Error Code 0x80004002 - What is it?
Error Code 0x80004002 is a Windows-based error code that affects Windows 10 and previous operating systems, including Windows XP, Vista, Windows 7, and Windows 8. In most instances, the message box that shows Error Code 0x80004002 pops up as you attempt to install new software or programs on your machine.
Common symptoms include:
- Problems running programs that once worked
- Slow response time of your computer to commands entered with the keyboard or mouse
- Trouble shutting down or starting up your machine
- Error message regarding your registry, updates, or response time.
There are a number of different solutions that you can use to attempt to resolve Error Code 0x80004002. Because there are multiple causes to the issue, some of the methods used to successfully address the problems at hand are fairly simple, while others require advanced knowledge or abilities to complete. If the methods below are not successful in the resolution of the issue or if you aren’t confident in your skills to implement these methods, contact a qualified Windows repair technician to assist you. Once this error message is not rectified, you could be exposing your computer to other error messages, including error code 0x80240020.
Solution
Error Causes
There are many different issues that can contribute to the appearance of Error Code 0x80004002. The most common causes for this particular error message include:
- Errors in registry files
- Missing system files that have accidentally been associated with other programs and deleted
- Viruses or malware that cause corruption in program or system files
- Installations that have failed to complete fully
Further Information and Manual Repair
Due to the number of causes that can contribute to Error Code 0x80004002, there are a number of methods that you can use to attempt to resolve the issues behind the error. While some of these methods are fairly easy to implement, others may require you to use programs like registry cleaners and driver installation wizards, so if you are not comfortable using these kinds of software, contact a certified Windows repair technician to assist you.
Here are the top ways that you can attempt to address Error Code 0x80004002:
Method One: Run Your Windows Registry Cleaner
Many different registry cleaning tools exist on the Internet, but not all of these are provided by trustworthy sources. Rather than trusting a file from an unknown publisher, you can use the registry cleaning program included in your Windows software package.
Run this tool to complete a scan of your files, discovering which ones may need to be repaired. In most cases, the registry cleaner itself can repair the necessary files and resolve the error.
It is always a good idea to restart your computer after you have run the registry cleaning tool to ensure that your machine can accurately assess the newly repaired files.
Method Two: Update Your Drivers and Software
In some cases, Error Code 0x80004002 arises when drivers are out of date. If you believe that this is the case, you can check on the status of your various drivers by going into the settings for your operating system and selecting the “Update Drivers” option.
You can also check your system for any necessary updates to your Windows software, which may serve to address the error code.
After you have checked and installed any necessary drivers, make sure to restart your computer to fully apply any changes that the installation process has introduced.
Method Three: Reinstall Your Windows Software
In some cases, the best way to address the missing or corrupt files that can cause Error Code 0x80004002 is to simply reinstall your copy of Windows. Always make sure to back up your files before reinstalling your software.
Method Four: Run Your Virus Scan Software
Because Error Code 0x80004002 can also be caused by malware or a virus, you can run your virus scan software to detect and resolve the problem. After doing so, run the registry repair tool to fix any affected files and restart your computer.


 Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.
Once it opens, click on Device Manager to open it,
If you have a driver device error inside Windows, you should see it immediately when entering the Device Manager, it will have a yellow exclamation mark beside it. Right-click on it and choose update driver.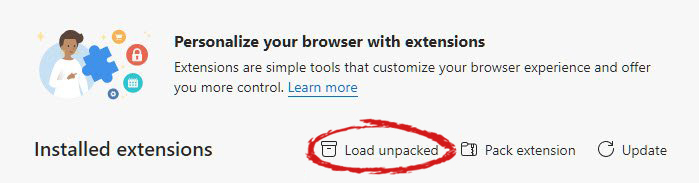
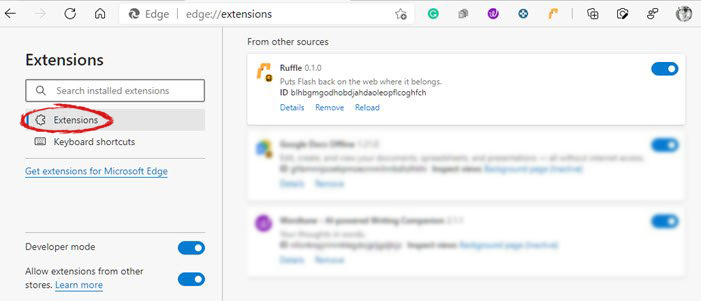
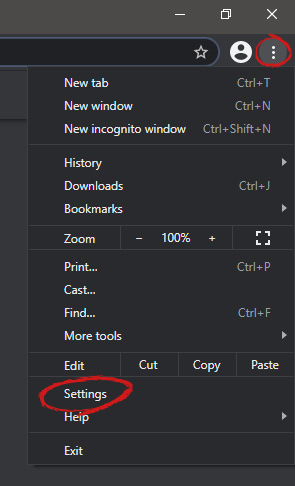 When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
When you are in settings, on the left side move toward the bottom until you run into a tab that says On Startup and click on it. On right, a new section will open, click on Open a specific page or set of pages.
