If you are a kid or in your teenage years you maybe will be not familiar with Commodore 64 but we are welcoming you anyway to go with us on this journey through time and find out about one of the most influential and beloved home computer of all time.
 History of Commodore
History of Commodore
Firstly shown to the world in January of 1982, at the Consumer Electronics Show, C64 caught attention right away with its low price of only $595. Although it had some issues like limited functionality in some fields and a non-wide range of use by 1984 its price dropped below $200 and it cemented itself as an affordable home computer for the middle class.
In as same year Apple has released their Apple II computer with far superior capabilities, commodore 64 remains a middle-class favorite due to its price.
Also, the company has decided to distribute its homemade computer via some other means including not only just electronics stores specialized in that kind of equipment but in general shops and big department stores, through toy stores and book shops as well as through specialized dealers. This has given C64 a more competitive edge and mixed with the affordable price it soon became a staple of home computing.

With sales booming and the early reliability issues with the hardware addressed, software for the C64 began to grow in size and ambition during 1984. This growth shifted to the primary focus of most US game developers. The two holdouts were Sierra, who largely skipped over the C64 in favor of Apple and PC compatible machines, and Broderbund, who was heavily invested in educational software and developed primarily around the Apple II. In the North American market, the disk format had become nearly universal while cassette and cartridge-based software all but disappeared. So most US-developed games by this point grew large enough to require multi-loading.
At a mid-1984 conference of game developers and experts at Origins Game Fair, Dan Bunten, Sid Meier, and a representative of Avalon Hill said that they were developing games for the C64 first as the most promising market. By 1985, games were an estimated 60 to 70% of Commodore 64 software. Over 35% of SSI's 1986 sales were for the C64, ten points higher than for the Apple II.
Everything was great for Commodore but the industry was moving forward and by the year 1988, PC compatible computers were stated to be the largest and fastest-growing home entertainment systems pushing C64 on to second place. Also, Nintendo’s gaming system has started to take hold in the world with amazing 7 million systems sold in 1988 only.
By the year 1991, many developers exited the gaming market for Commodore 64 home computer system and its popularity started to fall due to lack of software and not so many hardware changes.
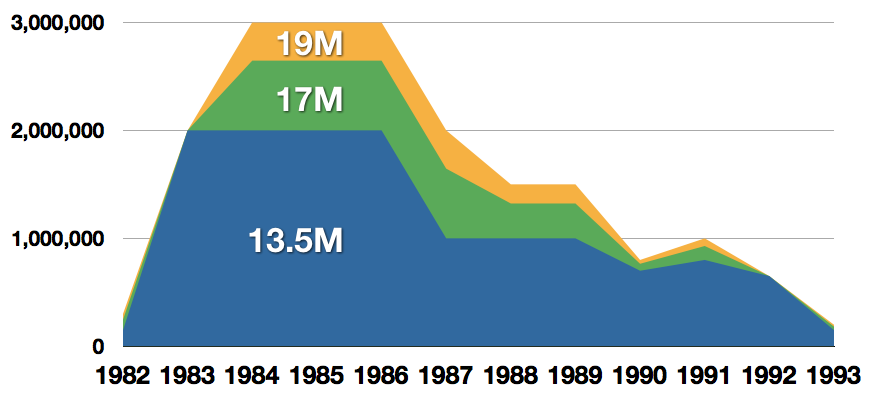
Commodore announced that the C64 would be finally discontinued in 1995.
However, only one month later in April 1994, the company filed for bankruptcy. When Commodore went bankrupt, all production on their inventory, including the C64, was discontinued, thus ending the C64's 11 and a half year production.
Legendary titles
The history of Commodore 64 is interesting ones and I believe that it has done much for computers in general, yes it ran 11 years and that seems like a small-time, but remember that it was 11 years of C64 alone, there were other computers released by the company but none except arguably AMIGA 500 has not reached that much popularity as Commodore 64.
That being said the system has left some of the great titles in its catalog that are great to be played even today and have been classic games on other platforms, even on PC itself. That being said I am giving you the top 100 games for Commodore 64:
 Zak McKracken and the Alien Mindbenders
Zak McKracken and the Alien Mindbenders- Pirates!
