and provides you real-time monitoring and protection against new internet threats. Along with anti-virus software, a system optimizer program, similar to Total System Care, can help you repair Windows registry errors, eliminate unwanted toolbars, secure your internet privacy, and stabilize software programs installed on your computer.
Malware Blocking Access To Safebytes Site And Anti-Malware Downloads - What To Do?
Malware can cause many kinds of damage to computer systems, networks, and data. Some malware types modify internet browser settings by including a proxy server or modify the PC’s DNS settings. In such cases, you’ll be unable to visit certain or all of the websites, and therefore unable to download or install the necessary security software to eliminate the malware. If you are reading this article, chances are you’re stuck with a virus infection that is preventing you to download and install Safebytes Anti-Malware program on your PC. Although this kind of issue will be tougher to get around, there are a few actions you can take.
Install in Safe Mode
In the event the malware is set to run at Windows start-up, then booting in Safe Mode should prevent it. Since only the minimum applications and services start-up in safe mode, there are hardly any reasons for conflicts to take place. The following are the steps you should follow to remove viruses in Safemode.
1) After switching on the computer, hit the F8 key while the Windows splash screen begins to load. This would invoke the “Advanced Boot Options” menu.
2) Select Safe Mode with Networking with arrow keys and press ENTER.
3) When this mode loads, you should have the internet. Now, utilize your internet browser normally and go to https://safebytes.com/products/anti-malware/ to download Safebytes Anti-Malware.
4) Immediately after installation, run a full scan and allow the software to get rid of the threats it detects.
Switch over to an alternate internet browser
Certain viruses may target vulnerabilities of a specific browser that block the downloading process. In case you suspect that your Internet Explorer has been hijacked by a virus or otherwise compromised by online hackers, the best course of action is to switch over to a different web browser like Firefox, Chrome, or Safari to download your favorite security software – Safebytes Anti-Malware.
Run anti-malware from your USB drive
Here’s yet another solution which is using a portable USB antivirus software that can scan your system for malicious software without needing installation. Follow these steps to run the anti-malware on the infected computer.
1) On a clean computer, download and install Safebytes Anti-Malware.
2) Plug in the USB flash drive to a USB slot on the clean computer.
3) Run the setup program by double-clicking the executable file of the downloaded application, with an .exe file extension.
4) When asked, choose the location of the USB drive as the place where you would like to store the software files. Follow the instructions on the screen to finish off the installation process.
5) Now, transfer the flash drive to the infected PC.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Run Full System Scan to detect and clean-up up all kinds of malware.
SafeBytes Anti-Malware: Light-weight Malware Protection for Windows Computer
Nowadays, anti-malware software can protect your computer from different types of online threats. But how to select the best one amongst many malware protection application that’s available in the market? Perhaps you might be aware, there are many anti-malware companies and tools for you to consider. Some of them are good, some are ok types, while some will affect your PC themselves! It is important to choose a company that creates industry-best anti-malware and it has attained a reputation as reliable. On the list of highly recommended software programs is SafeBytes Anti-Malware. SafeBytes carries a superb reputation for quality service, and clients seem to be happy with it.
SafeBytes antimalware is a highly effective and user-friendly protection tool which is suitable for users of all levels of computer literacy. Using its cutting-edge technology, this software will help you eradicate several types of malware including computer viruses, PUPs, trojans, worms, adware, ransomware, and browser hijackers.
SafeBytes has got a variety of wonderful features that can help you protect your PC from malware attack and damage. Some of them are listed as below:
Antimalware Protection: This deep-cleaning antimalware software goes much deeper than most antivirus tools to clean your computer system. Its critically acclaimed virus engine finds and disables hard to remove malware that hides deep inside your personal computer.
Real-time Active Protection: SafeBytes gives round the clock protection for your computer restricting the malware attacks instantly. This software will continuously monitor your PC for suspicious activity and updates itself continuously to keep current with the latest threats.
