When you have to connect to a drive that’s on a different computer or on external storage, that’s where the mapped network drives come in. Mapped network drives make accessing files a lot easier. However, there are times when it won’t work for some reason.
Windows will notify you about the unavailability of mapped network drives in several ways. For one, Windows might display a red X on the network drives or it could be that its status will be unavailable when you try to use it from the Command Prompt or via a notification.
It is recommended that you run a few scripts when you log in to your PC as it may so happen that the network drive takes more than usual to connect. Before you start troubleshooting the problem using the given options below, keep in mind that some workouts might only work under certain scenarios. You might need some network access at logon or you might need access to the Group Policy settings. So you need to choose what you prefer more.
You can try the given workarounds below if the mapped network drives are not showing or connecting or working on your Windows 10 computer. These workarounds use scripts to make sure that you are connected to them as soon as you start to use your PC.
As mentioned, before you can troubleshoot, you need to create scripts first. There are two scripts here namely MapDrives.ps1 which is executed by the second script named MapDrives.cmd and is done at a regular and non-elevated Command Prompt. Follow the steps below to get started.
- You have to create a script file named “MapDrives.cmd” first and then save it on a place where the files are safe. To do that, open a text editor like Notepad and then copy and paste the following script:
PowerShell -Command "Set-ExecutionPolicy -Scope CurrentUser Unrestricted" >> "%TEMP%StartupLog.txt" 2>&1
PowerShell -File "%SystemDrive%ScriptsMapDrives.ps1" >> "%TEMP%StartupLog.txt" 2>&1
- After that, save the file and name it “MapDrives.cmd”.
- Next, create a script file named “MapDrives.ps1” and then copy and paste the following content. Just make sure to save both scripts in the same folder.
$i=3
while($True){
$error.clear()
$MappedDrives = Get-SmbMapping |where -property Status -Value Unavailable -EQ | select LocalPath,RemotePath
foreach( $MappedDrive in $MappedDrives)
{
try {
New-SmbMapping -LocalPath $MappedDrive.LocalPath -RemotePath $MappedDrive.RemotePath -Persistent $True
} catch {
Write-Host "There was an error mapping $MappedDrive.RemotePath to $MappedDrive.LocalPath"
}
}
$i = $i - 1
if($error.Count -eq 0 -Or $i -eq 0) {break}
Start-Sleep -Seconds 30
}
Note: Now that you’ve created the script files, it’s time for you to proceed to the options given below.
Option 1 – Try creating a startup item
Note that this option only works on devices that have network access at login. So if it’s not there, the script will fail to reconnect the network drivers automatically. To create a startup item, here’s what you have to do:
- Open the Startup folder located at %ProgramData%MicrosoftWindowsStart MenuProgramsStartUp.
- From there, copy and paste the MapDrives.cmd.
- After that, open the Scripts folder located at %SystemDrive%Scripts copy-paste MapDrives.ps1 and then copy and paste MapDrives.ps1 in there.
Note: After you complete the steps above, a log file named “StartupLog.txt” will be created in the %TEMP% folder. Now all that’s left for you to do is to log out of your computer and then log back in. This will ensure that the mapped drives are open.
Option 2 – Create a scheduled task
It is possible to create a scheduled task that runs as soon as you log in to your computer. To create a scheduled task, follow the steps below.
- You have to copy the MapDrives.ps1 script file to the scripts folder of Windows located at %SystemDrive%Scripts.
- After that, open the Task Scheduler and select Action > Create Task.
- Next, type a name and description of the task in the General tab.
- Then click on the Change User or Group button and select a local user group and click OK.
- Now check the box labeled “Run with highest privileges” and switch to the Triggers tab.
- From there, create a new trigger with the “At Logon” option in the Begin the task drop-down menu and then click OK.
- After that, switch to the Actions tab and create a new action then choose to Start a program.
- Next, type “Powershell.exe” in the Program/Script field, and in the Add arguments (optional) field, type the following:
-windowsstyle hidden -command .MapDrives.ps1 >> %TEMP%StartupLog.txt 2>&1
- And in the Start in the (optional) field, type “%SystemDrive%Scripts” as the location of the script file.
