ListenToTheRadioNow is a Browser Extension that allegedly lets you listen to radio from your browser. However, all this extension does is add links to the popular radio stations on your home page.
This extension hijacks your home page and changes your default search provides to MyWay. While running it monitors browsing data from your browser, mining information such as website visits, clicked links, and sometimes even personal information. This information is later used to display targeted ads through your browser.
Several anti-virus scanners have marked this extension as a possible Browser Hijackers, and due to its data mining nature, it is not recommended to keep it on your computer.
About Browser Hijackers
Browser hijacking is a type of unwanted software, commonly a browser add-on or extension, which then causes modifications in the web browser’s settings. Browser hijackers could do more than just modifying homepages. In most cases, browser hijacking is used for earning ad revenue that comes from forced advert clicks and website visits. Even though it may seem naive, all browser hijackers are dangerous and therefore always regarded as security threats. They don’t just ruin your internet browsers, but browser hijackers could also modify the system registry to make your PC susceptible to other malicious programs.
How you can know whether the browser is hijacked?
There are several symptoms of browser hijacking:
1. home-page is changed
2. new bookmarks pointing to porn websites have been added to your bookmarks
3. the default internet search engine and/or the default web browser settings are altered
4. find new toolbars that you did not add
5. unstoppable flurries of popup ads show up on your PC screen
6. webpages load very slowly and often incomplete
7. you have prohibited entry to certain web pages, for example, the site of an anti-malware software firm like SafeBytes.
So how does a browser hijacker infect a PC
A browser hijacker could be installed on your computer or laptop if you visit an infected website, click on an e-mail attachment, or download something from a file-sharing website. They also come from add-on programs, also referred to as browser helper objects (BHO), browser plug-ins or toolbars. Also, some shareware and freeware can put the hijacker inside your computer through “bundling”. A good example of some popular browser hijackers includes Babylon, Anyprotect, Conduit, SweetPage, DefaultTab, Delta Search, and RocketTab, but the names are regularly changing.
Tips on how to get rid of a browser hijacker
Some hijackers can be removed by uninstalling the freeware they were included with or by eliminating any extension you’ve recently added to your computer. However, most hijacking codes are not very easy to eliminate manually, since they go deeper into your operating system. Furthermore, manual removal expects you to perform several time-consuming and tricky actions that are hard to do for new computer users.
Professionals always recommend users to get rid of any malicious software including browser hijacker with an automatic malware removal tool, which is simpler, safer, and faster than the manual removal technique. One of the top tools for correcting browser hijacker malware is SafeBytes Anti-Malware. It can help you eliminate any pre-existing malicious software in your computer and provides you real-time monitoring and protection from the latest internet threats. Employ a PC optimizer along with your anti-malware software to correct various registry problems, remove computer vulnerabilities, and improve your computer overall performance.
Help! Malware Preventing Antivirus Installation And Access To The Internet
All malware is bad, but certain kinds of malware do a lot more damage to your computer than others. Some malware sits in between the computer and the net connection and blocks some or all internet sites that you want to check out. It will also prevent you from installing anything on your system, especially anti-virus applications. If you’re reading this, chances are you’re stuck with a malware infection that is preventing you to download and install the Safebytes Anti-Malware program on your computer. Do as instructed below to get rid of the malware by alternate methods.
Install the anti-malware in Safe Mode
Safe Mode is actually a special, basic version of Windows in which just minimal services are loaded to counteract viruses and other troublesome programs from loading. In the event, the malicious software is set to load automatically when the computer boots, switching to this mode may well prevent it from doing so. To start the computer into Safe Mode, hit the “F8” key on your keyboard just before the Windows logo screen comes up; Or right after normal Windows boot up, run MSConfig, check Safe Boot under Boot tab, and click Apply. Once you’re in Safe Mode, you can attempt to download and install your antivirus software application without the hindrance of the virus. After installation, run the malware scanner to get rid of most standard infections.
