Error Code 0x80070643 – What is it?
Error Code 0x80070643 or Windows Update error code affects various versions of the Windows operating system, including Windows 10. Error code 0x80070643 usually occurs due to corruption within the .Net Framework. When this occurs, users will be unable to install updates they have downloaded on their PC.
Solution
 Error Causes
Error Causes
Error codes within Windows occur for many reasons including corrupt system files, viruses, and lack of space on your PC. In terms of error code 0x80070643 in Windows 10, the cause usually relates to a problem with the .NET framework or errors within one’s registry.
Further Information and Manual Repair
To solve error code 0x80070643 in Windows 10, users will need to employ various manual repair methods. These methods seek to fix core problems that result in the error being present on your device in the first place. Thus, the methods include the use of the .Net Framework Repair tool, resetting Windows Update components, or running a clean boot.
Note that the instructions provided in this article must be followed correctly, as making changes to your computer via these manual repair methods can result in serious problems if mistakes are made. Consider a Windows repair technician if you are unable to complete the steps mentioned in the manual repair methods below. Note, failure to rectify this error might result in other error messages, such as error code 0xc004fc03
Method One: Run the .Net Framework Repair Tool
As error code 0x80070643 may be triggered by issues related to the .Net Framework on your machine, it’s important that you download the .Net Framework Repair tool. This tool, as the name suggests, helps to repair errors it detects within the setup or updates associated with the framework.
The tool is available on the official Windows site. Download the tool and follow the instructions provided. Once you’ve downloaded the .Net Framework Repair tool, run it and wait until it fixes all problems detected within the framework.
Afterward, reboot your computer and check to see if Windows Update is functioning properly. If the error code reoccurs, proceed to another solution by implementing the second manual repair method listed in this article.
Method Two: Reset Windows Update Components
This method is the most technical of all the methods mentioned in this article. It will require that Windows 10 user access Command Prompt and make modifications to the Windows registry – an area of the operating system which stores important information, settings and other details regarding hardware and programs installed on your machine. Follow the steps carefully and be sure to back up the registry before proceeding with this manual repair method.
Step one: Type Command Prompt in the search box near Start, then select Command Prompt (Admin).
Step two: Select Yes as soon as the User Account Control box appears.
Step three: Stop Windows Update service, the BITS service, and Cryptographic service by typing the following commands:
net stop bits
net stop wuauserv
net stop appidsvc
net stop cryptsvc
Step four: Be sure to press Enter after typing each command.
Step five: Type the following command, then Enter to delete qmgr*.dat files:
Del "%ALLUSERSPROFILE%Application DataMicrosoftNetworkDownloaderqmgr*.dat"
Step six: Press enter after typing the following command:
cd /d %windir%system32
Step seven: Reregister the files for BITS and Windows Update that you stopped in step three. To do this, type the following commands, selecting Enter after each command:
regsvr32.exe atl.dll
regsvr32.exe urlmon.dll
regsvr32.exe mshtml.dll
regsvr32.exe shdocvw.dll
regsvr32.exe browseui.dll
regsvr32.exe jscript.dll
regsvr32.exe vbscript.dll
regsvr32.exe scrrun.dll
regsvr32.exe msxml.dll
regsvr32.exe msxml3.dll
regsvr32.exe msxml6.dll
regsvr32.exe actxprxy.dll
regsvr32.exe softpub.dll
regsvr32.exe wintrust.dll
regsvr32.exe dssenh.dll
regsvr32.exe rsaenh.dll
regsvr32.exe gpkcsp.dll
regsvr32.exe sccbase.dll
regsvr32.exe slbcsp.dll
regsvr32.exe cryptdlg.dll
regsvr32.exe oleaut32.dll
regsvr32.exe ole32.dll
regsvr32.exe shell32.dll
regsvr32.exe initpki.dll
regsvr32.exe wuapi.dll
regsvr32.exe wuaueng.dll
regsvr32.exe wuaueng1.dll
regsvr32.exe wucltui.dll
regsvr32.exe wups.dll
regsvr32.exe wups2.dll
regsvr32.exe wuweb.dll
regsvr32.exe qmgr.dll
regsvr32.exe qmgrprxy.dll
regsvr32.exe wucltux.dll
regsvr32.exe muweb.dll
regsvr32.exe wuwebv.dll
Step eight: Reset Winsock in Command Prompt by typing the following command, then selecting Enter:
netsh winsock reset
Step nine: Configure proxy settings in Windows 10 with the following command, then press Enter:
netsh winhttp reset proxy
Step ten: To restart the BITS, Windows Update, and Cryptographic service, type the following commands, then press Enter:
net start bits
net start wuauserv
net start appidsvc
net start cryptsvc
Step eleven: Install the latest Windows Update Agent.
