What is Windows 10X
Windows 10X is a new version of Windows that has been built from the ground up for new PCs and will begin shipping on hardware in 2021. It's built on top of a new modern version of Windows called 'Windows Core OS' that guts legacy components and features in favor of contemporary user experiences and enhanced security. This means everything from the Windows Shell to the underlying OS has been rebuilt with modern technologies.
As a result, Windows 10X does not support legacy Win32 applications at launch. Windows 10X PCs in 2021 will be able to run Microsoft Edge, UWP, and web apps. Legacy Win32 application support will arrive at a later date, however. When it does, Win32 applications will run in a secure container by default, meaning those legacy applications cannot affect system performance and battery life when closed. Windows 10X is a much more secure and stable OS as a result of this, as there's no opportunity for legacy apps to cause bitrot.
Windows 10X features a new shell of the user interface that has been built with modern technologies. It's an adaptive user experience that can adjust depending on the "posture" of your device. For example, with a foldable PC, the user might want to use it in several different ways; as a laptop, or tablet, or in tent mode for movies. Because of this, the user interface must adapt to provide the best experience no matter which way your device is being used.
This also means that legacy shell elements, such as the Control Panel, File Explorer, and error dialogs and icons are gone on Windows 10X. As Microsoft has rebuilt the entire shell, it doesn't include any of the legacy things that make Windows 10 so inconsistent when it comes to UI. The Windows Shell on Windows 10X should be much more consistent. At launch, Windows 10X will only be available on traditional clamshell PCs aimed primarily at the education and enterprise markets. The platform will eventually ship on the new devices from factors such as foldable PCs, but that won't be happening in 2021.
Start menu
Microsoft is redesigning the Start menu experience on Windows 10X with a focus on productivity. It features a system-wide search bar along the top that can also search the web and a grid of installed apps below that in place of live tiles. It also has a "recent activities" area that dynamically updates with things the user might want to jump straight into, such as recent Office documents and visited websites. The apps list can be customized, with the ability for users to rearrange which apps show up in the first few rows.
Taskbar
Windows 10X also has a new adaptive Taskbar that features a centered design. The Start and Task View buttons appear in the center, with running and pinned apps appearing between the two. When you open an app, the Start and Task View buttons gently spread apart, giving the Taskbar a much more fluid appearance. There are some new animations; the Start and Task View buttons have their own animations when clicked on, and there's a subtle bounce to app icons when you minimize running apps to the Taskbar.
In addition to the new design, there are also up to three different Taskbar sizes: Small, medium, and large. Large is great for tablets, while medium and small mimic the usual sizes we already have today on Windows 10. On tablets, users can now swipe up anywhere on the Taskbar to access the Start menu, making it easier for touch users to access their apps list. You no longer have to hit the specific Start button to access your Start menu.
Action center
In addition to the new Start and Taskbar experiences, there's also a new Action Center to compliment them. This new Action Center puts more emphasis on quick actions, with the ability to jump into specific quick actions for further control without leaving the Action Center at all. It's also designed in such a way that mimics a control center, with notifications housed above it in a separate box. This new Action Center includes things like volume controls, power options, and battery percentage. There's also a new music control UI that appears in the Action Center when music is playing from a supported app.
State separation feature
Unlike Windows 10, Windows 10X features something called "state separation" which is how the OS lays itself out on a drive. Windows 10 today installs everything into a single partition, which means the user can access system files, as can apps and potential attackers. On Windows 10X, everything goes into its own read-only partition. So OS files are locked away, as are app files, as are drivers, and the registry. The only thing the user and applications can access is the user partition.
This means that malware or viruses can't get in and affect the system because those programs are only able to operate in a single partition, and that assumes they're able to get outside of the app container system Microsoft has built. All apps on Windows 10X run in a container and need explicit permissions to access things that are outside that container. This is already how UWP apps work on Windows 10, and Microsoft will be extending that to Win32 apps on Windows 10X when support for Win32 apps arrives.
Launch date and info
Windows 10X will launch this spring first for commercial markets. Commercial markets include education and enterprise industries looking for sub-$600 PCs for students in the classroom or first-line workers. Windows 10X won't be launching on consumer PCs in 2021, meaning you won't find it on a flagship Dell or HP device. It's also only for clamshell PCs, with foldable, tablets, and other form factor support coming in 2022 and beyond.