- Now under the Conditions tab, select the “Start only if the following network connection is available” option and then select Any connection and click OK.
- Restart your computer or log off from your account and then log back in so that the task will be executed.
Option 3 – Use the Group Policy settings
You need this option if the mapped network drives are defined via Group Policy settings. You have to update the action of the drive maps to Replace. As a result, it will delete the existing mapped drive and create the mapping on each logon again. However, any settings on the mapped drive that are changed from the Group Policy settings will be gone on each logon. So if the changes don’t work, you need to run the gpupdate command together with the /force parameter in order to refresh the Group Policy setting quickly.


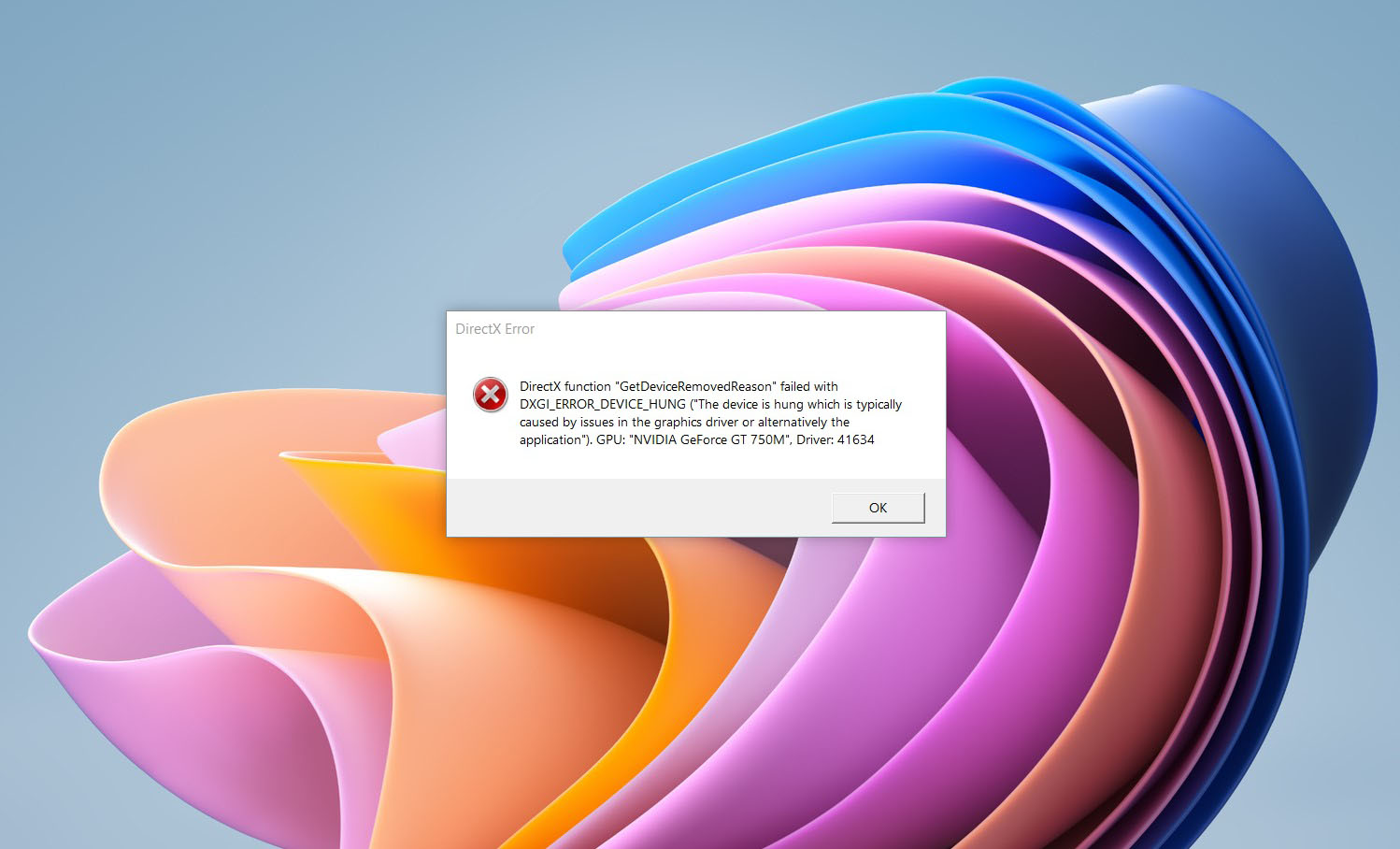 If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.

