Error 0xe0434f4d displays when a remote computer runs an instance of the SQL Server 2005 but it fails to initialize. When the plan is started, this error displays in a status window on the SQL Server. Also, when the Update-OffilineAddressBook cmdlet is started in Microsoft Exchange Server, this error can occur.
 Error Causes
Error CausesError 0xe0434f4d can occur for possibly two main reasons. The first one is when the System Attendant Service is not properly running, and the second when you don’t have the permission to run the update. Other causes are when the .NET Framework 2.0 security does not allow sqlplanlaunch access to run from a shared network. Another cause is when the Offline Address Book (OAB) is not found in the Configuration Domain Controller server that the server of OAB generation uses.
In case you didn’t know, the Offline Address Book generation server is a mailbox server, and in order to resolve error 0xe0434f4d, you will have to replicate the OAB object to the Configuration Domain Controller server. In order to do so, follow steps:
Make sure the OAB object is reproduced in the Configuration Domain Controller Server. Follow these steps to do that:
When the OAB generation server receives this, then it will connect to the Configuration Domain Controller server and will locate the OAB object. If the OAB generation server is unable to find the OAB object, then the error will return on the cmdlet.
On SQL Server, you should change the .NET permissions to allow sqlplanlaunch application access to run from shared administration. For that, follow these steps:

 Is There Any Deal
Is There Any Deal Cheap Shark
Cheap Shark Humble Bundle
Humble Bundle Fanatical
Fanatical Slick Deals
Slick Deals Green Man Gaming
Green Man GamingRegular and gaming headphones have many differences between them and not knowing what they are can lead you to get yourself the wrong one. In this article, our goal is to analyze the differences between them so you can choose the right one for you.

One thing that goes in both worlds is that the cheapest models on both sides are not really worth the purchase since both the quality and longevity will be very low. If we compare high-end models, regular headphones are far far more expensive than gaming ones. Hi-end gaming models can go as far as 400$, perhaps a little more but hi-end audio regular headphones are going even for over 2000$.
If we compare same-price headphones generally regular ones will offer you a little better sound quality but gaming headphones will offer some features such as positional audio that regular ones do not have.
One of the main advantages of gaming headsets is positional audio and true surround sound. this technology is built-in so you can hear more clearly where your enemy is coming from that is a big help in competitive games. This is achieved by positioning multiple speakers in various positions and angles inside them. Each speaker has a different sound channel that is mixed with another speaker in order to provide you with a full surround experience.
Regular headphones have typically one or two speakers on both sides aimed at the same angle and can not offer precise surround or positional audio.
Both gaming and hi-fi headphones offer some sort of noise cancelation to minimize outside noise but if you really want to focus and have good noise cancelation you will have to look out for headphones with active noise cancelation or ANC.
Let us say this right at the start, most middle and quality regular audio headphones do not have a microphone at all, and ones that might pack one usually have it at a lower quality than gaming ones. This of course makes perfect sense since regular headphones will focus on audio, and gaming ones will focus on playing games where having a good microphone is essential in order to game properly.
Speaker quality will reflect directly on the sound quality and fidelity. This is where audio regular headphones have an advantage over gaming ones. Since they do not have many small speakers positioned at various angled and instead have just a few, usually 2 or 1 large one, that one is of much better quality and range for audio than a pack of small ones. If you are searching for clarity and quality of the audio itself, especially if you are listening to some FLAC uncompressed music, then regular HiFi ones are a much better choice.
Another area where regular ones have an advantage but that is no surprise since their price goes far up compared to gaming ones. Most of the time everything in hi-end audio headphones is made from quality materials and designed to last a long time and therefore advantage. Most of the time gaming headphones will come in plastic versions whereas higher quality audio ones pack a lot of durable metal in frames and in buds making them much more durable. Of course, we are talking here about proper headphone use, not extreme cases of throwing, etc.
“Error code: 0x80070035. The network path was not found.”One of the common causes of this error is the antivirus program or the Firewall installed on your computer. It could also be that the drive is not shared in the first place or there are some issues with your network drivers. Whichever the case is, here are some potential fixes you need to check out to fix the Error code: 0x80070035.
