Fooriza is a browser extension for Google Chrome. This extension offers users the latest trending news from the internet. These news widgets are usually sponsored content that the application displays based on your search history or visited links. While this extension is not that dangerous on its own, it usually comes bundled with other Potentially Unwanted Programs and Browser Hijackers that could pose a security risk.
When installed this extension changes your default search engine to yahoo. And while active you might see some additional ads injected into the search results.
Due to its bundled nature with other PUP-s and the potential dangers that might come with them, several anti-virus scanners have detected this extension as a Browser Hijacker and are marked for removal.
About Browser Hijackers
Browser hijackers (also called hijackware) are a kind of malware that alters internet browser configurations without the user’s knowledge or consent. These kinds of hijacks appear to be increasing at a worrying rate around the world, and it could be really nefarious and often dangerous too. They’re made to interfere with browser functions for many different purposes. In general, hijackers are programmed for the benefit of internet hackers often through revenue generation from forced advert clicks and site visits. However, it isn’t that harmless. Your internet safety is compromised and it is extremely irritating. Additionally, hijackers can make the whole infected system vulnerable – other destructive malware and viruses would seize these opportunities to get into your PC effortlessly.
Indications of browser hijack
Signs that your web browser is hi-jacked include:
1. your browser’s home page is suddenly different
2. you find yourself constantly directed to a different web page than the one you actually intended
3. default web engine is changed
4. you’re getting new toolbars you haven’t seen before
5. you may find numerous pop-up ads on your computer screen
6. your web browser gets sluggish, buggy, and crashes frequently
7. you are blocked to access those sites of anti-malware solution providers.
Exactly how browser hijacker finds its way to your computer
Browser hijackers infect computer systems in numerous ways, including via a file-share, a drive-by download, or an infected e-mail attachment. They are usually included with toolbars, BHO, add-ons, plug-ins, or browser extensions. Also, some freeware and shareware can put the hijacker in your PC through “bundling”. Some of the most well-known hijackers are Fooriza, Babylon Toolbar, Conduit Search, OneWebSearch, Sweet Page, and CoolWebSearch.
Browser hijacking could lead to serious privacy issues and even identity theft, disrupt your web browsing experience by taking control over outbound traffic, drastically slows down your personal computer by consuming lots of resources, and cause system instability also.
Browser Hijacker Malware – Removal
Some hijackers can be simply removed by deleting the freeware they came with or by deleting any add-ons you have recently added to your system. At times, it can be a challenging task to discover and remove the malicious program since the associated file will be running as part of the operating system process. You should think of carrying out manual repairs only if you happen to be a tech-savvy person since there are potential risks associated with messing around with the computer registry and HOSTS file.
Installing and running antivirus software on the affected system can automatically erase browser hijackers and other malicious applications. SafeBytes Anti-Malware detects all kinds of hijackers – such as Fooriza – and eliminates every trace quickly and efficiently.
What To Do If You Cannot Install Safebytes Anti-Malware?
Every malware is bad and the degree of the damage will vary greatly with regards to the type of infection. Some malware is designed to interfere with or prevent things that you wish to do on your personal computer. It may not allow you to download anything from the internet or prevent you from accessing some or all of the websites, in particular the antivirus websites. If you are reading this, you probably have infected by malware that prevents you from installing a computer security application like Safebytes Anti-Malware. There are a few actions you can take to get around this problem.
Get rid of malware in Safe Mode
If the malware is set to load at Windows start-up, then booting in Safe Mode should avoid it. Just minimal required programs and services are loaded when you boot your PC in Safe Mode. The following are the steps you should follow to eliminate malware in Safemode.
1) At power on, press the F8 key while the Windows splash screen starts to load. This will bring up the Advanced Boot Options menu.
2) Choose Safe Mode with Networking with arrow keys and press Enter.
3) When you are into this mode, you should have access to the internet again. Now, obtain the malware removal program you need by using the internet browser. To install the software, follow the guidelines within the installation wizard.
4) Once the software is installed, allow the diagnostic scan to run to eliminate viruses and other malware automatically.
Use an alternate web browser to download the anti-malware application
Some malware might target vulnerabilities of a specific web browser that block the downloading process. The ideal way to overcome this problem is to select an internet browser that is known for its security measures. Firefox contains built-in Malware and Phishing Protection to help keep you secure online.
