Gaming Wonderland is a Browser Extension for Google Chrome developed by Mindspark. This extension allows you to look up some popular browser games, as well as to find multiplayer games.
When installed it changes your default search provider and your default home page to MyWebSearch. While browsing the internet, this extension will gather your browsing information, website visits, clicks, and other information that is later sent to Mindspark ad servers and used to better target ads.
While using this extension you will see additional unwanted ads appearing throughout your browser sessions.
Due to the nature of this application and the fact that it has been marked as a Browser Hijacker by several anti-virus scanners, it is not recommended to keep it on your computer.
About Browser Hijackers
Browser hijacking means that a malicious code has power over and modified the settings of your internet browser, without your consent. They are made to disrupt browser functions for a variety of reasons. These are generally used to force visitors to a specific site, manipulating web traffic to generate ad revenue. It may appear harmless, but the majority of such sites are not legitimate and will present a serious risk to your online safety. As soon as the program attacks your computer or laptop, it begins to mess things up a whole that slows your system down to a crawl. In the worse case, you could be pushed to tackle serious malware threats as well.
Browser hijacking symptoms
When your web browser is hijacked, the following could happen: you find unauthorized modifications to your web browser’s home-page; new bookmarks pointing to pornographic websites have been added to your bookmarks; default web engine is changed; you are finding browser toolbars you haven’t noticed before; unstoppable flurries of popup advertisements show up on your PC screen; your browser gets slow, buggy, crashes quite often; you’re prohibited access to specific websites, including the site of an anti-malware software firm like SafeBytes.
How does a browser hijacker infect a PC
Browser hijackers might use drive-by downloads or file-sharing websites or even an e-mail attachment in order to reach a targeted computer. They could also be deployed through the installation of a web browser toolbar, add-on, or extension. A browser hijacker can also be installed as a part of freeware, shareware, demoware, and pirated programs. A good example of a notorious browser hijacker is the latest Chinese malicious software called “Fireball”, which has attacked 250 million PCs worldwide. It works as a hijacker but can be turned into a fully functioning malware downloader later on.
Browser hijackers will affect the user’s browsing experience severely, keep track of the websites visited by users and steal private information, cause problems in connecting to the net, and eventually create stability issues, making applications and computers freeze.
Browser Hijacker Malware – Removal
Some kinds of browser hijackers can be removed from your computer by deleting malicious software applications or any other recently added shareware. At times, it can be a tough task to discover and get rid of the malicious component since the associated file might be running as part of the operating system process. Novice PC users should not try for the manual form of removal, since it calls for thorough computer knowledge to do fixes on the system registry and HOSTS file.
Installing and running antivirus applications on the affected system will automatically erase browser hijackers and also other unwanted applications. Safebytes Anti-Malware incorporates a cutting-edge anti-malware engine that will help you prevent browser hijacker infection in the first place, and clean up any existing problems. Use a system optimizer together with your antivirus software to fix various registry problems, remove system vulnerabilities, and boost your computer's overall performance.
Help! Malware Blocking Antivirus Installation And Access To The Web
Viruses can cause plenty of damage to your PC. Some malware variants alter internet browser settings by adding a proxy server or change the PC’s DNS settings. In such cases, you will be unable to visit certain or all websites, and therefore not able to download or install the required security software to eliminate the malware. So what you should do if malware keeps you from downloading or installing Safebytes Anti-Malware? There are a few actions you can take to circumvent this issue.
Use Safe Mode to resolve the issue
In Safe Mode, you may change Windows settings, uninstall or install some programs, and remove hard-to-delete viruses and malware. In case the virus is set to load immediately when the PC starts, shifting into this mode may well prevent it from doing so. To boot into Safe Mode, press the “F8” key on the keyboard right before the Windows logo screen appears; Or right after normal Windows boot up, run MSCONFIG, look over Safe Boot under Boot tab, and then click Apply. Once you’re in safe mode, you can try to install your antivirus program without the hindrance of malicious software. At this point, you can actually run the antivirus scan to get rid of viruses and malware without any interference from another malicious application.
