Code 18 - What is it?
Code 18 is a typical Device Manager error code that occurs when the device driver is damaged. Device Manager is an important tool that allows Windows PC users to have an overall look at the connected hardware.
Furthermore, it also allows diagnostic testing. It is vital too and errors associated with the Device Manager such as error code 18 should and must be resolved quickly.
Error code 18 is usually presented in the following formats:
“The drivers for this device are not installed. (Code 18)”
Or
“Reinstall the drivers for this device.”
Solution
 Error Causes
Error Causes
Error code 18 may be triggered due to several reasons such as:
- Outdated drivers
- Corrupted drivers
- Improperly configured drivers
Error code 18 may cause a great deal of inconvenience. It may hamper your ability to use certain devices on your PC.
For example, if code 18 pops up due to a corrupted or improperly configured keyboard driver, then it may hamper your ability to use your keyboard and work on your PC.
Further Information and Manual Repair
The good news is that Device Manager error codes like error code 18 are easy to resolve. Below are some of the easiest and effective methods to repair error code 18 on your PC. Try one of these methods to repair error code 18 in no time:
Method 1 - Uninstall and Reinstall Device Drivers
One of the easiest ways to repair error code 18 and to ensure that this error doesn’t pop up on your PC again is to uninstall the problematic driver. For this, simply:
- Go to the start menu
- Type Device Manager and press enter
- Now click on the device whose driver you want to uninstall.
- Press right-click and then click on uninstall. Windows will prompt you to confirm the removal of the driver.
- Click OK to confirm and then reboot your PC to activate changes.
- Now scan for new hardware and follow the same process to reinstall the uninstalled device driver.
Method 2 - Update Drivers Automatically
Finding problematic drivers and then updating them individually can be frustrating and a time-consuming process. It can take a lot of time to perform updates and resolve the error code on your PC.
If you have projects to work on with pressing deadlines, then updating drivers on your PC separately can cause you a great deal of inconvenience and waste your precious time.
However, to avoid this situation, we advise you to set your drivers to update automatically. Automatic update installation requires only a few seconds.
And to update drivers automatically, it is recommended you download DriverFIX.
As the name suggests, this software is designed to assist programmers to upgrade device drivers automatically. In just a few clicks, you can update all your outdated drivers and repair error code 18.
DriverFIX is easy to use and an advanced program that is smoothly integrated with an intelligent programming system. This system identifies and detects all the problematic drivers on your PC and then updates each driver automatically to their latest versions.
It continues to update drivers regularly ensuring that you never come across device driver problems on your system.
Click here to download DriverFIX and repair error code 18 today!
 Sadly receiving this blue screen does not really explain which of the three cases is the correct one and causing the unwanted issue.
That being said, this article will not offer you a direct solution this time, it will be more like a guide on what to check and to do in order to remove this error, reason for this is the nature of the error itself.
If your computer is booting properly and you can enter Windows without issues the first thing you can try is going into power options and set it to high performance, if you are on a laptop set high performance both ways, when plugged and when on battery. Power performance settings can reflect on some hardware and can cause mayhem. After setting reboot the computer and see if the error repeats itself.
If the error persists go to the device manager and see if there is hardware that has any kind of warning beside it. If there is, update the driver or remove the driver of the device to see if this fixes the issue.
If all of the previous two things fail there is another thing you could try. Turn off your computer and disconnect all hardware except the most basic one. Now, this may take a long period of time but boot your computer and then repeat this process but each time add a new piece of hardware to eliminate and find which one is causing the issue. When found try to see if it is repairable through driver updates or get a new device.
Sadly receiving this blue screen does not really explain which of the three cases is the correct one and causing the unwanted issue.
That being said, this article will not offer you a direct solution this time, it will be more like a guide on what to check and to do in order to remove this error, reason for this is the nature of the error itself.
If your computer is booting properly and you can enter Windows without issues the first thing you can try is going into power options and set it to high performance, if you are on a laptop set high performance both ways, when plugged and when on battery. Power performance settings can reflect on some hardware and can cause mayhem. After setting reboot the computer and see if the error repeats itself.
If the error persists go to the device manager and see if there is hardware that has any kind of warning beside it. If there is, update the driver or remove the driver of the device to see if this fixes the issue.
If all of the previous two things fail there is another thing you could try. Turn off your computer and disconnect all hardware except the most basic one. Now, this may take a long period of time but boot your computer and then repeat this process but each time add a new piece of hardware to eliminate and find which one is causing the issue. When found try to see if it is repairable through driver updates or get a new device.  Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.
Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.