Still sitting on the fence about upgrading to Windows 11 because you don’t know what to expect? Interestingly, the new edition somehow manages to be both a total revamp and still very similar to its predecessor in many ways. It’s really something to experience for yourself.
We do want to give you a sneak peek, though. So here’s an overview of the biggest changes Windows 11 brings to the table.
The first thing anyone will notice after switching to Windows 11 is the striking visual difference. The entire interface is smoother, cleaner and more minimalistic than on Windows 10, even resembling the macOS in some instances.
Perhaps the most obvious change in appearance is the Start menu and Taskbar location, which is now at the bottom center. It’s actually very neat, but if you’re someone who loves familiarity, don’t worry, you can move it back to the left.
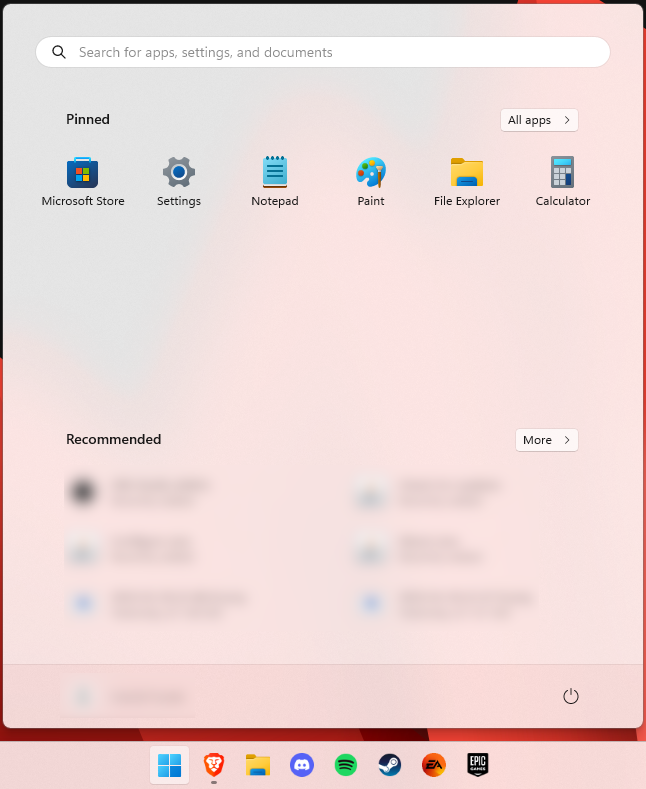
Moreover, you’ll notice that the Taskbar includes a Microsoft Teams icon by default (which you can, of course, remove) and that Live Tiles are gone. The News and Interests section has also been removed - or, shall we say, replaced. As opposed to Windows 10, news, weather forecasts and other information are now displayed as widgets.
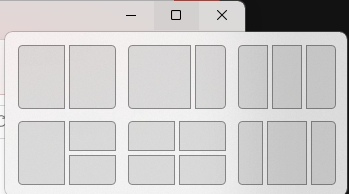
To add to the cleanliness of the UI, Microsoft also enhanced the ‘Snap Layouts’ feature to help you better organize your windows and maximize screen real estate. It’s similar to app grouping on your smartphone. In Windows 10 this feature is slightly restricted, as it requires some manual resizing and dragging. In Windows 11, you can just hover over the minimize/maximize option on a window, select a layout and throw the windows in there.
Microsoft has certainly paid attention to accessibility with Windows 10, but Windows 11 takes this to a whole new level.
One of the ways Windows 11 has taken things up a notch is by adding the long-awaited ‘Live Captions’ feature and advanced Narrator options.
Live Captions apply both to media played on your PC as well as your own speech when you’re using the microphone. Keep in mind that, as with almost all kinds of subtitles, you have to be prepared for a potential delay. However, it’s barely noticeable and doesn’t take away from the usefulness of this awesome new feature whatsoever.
As for the Narrator, there are three new voice packs to choose from. Microsoft has tried to put emphasis on a more natural voice than we are used to. So, now you can choose between Aria, Jenny and Guy, who will read pretty much anything off your screen out loud. Aside from this, Microsoft has also expanded the list of braille displays supported by the Narrator feature.
For users with anxiety or trouble concentrating, a welcomed addition is the Focus app, which is no longer part of the Clock app. It’s now separate and called ‘Focus Sessions’, automatically triggering the Do Not Disturb mode when activated. It blocks all pop-ups and flashes and lets you work in peace until you’re ready to switch it off.