Step twelve: Restart your machine.
Once you’ve restarted your PC, check Windows Update to verify if the error code is resolved. You should now be able to access the latest updates on your device. However, if a problem has arisen and the error code reoccurs, you will need to proceed with a Clean Boot.
Method Three: Download an Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 8 and other related issues when they do arise, download and install a powerful automated tool.
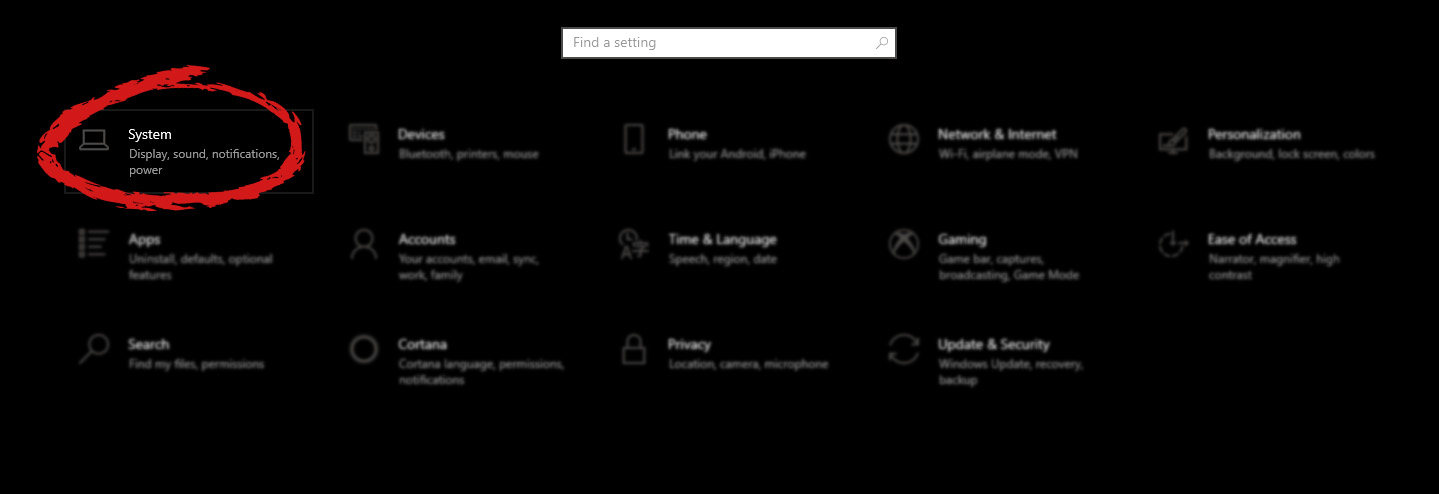 Once you are in the system, on the left tabs find and click on Clipboard.
Once you are in the system, on the left tabs find and click on Clipboard.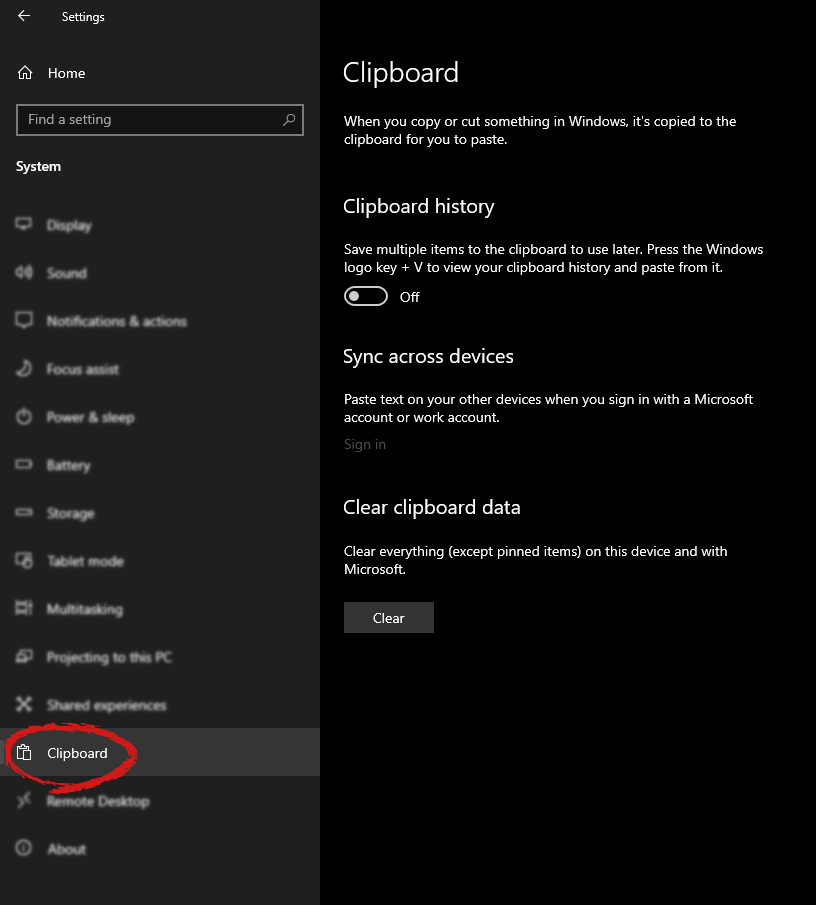 If you are not logged in to your Microsoft account do so on the right panel by locating Sync across devices and click on sign in.
