The GifsGalore Toolbar from Mindspark Interactive Network, Inc. is proposed to active Web users who like to embed GIFs into their emails and share entertaining GIFs with friends via social media services. The GifsGalore software can be added to your Internet client for free but you need to be using Google Chrome, Internet Explorer or Mozilla Firefox for the GifsGalore Toolbar to be activated.
When installed it hijacks your New tab page and default search engine changing them to search.myway.com. This extension also monitors user browsing activity recording information such as: visited websites, clicked links, viewed products, etc. This information is later used to better target ads.
While browsing the internet with this extension enabled you will see additional pop-up ads, as well as sponsored links and injected ads throughout your browsing session, especially in search results.
About Browser Hijackers
Browser hijacking is actually a form of unwanted software program, often a browser add-on or extension, which causes modifications in web browser’s settings. There are various reasons why you may experience an internet browser hijack; however commercial, advertising, and marketing are definitely the main reasons for their creation. The idea would be to force users to visit specific sites that are aiming to improve their site visitor traffic and generate higher ad earnings. It could seem naive, but most of these sites are not legitimate and could present a serious risk to your online safety. Browser hijackers can even let other vicious programs without your knowledge further damage the computer.
Find out how to identify a browser hijack
When your web browser is hijacked, the following can happen: the browser’s homepage is modified; bookmark and the new tab are also changed; the default search engine has been changed and your browser security settings have been lowered without your knowledge; you see unwanted new toolbars added; unstoppable flurries of popup ads appear on your computer screen; your web browser gets sluggish, buggy, crashes very often; you are prohibited access to particular web pages, including the site of an anti-malware software developer like SafeBytes.
How browser hijacker finds its way onto your computer system
Browser hijackers might use drive-by downloads or file-sharing networks or perhaps an email attachment to reach a targeted computer. They may also come from any BHO, browser extension, toolbar, add-on, or plug-in with malicious purpose. Other times you might have unintentionally accepted a browser hijacker as part of an application package (usually freeware or shareware). Examples of well-known browser hijackers are Fireball, CoolWebSearch. save, Ask Toolbar, RocketTab, and Babylon Toolbar.
Removal
Some browser hijacking could be quite easily reversed by discovering and removing the corresponding malware software from your control panel. Yet, certain hijackers are far harder to find or eliminate since they might get themselves associated with some crucial computer files that enable them to operate as a necessary operating system process. Additionally, manual removals demand deep system knowledge and therefore can be a very difficult job for novices.
Installing and running an anti-malware program on the affected computer could automatically erase browser hijackers and other malicious applications. Safebytes Anti-Malware has a sophisticated anti-malware engine to help you prevent browser hijacking in the first place, and mop up any pre-existing problems. And use a PC optimizer, like Total System Care, to get rid of all related files in the registry and repair browser issues.
What you can do if Malware Stops You From Downloading Or Installing Anything?
All malware is bad, but certain types of malware do a lot more damage to your computer than others. Some malware is created to restrict or prevent things that you want to do on your PC. It may well not let you download anything from the internet or stop you from accessing some or all websites, particularly the antivirus websites. If you’re reading this article, you may have infected by a virus that stops you from installing security software such as Safebytes Antimalware on your PC. There are some actions you can take to circumvent this problem.
Remove malware in Safe Mode
The Windows OS includes a special mode known as “Safe Mode” in which just the bare minimum required programs and services are loaded. If the malware is obstructing internet access and affecting the computer, launching it in Safe Mode allows you to download anti-virus and run a scan whilst limiting possible damage. To enter into Safe Mode or Safe Mode with Networking, press the F8 key while the computer is starting up or run MSConfig and find the “Safe Boot” options in the “Boot” tab. After you restart into Safe Mode with Networking, you can download, install, as well as update the anti-malware program from there. At this point, you could run the antivirus scan to remove computer viruses and malware without any interference from another application.
Download the security software using an alternate web browser
Web-based viruses can be environment-specific, aiming for a particular browser or attacking specific versions of the browser. If you are not able to download the anti-malware software program using Internet Explorer, it means the virus could be targeting IE’s vulnerabilities. Here, you should switch over to a different browser like Firefox or Chrome to download the Safebytes Anti-malware program.
