AnytimeAstrology is a browser extension for Google Chrome developed by Mindspark Inc. When installed, this extension will change your default new tab page to a custom search provider called MyWay (search.myway.com).
While browsing the internet with this extension installed, you will see additional ads through your browsing sessions, including but not limited to Sponsored Content, Injected Ads and Pop-up Ads.
While AnytimeAstrology is active it will monitor your browsing habits, recording website visits, clicked links, viewed products, etc. This information is later sent back to Mindspark Ad network servers where it is used to better target additional injected ads into your web pages.
Several anti-virus applications have marked this extension as a Browser Hijacker and it is recommended to remove it from your computer.
About Browser Hijackers
Browser hijackers (also known as hijackware) are a kind of malicious software that modifies web browser configuration settings without the computer owner’s knowledge or approval. These hijacks are raising at an alarming rate globally, and it can be actually nefarious and often harmful too. Browser hijackers could do more than just changing homepages. In most cases, hijackers are created for the benefit of online hackers usually through income generation that comes from forced ad clicks and site visits. While it might seem harmless, these tools are made by malicious people who always try to take advantage of you, so that they can earn money from your naive and distraction. Browser hijackers can also permit other vicious programs without your knowledge to further damage your computer.
Key symptoms that your browser has been hijacked
The following are some symptoms that indicate you’ve been hijacked:
1. your homepage has been reset to some unfamiliar site
2. your browser is constantly being redirected to porn sites
3. default internet search engine is modified
4. you find unwanted new toolbars added
5. you observe a lot of pop-up ads on your screen
6. your browser has become unstable or starts running slowly
7. you can’t visit certain websites such as homepages of antivirus software.
How browser hijacker finds its way to your computer
Browser hijackers could use drive-by downloads or file-sharing websites or perhaps an e-mail attachment in order to reach a targeted computer. They could also come from add-on software, also referred to as browser helper objects (BHO), web browser extensions or toolbars. Browser hijackers sneak into your computer along with free software downloads that you unwittingly install along with the original. An example of some well known browser hijacker includes Conduit, Anyprotect, Babylon, SweetPage, DefaultTab, RocketTab, and Delta Search, but the names are constantly changing.
The existence of any browser hijacker on your computer might considerably diminish the web browsing experience, monitor your internet activities that result in serious privacy issues, produce system stability issues and ultimately cause your PC to slowdown or to an almost unusable condition.
The best ways to remove a browser hijacker
Some hijackers can be simply removed by deleting the free software they came with or by eliminating any extension you have recently added to your system. The sad thing is, the majority of the software applications used to hijack a internet browser are deliberately built to be hard to eliminate or detect. Novice computer users should never attempt for the manual form of removal methods, since it calls for thorough computer knowledge to carry out repairs on the computer registry and HOSTS file.
Installing and running anti-malware application on the affected system will automatically erase browser hijackers and other unwanted applications. SafeBytes Anti-Malware could counter persistent hijackers and give you proactive computer protection against all kinds of malware. Together with the anti-virus tool, a system optimizer, such as SafeBytes’s Total System Care, could help you in removing all linked files and modifications in the registry automatically.
How to Get rid of Malware that is Blocking Websites or Preventing Downloads
Malware could potentially cause a great deal of damage to your PC. Some malware sits in between the computer and the internet connection and blocks some or all websites that you really want to visit. It might also prevent you from adding anything to your PC, especially anti-malware software. If you’re reading this article, you may have got affected by a virus that prevents you from installing a security software like Safebytes Anti-Malware. Follow the instructions below to get rid of malware through alternate methods.
Eliminate malware in Safe Mode
If the malware is set to run immediately when Windows starts, entering safe mode could very well block the attempt. Just the minimum required programs and services are loaded when you start your PC in Safe Mode. To launch your Windows XP, Vista or 7 computer in Safe Mode with Networking, do as instructed below.
