Error 0x00000643 - What is it?
This is a Windows Vista printer error. It occurs when you try to use the plug-and-play service to install a WSD printer on your PC.
WSD is the abbreviation for Web Services for Devices.
It is a Microsoft API to simply programming connections to web service enabled devices such as printers, file shares and scanners. The error 0x00000643 code is displayed in the following format:
“Operation could not be completed (error 0x00000643)”
Solution
 Error Causes
Error Causes
The error 0x00000643 may occur due to multiple reasons, including:
- No suitable driver installed for your printer
- A firewall or other security program is too restrictive
- Registry file has invalid entries
- Virus and Trojan
- Outdated system drivers
Further Information and Manual Repair
To resolve this error code on your PC, you don’t have to hire a professional technician and spend hundreds of dollars to perform system repair. You can resolve it all by yourself, even if you are not a computer programmer or lack technical expertise.
Here are some of the easiest and proven methods to fix the error 0x00000643 on your PC:
1. Update Outdated Drivers
This can be done by accessing the ‘Device Manager’. All you have to do is, go to the start menu and type
Device Manager in the start search box. Then click on the Device Manager in the list. On the action menu, click the scan for hardware changes or update the driver.
2. Delete the WSD Port to Resolve Error
Go to the start menu and type printers in the search box. Click printers in the given program list and then click the option add a new printer.
After that, select the existing WSD port and any printer driver. Now delete the printer. The WSD will be deleted automatically. Once this is done, connect the printer to your computer. You will see the plug-and-play service will begin to install the printer again. This process is most likely to resolve the issue and reinstall your printer.
3. Disable Firewall
Sometimes the error may occur if the security programs are too restrictive such as the Firewall. To fix the problem simply disable Firewall.
4. Viral Infection
If the underlying cause of the error is a viral infection, then download a powerful antivirus and run it on your PC. Scan for viruses and delete them.
5. Registry Invalid Entries
If you don’t
clean the registry regularly, this overloads with unnecessary, redundant and obsolete files like cookies, internet history, junk files, bad registry keys and invalid entries. This damages the registry and generates such error codes. Although you can resolve and repair the registry manually, but that method is slight tricky and time consuming. It may require technical expertise.
However, another quick and easy way to clean and restore the registry and resolve error 0x00000643 on your system is to download Restoro. This is a next-generation, advanced, and highly functional PC Repair Tool. It is deployed with an intuitive algorithm and multiple utilities such as a smart registry cleaner, a powerful antivirus, and a system optimizer.
The registry cleaning utility detects all registry issues on your PC, removes invalid entries cluttering the registry, and repairs it right away thereby resolving error 0x00000643.
The antivirus simultaneously detects malware on your PC and removes them while the system optimizer boosts the speed of your computer significantly.
Restoro is bug-free, safe, and efficient. It has simple navigations and a user-friendly interface. This software is compatible with all Windows versions including Vista.
To fix error 0x00000643 on your system in seconds,
click here to download Restoro now!

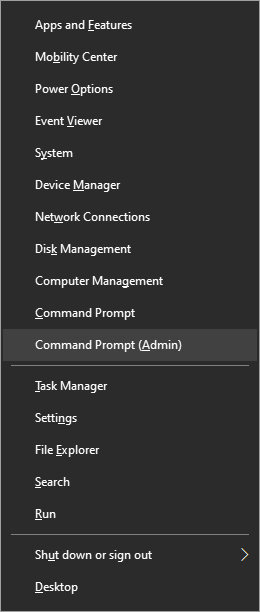
 From the menu choose command prompt (admin)
From the menu choose command prompt (admin)
 In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer
In command prompt type sfc /scannow and press ENTER
Leave the computer for the operation to be completed and Reboot your computer This, of course, means that you will be able to have both Proton and Windows on your device letting you play anything that you wish if the hardware is strong enough. Valve also said that you can launch OS from an SD card! This of course will save space available for games themselves, especially for entry models with less than one available.
All of this information really pushes Deck into the territory of a handheld PC and not just another console and I must admit that this announcement left a smile on my face.
This, of course, means that you will be able to have both Proton and Windows on your device letting you play anything that you wish if the hardware is strong enough. Valve also said that you can launch OS from an SD card! This of course will save space available for games themselves, especially for entry models with less than one available.
All of this information really pushes Deck into the territory of a handheld PC and not just another console and I must admit that this announcement left a smile on my face. 

