The Get Coupons Fast Toolbar is a Browser Extension for Google Chrome developed by Mindspark Inc. This extension allows quick access to the most popular coupon websites available. While this might look like a good useful idea, keep in mind that it has been classified as a Browser Hijacker by Several anti-virus applications.
When installed this extension will hijack your new tab page, changing it to a customized version of Search.MyWay.com. While active It records user browser activity, this data is later used to better target ads.
While browsing the internet with this extension installed you will see additional pop-up ads, sponsored content, and injected ads into your browser search results and pages. GetCouponsFast usually comes bundled with other PUP-s or Browser Hijackers that may harm your computer and it is recommended you remove it from your PC.
About Browser Hijackers
Browser hijacking means that a malicious code has taken control over and altered the settings of your internet browser, without your permission. They are created to disrupt browser functions for various reasons. It redirects you to the sponsored sites and inserts ads on your internet browser that assists its developer to generate revenue. While it might seem harmless, these tools were created by malicious people who always look to take advantage of you, so that they could make money from your naivety and distraction. They did not just ruin your browsers, but browser hijackers can also modify the system registry, making your computer or laptop susceptible to various other types of attacks.
Signs of browser hijacker infection
There are plenty of signs that indicate the web browser has been highjacked:
1. you notice unauthorized modifications to your web browser’s home-page
2. you find re-directed to internet sites you never intended to visit
3. the default browser configurations have been modified and/or your default web engine is altered
4. you’ll see many toolbars on your browser
5. you might see never-ending pop-up adverts on your computer screen
6. your browser has become unstable or starts running slowly
7. you are blocked to access the websites of antivirus solution providers.
How does a computer get infected with a browser hijacker?
Browser hijackers might use drive-by downloads or file-sharing networks or an email attachment in order to reach a targeted computer system. They could also come from add-on applications, also known as browser helper objects (BHO), web browser extensions, or toolbars. Some internet browser hijackers spread in user’s computers using a deceptive software distribution method called “bundling” (often through freeware and shareware).
Browser hijackers will affect the user’s web browsing experience severely, monitor the websites visited by users and steal sensitive information, cause difficulty in connecting to the web, and eventually create stability problems, making programs and systems freeze.
Removal
Some hijackers can be simply removed by deleting the free software they were included with or by deleting any add-ons you have recently added to your browser. Unluckily, the majority of the software applications utilized to hijack an internet browser are deliberately designed to be difficult to detect or get rid of. And there is no denying the very fact that manual repairs and removal can certainly be a difficult task for a novice PC user. Moreover, there are various risks connected with tinkering around with the system registry files.
Installing and running anti-malware software on the affected computer will automatically erase browser hijackers as well as other unwanted programs. In order to get rid of persistent browser hijackers effectively, install the award-winning Anti-Malware tool Safebytes Anti-Malware. Employ a pc optimizer (such as Total System Care) along with your anti-malware to repair various computer registry problems, remove computer vulnerabilities, and improve your computer performance.
How To Get Eliminate Virus That Is Blocking Antivirus Downloads?
Malware could cause all sorts of damage once they invade your computer, starting from stealing your private details to erasing data files on your computer system. Some malware is created to hinder or block things that you wish to do on your PC. It may not permit you to download anything from the net or it will prevent you from accessing a few or all of the websites, in particular the anti-virus sites. If you are reading this article right now, you may have perhaps realized that a malware infection is a reason for your blocked internet connectivity. So what to do if you want to download and install an anti-virus application like Safebytes? There are some steps you can take to circumvent this problem.
Boot Windows in Safe Mode
Safe Mode is actually a unique, simplified version of Windows in which just bare minimum services are loaded to prevent malware and also other troublesome programs from loading. If the malicious software is set to load automatically when the PC starts, shifting into this mode may prevent it from doing so. In order to enter into Safe Mode or Safe Mode with Networking, press the F8 key while the system is booting up or run MSCONFIG and find the “Safe Boot” options under the “Boot” tab. Once you are in safe mode, you can attempt to install your anti-malware program without the hindrance of the malicious software. Right after installation, run the malware scanner to remove standard infections.
Use an alternate web browser to download security software
Web-based malware can be environment-specific, aiming for a particular browser or attacking particular versions of the browser. The best solution to avoid this issue is to choose an internet browser that is known for its security features. Firefox contains built-in Malware and Phishing Protection to keep you secure online.
Run anti-virus from a pen drive
Another option would be to make a portable anti-malware program onto your USB flash drive. To run anti-virus using a pen drive, follow these simple measures:
1) Download Safebytes Anti-Malware or Windows Defender Offline onto a virus-free PC.
2) Plug the USB drive into the clean computer.
3) Double-click the Setup icon of the anti-malware program to run the Installation Wizard.
4) Select thumb drive as the place when the wizard asks you where you wish to install the application. Follow the directions to complete the installation process.
