If, while using your computer, you encounter the ACPI.sys Blue Screen error, read on as this post will guide you in fixing the problem. The ACPI.sys file is a Windows operating system file that is related to the MSDN 2939. ACPI.sys, the Windows ACPI driver, is an inbox component of the Windows operating system. It is the one that supports the power management as well as the Plug and Play or PnP device enumeration. And so if this file ends up getting corrupted, it is known to cause a Blue Screen error.
Another possible cause for the ACPI.sys Blue Screen error includes RAM issues, incompatible firmware, hard disk issues, corrupted drivers or malware infection, and so on. Here are some Blue Screen errors that can be triggered by the ACPI.sys file:
- KMODE EXCEPTION NOT HANDLED
- PAGE FAULT IN A NONPAGED AREA
- SYSTEM THREAD EXCEPTION NOT HANDLED
- IRQL NOT LESS OR EQUAL
- KERNEL DATA INPAGE
- SYSTEM SERVICE EXCEPTION
To fix the Blue Screen error associated with the ACPI.sys file, refer to the instructions provided below.
Option 1 – Try to recreate the ACPI.sys file
If the first option didn’t work, the next thing you can do is to recreate the ACPI.sys file. Every time your Windows 10 PC boots up, it looks for all the system drivers in place and if it is unable to find them, it tries to create them. This is why if you remove your corrupt driver file, chances are, you might get a fixed file recreated just for you. How? Refer to the steps below.
- Boot your Windows 10 PC in Safe Mode.
- Then open File Explorer and navigate to this location: C:/Windows/System32/drivers
- From there, look for the file named ACPI.sys and rename it to ACPI.old.
Note: As you can see, the file’s extension has changed from .sys to .old.
- Now restart your computer and check if the ACPI.sys Blue Screen error is now fixed.
Option 2 – Try to update or rollback the ACPI Driver
The first thing you can try to fix the Storport.sys Blue Screen error is to either update or roll back the device drivers. It is most likely that after you updated your Windows computer that your driver also needs a refresh. On the other hand, if you have just updated your device drivers then you need to roll back the drivers to their previous versions. Whichever applies to you, refer to the steps below.
- Tap the Win + X keys to open the Win X menu and from there, select the Device Manager.
- After opening the Device Manager, look for the ACPI.sys driver and right-click on it, and then select Properties.
- Next, go to the Driver section. Note that the rollback option would only be available if you’ve recently updated the ACPI.sys driver. So if you can’t see it then click on the Update Driver button.
- After that, Windows will automatically check for the problems that could be related to the Blue Screen error.
- Finally, restart your computer. It will just reinstall the device drivers automatically.
Note: You can also directly download the relevant drivers of your computer from the manufacturers’ website. So if you have an SSD, the issue might be due to an old storage driver. On the other hand, if updating the ACPI driver, didn’t work, you can also try to copy the ACPI.sys system driver file from the System32 folder of another computer that’s functioning properly and runs the same Windows OS version. Afterward, place it on your problematic computer and check if it fixes the BSOD error or not.
Option 3 – Run System File Checker or SFC scan
System File Checker or SFC is a built-in command utility that helps in restoring corrupted files as well as missing files. It replaces bad and corrupted system files with good system files. To run the SFC command, follow the steps given below.
- Tap Win + R to launch Run.
- Type in cmd in the field and tap Enter.
- After opening Command Prompt, type in sfc /scannow
The command will start a system scan which will take a few whiles before it finishes. Once it’s done, you could get the following results:
- Windows Resource Protection did not find any integrity violations.
- Windows Resource Protection found corrupt files and successfully repaired them.
- Windows Resource Protection found corrupt files but was unable to fix some of them.
Reboot your PC.
Option 4 – Run the Blue Screen Troubleshooter
Troubleshooting Blue Screen of Death errors wouldn’t be complete without the Blue Screen troubleshooter. As you know, it is a built-in tool in Windows 10 that helps users in fixing BSOD errors like ACPI.sys. It can be found on the Settings Troubleshooters page. To use it, refer to these steps:
- Tap the Win + I keys to open the Settings panel.
- Then go to Update & Security > Troubleshoot.
- From there, look for the option called “Blue Screen” on your right-hand side and then click the “Run the troubleshooter” button to run the Blue Screen Troubleshooter and then follow the next on-screen options. Note that you might have to boot your PC into Safe Mode.
Option 5 – Run System Restore
- Tap the Win + R keys to open the Run dialog box.
- After that, type in “sysdm.cpl” in the field and tap Enter.
- Next, go to the System Protection tab then click the System Restore button. This will open a new window where you have to select your preferred System Restore point.
- After that, follow the on-screen instructions to finish the process and then restart your computer and check if the problem is fixed or not.
 Microsoft office has two major packages, an online one, and an offline version. The online version of the course is Office 365 that requires a monthly subscription and it is always regularly updated and maintained. Another version is more of a typical old school application, install it and use it, no constant internet connection is required and no monthly subscription is required, buy once and use it.
The last version of buying it once and use it was Office 2019 and after two years we are going to receive a new version soon. Microsoft has set its release date for October 5th of this year and as always it will feature the current latest version of office applications and one-time purchase.
The new office will support dark mode and other improvements tied to the new Windows 11 and some specific features tied to Office itself.