Install and run antivirus from your USB drive
Another solution is to create a portable anti-malware program onto your USB stick. Adopt these measures to run the antivirus on the affected computer system.
1) Make use of another virus-free computer to download Safebytes Anti-Malware.
2) Plug the Thumb drive into the uninfected computer.
3) Double click on the executable file to run the installation wizard.
4) Select flash drive as the place when the wizard asks you where you wish to install the software. Do as instructed on the screen to finish up the installation process.
5) Now, transfer the USB drive to the infected computer system.
6) Double click the Safebytes Anti-malware icon on the thumb drive to run the software.
7) Click on “Scan Now” to run a complete scan on the affected computer for malware.
How SafeBytes Anti-Malware Keep your Computer Virus Free
If you’re planning to purchase anti-malware for your desktop, there are plenty of brands and utilities for you to consider. A few of them are good but there are lots of scamware applications that pretend as legit anti-malware programs waiting around to wreak havoc on your computer. You need to go with a tool that has obtained a strong reputation and detects not only viruses but other kinds of malware as well. Amongst few good applications, SafeBytes Anti-Malware is the strongly recommended software program for the security-conscious individual.
SafeBytes anti-malware is a trusted tool that not only protects your PC completely but is also extremely user-friendly for people of all ability levels. With its cutting-edge technology, this application can help you remove multiples types of malware which include viruses, trojans, PUPs, worms, ransomware, adware, and browser hijackers.
SafeBytes anti-malware provides a myriad of enhanced features that sets it aside from all others. Below are a few of the good ones:
Robust, Anti-malware Protection: Built upon a greatly acclaimed anti-virus engine, this malware removal tool can identify and remove several stubborn malware threats like browser hijackers, PUPs, and ransomware that other common antivirus software will miss.
Live Protection: SafeBytes gives you round-the-clock protection for your personal computer restricting malware intrusions instantly. They’re extremely effective in screening and removing numerous threats because they are regularly improved with new updates and alerts.
Web Filtering: SafeBytes inspects the links present on a web page for possible threats and alerts you whether the website is safe to browse or not, through its unique safety ranking system.
Fast Scan: SafeBytes’s virus scan engine is one of the quickest and most efficient in the industry. It's targeted scanning greatly increases the catch rate for viruses which is embedded in various computer files.
Very Low CPU and RAM Usage: SafeBytes is a lightweight and easy-of-use anti-virus and anti-malware solution. Since it uses low computer resources, this application leaves the computer power exactly where it belongs to: with you.
24/7 Premium Support: You will get 24/7 technical support to quickly resolve any issue with your security tool.
To sum it up all, SafeBytes Anti-Malware offers superb protection combined with very low system resource usage with both great malware detection and prevention. You now may realize that this particular software does more than just scan and eliminate threats from your computer. You’ll get the best all-around protection for the money you spend on SafeBytes AntiMalware subscription, there isn’t any doubt about it.
Technical Details and Manual Removal (Advanced Users)
To remove GifsGalore manually, go to the Add or Remove programs list in the Windows Control Panel and select the program you want to get rid of. For internet browser extensions, go to your web browser’s Addon/Extension manager and choose the add-on you would like to remove or disable. You’ll probably also want to reset your web browser.
If you choose to manually delete the system files and registry entries, use the following list to make sure you know precisely what files to remove before undertaking any actions. However, editing the registry is usually a difficult task that only experienced users and professionals should try to fix it. Moreover, some malware is capable of replicating or preventing deletion. Carrying out this malware-removal process in Safe Mode is recommended.
Files:
%LOCALAPPDATA%\GifsGaloreTooltab
%UserProfile%\Local Settings\Application Data\GifsGaloreTooltab
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Sync Extension Settings\fnjgjdfhhakkbojkgmiihabbbjhgbchh
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\fnjgjdfhhakkbojkgmiihabbbjhgbchh
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Sync Extension Settings\fnjgjdfhhakkbojkgmiihabbbjhgbchh
Registry:
HKEY_LOCAL_MACHINE\Software\[APPLICATION]\Microsoft\Windows\CurrentVersion\Uninstall..Uninstaller
GifsGaloreTooltab Uninstall Internet Explorer
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry\DOMStorage\gifsgalore.dl.tb.ask.com
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry\DOMStorage\gifsgalore.dl.myway.com
HKEY_CURRENT_USER\Software\GifsGalore









 For many people that are playing online games, this is not such a big deal since they always must have the latest version in order to play their games but for other ones, this has arrived as a bit of a problem. Many people preferred older game versions since often updates can change certain mechanics inside the game making it different as an experience or introduce some elements that not everyone likes.
