From the various report, it is now clear that no one is prone to Ransomware attacks. Cyber-criminals never target any specific field of the user workgroup for this Ransomware attack. But in past few years, it has hugely affected home users, businesses, organizations.
We can say, Ransomware victims come in all shapes & sizes. Many business owners think that they will never be attacked by Ransomware crooks because their business is not so big. But that’s not true.
A huge proportion of Ransomware attacks happened in small sector businesses because of their weak security resistances.
Some leading negative consequences of Ransomware attacks faced by almost every victim are:
- Permanent or temporary loss of proprietary or sensitive information.
- Lots of trouble in performing regular operations.
- Huge financial losses sustain for restoring up your files and systems.
- Latent harm to the reputation of an organization.
- Even making the Ransom payment doesn’t guarantee the safe releasing of your encrypted files.
- Attackers get the victim’s money along with their banking details.
- Getting the decrypting files doesn’t mean malware infection has completely been removed.
Ransomware put a tremendous impact on disturbing business operations and in the end, leads to data loss situations.
Here are some huge impacts of Ransomware attacks on business are:
- Damage or loss of all the crucial information
- In the Ransomware post-attack period Business disrupts a lot.
- Destruction of hostage data, file, and system.
- Business downtime
- Victimized company’s reputation dropdown
- Productivity loss
Apart from the ransom, the cost of downtime because of restricted system access will bring major concerns.
It’s a fact that due to downtime victims may has to pay a cost of ten thousand dollars daily.
As, Ransomware is becoming more and more widespread, so all companies require to brush up on their annual cyber-security goals. Moreover, approach for some appropriate implementations of Ransomware recovery plans and commit sufficient funds in their IT budgets for cyber-security resources.
Among the most effective impact of Ransomware, “data encryption” is very hard to deal with.
Meanwhile, this victim is completely restricted to access any of their encrypted data.
The only way for unlocking these encrypted files is through the decryption key which only belongs to hackers.
Many times, the decryption key is given to the organization, after the payment of the ransom. But there are also some cases when data is not handover to the victim, even after the ransom payment.
The main risk that generates with “operational impact of Ransomware” is on the businesses. Can you just imagine, what will happen if all of a sudden entire services or processes of your business halt down?
Well, this dreadful Ransomware threat is so impactful that it can:
- Close down the entire plant
- Freeze manufacturing control system
- Make other backlogs
All the damages that occur due to downtime can be a major one and can have so many consequences.
A well-organized strategy of backup and recovery will not certainly make the Ransomware attack painless.
As this takes an extensive amount of money and time for data restoration.
Apart from that, the decision of recovering your system using the backup moreover depends on three things:
- First the amount of data loss that is considered acceptable by your business or organization.
- Up to how extent, the impact of Ransomware has spread
- How fast the Ransomware attack was spotted.
However, in many cases, data gets so encrypted that you can’t revert back to the restore point. At that time external backup is considered the best option.
Among the wide-reaching impact of Ransomware “Data loss” is the most effective one. As it starts from little disruption and leads to permanent business failure.
Sometimes data loss in a Ransomware attack leads to disclosure of all your confidential information which ends up in fines and lawsuits.
Attackers always look for backup files and folders after encrypting your system data. So that user can’t retrieve their corrupted file from the backup. Such dreadful activities make this Ransomware threat so profitable and effective.
Victims don’t have any choice left either they have to pay the ransom or they have to face their risk of data loss.



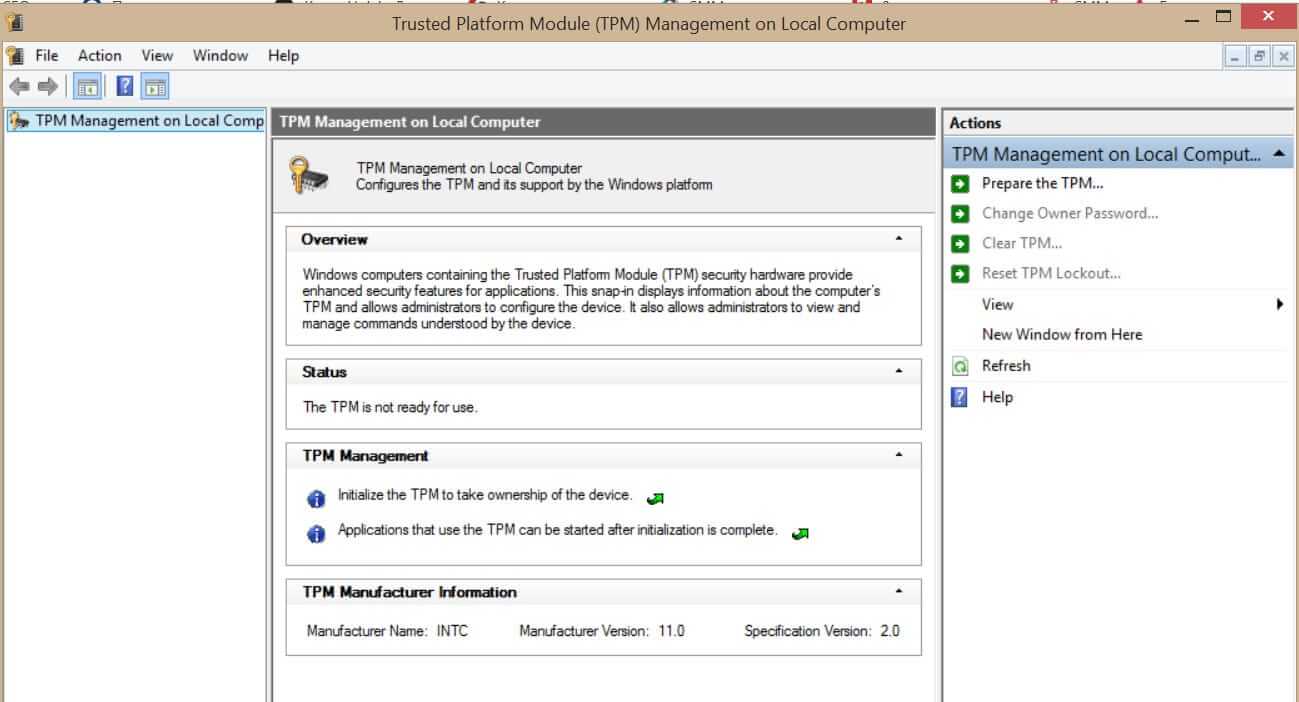 What exactly is TPM?