Switch to an alternate internet browser
Some viruses might target vulnerabilities of a specific browser that obstruct the downloading process. If you seem to have a trojan attached to Internet Explorer, then switch to an alternate browser with built-in security features, such as Firefox or Chrome, to download your favorite antivirus program – Safebytes.
Create a bootable USB antivirus drive
Another solution is to save and run an antivirus software program completely from a USB drive. Adopt these measures to run the anti-malware on the infected computer.
1) On a virus-free computer, install Safebytes Anti-Malware.
2) Connect the USB drive to a USB port on the clean computer.
3) Double-click the Setup icon of the antivirus software to run the Installation Wizard.
4) Select the drive letter of the flash drive as the place when the wizard asks you exactly where you want to install the antivirus. Follow the activation instructions.
5) Unplug the USB drive. Now you can use this portable anti-virus on the affected computer.
6) Run the Safebytes Anti-malware directly from the USB drive by double-clicking the icon.
7) Simply click “Scan Now” to run a complete scan on the infected computer for viruses.
Detect And Remove Viruses With SafeBytes Anti-Malware
If you are looking to download the anti-malware program for your PC, there are various tools on the market to consider however, you cannot trust blindly anyone, regardless of whether it is paid or free program. A few are really worth your money, but most aren’t. You must opt for a company that creates industry-best antimalware and has earned a reputation as reliable. On the list of strongly recommended software is SafeBytes AntiMalware. SafeBytes carries a good track record of quality service, and customers appear to be happy with it.
SafeBytes anti-malware is trustworthy software that not only protects your system completely but is also quite user-friendly for people of all skill levels. Using its outstanding protection system, this tool will automatically detect and eliminate most of the security threats, including browser hijackers, viruses, adware, PUPs, trojans, worms, and ransomware.
SafeBytes anti-malware takes computer protection to a totally new level with its advanced features. Below are some of the features you might like in SafeBytes.
Anti-Malware Protection: This deep-cleaning anti-malware software program goes much deeper than most anti-virus tools to clean out your personal computer. Its critically acclaimed virus engine locates and disables hard-to-remove malware that hides deep within your personal computer.
Real-time Protection: SafeBytes delivers complete and real-time security for your PC. It’ll constantly monitor your pc for hacker activity and also provides end-users with sophisticated firewall protection.
Website Filtering: SafeBytes gives an instant safety rating to the pages you are going to visit, automatically blocking unsafe sites and making sure that you are certain of your safety while browsing the net.
High-Speed Malware Scanning Engine: SafeBytes’s high-speed malware scanning engine lessens scan times and extends battery life. Simultaneously, it will effectively find and get rid of infected computer files or any internet threat.
Low CPU/Memory Usage: SafeBytes is well-known for its low impact on processing power and great detection rate of various threats. It runs silently and efficiently in the background so you are free to utilize your personal computer at full power all the time.
24/7 Premium Support: You can get 24/7 technical assistance to quickly resolve any issue with your security software.
To sum it up, SafeBytes Anti-Malware provides outstanding protection combined with very low system resource usage with great malware prevention and detection. You now may know that this tool does more than just scan and remove threats from your PC. If you’re searching for the absolute best malware removal application out there, and if you don’t mind spending a few bucks for it, go for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you would like to do the removal of Gaming Wonderland manually instead of using an automated software tool, you may follow these measures: Go to the Windows Control Panel, click the “Add or Remove Programs” and there, select the offending application to uninstall. In case of suspicious versions of browser plug-ins, you can easily get rid of it through your web browser’s extension manager. You may even want to reset your home page and search engine providers, and also delete temporary files, browsing history, and cookies.