If you are not logged in to your Microsoft account do so on the right panel by locating Sync across devices and click on sign in.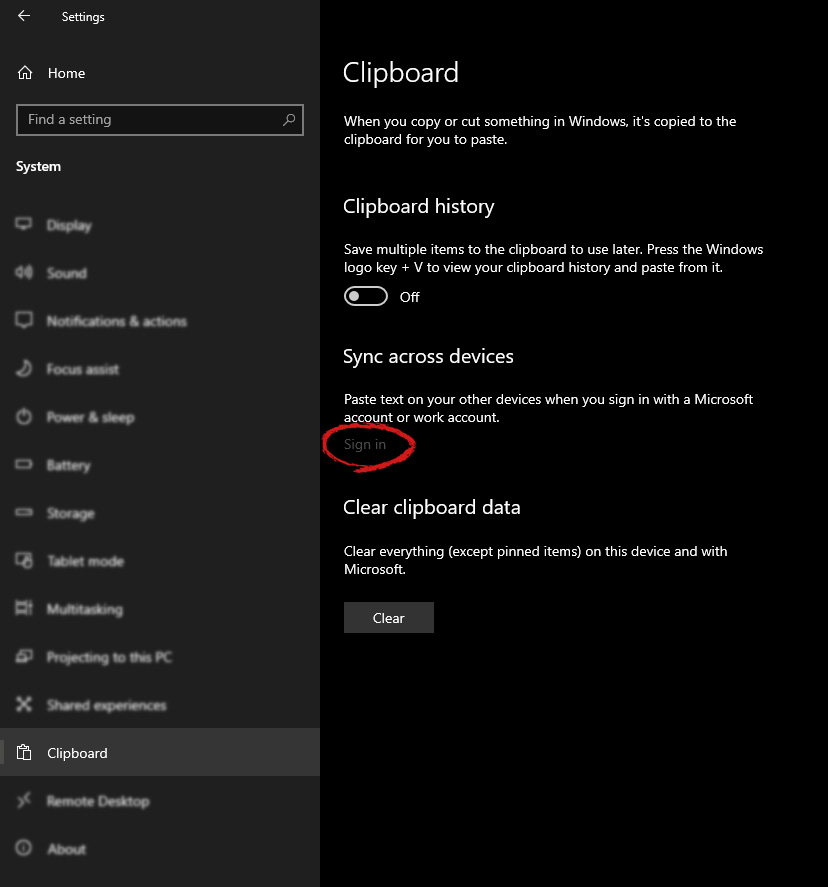 When you are signed in click on the option to turn it on.
When you are signed in click on the option to turn it on.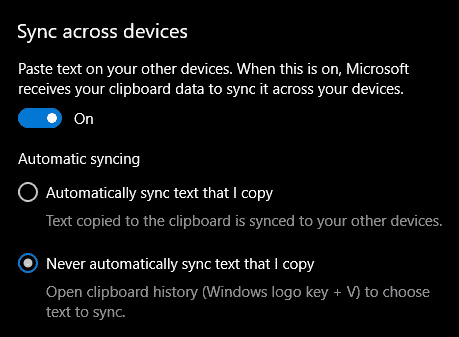 One option is turned ON, you will be greeted with two choices, to copy everything from the clipboard automatically or to choose text which you want to sync and paste it with ⊞ WINDOWS + V. Choose whatever better suits your needs, and you are done.
One option is turned ON, you will be greeted with two choices, to copy everything from the clipboard automatically or to choose text which you want to sync and paste it with ⊞ WINDOWS + V. Choose whatever better suits your needs, and you are done.

