Error Code 0xc004fc03 – What is it?
Error code 0xc004fc03 occurs when Windows users fail to activate their Windows operating system due to a networking problem. The error code’s common symptoms include the following:
- Inability to activate Windows 10 operating system
- Message box with error code 0xc004fc03
Solution
 Error Causes
Error Causes
Error code 0xc004fc03 in Windows 10 usually occurs due to issues related to a Windows user’s network. Your computer may be having problems connecting to the Internet or your firewall may be blocking or interrupting your device’s ability to activate Windows 10. In some cases, users may simply need to wait a day or two to reattempt to activate their system using a valid product key, as there may be an issue with the Windows activation servers. Failure to promptly fix this error code might result in other Windows 10 error messages, such as error code 0xc004f034.
Further Information and Manual Repair
To rectify the error code, Windows 10 users will need to perform manual repair procedures that fix the underlying problems causing error code 0xc004fc03. These procedures may include reconnecting to one’s network, checking your firewall settings, or activating your Windows operating system via phone. The manual repair methods are simple and do not require technical knowledge of the Windows operating system. If your attempts at manually repairing this error code fail, however, you may need to try a few other procedures.
Method One: Verify Internet Connection
To check your Internet connection, you’ll need to access the Network & Internet tab in Windows 10. Follow the instructions below to access this tab and fix Internet connectivity issues if they are preventing you from activating Windows on your machine.
- Step one: Click the Start button and select Settings
- Step two: Select Network & Internet
- Step three: Click the Status section of the Network & Internet tab
If your status shows that you are not connected to a network, you will need to fix your connection. Simply use the Network Troubleshooter to troubleshoot your connection. You will be able to activate your copy of Windows once your connectivity issues are resolved.
If, however, the problem persists and error code 0xc004fc03 occurs during the activation process, this simply means that the existence of the error code is not due to connectivity or networking problems. In such a case, move to the next manual repair method listed below and follow the exact instructions given.
Method Two: Check Firewall Settings
Windows Firewall protects your PC from hackers, worms, and other malicious programs. However, in some cases, it may result in error codes like error code 0xc004fc03. If your firewall is interfering with the Windows 10 activation, you’ll be able to rectify the problem by simply adjusting your settings. Follow the steps below to check – and adjust if necessary – your Windows Firewall settings.
- Step one: Click search bar and type firewall
- Step two: Select Windows Firewall
- Step three: Select Turn Windows Firewall on or off
In some cases, Windows users may not be able to adjust settings within the Windows Firewall tab, as your firewall settings may be controlled by a third party antivirus software. If this is the case, open the antivirus software and turn off the firewall if the software does not prevent you from making such changes to its settings.
Note, however, that you will need to readjust the settings as soon as you activate your version of Windows 10. This is due to the fact that turning off your firewall settings permanently may lead to exposure to worms and other malicious programs.
Method Three: Activate Windows by Phone
Activation of Windows via phone is another option for individuals experiencing error code 0xc004fc03. The activate by phone option in the Update & Security tab will be available once you fail to activate Windows 10. To complete this manual repair method, follow the steps below.
- Step one: Select Settings
- Step two: Click Update & security
- Step three: Select Activate by phone
- Step four: Follow the instructions provided thereafter.
This is one of the most effective ways to fix error code 0xc004fc03. If the issue persists, however, you can proceed to the last resort.
Method Four: Download an Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 8 and other related issues when they do arise, download and install a powerful automated tool.