1) At power-on/startup, press the F8 key in 1-second intervals. This will invoke the Advanced Boot Options menu.
2) Select Safe Mode with Networking using arrow keys and press ENTER.
3) Once this mode loads, you will have an internet connection. Now, use your internet browser normally and navigate to https://safebytes.com/products/anti-malware/ to download Safebytes Anti-Malware.
4) As soon as the software program is installed, allow the scan run to eliminate trojans and other threats automatically.
Use an alternate web browser to download an antivirus application
Some malware mainly targets particular internet browsers. If this is your case, make use of another browser as it might circumvent the computer virus. If you suspect that your Internet Explorer happens to be hijacked by a virus or otherwise compromised by online hackers, the best plan of action is to switch to a different browser such as Mozilla Firefox, Google Chrome, or Apple Safari to download your favorite security application – Safebytes Anti-Malware.
Make a bootable USB anti-virus drive
To successfully eliminate the malware, you will need to approach the problem of running antivirus program on the affected PC from a different angle. Follow these steps to employ a USB flash drive to fix your infected PC.
1) Download the anti-malware program on a virus-free PC.
2) Insert the pen drive on the same system.
3) Run the setup program by double-clicking the executable file of the downloaded application, which has an .exe file extension.
4) When asked, select the location of the USB drive as the place where you want to put the software files. Follow the onscreen instructions to finish the installation.
5) Remove the pen drive. You can now use this portable antivirus on the affected computer.
6) Double-click the antivirus program EXE file on the thumb drive.
7) Run Full System Scan to detect and clean-up up all types of malware.
Protect Your Computer Against Viruses and Malware With SafeBytes Anti-Malware
Would you like to download the best anti-malware software program for your desktop? There are numerous applications in the market that comes in free and paid versions for Microsoft Windows computers. Some are good ones, some are ok types, while some are simply just bogus anti-malware software which will damage your personal computer themselves! You must pick one that is dependable, practical and has a strong reputation for its malware protection. On the list of recommended software programs is SafeBytes AntiMalware. SafeBytes has a really good history of excellent service, and customers appear to be very happy with it.
SafeBytes antimalware is a highly effective and easy-to-use protection tool which is created for users of all levels of IT literacy. Through its cutting-edge technology, this software will help you protect your PC against infections brought on by different kinds of malware and similar threats, including adware, spyware, computer viruses, worms, trojan horses, keyloggers, potentially unwanted program (PUPs), and ransomware.
There are plenty of amazing features you will get with this security product. Listed below are some of the great features included in the application.
World-class AntiMalware Protection: This deep-cleaning antimalware program goes much deeper than most antivirus tools to clean out your computer system. Its critically acclaimed virus engine detects and disables hard to remove malware that conceals deep within your personal computer.
Active Protection: SafeBytes delivers complete and real-time security for your computer system. They are highly effective in screening and removing numerous threats since they’re continuously improved with new updates and alerts.
Safe Web Browsing: Through its unique safety ranking, SafeBytes tells you whether a site is safe or not to visit it. This will ensure that you’re always certain of your online safety when browsing the web.
Faster Scanning: SafeBytes’s virus scan engine is among the fastest and most efficient within the industry. It's targeted scanning considerably increases the catch rate for malware that is embedded in various PC files.
Lightweight Application: SafeBytes is a lightweight application. It consume a really small amount of processing power as it works in the background so you’re free to use your Windows-based PC the way you really want.
24/7 Premium Support: You can get absolutely free 24/7 technical support from their IT experts on any product queries or PC security concerns.
SafeBytes has created a fantastic anti-malware solution to help you conquer the latest malware threats and virus attacks. You can be sure that your computer system will be protected in real-time as soon as you put this software to use. So if you are searching for the best anti-malware subscription for your Windows-based PC, we suggest the SafeBytes Anti-Malware application.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually get rid of AnytimeAstrology without the use of an automated tool, it may be possible to do so by removing the program from the Windows Add/Remove Programs menu, or in cases of web browser plug-ins, going to the browser’s AddOn/Extension manager and removing it. You will most probably also want to totally reset your browser to its default configuration settings.