Android users may rejoice! Windows 11 supports the use of your favorite applications now.
Microsoft has done this by integrating the Amazon Appstore to the Windows 11 Microsoft Store. From there, you can download your favorite Android apps and use them on your PC in a smartphone-like window.
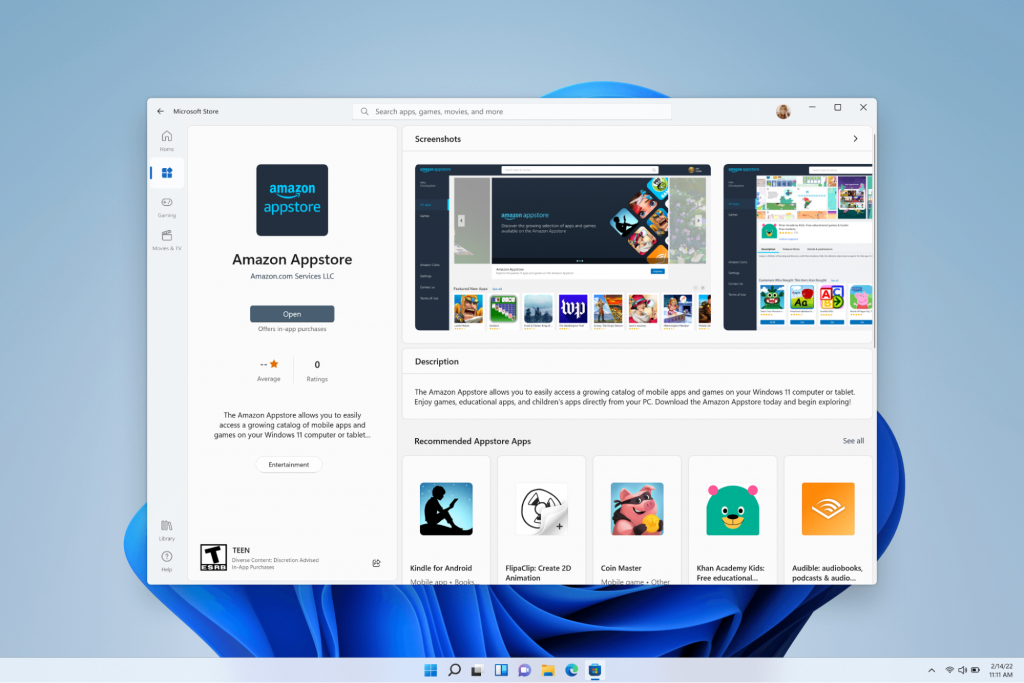
Unfortunately not too many apps are supported at this time, but Microsoft is working on making the emulation possible for many more. Also, the option is only available in specific regions at this moment - check out if you’re one of the lucky ones.
Avid gamers will be happy to hear that Microsoft has put some effort into streamlining Windows 11 for their gaming needs.
To give gamers a supreme visual experience, Windows 11 offers the ‘Auto HDR’ feature. As long as your monitor is HDR-compatible, this feature will automatically adjust the colors, brightness and contrast of games without any input from you.
Another update is DirectStorage, which we were introduced to in Windows 10 already. In Windows 11, it’s been improved to tweak loading times and overall gaming performance efficiency even better. The predisposition for it to work optimally is that your device has an NVMe SSD.
The Xbox Game Bar also helps gamers towards a smoother experience. It allows in-game screenshots, viewing processes that are running (similar to the Task Manager), monitoring the CPU and GPU performance and frame rate, integrating the Xbox App and more. There’s also a number of widgets you can now use with the Game Bar, for example the Spotify widget.