Run anti-malware from your USB drive
Another option is to make a portable anti-malware program on your USB stick. Do these simple actions to clean up your affected PC using a portable antivirus.
1) On a clean PC, install Safebytes Anti-Malware.
2) Put the USB drive into the clean PC.
3) Double-click the executable file to run the installation wizard.
4) When asked, choose the location of the USB drive as the place in which you would like to put the software files. Follow the instructions on the computer screen to finish off the installation process.
5) Disconnect the USB drive. You may now use this portable anti-virus on the affected computer.
6) Double-click the antivirus program EXE file on the pen drive.
7) Press the “Scan” button to run a full system scan and remove malware automatically.
How SafeBytes Anti-Malware Keep your Machine Virus Free
Nowadays, an anti-malware program can protect your PC from different types of internet threats. But how to decide on the best one amongst plenty of malware protection application that’s available out there? As you might be aware, there are many anti-malware companies and tools for you to consider. A few of them do a good job in removing malware threats while many will ruin your computer by themselves. When searching for an antimalware program, purchase one that gives dependable, efficient, and complete protection against all known viruses and malware. Among few good applications, SafeBytes Anti-Malware is the highly recommended program for the security-conscious individual.
SafeBytes anti-malware is a very effective and easy-to-use protection tool that is designed for end-users of all levels of IT literacy. With its cutting-edge technology, this application will assist you to get rid of several types of malware including computer viruses, trojans, PUPs, worms, adware, ransomware, and browser hijackers.
SafeBytes anti-malware takes computer protection to a whole new level with its enhanced features. These are some of the great features included in the software.
Active Protection: SafeBytes provides real-time active checking and protection against all known computer viruses and malware. This utility will constantly monitor your PC for any suspicious activity and updates itself regularly to keep abreast of the latest threats.
Robust, Anti-malware Protection: Using its advanced and sophisticated algorithm, this malware elimination tool can detect and remove the malware threats hiding in the computer system effectively.
Extremely Speed Scanning: This application has got one of the fastest and most efficient virus scanning engines in the industry. The scans are highly accurate and take a short amount of time to complete.
Web Filtering: SafeBytes checks the links present on a web page for possible threats and alerts you whether the website is safe to explore or not, through its unique safety rating system.
Light-weight: SafeBytes gives total protection from online threats at a fraction of the CPU load because of its enhanced detection engine and algorithms.
24/7 Assistance: You may get high levels of support round the clock if you’re using their paid software.
All in all, SafeBytes Anti-Malware is a solid program as it has lots of features and can identify and remove any potential threats. You now may understand that this particular software does more than just scan and delete threats on your computer. So if you’re trying to find a comprehensive antivirus program that’s still simple enough to use, SafeBytes Anti-Malware is just what you need!
Technical Details and Manual Removal (Advanced Users)
If you want to perform the removal of Fooriza manually rather than employing an automated software tool, you may follow these steps: Go to the Windows Control Panel, click the “Add or Remove Programs” and there, choose the offending program to remove. In case of suspicious versions of browser plug-ins, you can easily remove them through your web browser’s extension manager. It is also advised to factory reset your browser to its default condition to fix corrupt settings.
Finally, examine your hard disk for all of the following and clean your computer registry manually to remove leftover application entries following uninstalls. Please note that only experienced computer users should try to manually edit the system files mainly because deleting any single vital registry entry leads to a major problem or even a computer crash. Moreover, some malware keeps replicating which makes it tough to remove. Doing this malware-removal process in Safe Mode is recommended.