- Maniac Mansion
- IK+
- Bubble Booble
- Turrican II: The Final Fight
- Last Ninja 2
- Space Rogue
- Ultima IV: Quest of the Avatar
- Archon: The Light and the Dark
- Turrican
- Wasteland
- Defender of the Crown
- Elite
- Ultima V: Warriors of Destiny
- Laser Squad
- Prince of Persia
- Impossible Mission
- U.L.E.
- Pool of Radiance
- Bruce Lee
- Paradroid
- Project Stealth Fighter
- Curse of the Azure Bonds
- Ultima III: Exodus
- Legacy of the Ancients
- Winter Games
- Leaderboard Golf
- Supremacy
- Airborne Ranger
- Exile
- Last Ninja, The
- World Class Leader Board
- MicroProse Soccer
- Project Firestart
- Boulder Dash
- Summer Games 2
- Great Giana Sisters, The
- Neuromancer
- Mad Doctor
- Mail Order Monsters
- Zork I: The Great Underground Empire
- Buck Rogers: Countdown to Doomsday
- Katakis
- Bard's Tale, The: Tales of the Unknown
- WIzball
- Times of Lore
- Emlyn Hughes International Soccer
- Ultimate Wizard
- Alternate Reality: The Dungeon

- World Games
- Leaderboard Executive
- California Games
- Samurai Warrior: The Battles of Usagi Yojimbo
- Summer Games
- Creatures 2: Torture Trouble
- Gunship
- Space Taxi
- International Karate
- Silent Service
- Bard's Tale III, The: Thief of Fate
- Seven Cities of Gold
- Armalyte
- Raid on Bungeling Bay
- Alter Ego: Male Version
- Enforcer: Fullmetal Megablaster
- Detective Game, The
- Creatures
- Skate or Die!
- Heart of Africa
- E.R.O. - Helicopter Emergency Rescue Operation
- Way of the Exploding Fist, The
- Stunt Car Racer
- Wizard of Wor
- Bard's Tale II, The: The Destiny Knight
- Mayhem in Monsterland
- Train, The: Escape to Normandy
- Jumpman
- Champions of Krynn
- Pitstop II
- Barry McGuigan World Championship Boxing
- Montezuma's Revenge
- Boulder Dash II: Rockford's Revenge
- Spy vs Spy
- Mercenary: Escape from Targ
- Midnight Resistance
- Lords of Midnight
- Lode Runner
- Castles of Doctor Creep, The
- Boulder Dash Construction Kit
- Buggy Boy
- Racing Destruction Set
- Dino Eggs
- Realm of Impossibility
- Rainbow Islands
- Beach-Head II: The Dictator Strikes Back
- Barbarian: The Ultimate Warrior
- Grand Prix Circuit
- Head Over Heels
- Sentinel, The
Commodore 64 emulator and game ROMs
Commodore 64 might be in the past but its legacy still lives on even today through emulators and ROMs for emulators. You can even purchase one in working condition if you want and relive the full experience as it once was.
If you are not keen on spending money for reliving and checking games or software of C64 here are some links to help you to at least experience part of it completely free.
Commodore 64
Emulator
C64 Game
ROMs
Conclusion
It is without a doubt that the C64 home system has made a great mark on home computers echoing even today and I am very grateful that I have been part of it as a kid. Sometimes today I will still spin some old classic via emulator just for nostalgia and enjoy its simplicity.
Thank you for reading the article and I hope to see you soon again.

