WeatherBlink is an extension for google chrome, Mozilla, and internet explorer. It allows users to check out the weather anywhere in the world at any time. This might seem like a convenient feature, however, this toolbar also displays unwanted ads, hijacks your browser home page, collects personal data about your web surfing habits, visits, and clicks.
From the author: Access local weather forecasts, weather radar, allergy, and pollen reports, and worldwide weather news – all in one convenient spot!
This extension configures your New Tab page to WeatherBlink™ to provide these features.
Be prepared with instant weather forecasts. Access FREE and accurate weather forecasts with one click!
About Browser Hijackers
Browser hijack is a very common type of online fraud where your web browser settings are modified to make it do things you do not intend. Browser hijackers can do more than simply modifying home pages. It redirects you to the sponsored internet sites and inserts ads on the internet browser that helps its creator generate ad revenue. A lot of people assume that these kinds of websites are legitimate and harmless but that is not true. Nearly every browser hijacker poses an actual threat to your online safety and it is necessary to classify them under privacy dangers. In a worst-case scenario, your internet browser could be hi-jacked to open up your computer to a host of additional computer infections.
Indications of browser hijack
Below are some symptoms that indicate you’ve been hijacked:
1. the browser’s home page is changed
2. bookmark and the new tab are also modified
3. default online search engine is modified
4. you see unwanted new toolbars added
5. you notice a lot of pop-ups on your computer screen
6. web pages load very slowly and often incomplete
7. you’ve disallowed entry to particular web pages, for example, the website of an antimalware software firm like SafeBytes.
So how exactly does a browser hijacker infect a computer?
A browser hijacker could be installed on your PC when you go to an infected website, click an email attachment, or download something from a file-sharing website. They also come from add-on applications, also referred to as browser helper objects (BHO), browser extensions, or toolbars. Sometimes you may have mistakenly accepted a browser hijacker as part of a software program bundle (usually freeware or shareware). Typical examples of browser hijackers include CoolWebSearch, Conduit, RocketTab, OneWebSearch, Coupon Server, Searchult.com, Snap.do, and Delta Search.
Tips on how to remove browser hijackers
Certain browser hijacking can be easily stopped by discovering and eliminating the corresponding malware application from your control panel. However, certain hijackers are more difficult to find or eliminate as they might get themselves associated with certain crucial system files that enable it to work as a necessary operating-system process. You should think about carrying out manual repairs only if you’re a tech-savvy person because there are possible risks associated with fiddling around with the system registry and HOSTS file.
How One Can Eliminate Malware that is Blocking Websites or Preventing Downloads
Malware could potentially cause several different types of damage to PCs, networks, and data. Certain malware goes to great lengths to prevent you from downloading or installing anything on your PC, especially anti-malware applications. If you’re reading this, you probably have got infected by a virus that prevents you from downloading security software like Safebytes Anti-Malware. There are a few fixes you could try to get around with this issue.
Start Windows in Safe Mode
Safe Mode is actually a unique, basic version of Windows where just essential services are loaded to counteract malware as well as other problematic programs from loading. In the event the malware is blocking access to the internet and affecting your PC, launching it in Safe Mode enables you to download anti-virus and run a diagnostic scan while limiting possible damage. To start the computer into Safe Mode, hit the “F8” key on your keyboard right before the Windows logo screen comes up; Or after normal Windows boot up, run MSCONFIG, check Safe Boot under Boot tab, and click Apply. Once you restart into Safe Mode with Networking, you may download, install, as well as update anti-malware software from there. At this point, you could run the anti-malware scan to eliminate computer viruses and malware without any interference from another application.
Switch over to an alternate browser
Some malware may target vulnerabilities of a specific browser that block the downloading process. The most effective solution to avoid this problem is to pick a browser that is renowned for its security features. Firefox has built-in Phishing and Malware Protection to help keep you secure online.
Install antivirus on a thumb drive
To effectively remove the malware, you have to approach the problem of running an anti-malware software program on the affected computer from a different angle. Adopt these measures to run the anti-virus on the affected computer.
1) Download Safebytes Anti-Malware or Windows Defender Offline onto a virus-free computer system.
2) Plug the USB drive into the clean PC.