5) Unplug the flash drive. Now you can utilize this portable anti-virus on the infected computer.
6) Double click the Safebytes Anti-malware icon on the pen drive to run the application.
7) Click the “Scan Now” button to start the virus scan.
SafeBytes Anti-Malware Overview
Want to download the best anti-malware application for your desktop? There are many applications on the market that comes in free and paid versions for Windows systems. Some are very good ones, some are ok types, while some are just fake anti-malware programs that will damage your personal computer themselves! While looking for an antimalware program, pick one that offers reliable, efficient, and total protection against all known viruses and malware. On the list of recommended software is SafeBytes AntiMalware. SafeBytes has a good history of quality service, and customers appear to be happy with it.
Safebytes is among the well-established PC solutions companies, which provide this all-inclusive anti-malware application. With its outstanding protection system, this tool will automatically detect and remove most of the security threats, which include adware, viruses, browser hijackers, PUPs, trojans, worms, and ransomware.
SafeBytes possesses a variety of wonderful features that can help you protect your computer from malware attacks and damage. Listed below are a few of the great ones:
Real-time Protection: SafeBytes provides round-the-clock protection for your computer restricting malware intrusions in real-time. They are very efficient in screening and getting rid of numerous threats because they’re regularly improved with new updates and alerts.
Robust Anti-malware Protection: Built on a highly acclaimed antivirus engine, this malware removal tool has the capacity to find and remove various stubborn malware threats such as browser hijackers, PUPs, and ransomware that other common antivirus programs will miss.
Web protection: SafeBytes checks the hyperlinks present on a webpage for possible threats and tells you if the website is safe to explore or not, through its unique safety rating system.
Minimal CPU and Memory Usage: SafeBytes is a lightweight and simple to use antivirus and anti-malware solution. As it utilizes very low computer resources, this software leaves the computer power exactly where it belongs: with you.
24/7 Customer Service: Support service is available 24 x 7 x 365 days via chat and email to answer your queries.
Overall, SafeBytes Anti-Malware is a solid program since it has lots of features and could identify and remove any potential threats. Now you may realize that this tool does more than just scan and delete threats on your computer. So when you need advanced forms of protection features and threat detections, purchasing SafeBytes Anti-Malware could be well worth the dollars!
Technical Details and Manual Removal (Advanced Users)
If you don’t want to use malware removal software and prefer to eliminate GetCouponsFast manually, you could do so by going to the Windows Add/Remove Programs menu in the control panel and deleting the offending program; in cases of browser extensions, you can remove it by visiting the browser’s Add-on/Extension manager. Additionally, it is advised to reset your web browser settings to their default state.
Lastly, check your hard disk for all of the following and clean your registry manually to remove leftover application entries after uninstallation. Please keep in mind that only advanced users should attempt to manually edit the system files since deleting any single vital registry entry results in a serious problem or even a PC crash. Moreover, certain malicious programs are capable to defend against its removal. It is recommended that you do the removal process in Windows Safe Mode.
Files:
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\iadmakoacmnjmcacmhlcjcameijgcopj
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\iadmakoacmnjmcacmhlcjcameijgcopj
%UserProfile%\Local Settings\Application Data\GetCouponsFastTooltab
%LOCALAPPDATA%\GetCouponsFastTooltab
Registry:
HKEY_LOCAL_MACHINE\Software\[APPLICATION]\Microsoft\Windows\CurrentVersion\Uninstall..Uninstaller



 Without any fanfare, news, or information Bethesda has released a completely free upgrade for legendary Quake 1. Free upgrade is automatically applied to all users who possess the original game and it has already been rolled out.
Without any fanfare, news, or information Bethesda has released a completely free upgrade for legendary Quake 1. Free upgrade is automatically applied to all users who possess the original game and it has already been rolled out.
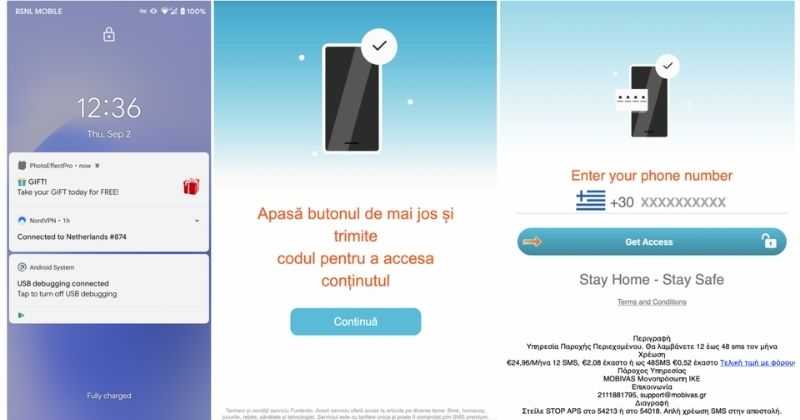 According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