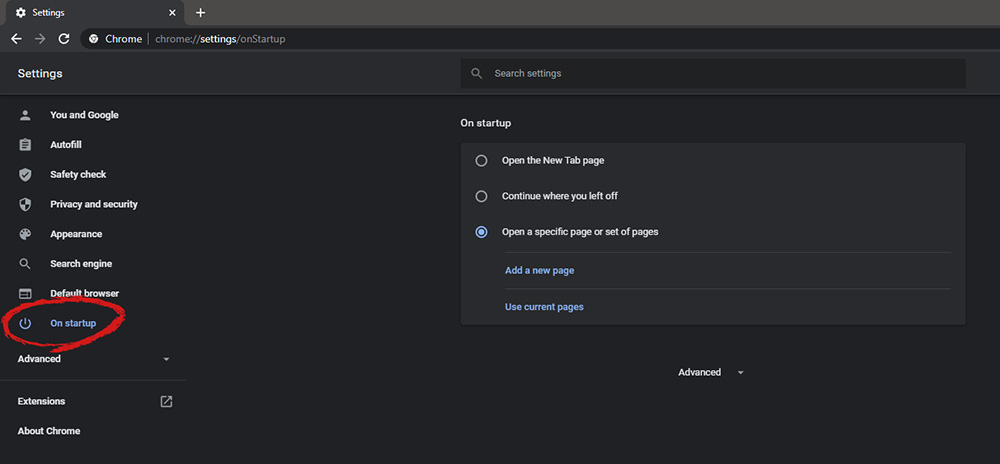 You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.
You will be presented with the option to add a new page by typing its URL or getting it from bookmarks or using a specific opened one. You can repeat this process until you have added all pages that you wish to be automatically opened once Chrome is opened for the first time.
 I going to admit right here that I am a big fan of Cooler Master PC cases, I like them and they are always one of the things that I consider when building a new PC, overall I like their ideas and quality so personal for me it was quite a surprise to see that they are one that is making a new generation gaming chair.
Now truth to be told Orb X is not your typical gaming chair as you can clearly see from the pictures. The chair itself will come in two colors: white or black and RGB lighting looks to be prominently featured throughout.
I going to admit right here that I am a big fan of Cooler Master PC cases, I like them and they are always one of the things that I consider when building a new PC, overall I like their ideas and quality so personal for me it was quite a surprise to see that they are one that is making a new generation gaming chair.
Now truth to be told Orb X is not your typical gaming chair as you can clearly see from the pictures. The chair itself will come in two colors: white or black and RGB lighting looks to be prominently featured throughout.
 The chair itself is advertised as both meant and aimed for professional and gaming crowds but I believe the gaming crowd is in general more interested in this hardware piece.
Hardware is enclosed in a fully motorized shuttle dome which aims to maximize your privacy, it supports a single 49inch display or three 27inch monitors along with surround speakers if you do not wish to use headphones.
The chair itself is advertised as both meant and aimed for professional and gaming crowds but I believe the gaming crowd is in general more interested in this hardware piece.
Hardware is enclosed in a fully motorized shuttle dome which aims to maximize your privacy, it supports a single 49inch display or three 27inch monitors along with surround speakers if you do not wish to use headphones.
 It offers an adjustable headrest, lumbar support, and footrest so you can spend some time in it and be comfortable. Controls on the chair itself allow you to raise or lower the dome for easier getting in and out of it.
Orb X also has a compartment in its backside, it folds out and has a sliding tray designed to hold your PC or console. Everything is enclosed so wiring is not the issue.
Overall Orb X seems really like the computer chair of the future, Cooler Master expects to release the Orb X by December 2021, priced around $12,000-$14,000.
It offers an adjustable headrest, lumbar support, and footrest so you can spend some time in it and be comfortable. Controls on the chair itself allow you to raise or lower the dome for easier getting in and out of it.
Orb X also has a compartment in its backside, it folds out and has a sliding tray designed to hold your PC or console. Everything is enclosed so wiring is not the issue.
Overall Orb X seems really like the computer chair of the future, Cooler Master expects to release the Orb X by December 2021, priced around $12,000-$14,000. 