Files:
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\nnamllomkmngnaklpijbbaokmonnkcne
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\nnamllomkmngnaklpijbbaokmonnkcne

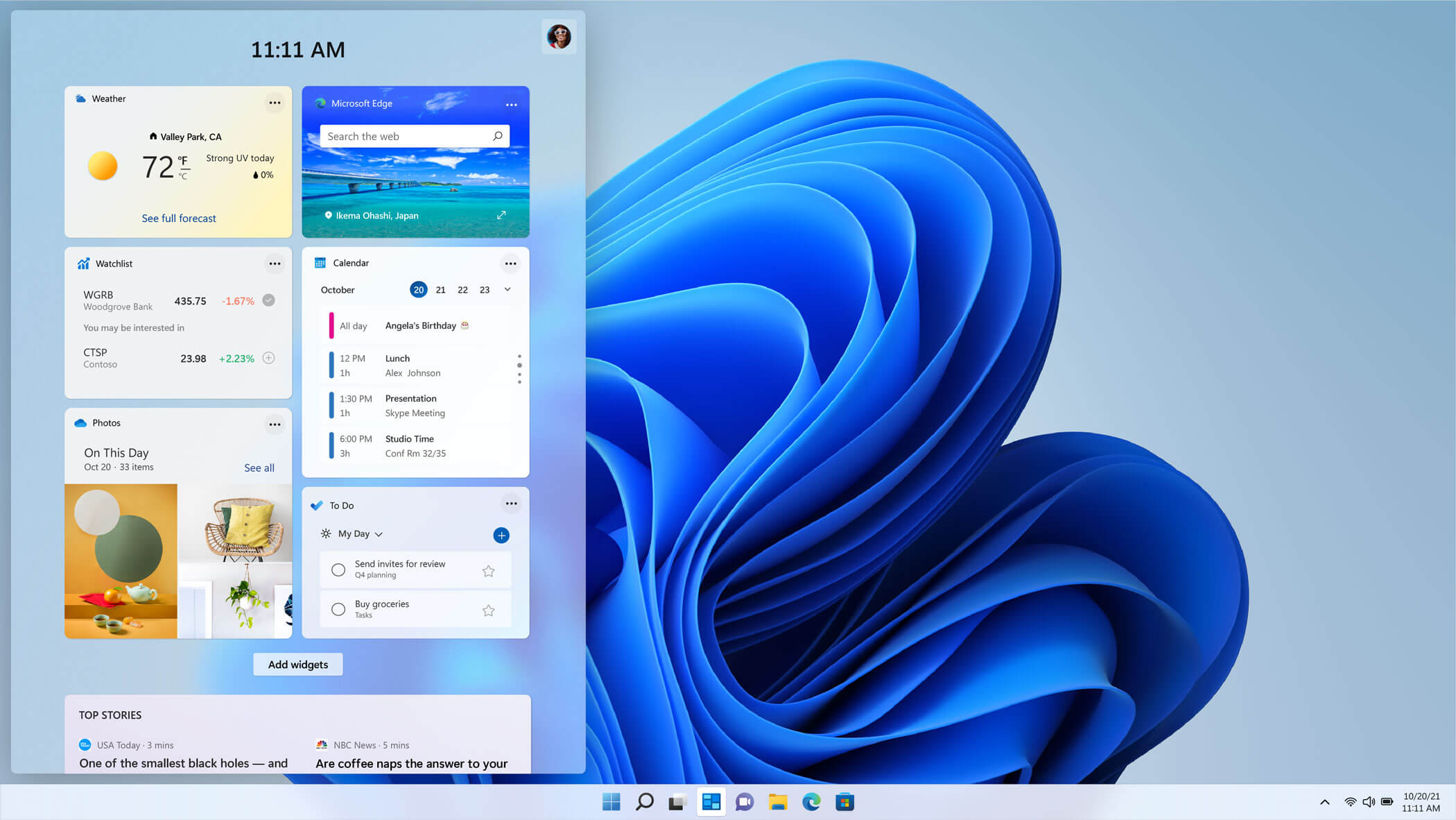 The new widget's menu inside Windows 11 is generally met with a positive attitude but there are still users which prefer not to have it. Luckily for them, Microsoft included a very easy way to turn the widgets menu on or off. Follow this easy guide to see how.
Right-click on the widget button in the taskbar and click on Hide from Taskbar and that’s it
Alternatively, you can also turn it off via the setting app.
Go to the settings app and navigate to Personalization > Taskbar > Taskbar Items and flipping the switch beside Widgets to Off.
Please note that both methods will only hide the button to toggle widgets menu, at the current state there is no really a way to actually turn it off, only hide it and make it not available to bring it up.
The new widget's menu inside Windows 11 is generally met with a positive attitude but there are still users which prefer not to have it. Luckily for them, Microsoft included a very easy way to turn the widgets menu on or off. Follow this easy guide to see how.
Right-click on the widget button in the taskbar and click on Hide from Taskbar and that’s it
Alternatively, you can also turn it off via the setting app.
Go to the settings app and navigate to Personalization > Taskbar > Taskbar Items and flipping the switch beside Widgets to Off.
Please note that both methods will only hide the button to toggle widgets menu, at the current state there is no really a way to actually turn it off, only hide it and make it not available to bring it up.