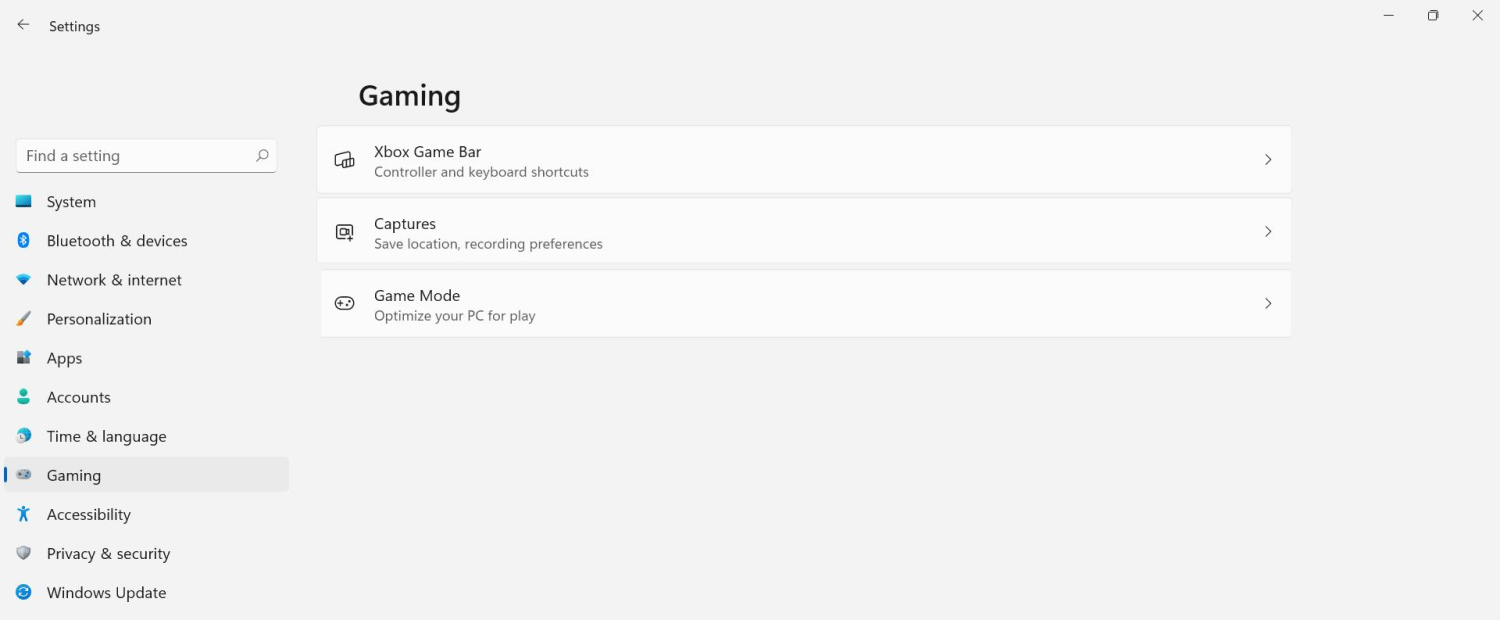 The game mode is active at all times and usually, everything works great but in some instances, it can sadly cause some performance issues. If you are one of these unlucky people where game mode is not working as supposed to do, don’t panic, we have a quick guide for you on how to turn it off.
The game mode is active at all times and usually, everything works great but in some instances, it can sadly cause some performance issues. If you are one of these unlucky people where game mode is not working as supposed to do, don’t panic, we have a quick guide for you on how to turn it off.
