Error 1753 - What is it?
Error 1753 is an RPC endpoint mapper error code. This code is typically displayed as
"EPT_S_NOT_REGISTERED" or sometimes as the hexadecimal value
0x6D9. Error 1735 indicates that there are no more endpoints available from the endpoint mapper.
To understand this better, basically, RPC is an inter-process communication (IPC) method.
This is used by clients and servers for communication purposes. RPC is used by programs to execute programs on a server computer. The perfect example of this is Microsoft Outlook. You communicate with
Microsoft Exchange Server using RPC.
This enables you to send and receive emails. When you use Microsoft Outlook to send emails, your computer sends a message to the server computer in an obscure coding.
The server responds to your computer with another message that contains the results of the executed program. This is all being carried at the backend of the running program.
Integral to this is the endpoint. The endpoint includes the name, port, or a group of ports on a computer that is monitored by the server for incoming client requests. This is a network-specific address to be precise.
The endpoint mapper is the part of the RPC subsystem that is responsible for dynamically assigning endpoints to the server. When this function fails it leads to error 1753 message display. It shows that RPC service is not available.
Solution
 Error Causes
Error Causes
The error code 1753 indicating RPC endpoint mapper service failure is triggered due to multiple reasons. These include:
- Windows registry damage and corruption
- Malfunctioning of the hardware
- Spyware intrusion or viral infections
- Device driver conflicts
Further Information and Manual Repair
This error code may cause a great deal of inconvenience to execute programs that are dependent on the server. It can lower your productivity and performance. To avoid the hassle, it is advisable to repair the error 1753 immediately.
The best way to resolve this error 1753 in seconds is to
download Restoro. By using this repair tool, you can fix the error right away for free without paying hundreds of dollars to a professional expert.
Restoro is a new and innovative PC fixer integrated with an automated algorithm and intuitive technology that enables users to sit back and relax while Restoro runs on the system and detects all PC-related issues in the shortest time.
In just a few clicks you can resolve even the mightiest PC issues like the error code 1753 RPC endpoint mapper problem and resume back to the program in no time.
Why Restoro
It is efficient and user-friendly. Restoro can be used by users of all levels so even if this is your first experience using a repair tool, you don’t have to worry. To operate it, you don’t have to be a computer programmer or have sound technical expertise.
It is simple and very easy to use. The layout is simple and neat complimented nicely with easy navigation and a sophisticated user interface.
Restoro is a high and multi-functional error tool embedded with powerful, performance-driven, and value-adding utilities, all in one.
So, whether the error code 1753 is triggered due to a viral infection on your system or
registry corruption, you don’t have to look for different tools to resolve the error, simply run Restoro to fix the issue right away.
Restoro includes a dynamic registry cleaner that detects all registry issues and wipes out the clutter from the hard disk like junk files, internet history, and invalid entries which is by the way the number cause for registry corruption leading to error 1753.
It clears up disk space and RAM and repairs the misconfigured system files and corrupt registry in seconds thus resolving error 1753.
Restoro also functions as a system optimizer thus boosting the speed and performance of your PC massively and reducing boot time.
In addition to this, it also has a backup feature. This tool is embedded for safety purposes. This feature enables you to create backup files on your PC before you start system repair. This helps you recover data in the event of data loss during system repair.
To get started:
- Click here to download and install Restoro on your system
- After installation, run it to scan for errors like 1753
- Now press the repair tab to resolve
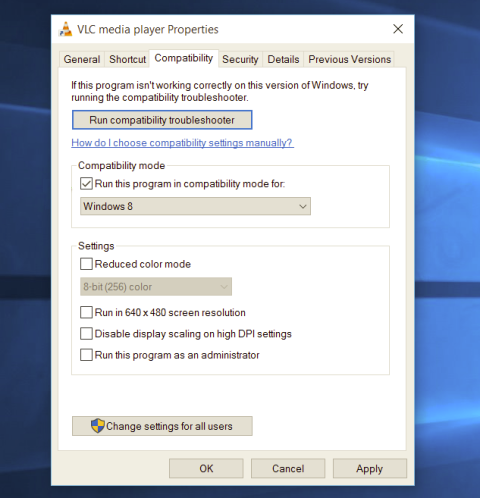 Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
Most of the time running applications with typical settings is fine but from time to time we might have some applications that will require running with administrator privilege in order to work properly. In this case, it is very easy to do it, you just right-click and choose run as administrator.
Although a very easy solution, it can be quite annoying if running the app is on a daily basis or even more times per day. If this is the case then right-clicking and choosing to run as administrator can be a daunting task, sometimes you can even forget to run it like this in heat of work and some unforeseen consequences might occur.
Luckily there is an easy hack so you can open the chosen application each time as an administrator with a simple double click each time.
 Microsoft starting as of today will block its Office 365 users if they are using Internet Explorer or early versions of Edge browsers.
Microsoft starting as of today will block its Office 365 users if they are using Internet Explorer or early versions of Edge browsers.