 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
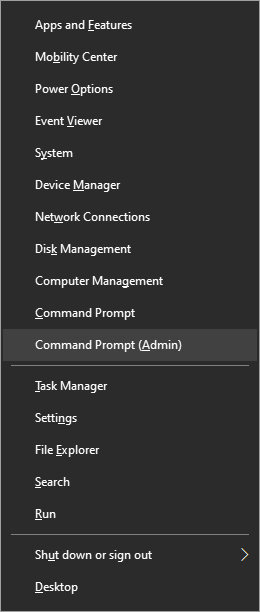 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
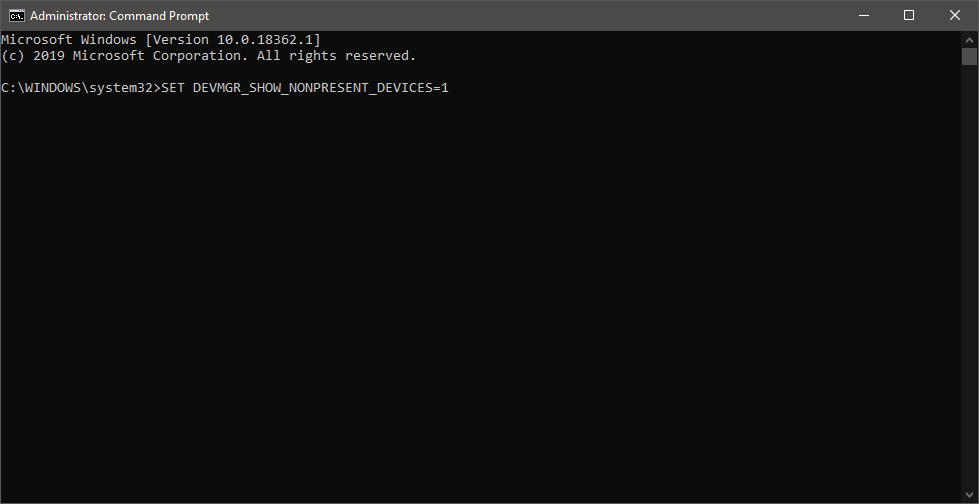 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
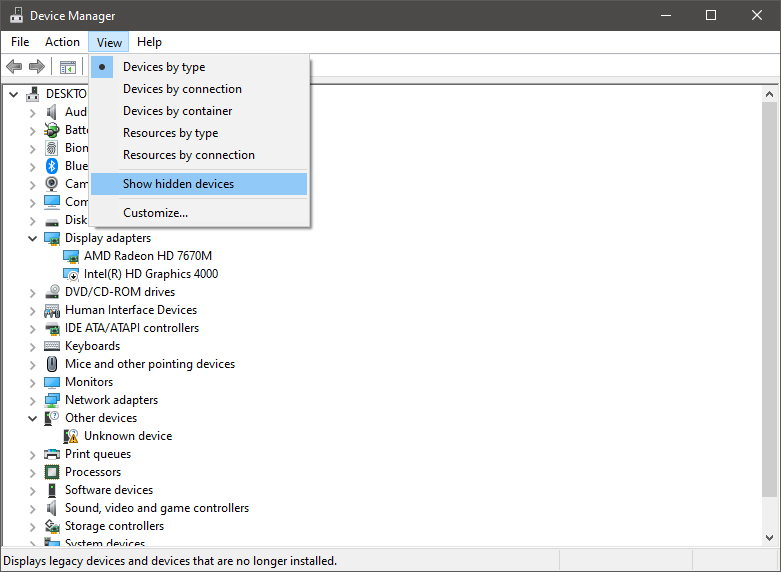
 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
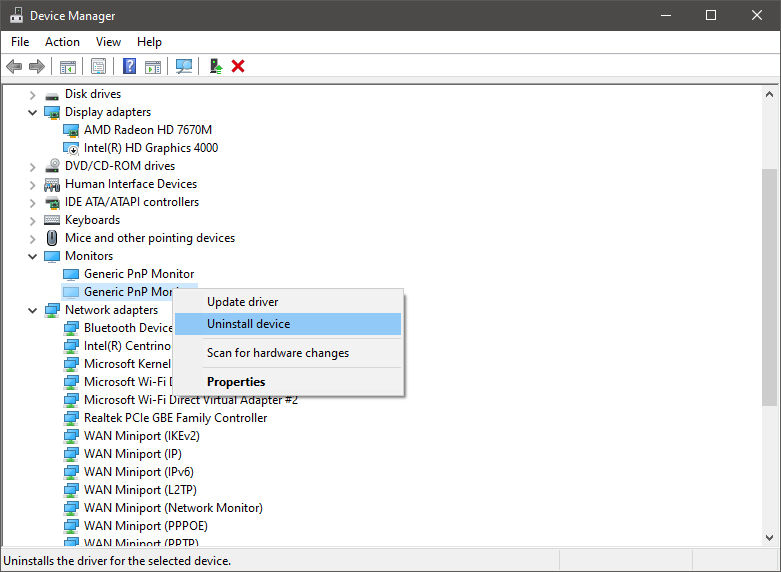 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 