Finally, examine your hard disk for all of the following and clean your computer registry manually to get rid of leftover application entries after uninstallation. Please remember that this is for professional users only and may be difficult, with wrong file removal leading to additional system errors. Additionally, some malicious programs have the capability to defend against its removal. You are urged to do this procedure in Windows Safe Mode.
Folders:
C:\USERS\username\APPDATA\LOCAL\AnytimeAstrologyTooltab
C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Extensions\bdcnkkhncapfcngcjkmfkikanomkgnmb\
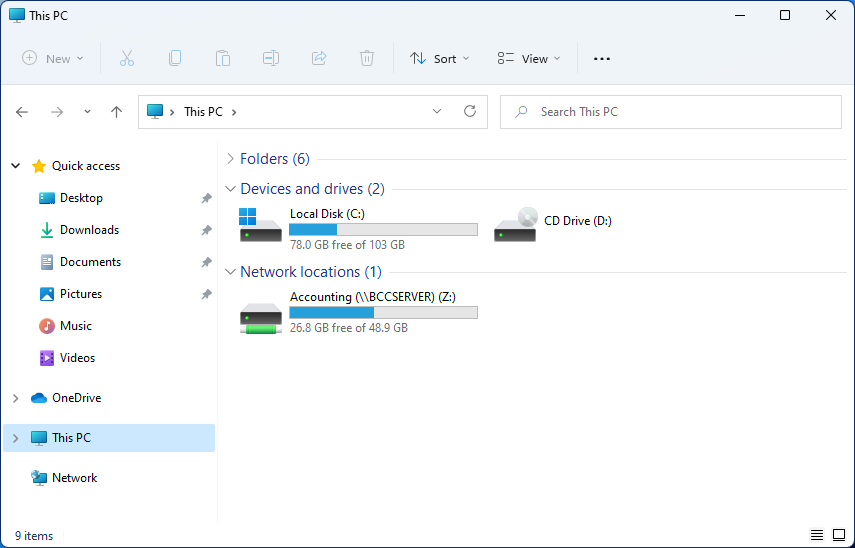 Mapping network drive has many benefits in terms of speed and ease of access of files via network. It lets you access the hard drive over the whole network like it was the hard drive inside your PC case. In order to easily and quickly map a folder as a network drive follow the guide below.
Mapping network drive has many benefits in terms of speed and ease of access of files via network. It lets you access the hard drive over the whole network like it was the hard drive inside your PC case. In order to easily and quickly map a folder as a network drive follow the guide below.




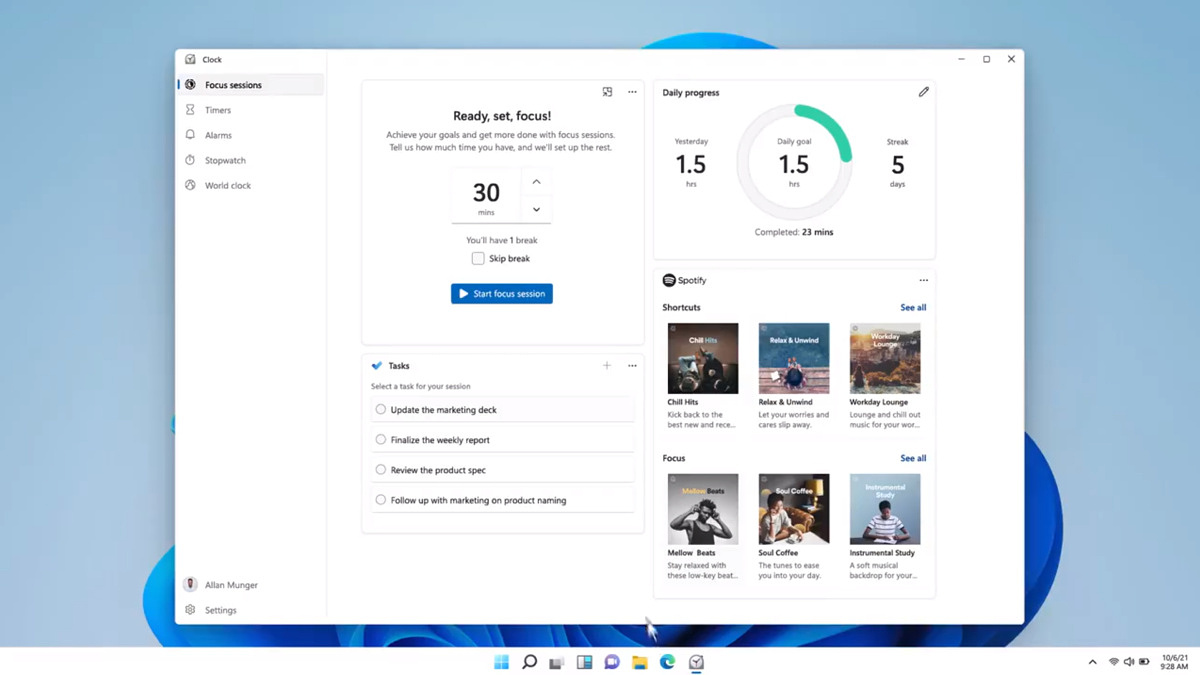 Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
Windows and Devices chief Panos Panay has revealed new focus sessions feature that will be in Windows 11 on his Twitter account today. He himself is referring to it as a game-changer especially with Spotify integration.