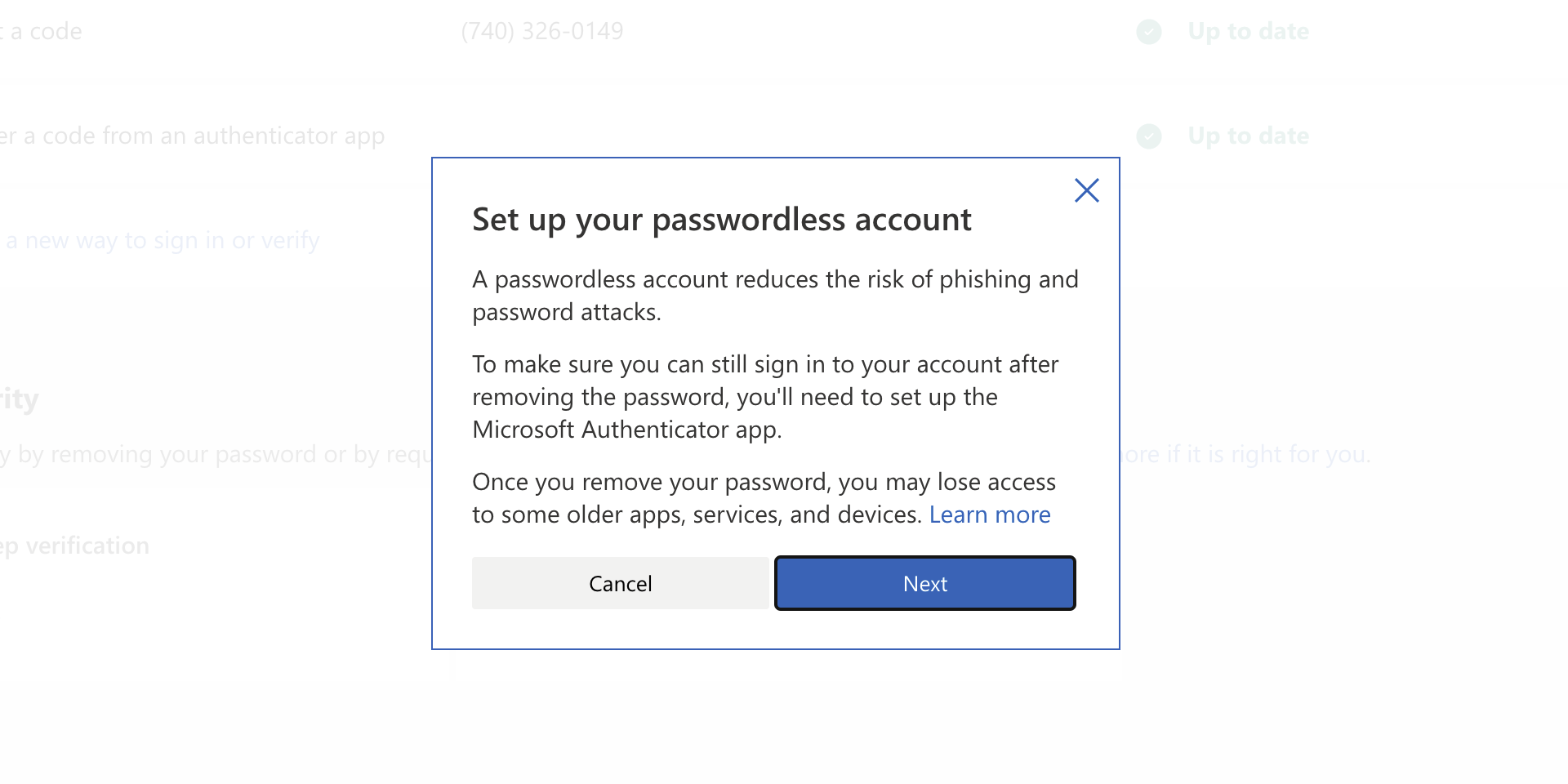 As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.
As of the time of writing this article you no longer need or are required to have a password if you plan to log in to your Microsoft account. Microsoft explored various options for account security and came to the conclusion that passwords are obsolete.
Microsoft is letting you access your account through the Microsoft Authenticator app, Windows Hello, a security key, SMS verification, or email verification code. All of these methods are way better in terms of security than passwords.


