What is BuzzDock?
Buzzdock is a browser extension. Buzzdock will be automatically enabled on IE and Chrome following installation, and you may begin using Buzzdock with no further action required. If you elect to optimize Buzzdock performance, the settings preferences of your browser may be adjusted after installation.
This browser extension changes your default search provider to Buzzdock.com custom search. It displays additional unwanted ads, banners & sponsored links on web pages that you visit, and it hijacks your browser home page. This browser extension has been flagged as malware by many anti-virus scanning programs.
About Browser Hijackers
Browser hijackers (sometimes called hijackware) are a type of malicious software that modifies web browser configuration settings without the user’s knowledge or consent. These hijacks are rising at an alarming rate worldwide, and it could be actually nefarious and sometimes dangerous too. They’re created to interfere with web browser programs for many different reasons. In most cases, hijackers are made for the benefit of online hackers often through income generation from forced ad clicks and site visits. Nonetheless, it’s not that harmless. Your online safety is jeopardized and it is extremely irritating. They not only screw up your browsers, but browser hijackers can even modify the computer registry, leaving your PC susceptible to other attacks.
Symptoms of browser hijacker malware
There are several signs that indicate the web browser is hijacked:
1. the home page of your browser is changed unexpectedly
2. you find new unwanted bookmarks or favorites added, typically directed to ad-filled or porn sites
3. The default search page of your web browser is changed
4. you see unsolicited new toolbars added
5. you notice a lot of pop-ups on your computer screen
6. your web browser gets slow, buggy crashes frequently
7. you are prohibited access to specific web pages, including the site of an anti-malware software firm like SafeBytes.
Exactly how browser hijacker finds its way onto your computer system
Browser hijackers infect computer systems in numerous ways, including through a file-share, a drive-by download, or an infected email. They are usually included with toolbars, BHO, add-ons, plug-ins, or browser extensions. Browser hijackers sneak to your computer along with free software downloads also that you unknowingly install alongside the original. Some of the most well-known hijackers are BuzzDock, Babylon Toolbar, Conduit Search, Sweet Page, OneWebSearch, and CoolWebSearch.
Browser hijacking can cause severe privacy problems and even identity theft, affect your web browsing experience by taking command over outbound traffic, substantially slows down your computer by consuming lots of resources, and result in system instability as well.
The best ways to get rid of browser hijackers
Certain browser hijacking can be quite easily corrected by discovering and removing the corresponding malware application from your control panel. However, most hijackers are hard to remove manually. No matter how much you try to get rid of it, it may keep returning over and over again. You should consider doing manual fixes only if you’re a tech-savvy person because there are potential risks associated with fiddling around with the system registry and HOSTS file.
Browser hijackers could be effectively removed by installing and running anti-malware software on the affected PC. Safebytes Anti-Malware can counter relentless browser hijackers and provide you proactive computer protection against all kinds of malware. Together with anti-malware, a system optimizer program, similar to Safebytes Anti-Malware, can help you correct registry errors, remove unwanted toolbars, secure online privacy, and enhance overall system performance.
Find Out How to Get rid of Malware that is Blocking Websites or Preventing Downloads
Malware could cause all sorts of damage when they invade your computer, starting from stealing your personal information to erasing files on your PC. Some malware sits in between the computer and the internet connection and blocks a few or all internet sites which you want to visit. It might also block you from adding anything to your system, especially anti-malware applications. So what should you do when malicious software prevents you from downloading or installing Safebytes Anti-Malware? There are a few fixes you can attempt to get around with this problem.
Boot Windows in Safe Mode
The Windows OS includes a special mode called “Safe Mode” where only the minimum required programs and services are loaded. In the event, the malicious software is set to load automatically when the computer starts, shifting to this mode may well prevent it from doing so. To get into Safe Mode or Safe Mode with Networking, press the F8 key while the computer is booting up or run MSCONFIG and find the “Safe Boot” options in the “Boot” tab. After you restart the PC into Safe Mode with Networking, you could download, install, as well as update anti-malware software from there. Right after installation, run the malware scanner to eliminate standard infections.
Use an alternate internet browser to download the anti-malware application
Malicious program code might exploit vulnerabilities in a specific browser and block access to all antivirus software sites. In case you suspect that your Internet Explorer has been hijacked by malware or otherwise compromised by online hackers, the best plan of action would be to switch to an alternate internet browser like Mozilla Firefox, Google Chrome, or Apple Safari to download your favorite computer security program – Safebytes Anti-Malware.
Create a portable USB antivirus for removing malware
Another way is to download and transfer an anti-malware program from a clean PC to run a scan on the affected computer. Adopt these measures to run the antivirus on the affected computer.
1) Download Safebytes Anti-Malware or Windows Defender Offline onto a clean computer.
2) Plug the Thumb drive into the uninfected computer.
3) Double-click the executable file to run the installation wizard.
4) Pick a USB flash drive as the location when the wizard asks you where you intend to install the software. Follow the directions to finish the installation process.
5) Transfer the thumb drive from the uninfected computer to the infected PC.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Run Full System Scan to identify and clean-up up all types of malware.
A Look at the Best AntiMalware Program
If you’re looking to download an anti-malware application for your PC, there are various tools out there to consider however, you just cannot trust blindly anyone, irrespective of whether it is free or paid software. Some of them are excellent, some are ok types, and some will harm your PC themselves! You need to pick a tool that has gained a good reputation and detects not just computer viruses but other types of malware as well. Amongst few good programs, SafeBytes Anti-Malware is the highly recommended program for the security-conscious individual.
SafeBytes anti-malware is a trustworthy tool that not only secures your PC completely but is also quite user-friendly for people of all skill levels. This software could easily detect, remove, and protect your computer from the latest malware threats including spyware, adware, trojan horses, ransomware, worms, PUPs, along with other possibly damaging software programs.