Microsoft office has two major packages, an online one, and an offline version. The online version of the course is Office 365 that requires a monthly subscription and it is always regularly updated and maintained. Another version is more of a typical old school application, install it and use it, no constant internet connection is required and no monthly subscription is required, buy once and use it.
The last version of buying it once and use it was Office 2019 and after two years we are going to receive a new version soon. Microsoft has set its release date for October 5th of this year and as always it will feature the current latest version of office applications and one-time purchase.
The new office will support dark mode and other improvements tied to the new Windows 11 and some specific features tied to Office itself. 
 Update Windows 11
Update Windows 11
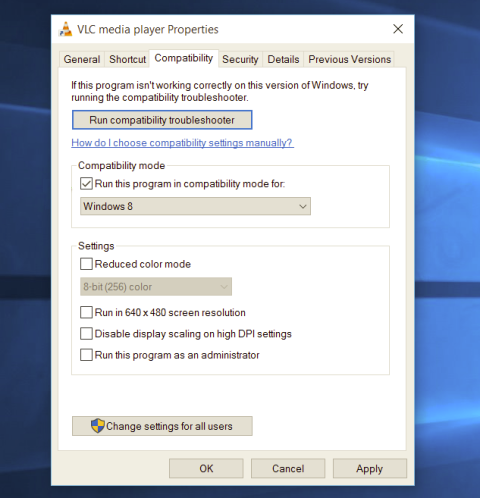 Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
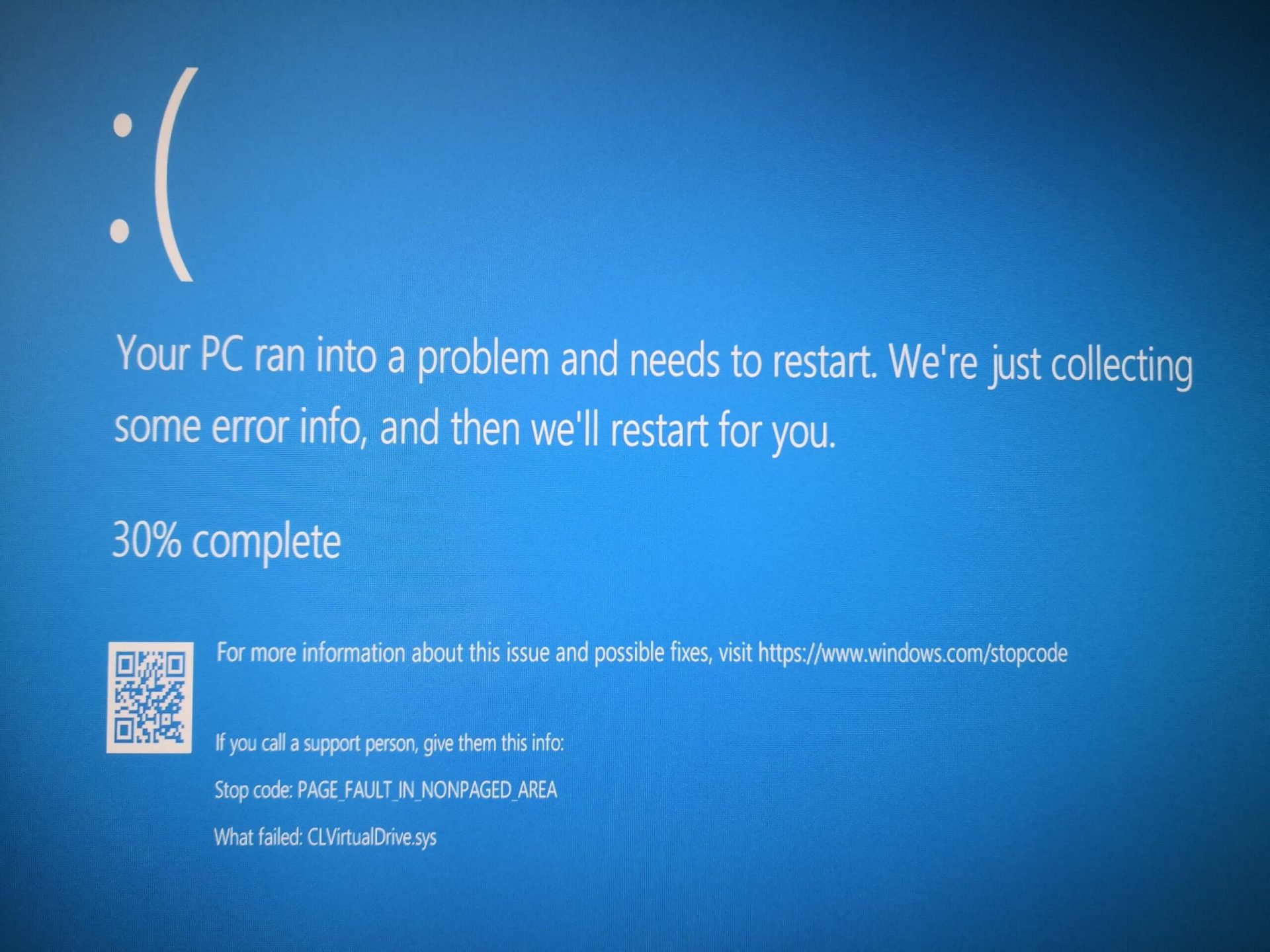 Rollback using system restore
Rollback using system restore