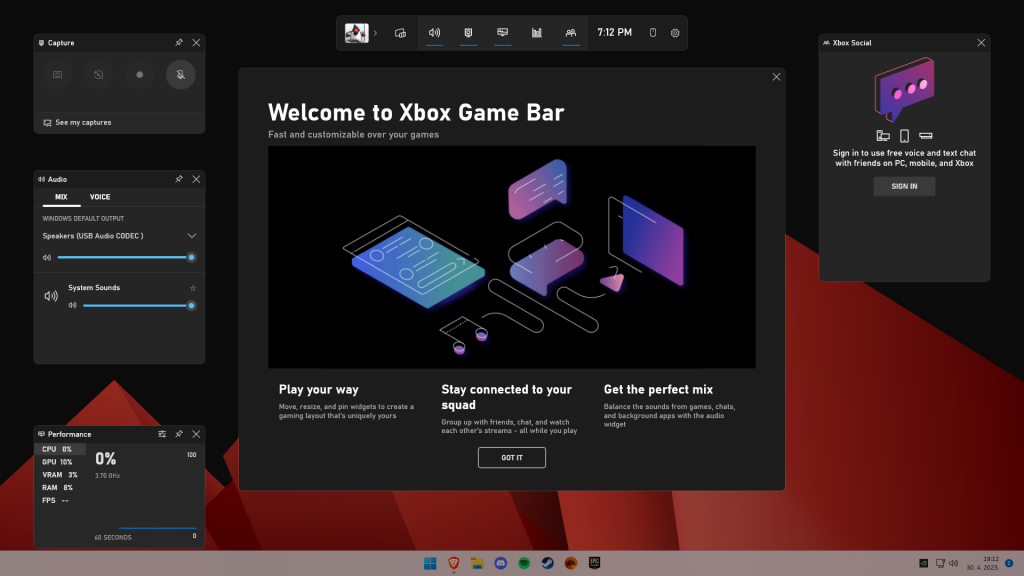
Another cool addition is the Xbox Game Pass, which unlocks hundreds of games to play on your Xbox App, with new additions coming in every month.
Aside from a sleek new look and better accessibility for all users, Windows 11 also comes with a security power-up. Bear in mind that this feature is only available on clean Windows 11 installs.
Smart App Control (SAC) is an AI-powered new feature designed to protect your PC from potential threats. It blocks untrustworthy apps and adware and helps detect potentially unwanted apps, maintaining your PC’s performance and keeping your system safe.
It comes with an ‘Evaluation’ mode, which you should definitely select when running SAC for the first time. That way, the app monitors your usage and assesses whether you’re a candidate for SAC. Some users need it to be on all the time, for others it might be too distracting. Evaluation mode will turn SAC on or off based on your usage.
Don’t disable SAC again unless you’re absolutely sure you don’t need it, since reenabling it will require a fresh install. We recommend you don’t turn it off, as it is a neat feature protecting your data and files from malware at all times.
Have we piqued your interest in trying Microsoft’s latest OS? It’s a pretty exciting new iteration, but we’ll let you find out for yourself. We hope you like it!
Loving Windows 11 so far? We sure are. Microsoft has clearly decided to take its OS to the next level and keeps showing it through every update. It makes you wonder what’s next - and today, you’ll find out!
Tons of new features have been leaked, and we can probably expect them with the 23H2 update. Here’s everything you need to know so far.

There are plenty of new features already confirmed for Windows 11. The only issue is we don’t know for sure if they’re coming with the 23H2 update or separately, at a different time. Whatever the case, a lot of them are pretty exciting.
Here’s an overview of what we might be getting this fall.
Another is AI-generated keywords, designed to improve the discoverability of apps you’re searching for. Moreover, the AI-generated review summary is designed to give us a simpler experience looking at reviews. Huge numbers of reviews will be compiled into a summary that’s easy to scan and lets us discover new content faster.
We’ve got some interesting stuff to look forward to with the next major Windows 11 update. And these are just the things the Internet’s actually heard of, so who knows what else Microsoft might be planning? It remains to be seen, hopefully just a few months from now. 23H2 has been released on October 31st.
DiscoverAncestry is a Browser Extension for Google Chrome developed by Mindspark Inc that presents itself as a web tool to discover the origins or meanings of particular family names. When installed this extension changes your default new tab page to search by MyWay, as well as your default search engine to Search.MyWay.com
While active, DiscoverAncestry logs user browsing information, recording clicked links, visited websites and viewed products. This information is later used to better target personal ads. Browsing the internet with this extension active will result in injection of additional ads, sponsored content and even pop-up ads throughout the browsing sessions.