In order to ensure the complete removal, manually examine your hard drive and registry for all of the following and remove or reset the values accordingly. Having said that, editing the Windows registry is really a difficult job that only advanced users and professionals should try to fix it. Furthermore, some malicious programs have the capability to defend against its deletion. It is advisable that you do the removal procedure in Windows Safe Mode.
Files:
%PROGRAMFILES%\GamingWonderland
%PROGRAMFILES(x86)%\GamingWonderland
%USERPROFILE%\AppData\LocalLow\GamingWonderland
%UserProfile%\Local Settings\Application Data\GamingWonderlandTooltab
%LOCALAPPDATA%\GamingWonderlandTooltab
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\fenbipnfkodbfdjlgndbgokhkneidbom
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\hjkdfjgajdjedjpapojndcfhekhbpkjp
%LOCALAPPDATA%\Google\Chrome\User Data\Default\hjkdfjgajdjedjpapojndcfhekhbpkjp
Registry:
HKEY_LOCAL_MACHINE\SOFTWARE\AppDataLow\HKEY_LOCAL_MACHINE\SOFTWARE\GamingWonderland
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.DynamicBarButton.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.FeedManager
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.FeedManager.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.HTMLMenu
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.HTMLMenu.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.HTMLPanel
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.HTMLPanel.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.MultipleButton
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.PseudoTransparentPlugin.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.Radio
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.Radio.1
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.RadioSettings
HKEY_LOCAL_MACHINE\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.RadioSettings.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ScriptButton
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ScriptButton.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.SettingsPlugin
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.SkinLauncher.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.SkinLauncherSettings
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.SkinLauncherSettings.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ThirdPartyInstaller
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ThirdPartyInstaller.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ToolbarProtector
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.ToolbarProtector.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GamingWonderland.XMLSessionPlugin.1
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\0c7bac04-8f5d-4bbd-956a-34fafa547752
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\16fbdf8c-476f-4d6b-8009-84471903cf96
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\82bacdc9-afce-41ee-92f5-b54f6db45a1c
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\8b70e4e8-100a-4b4f-b928-6d8126b730bb
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\c1151fbb-ef5b-4a2b-91e4-e8776f091f37
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\82bacdc9-afce-41ee-92f5-b54f6db45a1c
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\8b70e4e8-100a-4b4f-b928-6d8126b730bb
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\c1151fbb-ef5b-4a2b-91e4-e8776f091f37
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\e65f4fe3-b8a9-408f-9e8d-37689e565618
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\ab5d199e-9659-47a2-930b-fc3b69061353
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\f4d7584b-6643-4bc7-8e24-17c3258dc5ef
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\26A73C38-B71A-4D3A-80B7-E010420DA1E7
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\1a30aa28-2fc6-4360-9e14-cfa627d51b6c
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Ext\PreApproved\08fbcb5f-de4f-49e0-977e-e4269f4d7206
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\f4d7584b-6643-4bc7-8e24-17c3258dc5ef
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\99c8d756-4d22-4d0f-898a-34a232884ce1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\75faf80f-56c7-4bb3-b825-39d0a706b5a4
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\PreApproved\4c297ddf-0a36-4b17-b8fa-0c0395f2c5bc
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\MozillaPlugins\@GamingWonderland.com/Plugin
HKEY_LOCAL_MACHINE\SOFTWARE\MozillaPlugins\@GamingWonderland.com/Plugin
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run, value: GamingWonderland Search Scope Monitor
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GamingWonderlandbar Uninstall Firefox
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GamingWonderlandbar Uninstall Internet Explorer
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, value: GamingWonderland Search Scope Monitor
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\GamingWonderland
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Google\Chrome\Extensions\hpflffkopmgalfhfholanbnhoiblmajp
HKEY_LOCAL_MACHINE\SOFTWARE\Google\Chrome\Extensions\hpflffkopmgalfhfholanbnhoiblmajp
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Toolbar, value: a899079d-206f-43a6-be6a-07e0fa648ea0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Toolbar, value: a899079d-206f-43a6-be6a-07e0fa648ea0
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GamingWonderland Chrome Extension Uninstall
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\SearchScopes\3d29c02b-bf3e-4d3b-8a7a-e0e7d0f6dbab
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\3d29c02b-bf3e-4d3b-8a7a-e0e7d0f6dbab
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\c5ce0d8e-0300-4a17-a89c-6cc8078348ad
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\c5ce0d8e-0300-4a17-a89c-6cc8078348ad
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\DOMStorage\free.gamingwonderland.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\DOMStorage\gamingwonderland.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Approved Extensions, value: 7C8F8FE5-9785-4F74-BCF8-895EF9752D97
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Approved Extensions, value: A899079D-206F-43A6-BE6A-07E0FA648EA0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Approved Extensions, value: AB5D199E-9659-47A2-930B-FC3B69061353
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, value: GamingWonderland EPM Support
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run, value: GamingWonderland EPM Support
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\DOMStorage\gamingwonderland.dl.myway.com

 The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.