Windows 10X will launch without an in-box Mail and Calendar app. It's been removed from the first version of Windows 10X because the platform is aimed at commercial markets that will likely use Outlook Web or stream Outlook via Windows Virtual Desktop. Users can opt to reinstall the Mail and Calendar apps from the Microsoft Store if they wish.
Windows 10X for mainstream markets won't happen until 2022 when Win32 app support among other features comes to the OS as part of the Windows 10 "Nickel" release scheduled for the first half of 2022.
Because Windows 10X is a new operating system, it will not be released as an update for existing Windows 10 PCs. Users won't be able to install Windows 10X on a device that didn't come with Windows 10X, to begin with. There won't be any official ISO media and you won't be able to buy Windows 10X on its own to install on your existing device. It's for new PCs only.
If you would like to
read more helpful
articles and tips about various software and hardware visit
errortools.com daily.


 In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
In Windows 11 by default inside the Start menu, there is recommended section that contains recently opened folders, documents, and files. If you do not wish this section and do not want recent items in your Start menu there is an easy way to turn it off.
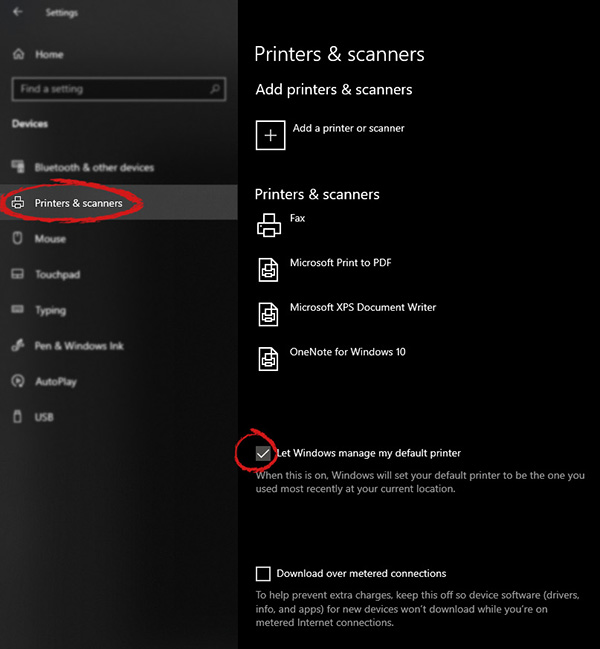
 Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
Once the device window opens, click once on printers and scanners, and on the right window go to the bottom and uncheck Let windows manage my default printer.
 Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
Unchecking that box will let Windows know that we do not wish anymore for him to set our default printers according to their use. Once the checkbox is clear go up to your printer list and click on the printer you wish to use as the default one. I will choose Microsoft Print to PDF as my default printer and click on it. Once the printer is clicked option menu will appear.
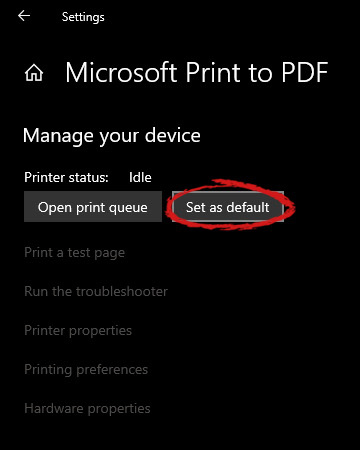
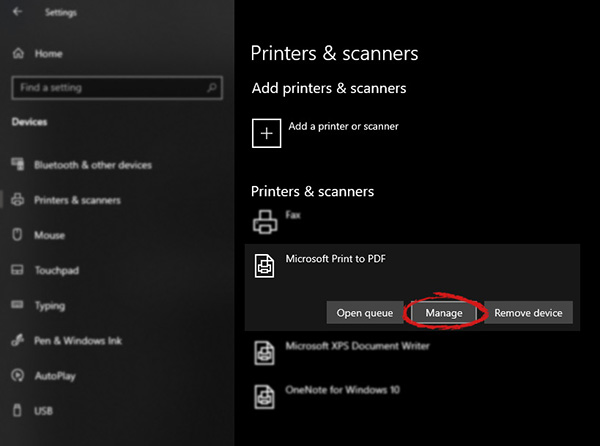 When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.
When the option menu appears under the printer name, click on Manage which will take you to the printer management screen. When you are on the manage screen, click on the Set as default button, and you are done.