Web Filtering: SafeBytes gives instant safety rating about the pages you’re going to check out, automatically blocking harmful sites and make sure that you’re certain of your online safety while browsing the internet.
Low CPU Usage: SafeBytes is well known for its low influence on computer resources and great detection rate of diverse threats. It runs silently and efficiently in the background so you are free to use your computer at full power all the time.
24/7 Customer Support: SafeBytes provides you with 24/7 technical support, automatic maintenance and updates for best user experience.
SafeBytes has come up with a wonderful anti-malware solution that can help you conquer the latest computer threats and virus attacks. There is no doubt that your computer system will be protected in real-time as soon as you put this software to use. So if you’re searching for the very best malware removal application out there, and if you don’t mind paying out some dollars for it, opt for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
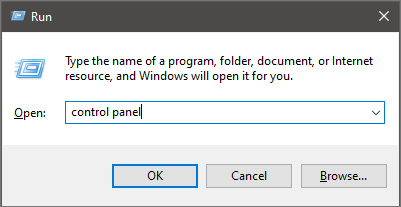
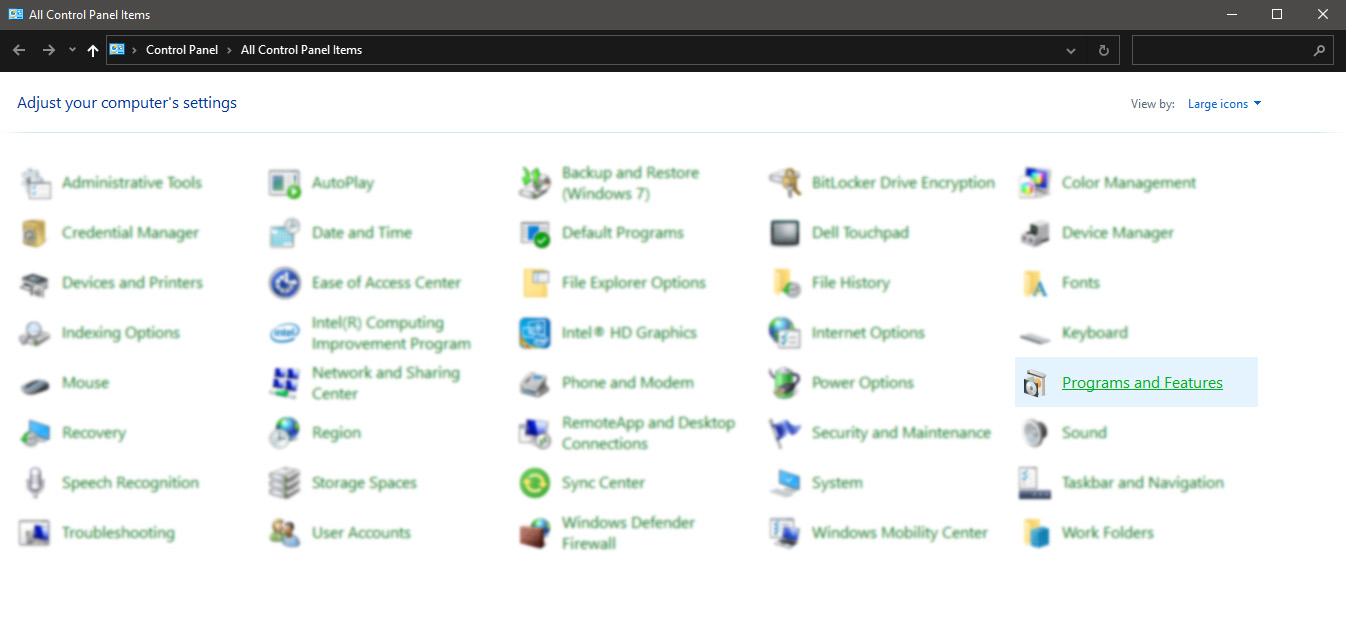
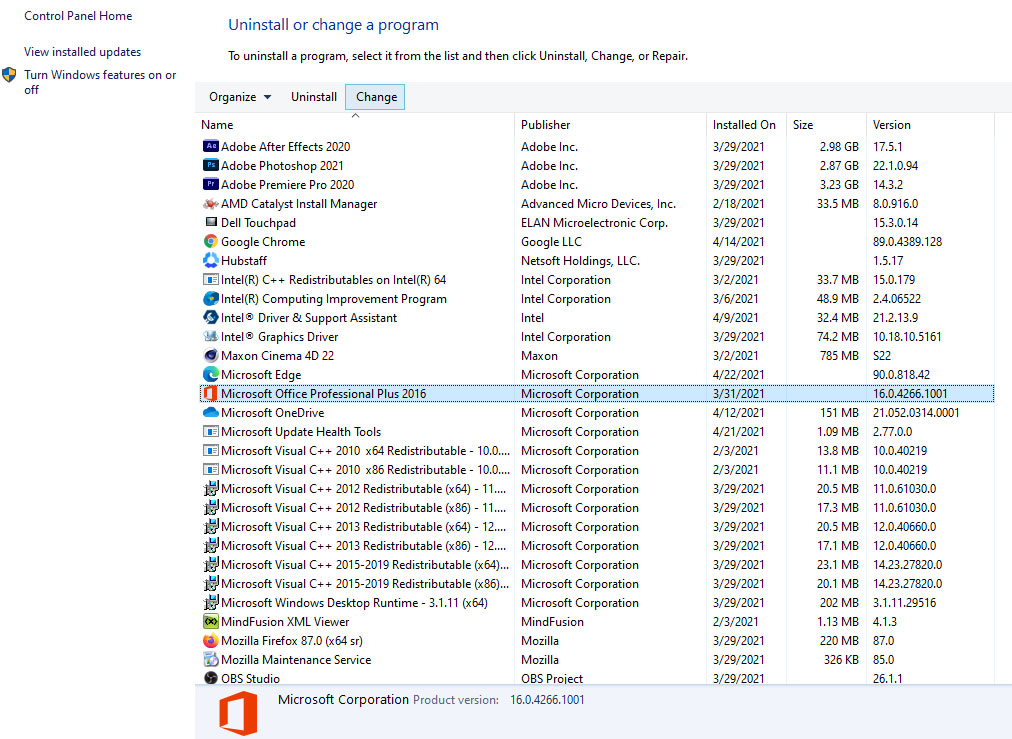
If you’d like to carry out the removal of DailyProductivityTools manually instead of using an automated tool, you may follow these simple steps: Navigate to the Windows Control Panel, click the “Add/Remove Programs” and there, choose the offending program to uninstall. In case of suspicious versions of web browser plug-ins, you can actually get rid of it through your web browser’s extension manager. You will likely also want to reset your internet browser.
If you opt to manually delete the system files and Windows registry entries, utilize the following checklist to make sure you know exactly what files to remove before carrying out any actions. But bear in mind, this can be a difficult task and only computer experts can perform it safely. Furthermore, certain malicious programs have the capability to defend against its removal. It is advisable that you carry out the removal procedure in Safe Mode.

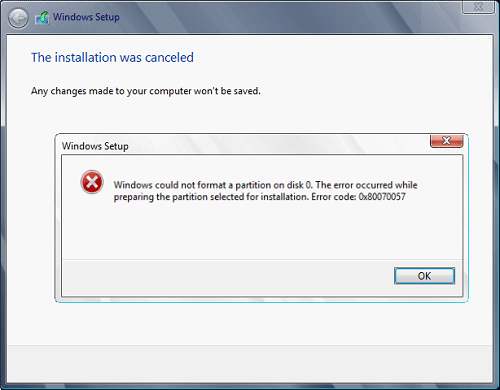 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.