The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.

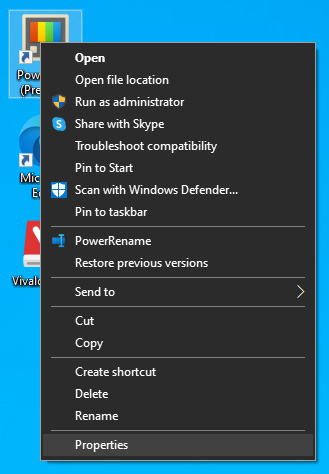 The application settings screen will open, in upper tabs locate Compatibility and left-click on it.
The application settings screen will open, in upper tabs locate Compatibility and left-click on it.
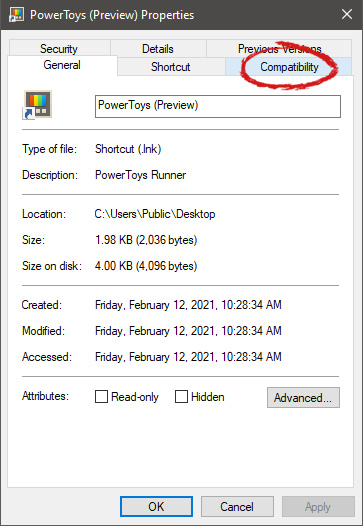 After the click, you will find yourself in application compatibility settings.
After the click, you will find yourself in application compatibility settings.
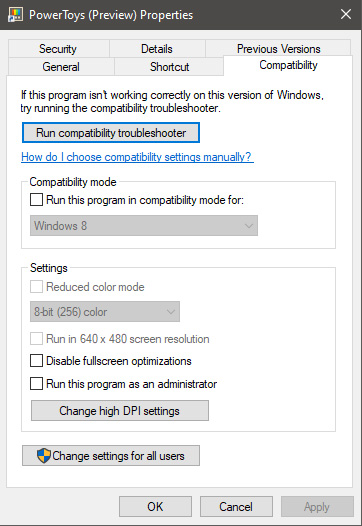 In this window, you will face different options to run the chosen application in various modes in order to make it run. How settings are self-explanatory and different applications will need different settings sadly we can not cover them all but your safest bet is to run them in an environment where they have worked.
For example, if the application was working fine in Windows XP and required administrator privileges, check Run this program as an administrator and Run this program in compatibility mode for Windows XP.
In this window, you will face different options to run the chosen application in various modes in order to make it run. How settings are self-explanatory and different applications will need different settings sadly we can not cover them all but your safest bet is to run them in an environment where they have worked.
For example, if the application was working fine in Windows XP and required administrator privileges, check Run this program as an administrator and Run this program in compatibility mode for Windows XP.  Following are proven solutions that will resolve the issue and provide you with a working device.
Following are proven solutions that will resolve the issue and provide you with a working device.
