If you are trying to copy a file but suddenly encountered an error message saying, “An unexpected error is keeping you from copying the file”, then you’ve come to the right place as this post will help you resolve the problem.
This error comes along with another message that states, “Error 0x80070037: The specified network resource or device is no longer available”. This kind of error occurs when the power supply to the external device is weak and causes the device to be disconnecting and reconnecting consistently. To fix this problem, you need to check out the potential fixes provided below.
Option 1 – Try to physically check the USB ports
You need to check the USB ports as there could be some ports that are loose or damaged physically which affects the overall performance of the port. You could also try to change the USB port since modern computers have a variety of USB ports. So if your USB drive supports USB 3.0 or 3.1, make sure that you plug it inside a USB 3.0 or 3.1 ports. If you’re not sure which port, just keep in mind that the USB 3 port is usually blue or you can also use your computer’s documentation or manual as a reference to locate it.
Option 2 – Check the connected cables physically
Aside from the USB ports, you also have to check the physical status of the connected cables because if there are damaged ones, just like with USB ports, it would also affect the overall connectivity of the device with the computer. So if you notice some irregularities in the connecting cable physically, you might have to buy another one and replace it and then see if it fixes the problem or not.
Option 3 – Update or reinstall the Universal Serial Bus Controller driver
Since it could be a driver issue, you can try to update or reinstall the Universal Serial Bus Controller drivers using the Device Manager. Refer to the following steps:
- First, click the Start button and type “device manager”.
- Then click on the “Device Manager” from the search results to open it.
- From there, look for the “Universal Serial Bus controllers” option and then right-click on each one of the USB drivers and select the Update Driver from the menu.
Note: If it is a regular USB drive, then it will be listed as a USB Mass Storage Device but if you have a USB 3.0 device, then look for a USB 3.0 Extensible Host Controller.
- Restart your PC and then click the “Search automatically for updated driver software” option.
Note: If updating the USB Controller drivers didn’t work, you can try to reinstall them instead.
Option 4 – Try connecting to a slower USB port
If connecting your device to USB 3.0 or 3.1 ports didn’t work, you might want to try connecting it to a slower USB port this time. There are times when the device is not capable of supporting the higher power supply from a USB 3.0 or 3.1 port which is why the weak circuits do not work properly. Thus, try connecting your device to a USB 2.0 port and check if your device is now working.
Option 5 – Try to turn off the Power Saving option
You could also try to turn off the Power Saving option to resolve the problem. All you have to do is switch to Power Management after you select the Properties of the USB device and from there, uncheck the “Allow the computer to turn off the device to save power” option. On the other hand, if you are using a laptop and did not use the USB device for a long time, then it could be powered off. This will ensure that the system does not turn off the USB device.
Option 6 – Try to connect your device to another computer
It is also possible that your computer does not support your device. To check that possibility, you can try connecting your device to a different computer and see if it is working without any issues. If it is, then you need to get another device that’s compatible with your computer.
Option 7 – Try to use a different device
You could also try using a different device and connect it to your computer. This will help you figure out if your device is damaged or not. So if the other device you connected is working just fine, then you might have to replace your device with a new one or consult an expert and have it repaired if possible.
Option 8 – Run the Hardware and Devices Troubleshooters
- The first thing you need to do is click on Start and then on the gear-like icon to pull up the window for Settings.
- After opening Settings, look for the Update and Security option and select it.
- From there, go to the Troubleshoot option located on the left-hand side of the list.
- Next, select Hardware and Devices from the list and open the Troubleshooter and run it. Once it is doing its job, wait for it to complete the process and then restart the system.
- After the system restarts, check if the problem’s now fixed. If not, refer to the next option given below.