Download the security program using an alternate web browser
Some malware mainly targets particular browsers. If this sounds like your case, use another web browser as it could circumvent the virus. If you appear to have a virus attached to Internet Explorer, then switch over to an alternate browser with built-in security features, such as Firefox or Chrome, to download your preferred anti-malware program – Safebytes.
Install and run anti-virus from the Thumb drive
Another solution is to store and operate an anti-malware program entirely from a Pen drive. Do these simple steps to clear up your affected PC using a portable antivirus.
1) Download the anti-malware on a virus-free PC.
2) Insert the USB drive onto the same system.
3) Run the setup program by double-clicking the executable file of the downloaded software, with a .exe file format.
4) Choose the drive letter of the pen drive as the place when the wizard asks you where you would like to install the antivirus. Follow the instructions on the computer screen to complete the installation process.
5) Unplug the pen drive. You may now utilize this portable anti-virus on the affected computer.
6) Double-click the EXE file to open the Safebytes software right from the pen drive.
7) Click the “Scan” button to run a full system scan and remove viruses automatically.
Protect Your PC and Privacy With SafeBytes Anti-Malware
To help protect your laptop or computer from many different internet-based threats, it’s important to install an anti-malware program on your laptop. However, with so many antimalware companies in the marketplace, nowadays it is hard to decide which one you should buy for your laptop. Some of them are great and some are scamware applications that pretend as genuine anti-malware software waiting to wreak havoc on your computer. While looking for an anti-malware tool, choose one that offers dependable, efficient, and complete protection against all known computer viruses and malware. On the list of recommended software by industry analysts is SafeBytes Anti-Malware, a popular security application for Windows computers.
SafeBytes anti-malware is really a powerful, highly effective protection software made to assist users of all levels of computer literacy in finding and removing harmful threats from their computer. Through its cutting-edge technology, this software protects your computer against infections caused by different kinds of malware and similar threats, including spyware, adware, viruses, worms, trojans, keyloggers, ransomware, and potentially unwanted program (PUPs).
SafeBytes anti-malware provides a myriad of advanced features that sets it apart from all others. Below are some of the great features included in the tool.
Robust Anti-malware Protection: Built on a highly acclaimed anti-virus engine, this malware removal application can find and get rid of many obstinate malware threats like browser hijackers, PUPs, and ransomware that other common antivirus applications will miss.
Live Protection: SafeBytes provides complete and real-time security for your computer. This software will continuously keep track of your computer for suspicious activity and updates itself continuously to keep current with the latest threats.
Web Filtering: Through its unique safety rating, SafeBytes informs you whether a site is safe or not to visit it. This will make sure that you’re always certain of your safety when browsing the web.
Faster Scanning: SafeBytes Anti-Malware possesses a multi-thread scan algorithm that works up to five times faster than any other antivirus software.
Lightweight Application: SafeBytes gives you complete protection from online threats at a fraction of the CPU load due to its enhanced detection engine and algorithms.
24/7 Live Expert Support: You will get 24/7 technical support to promptly resolve any issue with your security application.
SafeBytes can keep your PC safe from most advanced malware threats automatically, thus keeping your online experience secure and safe. Malware issues can become a thing of the past when you put this application to use. If you want sophisticated forms of protection features & threat detections, buying SafeBytes Anti-Malware will be worth the dollars!
Technical Details and Manual Removal (Advanced Users)
If you do not wish to use malware removal software and like to get rid of ListenToTheRadioNow manually, you might accomplish this by going to the Windows Add/Remove Programs menu in the control panel and deleting the offending software; in cases of web browser plug-ins, you could remove it by visiting the browser’s Add-on/Extension manager. You will likely also want to reset your web browser.
Finally, check your hard drive for all of the following and clean your Windows registry manually to get rid of leftover application entries after uninstalls. Please keep in mind that only experienced users should attempt to manually edit the system files because removing any single critical registry entry results in a serious problem or even a system crash. In addition, certain malware is capable of replicating or preventing removal. It is highly recommended that you carry out the removal process in Safe Mode.