What exactly is TPM? From the Device Manager choose the troublesome device and right-click on it, choose properties.
From the Device Manager choose the troublesome device and right-click on it, choose properties.
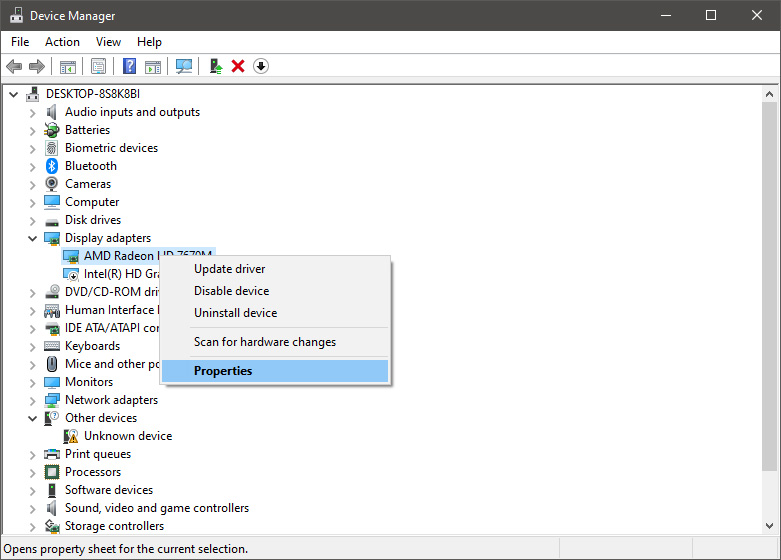 Device properties floating Window will appear.
Device properties floating Window will appear.
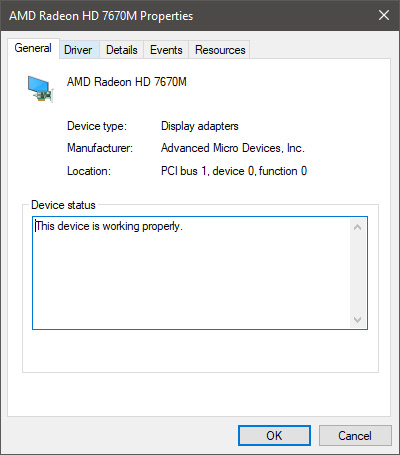 Click on the top tab which says, Driver. From the Driver tab, click on Roll Back Driver.
Click on the top tab which says, Driver. From the Driver tab, click on Roll Back Driver.
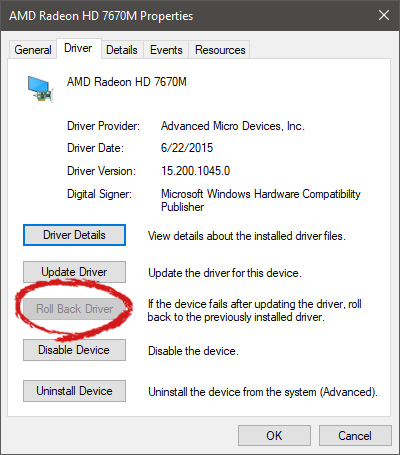 Note that if the device is working properly, the Roll Back Driver button will be greyed out and you will not be able to click on it meaning that chosen device is not the issue. If the device is not working properly and you can click on Roll Back driver, do it, choose the previous version, and reboot your computer.
You can use this method to get back to the previous driver version for any device that is causing issues in your computer.
Note that if the device is working properly, the Roll Back Driver button will be greyed out and you will not be able to click on it meaning that chosen device is not the issue. If the device is not working properly and you can click on Roll Back driver, do it, choose the previous version, and reboot your computer.
You can use this method to get back to the previous driver version for any device that is causing issues in your computer. 