So far, people could use the steamDB site to find depo of the game versions you would like to play and download it but if this beta code goes live that will not be an option anymore. Now, playing old games without updates could also be used for nostalgic reasons and these people have also been cut off with this update.
It is important to point that update is still in beta client only but users have already started to voice their opinions asking Valve not to place it live. In the end, it will all depend on Valve’s decision will they listen to their customers or decide to push updates on live service.
For many people that are playing online games, this is not such a big deal since they always must have the latest version in order to play their games but for other ones, this has arrived as a bit of a problem. Many people preferred older game versions since often updates can change certain mechanics inside the game making it different as an experience or introduce some elements that not everyone likes.
So far, people could use the steamDB site to find depo of the game versions you would like to play and download it but if this beta code goes live that will not be an option anymore. Now, playing old games without updates could also be used for nostalgic reasons and these people have also been cut off with this update.
It is important to point that update is still in beta client only but users have already started to voice their opinions asking Valve not to place it live. In the end, it will all depend on Valve’s decision will they listen to their customers or decide to push updates on live service. 
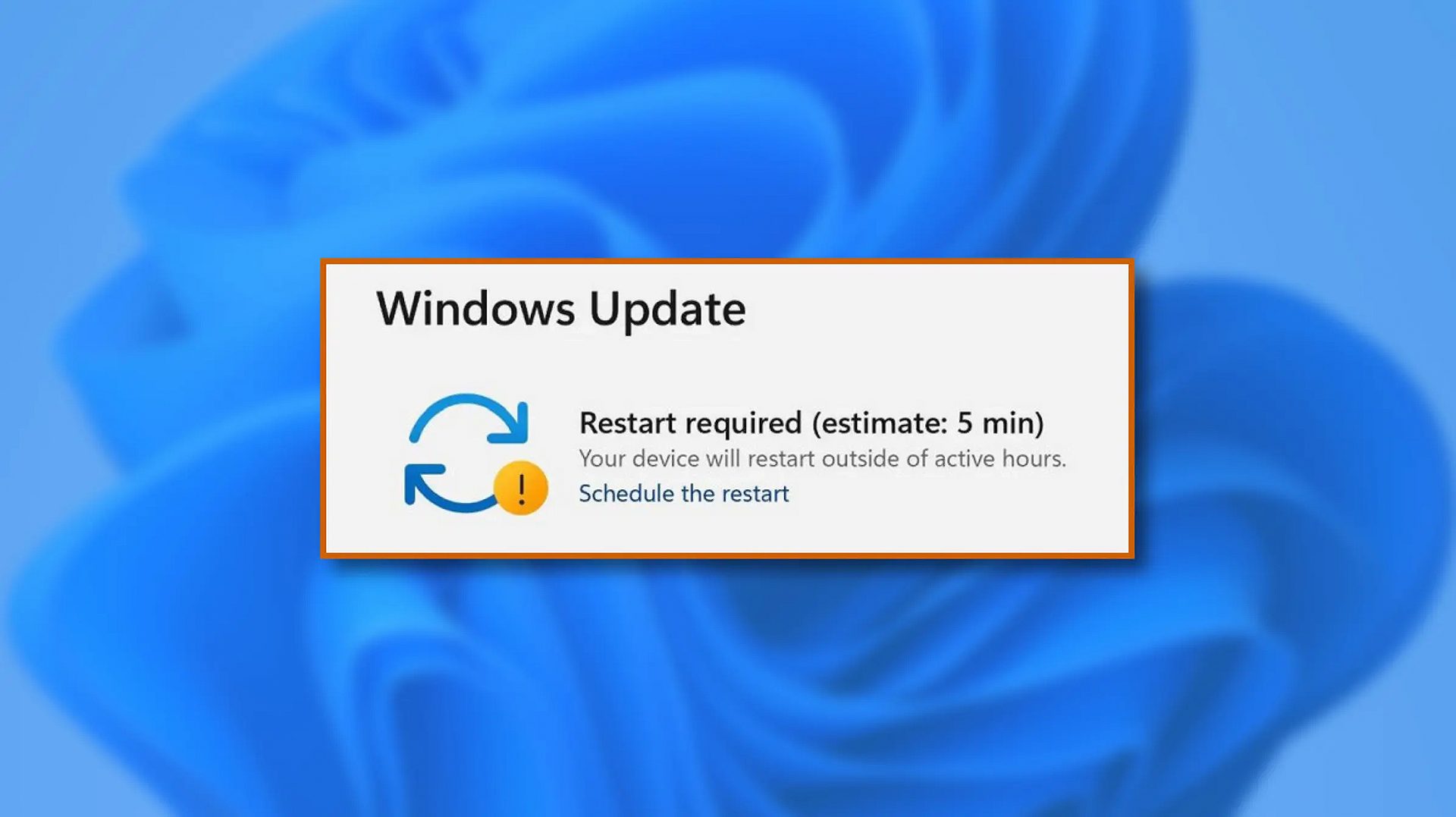 When Windows 11 update is available but you do not wish to restart right away because you are in the middle of using a computer, you can schedule a restart for up to 7 days. It is very easy and we will show you how to do it.