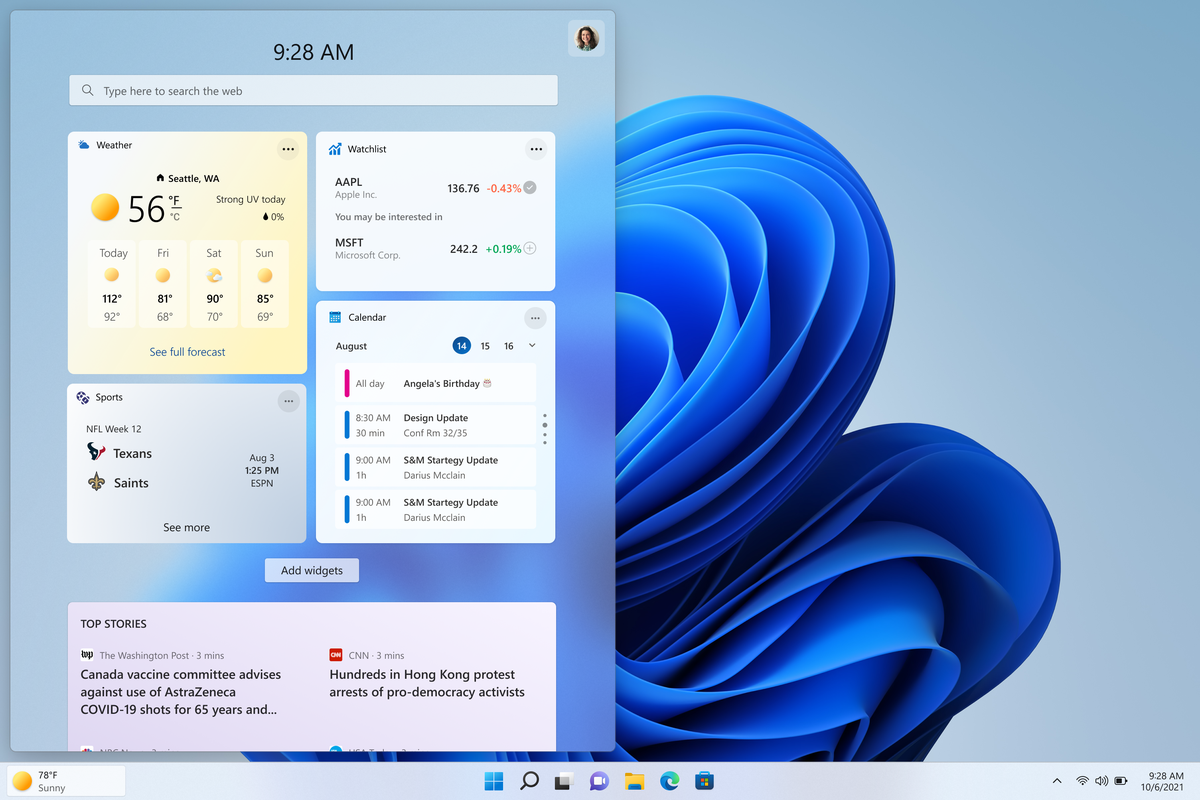 The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it.
The first step is to right-click anywhere on the taskbar (in empty space) and choose Taskbar settings
Once the taskbar settings are opened, find Widgets and click on the switch on the far right to turn it off, immediately no more information will be shown on the taskbar and it will be free again. And that is all there is to it. 
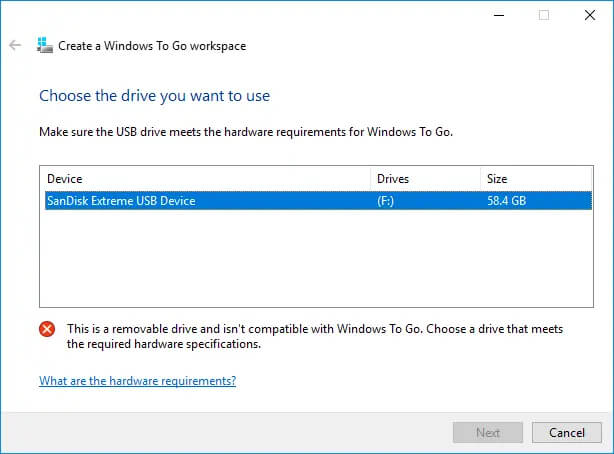 Many Linux users if not all of them can run their distros from a USB drive but did you know you can run Windows 10 from a USB drive as well?
Microsoft has introduced all the way back to Windows 8 one feature called Windows To Go and it kept it in Windows 8.1 and in Windows 10 as well.
This feature is intended as a convenient way for workers to carry their corporate environments with them, but having your own copy of Windows on a thumb drive could be handy for backup purposes, too, or if you frequently use public machines that lack your preferences/applications or that have a restricted OS.
Many Linux users if not all of them can run their distros from a USB drive but did you know you can run Windows 10 from a USB drive as well?
Microsoft has introduced all the way back to Windows 8 one feature called Windows To Go and it kept it in Windows 8.1 and in Windows 10 as well.