3) Double-click the Setup icon of the anti-malware program to run the Installation Wizard.
4) When asked, choose the location of the USB drive as the place in which you would like to store the software files. Follow activation instructions.
5) Unplug the flash drive. You may now utilize this portable anti-virus on the infected computer.
6) Double-click the Safebytes Anti-malware icon on the flash drive to run the program.
7) Press the “Scan Now” button to begin the virus scan.
SafeBytes Anti-Malware: Lightweight Malware Protection for Windows Computer
Do you want to install the best anti-malware software for your computer system? There are plenty of applications available in the market which comes in paid and free versions for Microsoft Windows computers. A few of them are good, some are ok types, while some will damage your computer themselves! You need to be careful not to select the wrong application, particularly if you purchase a paid application. On the list of recommended software programs is SafeBytes AntiMalware. SafeBytes has a very good track record of top-quality service, and customers seem to be very happy with it.
SafeBytes can be described as a powerful, real-time anti-spyware application that is made to assist the common computer end user in safeguarding their PC from malicious internet threats. Using its cutting-edge technology, this application can assist you to get rid of multiples types of malware which include computer viruses, PUPs, trojans, worms, ransomware, adware, and browser hijackers.
SafeBytes has a variety of features that can help you protect your PC from malware attacks and damage. Below are a few of the great ones:
Antimalware Protection: With a critically acclaimed anti-malware engine, SafeBytes gives multi-layered protection which is intended to find and eliminate viruses and malware that are concealed deep in your computer’s operating system.
Real-time Threat Response: SafeBytes provides round-the-clock protection for your PC restricting malware intrusions in real-time. It’ll regularly monitor your laptop or computer for hacker activity and also gives users sophisticated firewall protection.
Quick Multi-threaded Scanning: SafeBytes’s high-speed malware scanning engine lessens scan times and extends the life of the battery. At the same time, it’ll effectively detect and get rid of infected computer files or any internet threat.
Internet Security: Safebytes allots all sites a unique safety score that helps you to get an idea of whether the website you’re just about to visit is safe to browse or known to be a phishing site.
Low CPU/Memory Usage: SafeBytes is well known for its minimal influence on computer resources and great detection rate of numerous threats. It works quietly and efficiently in the background so you are free to utilize your computer or laptop at full power all the time.
24/7 Customer Support: You will get 24/7 technical support to promptly resolve any problem with your security tool.
Technical Details and Manual Removal (Advanced Users)
To remove WeatherBlink manually, go to the Add or Remove programs list in the Control Panel and select the program you want to get rid of. For internet browser plug-ins, go to your browser’s Addon/Extension manager and select the plug-in you want to remove or disable. You will probably also want to reset your internet browser.
Finally, examine your hard drive for all of the following and clean your registry manually to remove leftover application entries after uninstallation. Please remember that only experienced users should try to manually edit the registry because incorrect file deletion results in a major problem or perhaps a PC crash. Furthermore, certain malware is capable of replicating or preventing deletion.
Carrying out this malware-removal process in Safe Mode is recommended.


 Microsoft wants to escalate the situation from Australia to the EU, what a surprise.
Hello all and welcome to another news article, this time we are focusing on Microsoft pushing the EU to accept law proposition from Australia.
For all of you who are not familiar with the given situation let me quickly explain. The feud began when the Australian government proposed a new law that targeted Facebook and Google specifically. The government said that it believed that both of the tech giants were using content from news outlets without paying.
Have you ever seen the little news snippets that Google or Facebook sometimes show its users to keep them up to date? These are lifted directly from news websites, and the Australian government claimed that this practice meant that people didn't bother visiting the news website. This then staved news websites of revenue.
As such, the government put forward a new law that would mean Google and Facebook would have to pay the source website for every time they displayed a news snippet. Facebook responded by removing its Australian news coverage in light of the law.
Google, however, put up a fight. It argued that its snippets encouraged people to click on it to read more, thus driving more traffic to the news website. It also said that such a law would be too expensive to maintain in the long run.
As such, Google threatened to remove itself from Australia if the law passed. This was likely a scare tactic, as 95 percent of Australian web users use Google; however, it actually opened the door for its rival, Microsoft.