Files:
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Sync Extension Settings\mlpfmcjpkbijcpegdbkplcddgacjlgpf
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Sync Extension Settings\mlpfmcjpkbijcpegdbkplcddgacjlgpf
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\mlpfmcjpkbijcpegdbkplcddgacjlgpf
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\nhpggpakfcgbidnmlheodkbccemlenag
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\nhpggpakfcgbidnmlheodkbccemlenag
%USERPROFILE%\AppData\Local\Google
Registry:
HKEY_LOCAL_MACHINE\Software\ListenToTheRadioNow\Microsoft\Windows\CurrentVersion\Uninstall..Uninstaller
ListenToTheRadioNow




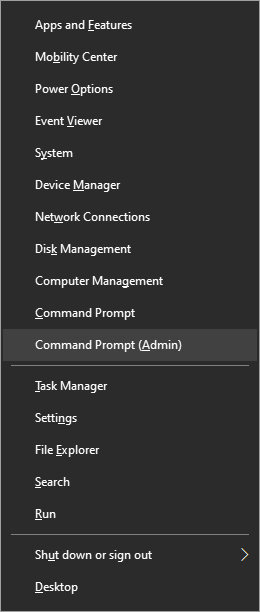
 Once the menu appears, click on Command Prompt (admin)
Once the menu appears, click on Command Prompt (admin)
 Once the command prompt with administrator privileges comes on-screen type in it following string:
Once the command prompt with administrator privileges comes on-screen type in it following string:
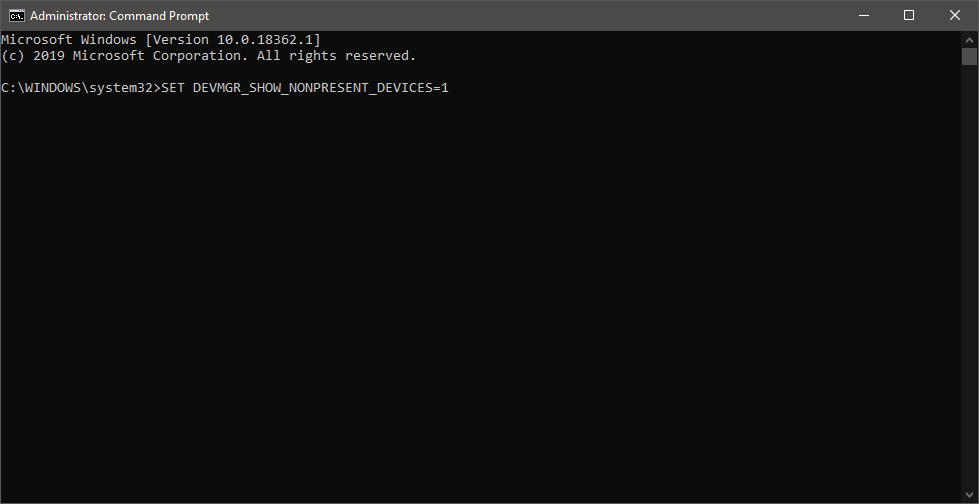 This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
This command will force Windows to show all devices in the device manager including old ones that are not used anymore, but since their drivers are still installed, devices will show up.
When you type command press ENTER.
Once again press WINDOWS + X to show the hidden menu but this time choose the device manager
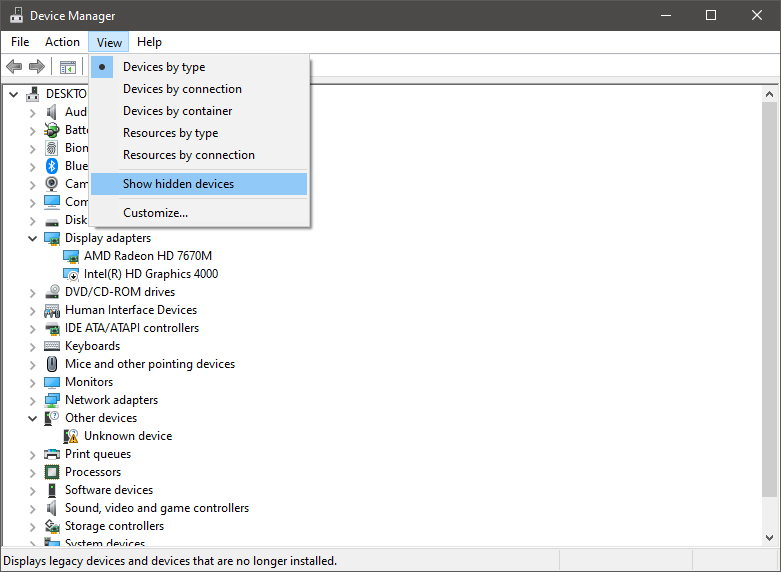
 The device manager will open, go to view > snow hidden devices in order to show unused devices.
