Error Code 0x801901F7 – What is it?
Error code 0x801901F7, also known as “The Server Stumbled” error because it shows a message saying “The Server Stumbled. We all have bad days” is associated with Windows Store. Server Stumbled Error 0x801901F7 is an error related to the MS server. The error occurs due to damaged registry files, malware, virus, and corrupted data. You should fix this error to prevent a system crash or a BSOD error. There are some things you can do to fix it. These are not so complex. So, anyone can try these methods to fix error 0x801901F7.
Common Symptoms for error 0x801901F7:
- Problems with Windows startup
- System becomes very slow or the system freezes
- Blue screen of death appears
- Windows fails to start some process due to Stop error code 0x801901f7
Solution
 Error Causes
Error Causes
- This error is generally caused by corrupt registry files.
- Virus infection can cause this problem.
- Outdated driver, missing .DLL files may also cause this error.
- Microsoft server overload may cause this problem as well.
- Incorrect configuration may cause this problem.
Further Information and Manual Repair
To fix error 0x801901f7, there are four methods listed below. Some might work for you and some might not. Please try all of them to fix this error.
Method 1:
Basic method to fix error code 0x801901F7: Resetting Windows Store Cache
Most of the time clearing or resetting the cache helps. It doesn't always work, but you should try this first before moving on to some advanced methods which are mentioned below.
To reset the Windows Store cache please follow the simple steps below
- Open RUN by searching or pressing "Windows Key + R"
- Type "wsreset.exe" and press Enter or click on OK.
- Windows Store will open automatically along with a command prompt.
- This will reset Windows Store and you might see it loading as it should.
This method might work but if it fails to solve Error 0x801901F7 then follow the method below.
Method 2:
Advanced method of fixing error code 0x801901F7: Deleting Windows Store database file.
By using this method, you will be deleting the database file for Windows Store. This file is located on your C drive or the drive where you installed your Operating System. Follow the steps below.
- Navigate to C:WindowsSoftwareDistributionDataStoreDataStore.edb.
- Delete DataStore.edb file from there.
- Now Open Windows Store and see if you still get error code 0x801901F7.
The Datastore.edb file that you deleted will be automatically created once you perform Step 3 which is launching Windows Store.
If you still cannot get this error away then Close Windows Store and Reboot your PC then Launch Windows Store Again.
Method 3:
Modifying Windows update properties:
Perform the steps below only if the above-mentioned methods fail. You will be tweaking a few things in the Windows update to see if it helps.
- Open Task Manager by right-clicking on Taskbar, then click on Task Manager.
- Go to Services Tab. Click on Open Services at the very bottom of the Window.
- Now a new window will pop up. Scroll down & find "Windows Update" from the list.
- Double click on Windows update to open up its Properties.
- Now from the Startup Type drop-down list, select Automatic. Click on Apply, Start, and then Ok.
Now you need to perform just one more step. Reset Windows Store again (Refer to method 1 for Steps). This should fix your Windows Store error that shows The Server Stumbled with 0x801901F7 Error Code.
Method 4:
If the error is due to a problem with a driver, then follow the method below to uninstall the current driver:
- Open the Run command and type “sysdm.cpl” in the text box.
- Click Enter.
- Open the Hardware tab on the system properties dialog box.
- Then press on Device Manager.
- Double press on Device type and then press on the hardware device that is reporting error code 0x801901F7.
- Go to the Driver tab and press on Uninstall button to uninstall the device driver completely.
- Now, install the new driver on your computer.
- Restart your computer.
- Run virus scan of your PC
- Try using a different USB port.
If you do not possess the technical expertise required to accomplish this yourself or do not feel comfortable doing so, download and install a
powerful automated tool to get the job done.