Microsoft saw how it could push its own search engine BING to replace google. It of course went and reached the Australian government to assure them that BING is more than capable to fulfill its needs and fully abide by the proposed law.
Now Microsoft knows that if this law passes it could see a similar situation happening in Europe and it is pushing it. US News reported on how Microsoft plans to encourage EU countries to adopt this new law too. The company has teamed up with the European Publishers Council and News Media Europe to make the following statement:
Publishers might not have the economic strength to negotiate fair and balanced agreements with these gatekeeper tech companies, who might otherwise threaten to walk away from negotiations or exit markets entirely
Microsoft wants to escalate the situation from Australia to the EU, what a surprise.
Hello all and welcome to another news article, this time we are focusing on Microsoft pushing the EU to accept law proposition from Australia.
For all of you who are not familiar with the given situation let me quickly explain. The feud began when the Australian government proposed a new law that targeted Facebook and Google specifically. The government said that it believed that both of the tech giants were using content from news outlets without paying.
Have you ever seen the little news snippets that Google or Facebook sometimes show its users to keep them up to date? These are lifted directly from news websites, and the Australian government claimed that this practice meant that people didn't bother visiting the news website. This then staved news websites of revenue.
As such, the government put forward a new law that would mean Google and Facebook would have to pay the source website for every time they displayed a news snippet. Facebook responded by removing its Australian news coverage in light of the law.
Google, however, put up a fight. It argued that its snippets encouraged people to click on it to read more, thus driving more traffic to the news website. It also said that such a law would be too expensive to maintain in the long run.