DiscoverAncestry is usually found bundled with other potentially unwanted software, this combined alongside its aggressive ad injection is why DiscoverAncestry has been marked as a Browser Hijacker, and it is recommended to remove it from your computer.
 Error Causes
Error CausesProblems occur when your PST file becomes corrupted or hits the size limit. Outlook will start to display error messages. These errors include like 0x80040119, 0x80040600, and 0x8004060c.
You might think Outlook problems are just a minor inconvenience. You can’t access your emails and contact information, but that doesn’t actually affect computer security, right? Wrong! Outlook problems can indicate serious corruption issues within your system.
In many cases, your PST file can even be targeted specifically by a virus.
Today, many viruses are specially designed to steal personal information and then sell that information on the online black market. Since so much personal data is stored within Outlook’s PST file, this is often the first place that viruses look.
If you don’t want some hacker in a foreign country to read your emails, steal your contact information, or do all sorts of other dangerous tasks, then we advise you to fix your PST problem as soon as possible.
Other causes include hitting the 2GB memory limit on older versions of Outlook, erroneous SMTP settings, etc,.
PST errors are an incredibly annoying problem. However, thanks to powerful software like Stellar Phoenix Outlook PST Repair, it has never been easier to fix Outlook and recover all of the data inside your PST file. That means that you won’t lose contact information, calendar entries, emails, or any other information stored in Outlook.
ScanPST.exe rarely fixes problems with the PST file. Since the application is only a few megabytes in size, its effectiveness is very limited. Although Microsoft designed ScanPST.exe to be an effective solution to any PST files, it fails miserably.
Ultimately, after downloading ScanPST.exe and running it, your Microsoft Outlook will still be unable to send or receive emails. And, to make matters worse, you might also be unable to access contact data or read your old emails.
Unlike other PST repair solutions, ScanPST.exe will not recover deleted emails or other lost Outlook data. In fact, using ScanPST.exe can sometimes cause your personal data to become even more difficult to recover.
If you do want to try out ScanPST.exe, then go ahead. While it probably won’t make your PST errors worse, it won’t even come close to fixing them. If you’re ready for a more serious solution to PST problems, then keep reading.
You might think Outlook problems are just a minor inconvenience. You can’t access your emails and contact information, but that doesn’t actually affect computer security, right? Wrong!
Outlook problems can indicate serious corruption issues within your system. In many cases, your PST file can even be targeted specifically by a virus.
Today, many viruses are specially designed to steal personal information and then sell that information on the online black market. Since so much personal data is stored within Outlook’s PST file, this is often the first place that viruses look.
If you don’t want some hacker in a foreign country to read your emails, steal your contact information, or do all sorts of other dangerous tasks, then we advise you to fix your PST problem as soon as possible.
Microsoft’s ScanPST.exe application clearly doesn’t work. So what’s the next best option? Well, a program called Stellar Phoenix Outlook PST Repair has been helping PC users solve Outlook problems for several years. As the world’s leading Outlook solution, Stellar Phoenix Outlook PST Repair will quickly and effectively repair any PST problems you encounter.
So how does Stellar Phoenix Outlook Repair work? Well, it starts by finding your PST file. Once the PST file has been found, Stellar Phoenix Outlook PST Repair determines if the file is corrupt or full. It will then repair your PST file either by removing the size limit or by fixing the corrupt files.
Once Stellar Phoenix Outlook PST Repair determines that your calendar appointments, contact data, and emails have all been successfully recovered, it permanently restores access to your PST file.
In fact, Stellar Phoenix Outlook PST Repair can even restore Outlook data that you deleted a long time ago. So, instead of just being a PST error recovery tool, Stellar Phoenix Outlook PST Repair is also a powerful data recovery program.
After letting Stellar Phoenix Outlook PST Repair go to work, open up Outlook and try it out. You’ll have full access to all of your Outlook files and folders, and all of those ScanPST.exe problems will be a thing of the past.
Stellar Phoenix Outlook PST Repair comes with many advantages. Here are just a few reasons why it’s such a popular program:
Stellar Phoenix PST Repair is superior to ScanPST.exe in every way. But Stellar Phoenix’s most important advantage is that it actually works. If you’re ready to quickly fix your Outlook PST errors, then Stellar Phoenix Outlook PST Repair can help. Download it here today to experience the magic of PST repair for yourself.