There are numerous great features you will get with this security product. The following are some of the great features included in the software.
Robust Anti-malware Protection: With its advanced and sophisticated algorithm, this malware removal tool can find and eliminate the malware threats hiding within your PC effectively.
Live Protection: SafeBytes gives real-time active monitoring and protection against all known computer viruses and malware. This software will continuously monitor your PC for any suspicious activity and updates itself regularly to keep current with the constantly changing threat landscape.
Website Filtering: Safebytes assigns all websites a unique safety score that helps you to get an idea of whether the webpage you are going to visit is safe to view or known to be a phishing site.
Low CPU and Memory Usage: SafeBytes is really a lightweight application. It consumes an extremely small amount of processing power as it runs in the background so you’re free to use your Windows-based PC the way you really want.
24/7 Online Tech Support: For any technical issues or product support, you could get 24/7 expert assistance through chat and email.
To sum it up, SafeBytes Anti-Malware offers great protection combined with an acceptable low system resources usage with both great malware detection and prevention. You now may understand that this particular software does more than just scan and delete threats from your PC. For optimum protection and the best value for your money, you can’t get better than SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove BuzzDock without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. You will likely also want to reset your browser.
To ensure the complete removal, manually check your hard drive and registry for all of the following and remove or reset the values accordingly. Please note that this is for advanced users only and may be difficult, with incorrect file removal causing additional PC errors. In addition, some malware is capable of replicating or preventing deletion. Doing this in Safe Mode is advised.
The following files, folders, and registry entries are created or modified by BuzzDock
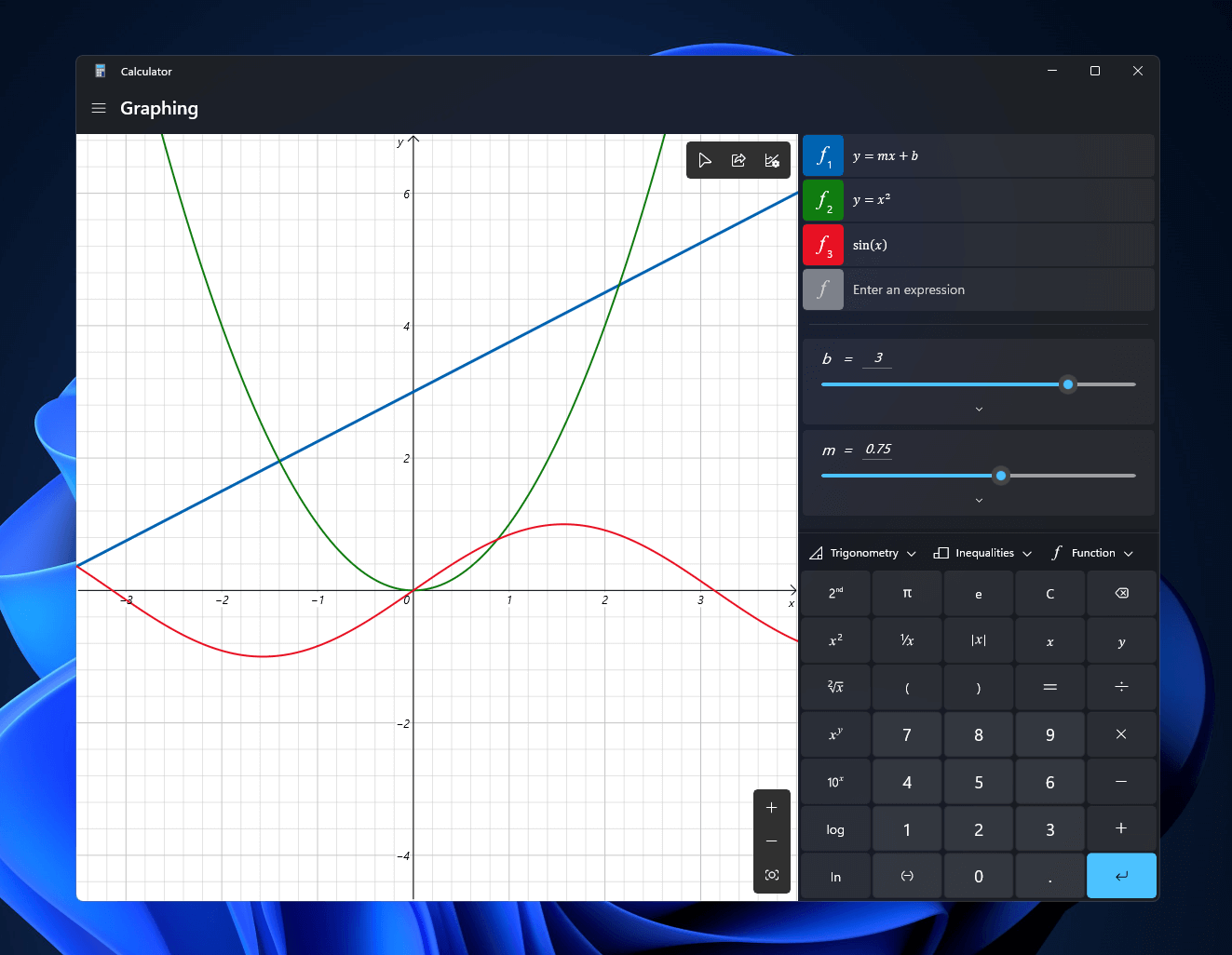 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.


 Therefore we are presenting a couple of solutions that will fix your issue, it is advisable to follow them as presented since they will go from the most common to the more complex one.
Therefore we are presenting a couple of solutions that will fix your issue, it is advisable to follow them as presented since they will go from the most common to the more complex one.