Afraid of the growing threats online? As you should be. But we’re here to show you what kinds of malware are out there and what you can do to keep them at bay.
Malware definition
Malware comes from the term malicious software. It’s software designed to attack and exploit devices and networks to the advantage of the hacker who made it.
Malware can be transmitted in different ways. Most commonly this happens via infected USB drives, downloadable files or malicious websites. Depending on the type and ultimate goal, the consequences of a malware attack can range from negligible to catastrophic.
What kinds of malware are there?
1. Virus
A virus is typically spread via infected files, websites or links. It’s one of the oldest malware types and one of the most difficult to get rid of. That’s because, once activated, it replicates itself - hence the name.
It can perform different kinds of attacks, depending on what the creator wants to achieve. The main characteristic of a virus is that it really doesn’t show itself until you activate the host. So that’s a scary thought for sure.
2. Adware
Sometimes an ad blocker isn’t enough to fight off unwanted ads. And some of them can, unfortunately, be malicious. They may redirect you to infected sites or prompt downloads of risky files. Even just opening a malicious site can lead to data theft.
So, definitely be careful when clicking around. Even if an ad seems completely legitimate, you can never be too sure.
3. Ransomware
Through ransomware, cybercriminals gain access to a user’s data and use it to extort them for money. Basically, the user is threatened with data deletion or even exposure if a ransom isn’t paid by a specific deadline.
This is a particularly nerve-wracking type of malware. If it targets an individual, it preys upon their sense of anxiety, fear, guilt and even shame. If it targets a business (which is a lot more common), it preys upon not only that business’s profit but also every single one of their customers and their data.
4. Trojans
This type of malware disguises itself very well as a legitimate-looking program. Once you download it, hackers can get full access and control of your device, data and network. They can even be hidden in games, apps and attachments. They cannot self-replicate, though, so we guess that’s… good news?
5. Worms
Worms can replicate, just like viruses, but you don’t need to actually activate the infected program for them to get going. They can be used for various purposes, ranging from data deletion to file encryption to support a ransomware attack.

6. Spyware
Spyware refers to malicious software that stays hidden on your computer and monitors your activity. The best-known type is keyloggers. This can be used to steal sensitive data like passwords and banking information.
7. Rootkits
Rootkits are among the most dangerous types of malware. They allow administrative access and full control of a device, which lets hackers continue hijacking all your data and monitoring your activity without your knowledge.
8. Botnets
Botnets are networks made up of bots - computers that cybercriminals have infected with malicious software. Bots and botnets give hackers remote access to users’ devices and allow them to spy on your camera, take screenshots, memorize passwords and launch Distributed Denial of Service attacks. This one truly makes your hair stand on end.
What can you do about it?
You know the old adage - better safe than sorry. And trust us, malware attacks are such a pain in the you-know-what that you really don’t want to be sorry.
Luckily, there are simple solutions that can shield you from most digital threats these days. What you want to be looking at is a solid antivirus program. Well, technically, you need an antimalware program, but since the latter evolved from the former, we still mostly refer to them as antivirus software.
The majority of antimalware programs these days don’t just shield you from potential risks online, but include additional features as well. For example, some Bitdefender antivirus packages also include parental control and a VPN. And Bitdefender is not just for PCs either - it offers protection for your beloved iPhone or Android as well. You can throw in a password manager in there too, for an additional layer of security.

If you aren’t too concerned about all these various threats or feel like you don’t need extra security, you can at least take a step to protect your information from being exposed to lurking cybercriminals as you’re browsing. This can be done through a good VPN like Surfshark, which hides your identity in the digital space and prevents your data from being tracked.
Choosing the right protective software is especially important if you have children with access to the Internet, since they’re unfortunately even more vulnerable to malicious attacks. If you aren’t sure what the right kind of antimalware program is right for you, you can reach out to us and we’ll be happy to help keep your entire household or office digitally secure.
The bottom line
The truth is that there’s no way to be 100% protected in the online world. Hackers are constantly coming up with new ways to infiltrate our devices. But malware-battling software evolves along with them and there’s still plenty you can do to keep risks away. Stay safe!

 This is a very interesting decision by Microsoft and I fully support it, this time users will be able to pay less and to choose only applications that they need instead of paying for the whole package and not using it.
This is a very interesting decision by Microsoft and I fully support it, this time users will be able to pay less and to choose only applications that they need instead of paying for the whole package and not using it.  When it comes to computer peripherals first thing that comes to people's minds is probably Mouse and Keyboard. Also when discussing peripherals brands, Razer is not a stranger and over the years it has built its name and cult following.
Razer’s mechanical keyboards have been always in the upper field of quality and trust from users and Huntsman is no different.
When it comes to computer peripherals first thing that comes to people's minds is probably Mouse and Keyboard. Also when discussing peripherals brands, Razer is not a stranger and over the years it has built its name and cult following.
Razer’s mechanical keyboards have been always in the upper field of quality and trust from users and Huntsman is no different.
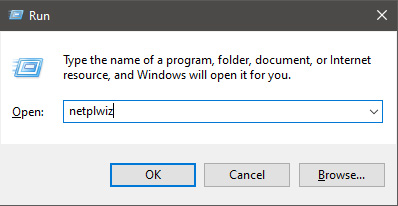
 In the dialog, type in netplwiz and press ENTER.
In the dialog, type in netplwiz and press ENTER.
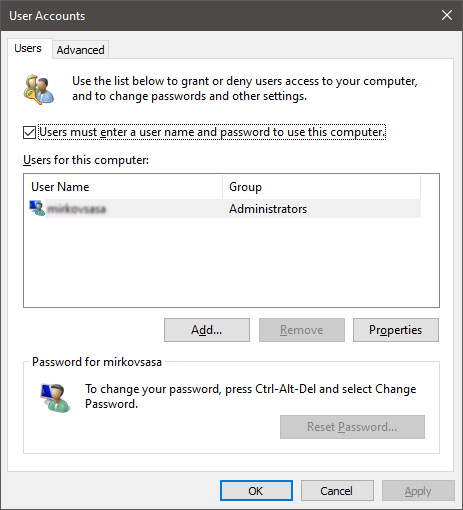
 You will find yourself in the User Accounts window, inside deselect Users must enter a user name and password to use this computer. Press OK
You will find yourself in the User Accounts window, inside deselect Users must enter a user name and password to use this computer. Press OK
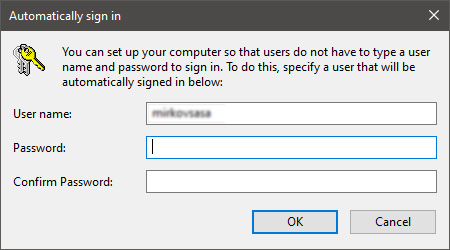
 Sign in the window will pop up where you will have to type in your password and confirm it in order to start the feature.
Sign in the window will pop up where you will have to type in your password and confirm it in order to start the feature.
 After typing in your password and confirming it, press OK. That's it, next time you wake your computer from hibernation or turn it ON, you will automatically be greeted with a desktop instead of a Windows login screen.
After typing in your password and confirming it, press OK. That's it, next time you wake your computer from hibernation or turn it ON, you will automatically be greeted with a desktop instead of a Windows login screen. 