As such, Google threatened to remove itself from Australia if the law passed. This was likely a scare tactic, as 95 percent of Australian web users use Google; however, it actually opened the door for its rival, Microsoft.
Microsoft saw how it could push its own search engine BING to replace google. It of course went and reached the Australian government to assure them that BING is more than capable to fulfill its needs and fully abide by the proposed law.
Now Microsoft knows that if this law passes it could see a similar situation happening in Europe and it is pushing it. US News reported on how Microsoft plans to encourage EU countries to adopt this new law too. The company has teamed up with the European Publishers Council and News Media Europe to make the following statement:
Publishers might not have the economic strength to negotiate fair and balanced agreements with these gatekeeper tech companies, who might otherwise threaten to walk away from negotiations or exit markets entirely 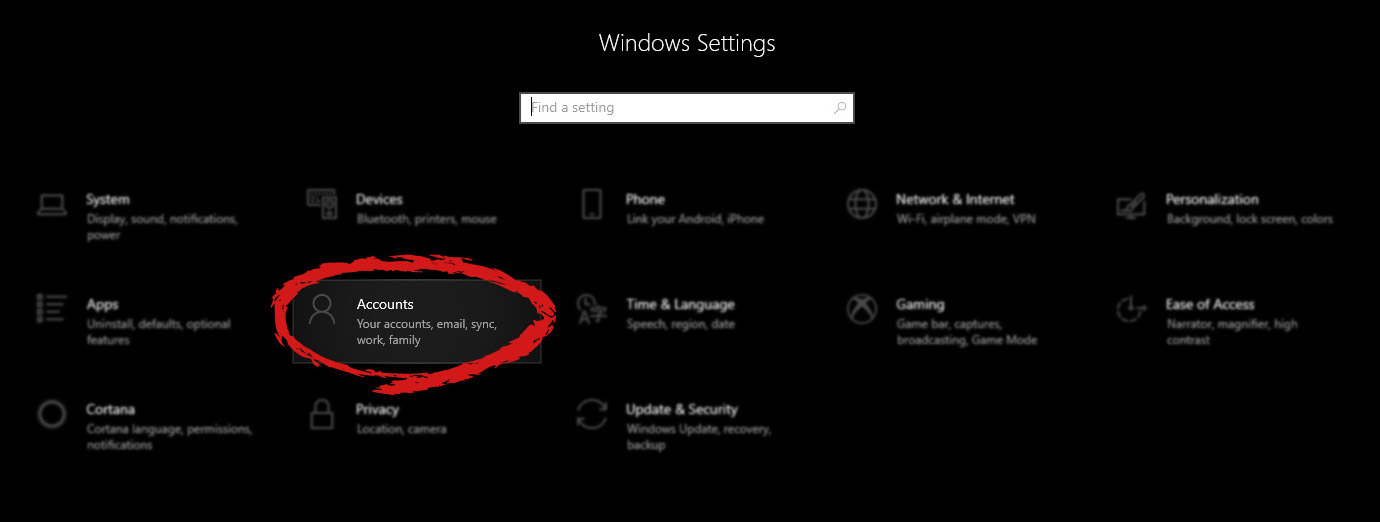 Windows will then go to the accounts settings page. Within that page, click on the Family & other users to open the setting for the chosen section on right. On the right settings, screen navigate to the lower section and click once with the left button on add someone else to this PC
Windows will then go to the accounts settings page. Within that page, click on the Family & other users to open the setting for the chosen section on right. On the right settings, screen navigate to the lower section and click once with the left button on add someone else to this PC
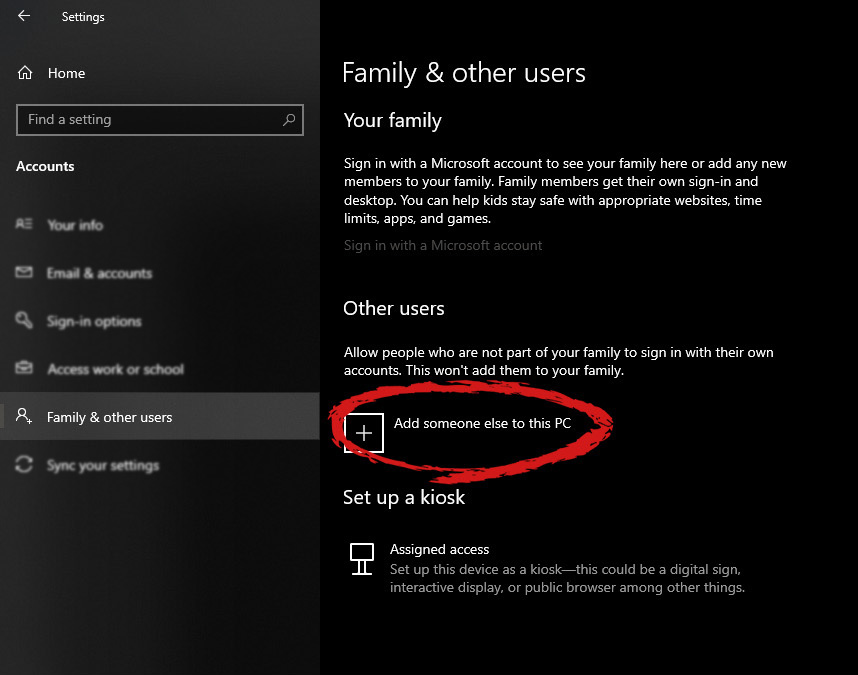 When add someone else to this PC is clicked, pop up window will appear which will ask you to provide the persons email address and later on the password of his/her Microsoft account, after the required information is provided you are done, a new user has been added and he can use his Microsoft credentials on the login screen to use this computer.
When add someone else to this PC is clicked, pop up window will appear which will ask you to provide the persons email address and later on the password of his/her Microsoft account, after the required information is provided you are done, a new user has been added and he can use his Microsoft credentials on the login screen to use this computer.
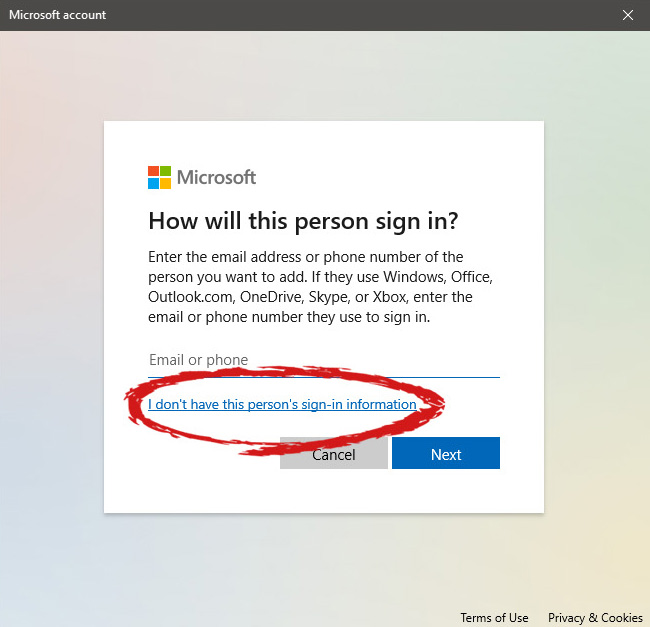 This will open yet another pop-up giving you the option to create a Microsoft account for this person, to use a phone number instead of a Microsoft account, or to create a new email address for the user. Any of these options will create a new user for this computer with provided credentials but there is the last option at bottom of the pop-up which will allow you to create a local user only without a Microsoft account. This user will be able to use this computer, will not be able to transfer his document through various devices like he/she would if using a valid Microsoft account but it could use the computer and personalize it fully to his/her liking.
This will open yet another pop-up giving you the option to create a Microsoft account for this person, to use a phone number instead of a Microsoft account, or to create a new email address for the user. Any of these options will create a new user for this computer with provided credentials but there is the last option at bottom of the pop-up which will allow you to create a local user only without a Microsoft account. This user will be able to use this computer, will not be able to transfer his document through various devices like he/she would if using a valid Microsoft account but it could use the computer and personalize it fully to his/her liking.
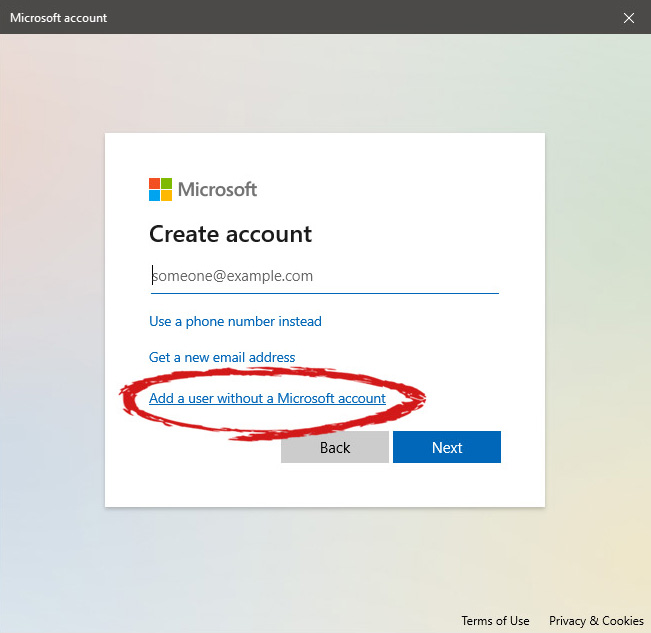 Once the link is clicked, you will be presented with a floating window requiring you to input needed information in order for the account to be created. You will need to provide username, password, and answers to 3 security questions.
Once the link is clicked, you will be presented with a floating window requiring you to input needed information in order for the account to be created. You will need to provide username, password, and answers to 3 security questions.
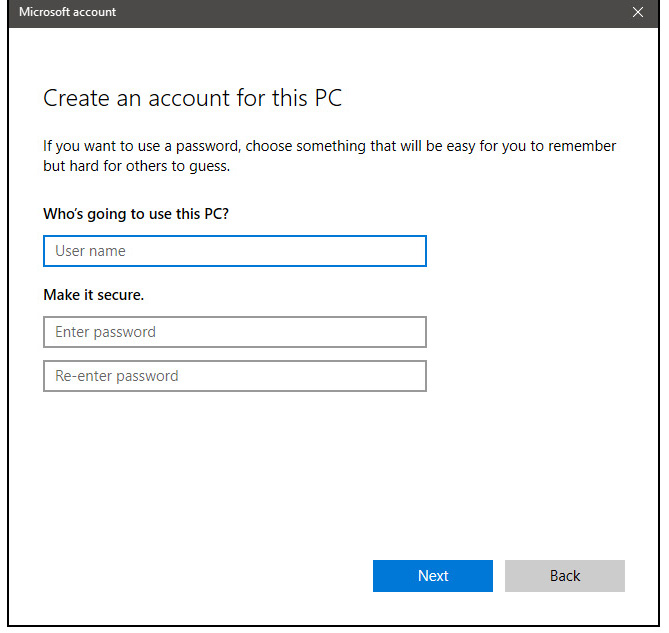 Once all information has been provided, click on next and your new non-Microsoft local user has been created. Now when you click on Family & other users you will see that Windows has added a new user with the provided name to this computer. If you wish, you can add another user in the same manner, following the previous steps. Microsoft Windows does not have a limit for how many users can be on one computer so feel free to create as many as you like.
Once all information has been provided, click on next and your new non-Microsoft local user has been created. Now when you click on Family & other users you will see that Windows has added a new user with the provided name to this computer. If you wish, you can add another user in the same manner, following the previous steps. Microsoft Windows does not have a limit for how many users can be on one computer so feel free to create as many as you like.
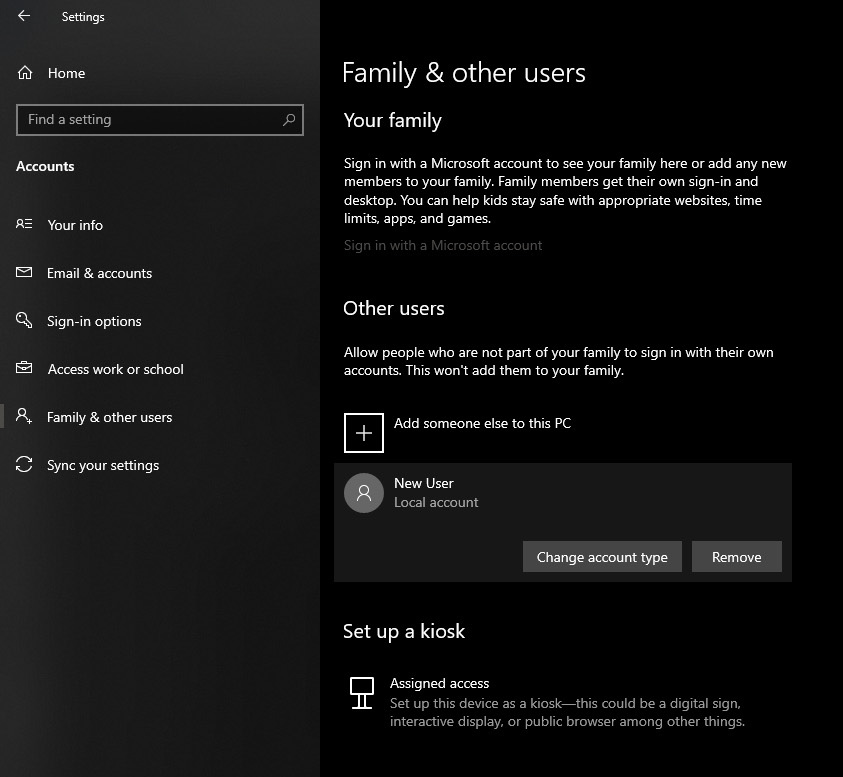 Click on Change account type.
Click on Change account type.
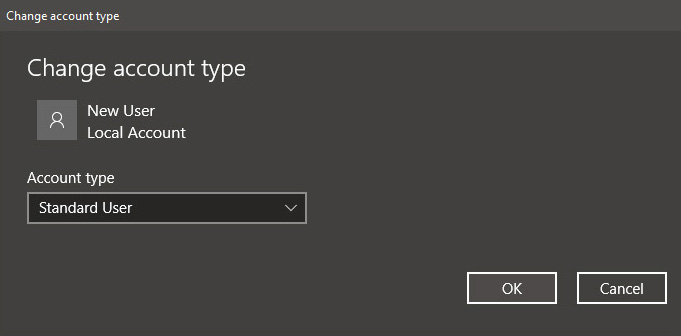 Under account type, you will have the option to promote this user to an administrator if you wish or you can leave it as a standard user.
Under account type, you will have the option to promote this user to an administrator if you wish or you can leave it as a standard user. 