The device manager will open, go to view > snow hidden devices in order to show unused devices.
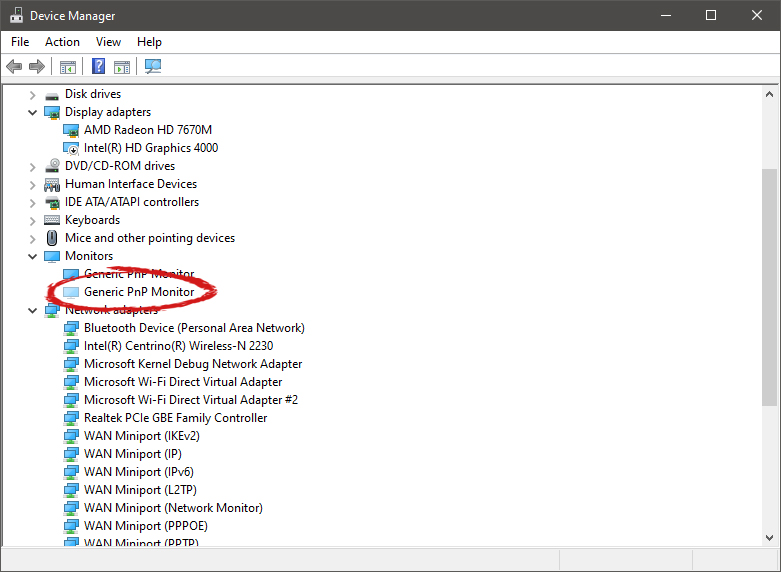 Right-click on the device and click on uninstall device to remove it completely from your system.
Right-click on the device and click on uninstall device to remove it completely from your system.
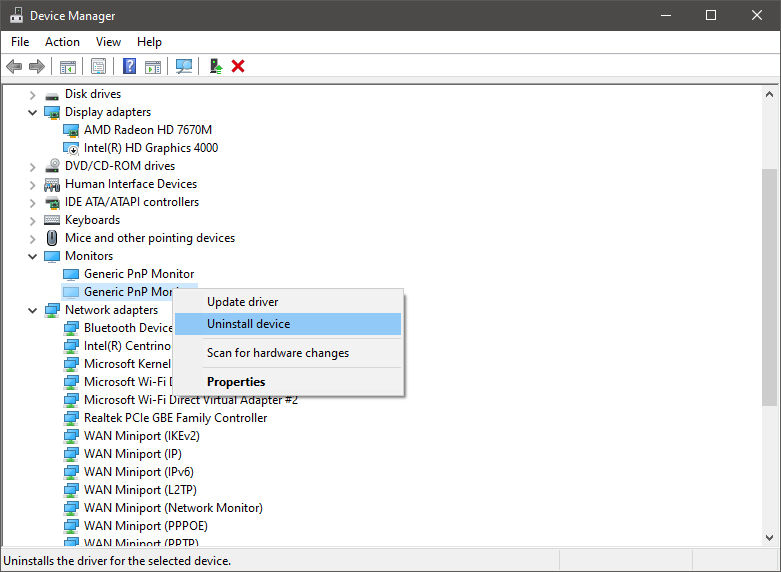 Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly.
Please always be careful when removing devices so you do not remove the device which is being used by mistake and always double-check that you are removing something that you used to have on your system. This method will show all hidden devices even ones that are hidden but crucial to the system working properly. 