This feature is intended as a convenient way for workers to carry their corporate environments with them, but having your own copy of Windows on a thumb drive could be handy for backup purposes, too, or if you frequently use public machines that lack your preferences/applications or that have a restricted OS.
 History of Commodore
History of Commodore With sales booming and the early reliability issues with the hardware addressed, software for the C64 began to grow in size and ambition during 1984. This growth shifted to the primary focus of most US game developers. The two holdouts were Sierra, who largely skipped over the C64 in favor of Apple and PC compatible machines, and Broderbund, who was heavily invested in educational software and developed primarily around the Apple II. In the North American market, the disk format had become nearly universal while cassette and cartridge-based software all but disappeared. So most US-developed games by this point grew large enough to require multi-loading.
At a mid-1984 conference of game developers and experts at Origins Game Fair, Dan Bunten, Sid Meier, and a representative of Avalon Hill said that they were developing games for the C64 first as the most promising market. By 1985, games were an estimated 60 to 70% of Commodore 64 software. Over 35% of SSI's 1986 sales were for the C64, ten points higher than for the Apple II.
Everything was great for Commodore but the industry was moving forward and by the year 1988, PC compatible computers were stated to be the largest and fastest-growing home entertainment systems pushing C64 on to second place. Also, Nintendo’s gaming system has started to take hold in the world with amazing 7 million systems sold in 1988 only.
By the year 1991, many developers exited the gaming market for Commodore 64 home computer system and its popularity started to fall due to lack of software and not so many hardware changes.
With sales booming and the early reliability issues with the hardware addressed, software for the C64 began to grow in size and ambition during 1984. This growth shifted to the primary focus of most US game developers. The two holdouts were Sierra, who largely skipped over the C64 in favor of Apple and PC compatible machines, and Broderbund, who was heavily invested in educational software and developed primarily around the Apple II. In the North American market, the disk format had become nearly universal while cassette and cartridge-based software all but disappeared. So most US-developed games by this point grew large enough to require multi-loading.
At a mid-1984 conference of game developers and experts at Origins Game Fair, Dan Bunten, Sid Meier, and a representative of Avalon Hill said that they were developing games for the C64 first as the most promising market. By 1985, games were an estimated 60 to 70% of Commodore 64 software. Over 35% of SSI's 1986 sales were for the C64, ten points higher than for the Apple II.
Everything was great for Commodore but the industry was moving forward and by the year 1988, PC compatible computers were stated to be the largest and fastest-growing home entertainment systems pushing C64 on to second place. Also, Nintendo’s gaming system has started to take hold in the world with amazing 7 million systems sold in 1988 only.
By the year 1991, many developers exited the gaming market for Commodore 64 home computer system and its popularity started to fall due to lack of software and not so many hardware changes.
 Commodore announced that the C64 would be finally discontinued in 1995.
However, only one month later in April 1994, the company filed for bankruptcy. When Commodore went bankrupt, all production on their inventory, including the C64, was discontinued, thus ending the C64's 11 and a half year production.
Commodore announced that the C64 would be finally discontinued in 1995.
However, only one month later in April 1994, the company filed for bankruptcy. When Commodore went bankrupt, all production on their inventory, including the C64, was discontinued, thus ending the C64's 11 and a half year production.
 Zak McKracken and the Alien Mindbenders
Zak McKracken and the Alien Mindbenders

 If you are not keen on spending money for reliving and checking games or software of C64 here are some links to help you to at least experience part of it completely free.
Commodore 64
If you are not keen on spending money for reliving and checking games or software of C64 here are some links to help you to at least experience part of it completely free.
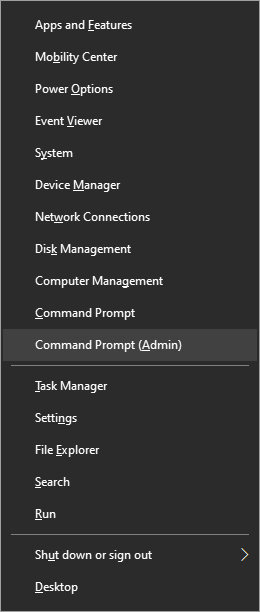
Commodore 64  From the menu choose command prompt (admin)
From the menu choose command prompt (admin)
 In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer
In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer