BigTech platforms Google and Facebook were hit with a series of antitrust lawsuits by the US federal government and states on charges they are operating monopolies and abusing their power.
Below is the status of the cases, as well as government probes of Apple and Amazon in their current states
Two lawsuits against Facebook
In a defeat, Judge James Boasberg said the Federal Trade Commission, which had sued Facebook in December asking that Facebook be forced to sell WhatsApp and Instagram, failed to show that Facebook had monopoly power in the social-networking market, among other problems. However, the FTC could file a new complaint by July 29.
He threw out a related state lawsuit entirely, saying that the attorney's general had waited too long. They are looking at their options.
Four lawsuits against Google
The US Justice Department sued Google in October, accusing the $1 trillion company of illegally using its market muscle to hobble rivals. A trial date was set for September 12, 2023.
A lawsuit by 38 US states and territories accuses Google of abusing its market power to try to make its search engine as dominant inside cars, TVs, and speakers as it is in phones. This was consolidated with the federal lawsuit for purposes of discovery.
Texas, backed by other states, filed a separate lawsuit against Google, accusing it of breaking antitrust law in how it runs its online advertising business.
Dozens of state attorneys general sued Google on July 7, alleging that it bought off competitors and used restrictive contracts to unlawfully maintain a monopoly for its app store on Android phones.
Justice Department investigates Apple
This probe, revealed in June 2019, appears to focus on Apple's app store. Some app developers have accused Apple of introducing new products very similar to existing apps created by other developers and sold in the Apple Store, and then trying to banish the older apps from the store because they compete with Apple's new product. Apple says it seeks to have only the highest-quality apps in the app store.
Justice Department probing Facebook and Amazon
In July 2019, the Justice Department said it was expanding its Big Tech probes to include "search, social media, and some retail services online", an apparent reference to Facebook and Amazon.
Federal Trade Commission on Amazon
In its investigation of Amazon, the FTC is likely looking at the inherent conflict of interest of Amazon competing with small sellers on its marketplace platform, including allegations that it used information from sellers on its platform to decide what products it would introduce.
 So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the
So if you ever wanted to learn about photoshop, maya, substance, unreal engine, or some general skills like sketching, drawing, etc. Now is the perfect time to level up your skills. Drop to the 
 Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.
Hacker group recently came up with claims that they have stolen data from 100 million T-Mobile customers. T-Mobile has responded with confirmation it has been compromised and that over 40 million records were stolen, among them are not just present customers, but anyone who has applied for T-Mobile service as well as past accounts.
 BigTech platforms Google and Facebook were hit with a series of antitrust lawsuits by the US federal government and states on charges they are operating monopolies and abusing their power.
Below is the status of the cases, as well as government probes of Apple and Amazon in their current states
BigTech platforms Google and Facebook were hit with a series of antitrust lawsuits by the US federal government and states on charges they are operating monopolies and abusing their power.
Below is the status of the cases, as well as government probes of Apple and Amazon in their current states
 From the recent blog, Gabriel Weinberg, CEO of DuckDuckGo, has stated:
From the recent blog, Gabriel Weinberg, CEO of DuckDuckGo, has stated:
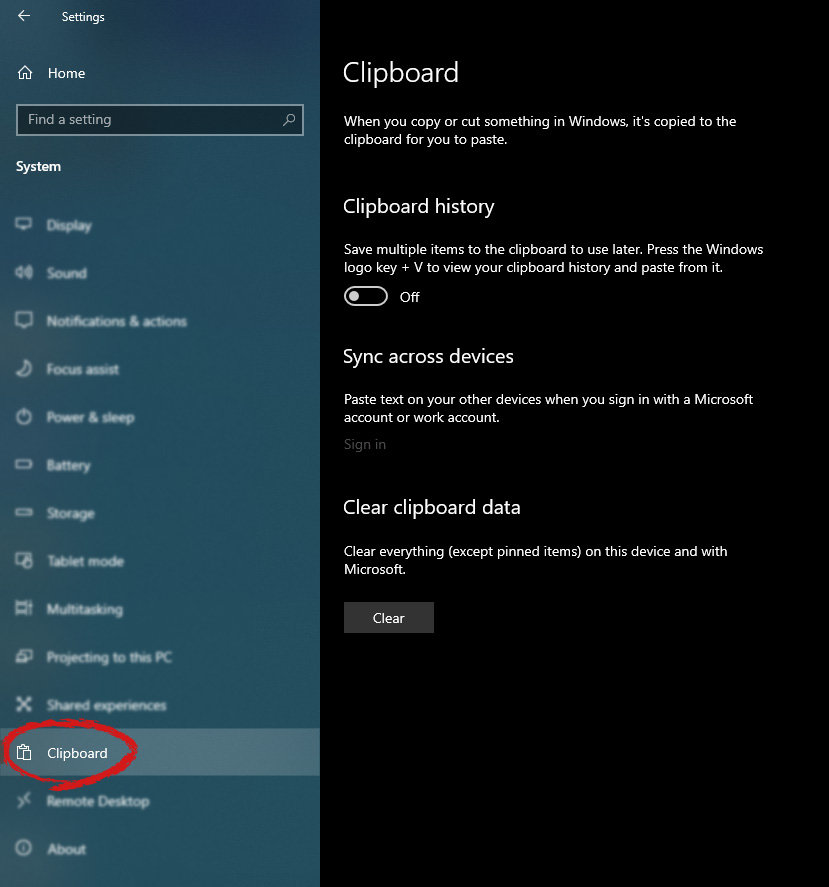
 If you are one of the users that are experiencing this kind of annoyance, we have a solution for you. Follow this guide as presented and repair this annoying error.
If you are one of the users that are experiencing this kind of annoyance, we have a solution for you. Follow this guide as presented and repair this annoying error.
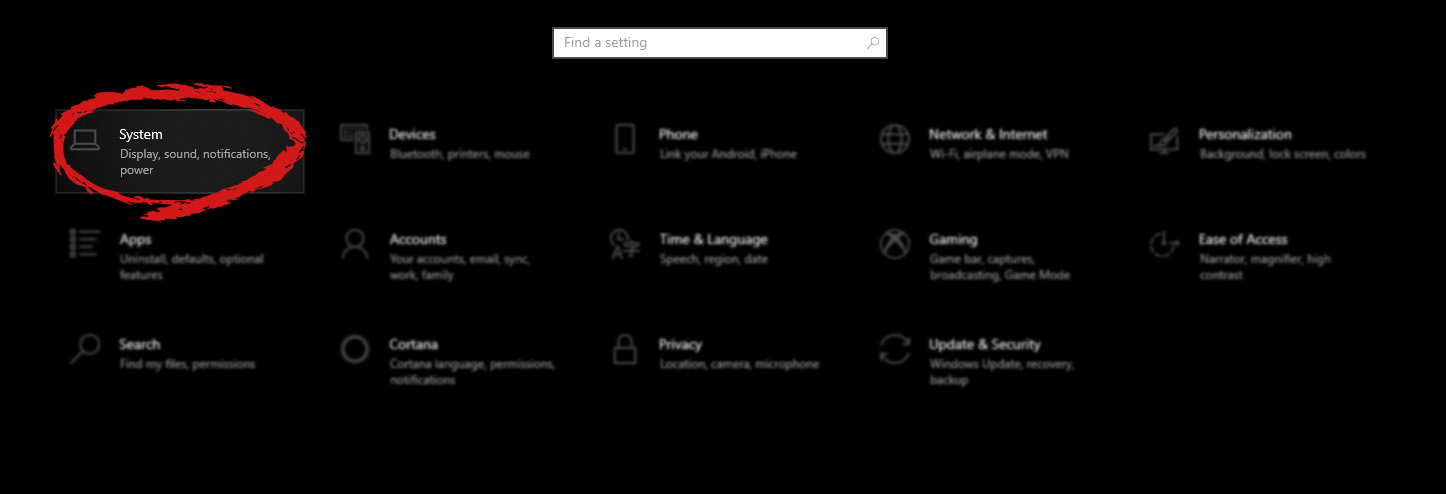 in system dialog click on the clipboard and on the right screen turn ON CLipboard history.
in system dialog click on the clipboard and on the right screen turn ON CLipboard history.