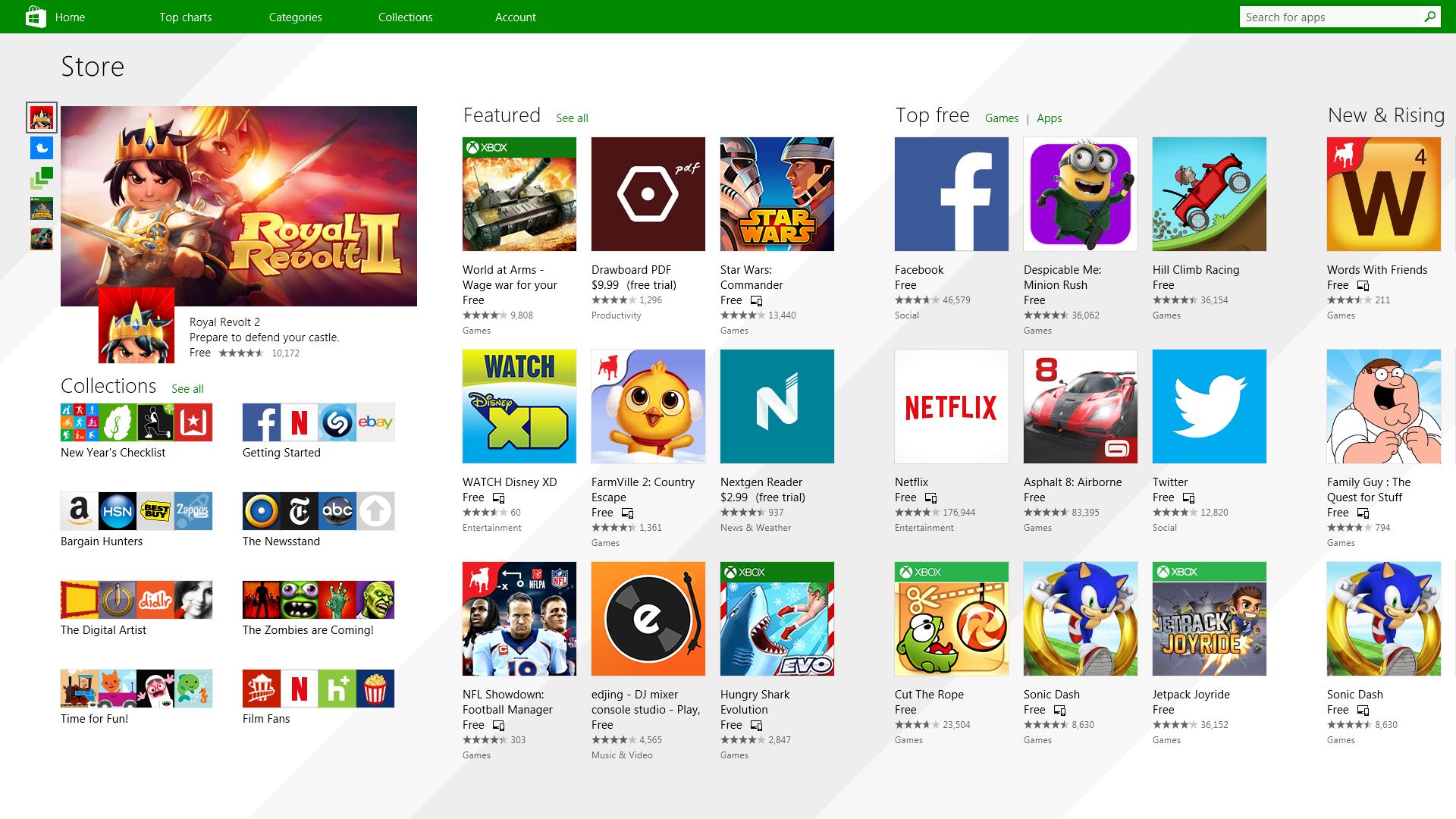 It has officially confirmed that many open source and free applications will be in it like Opera, VLC, discord, Libre office, etc. It seems that Microsoft wants to place its store as one place to go for all of your software needs.
Another great surprise is the coming of Epic games store implementation. It was officially confirmed but not explained in detail, will we have Epic store opened in Windows store or we will only get installer as a package we will see but this is some great news.
As for how it states now, it seems that the Windows store aims to eliminate searching the web for applications and bring them all into one environment with reviews and ratings so you know which one to install and use. It also features a great search engine to find proper applications for your needs.
The new store will come to Windows 10 as well but after all Windows 11 has been mostly released and adopted. So expect it via update in two or three months' time.
It would be great if some larger companies decide to join MS stores like Autodesk, Adobe, the Foundry, etc so you can install everything you need from it but one can only hope.
It has officially confirmed that many open source and free applications will be in it like Opera, VLC, discord, Libre office, etc. It seems that Microsoft wants to place its store as one place to go for all of your software needs.
Another great surprise is the coming of Epic games store implementation. It was officially confirmed but not explained in detail, will we have Epic store opened in Windows store or we will only get installer as a package we will see but this is some great news.
As for how it states now, it seems that the Windows store aims to eliminate searching the web for applications and bring them all into one environment with reviews and ratings so you know which one to install and use. It also features a great search engine to find proper applications for your needs.
The new store will come to Windows 10 as well but after all Windows 11 has been mostly released and adopted. So expect it via update in two or three months' time.
It would be great if some larger companies decide to join MS stores like Autodesk, Adobe, the Foundry, etc so you can install everything you need from it but one can only hope.