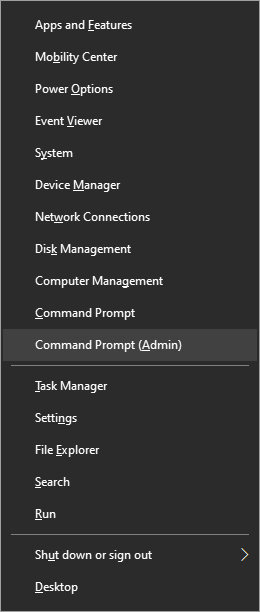
 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
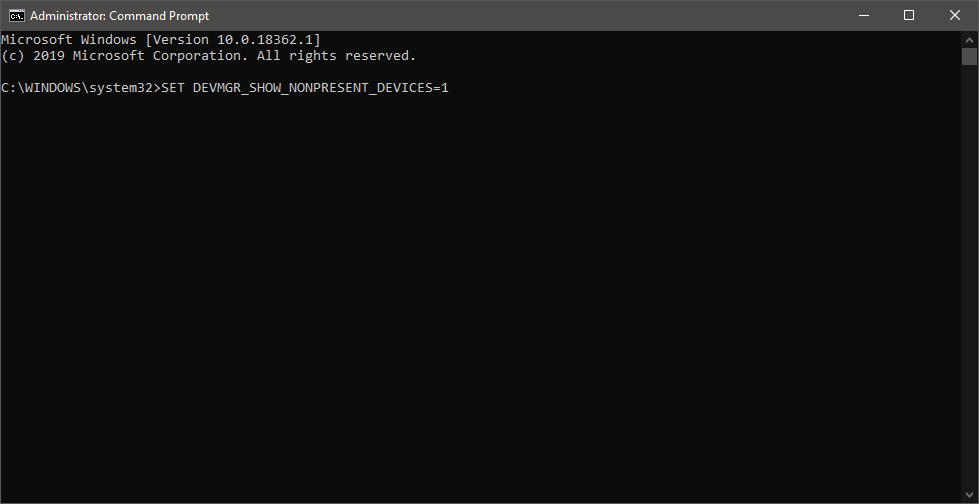 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
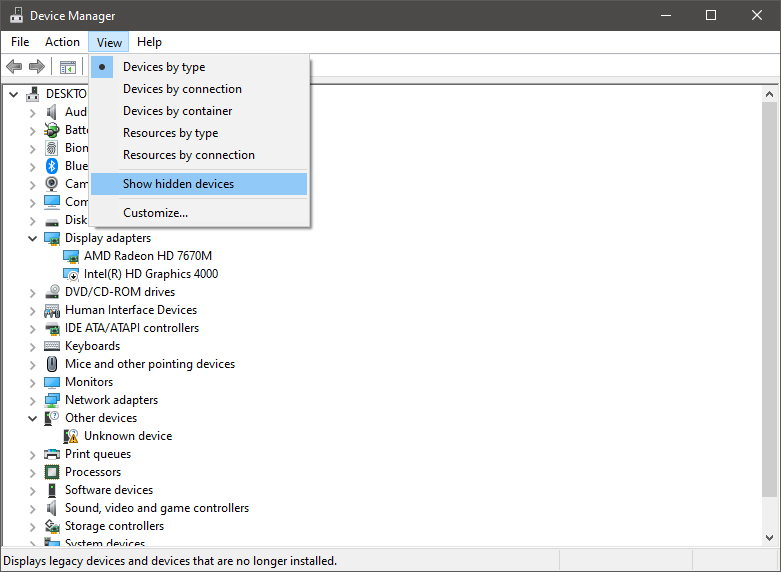
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
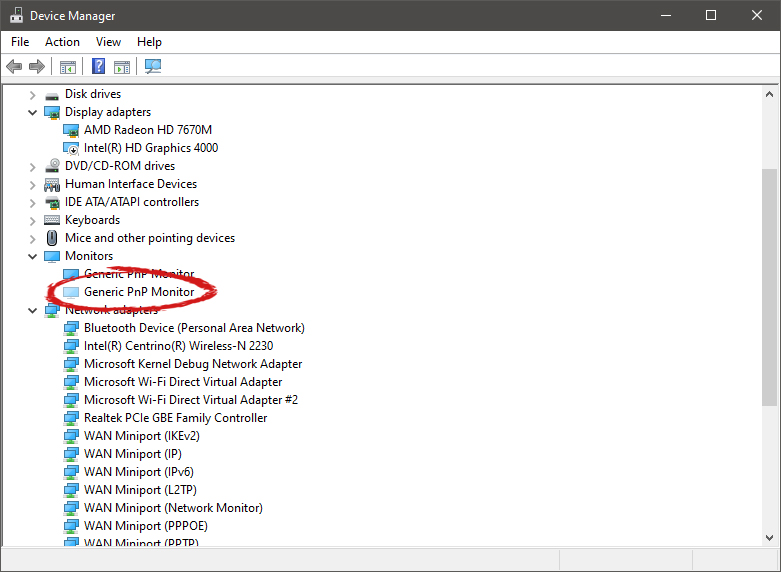 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
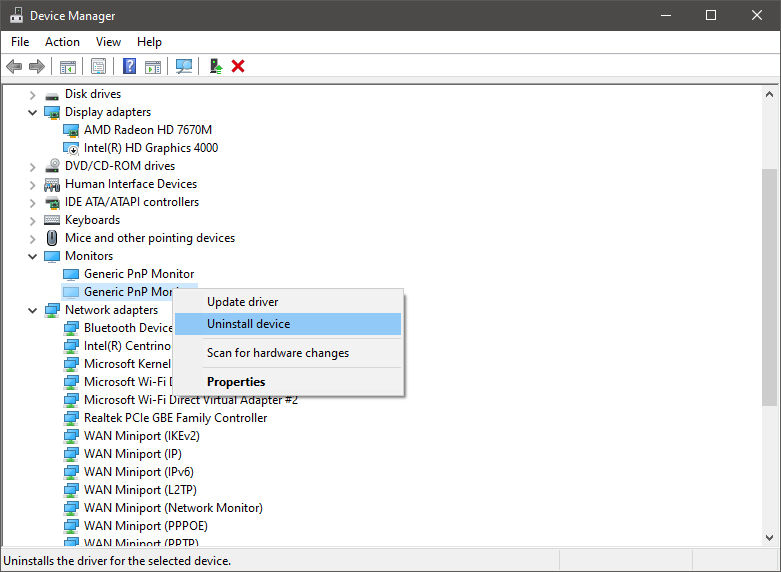 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.  The Clear Linux Project creates an operating system and software stack that offers highly optimized performance, security, versatility, and manageability.
Clearly optimized for Intel CPUs and based on GNOME it will offer you incredible speeds if you are on Intel CPU.
The big news, though, is that Clear Linux sports the shiny new Gnome 40. This is a fresher Gnome than you'll find even on Ubuntu's more experimental 21.04 release. The only big names that let you test drive Gnome 40 are Fedora and Arch Linux.
The Clear Linux Project creates an operating system and software stack that offers highly optimized performance, security, versatility, and manageability.
Clearly optimized for Intel CPUs and based on GNOME it will offer you incredible speeds if you are on Intel CPU.
The big news, though, is that Clear Linux sports the shiny new Gnome 40. This is a fresher Gnome than you'll find even on Ubuntu's more experimental 21.04 release. The only big names that let you test drive Gnome 40 are Fedora and Arch Linux.

 Speaking of old players of old Diablo 2, they can transfer their old characters into remaster and continue playing them within this new great HD environment. There are some steps and requirements but we are here to help and transferred characters will bring full stash, inventory, and equipped items with them.
Speaking of old players of old Diablo 2, they can transfer their old characters into remaster and continue playing them within this new great HD environment. There are some steps and requirements but we are here to help and transferred characters will bring full stash, inventory, and equipped items with them.