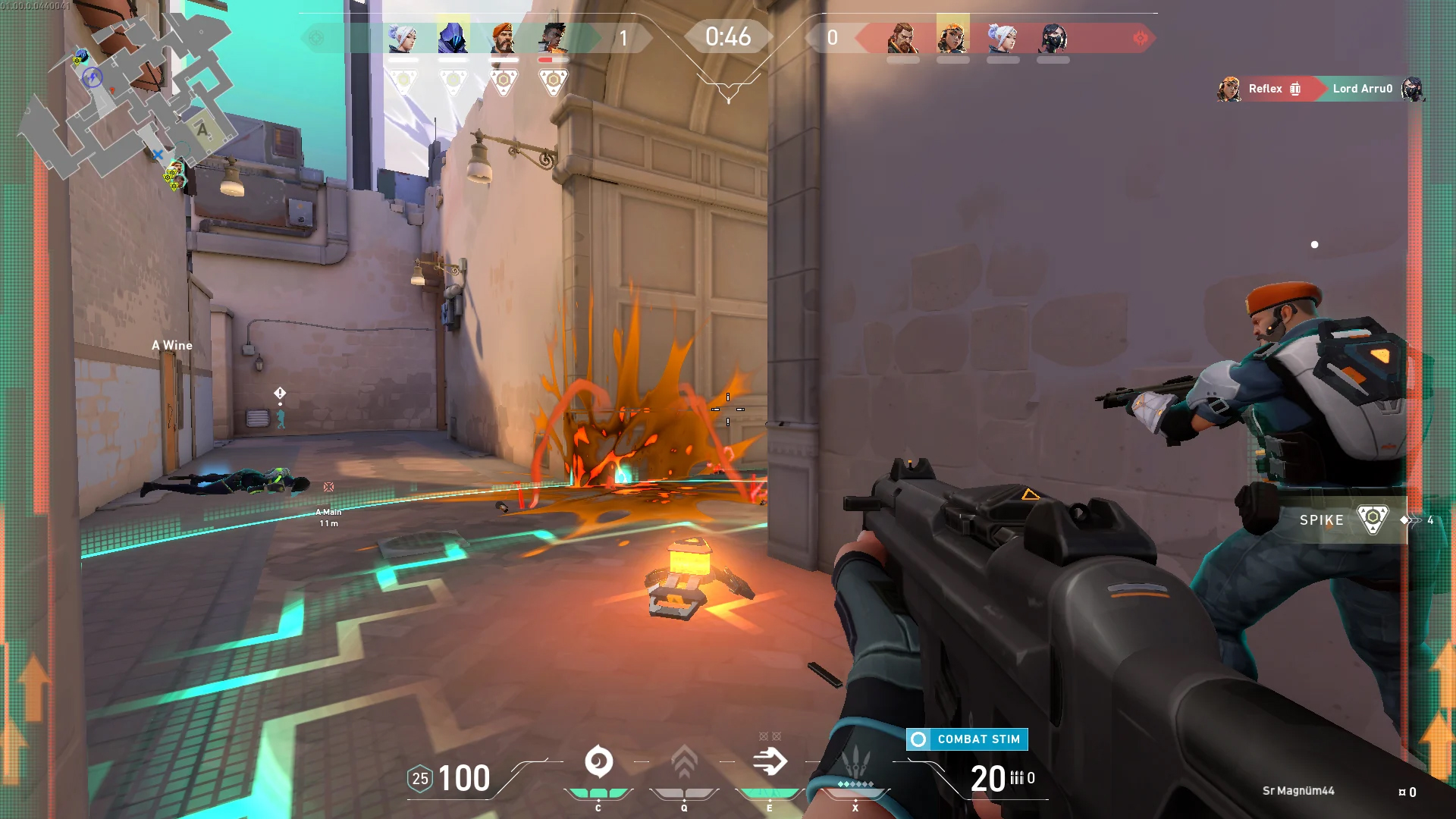 Bad or good news, depending on your view comes from RIOT for their game Valorant. It seems that Riot has decided to enforce Windows 11 TPM 2.0 feature into Valorant running on Windows 11 and there is a rumor that it will be de facto standard and that it will move to Valorant in general no matter on which system it runs.
Furthermore, there is a rumor circling around that other developers are also talking about implementing TPM 2.0 requirements so they can harvest advanced security features of Windows 11 in order to prevent hacks and other cheats in their games.
This is an interesting point to stand on, on one side, sure, advanced features that will prevent cheating and hacking is a great thing. On other hand denying access to many computers that do not support TPM 2.0 and removing them from the game can be a permanent loss of customers and therefore loss of money. It is a risk to be sure and I am not really sure that alienating gamers is a good choice for long-term income, especially when you will be able to install Windows 11 on an unsupported PC as stated by Microsoft.
We will all see how this Riot decision will reflect on their business, as not a big Valorant player myself I am not impacted too much with this decision, but it will be interesting to see if others will indeed go with this trend or they will decide to wait a while until much more PC’s are upgraded.
Bad or good news, depending on your view comes from RIOT for their game Valorant. It seems that Riot has decided to enforce Windows 11 TPM 2.0 feature into Valorant running on Windows 11 and there is a rumor that it will be de facto standard and that it will move to Valorant in general no matter on which system it runs.
Furthermore, there is a rumor circling around that other developers are also talking about implementing TPM 2.0 requirements so they can harvest advanced security features of Windows 11 in order to prevent hacks and other cheats in their games.
This is an interesting point to stand on, on one side, sure, advanced features that will prevent cheating and hacking is a great thing. On other hand denying access to many computers that do not support TPM 2.0 and removing them from the game can be a permanent loss of customers and therefore loss of money. It is a risk to be sure and I am not really sure that alienating gamers is a good choice for long-term income, especially when you will be able to install Windows 11 on an unsupported PC as stated by Microsoft.
We will all see how this Riot decision will reflect on their business, as not a big Valorant player myself I am not impacted too much with this decision, but it will be interesting to see if others will indeed go with this trend or they will decide to wait a while until much more PC’s are upgraded. 