When Windows 11 update is available but you do not wish to restart right away because you are in the middle of using a computer, you can schedule a restart for up to 7 days. It is very easy and we will show you how to do it.
 Before we move to the article I just want to say that technically there are no random crashes, there is always a reason why the system hangs up, why you received blue screen, annoying restarts out of nowhere and many more PC crashes. In this article, we will explore many possible reasons why something may occur and offer you straight forward solution on how to escape the situation and prevent it from happening again.
Without further delay, let's begin:
Before we move to the article I just want to say that technically there are no random crashes, there is always a reason why the system hangs up, why you received blue screen, annoying restarts out of nowhere and many more PC crashes. In this article, we will explore many possible reasons why something may occur and offer you straight forward solution on how to escape the situation and prevent it from happening again.
Without further delay, let's begin:
 The World of Superhero movies has gone through some interesting variations, from good ones to bad ones, from big-budget ones to small ventures, even from large well-known characters to niche ones.
No matter what you think of some of them no one would disagree that since the release of Iron Man and starting Marvel cinematic universe superheroes movies exploded in popularity.
Following the Superhero craze, let’s see what is coming up in comic books transferred to big screens with their release dates.
The World of Superhero movies has gone through some interesting variations, from good ones to bad ones, from big-budget ones to small ventures, even from large well-known characters to niche ones.
No matter what you think of some of them no one would disagree that since the release of Iron Man and starting Marvel cinematic universe superheroes movies exploded in popularity.
Following the Superhero craze, let’s see what is coming up in comic books transferred to big screens with their release dates.

 As in most usual online scams, everything starts with a strange email containing threats and other poorly written and composed speech. At the end of the given email, there would be a link claiming that you, of course, need to read it and follow instructions about the threat, if you click the link it will open a web page where you will have an innocent-looking PDF file with more information about the threat itself.
If you click on a seemingly innocent PDF file it will summon Windows 10's AppInstaller.exe tool, kickstarting a download-and-run process that'll put you in a bad place very quickly. From there, you'll have to deal with the dangers of malware BazarBackdoor, including data and credential theft.
This kind of scam is nothing new but the interesting thing here is that it uses App installer and by clicking on a link you are opening and giving permission for a malicious crook to use it. So, stay safe and do not click on any links from unknown emails no matter what.
As in most usual online scams, everything starts with a strange email containing threats and other poorly written and composed speech. At the end of the given email, there would be a link claiming that you, of course, need to read it and follow instructions about the threat, if you click the link it will open a web page where you will have an innocent-looking PDF file with more information about the threat itself.
If you click on a seemingly innocent PDF file it will summon Windows 10's AppInstaller.exe tool, kickstarting a download-and-run process that'll put you in a bad place very quickly. From there, you'll have to deal with the dangers of malware BazarBackdoor, including data and credential theft.
This kind of scam is nothing new but the interesting thing here is that it uses App installer and by clicking on a link you are opening and giving permission for a malicious crook to use it. So, stay safe and do not click on any links from unknown emails no matter what. 