Nectar Toolbar is a Browser addon for Internet Explorer developed by AIMIA Coalition Loyalty. This addon changed your default search provider to Yahoo UK. While installed, you might see additional unwanted ads and sponsored links injected in the search results.
From the Author: We all search the web every day for information from handy how-to’s, must know news about shopping. So wouldn’t it be great if you could collect extra Nectar points just for doing something you do already? Like to shop online? Nectar Search will also tell you when you’re on a shopping website (like Argos, Debenhams, Next, Play.com, and Apple) where you can collect points too.
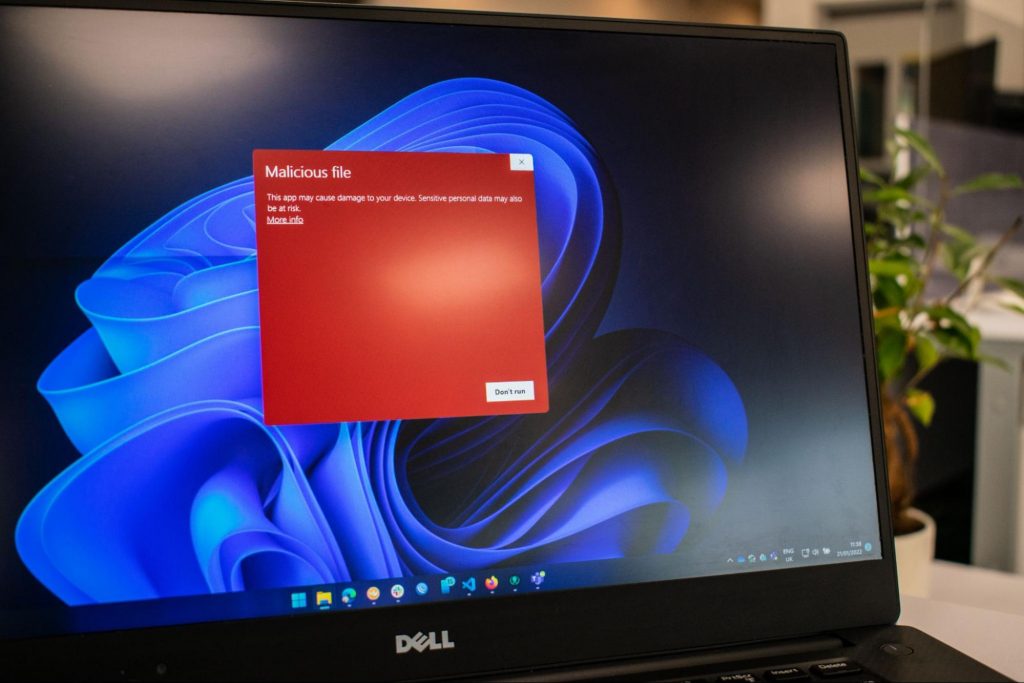
Several anti-virus scanners have marked this addon as a Browser Hijacker and are therefore not recommended to keep on your computer.
About Browser Hijackers
Browser hijacking means a malicious program code has power over and modified the settings of your browser, without your permission. Browser hijackers could do more than just changing home pages. In general, hijackers are developed for the benefit of online hackers often through income generation that comes from forced ad mouse clicks and website visits. Nonetheless, it isn’t that harmless. Your web safety is compromised and it is also really annoying. In a much worst case, your browser could be hijacked to download malicious software that will do a great deal of damage to your computer.
Key symptoms that your browser has been hijacked
When your browser is hi-jacked, the following can happen: you notice unauthorized changes to your internet browser’s homepage; you observe new unwanted favorites or bookmarks added, usually directed to advertisement-filled or porn websites; the default browser configurations have been changed and/or your default web engine is altered; unwanted new toolbars are added to your internet browser; you might notice numerous pop-up adverts on your computer screen; your browser has instability issues or exhibits frequent errors; You can’t access particular websites, especially anti-malware websites.
Exactly how they invade computers
A browser hijacker can be installed on your computer or laptop when you go to an infected site, click on an e-mail attachment, or download something from a file-sharing site. Many internet browser hijackings originate from add-on programs, i.e., browser helper objects (BHO), toolbars, or plug-ins added to browsers to provide them additional features. Other times you might have accidentally accepted a browser hijacker as part of a software bundle (generally freeware or shareware). Popular examples of browser hijackers include CoolWebSearch, Conduit, OneWebSearch, Coupon Server, RocketTab, Delta Search, Searchult.com, and Snap.do.
Browser hijacking can bring about serious privacy problems and even identity theft, affect your web browsing experience by taking control over outgoing traffic, drastically slows down your computer or laptop by depleting lots of resources, and lead to system instability also.
Browser hijacker removal methods
Some browser hijacking can be easily stopped by identifying and eliminating the corresponding malware software from your control panel. However, most hijackers are quite tenacious and require specialized applications to get rid of them. Moreover, browser hijackers could modify the Windows registry so it can be extremely tough to fix manually, particularly when you are not a tech-savvy person.
Browser hijackers can be effectively removed by installing and running an anti-malware application on the affected computer. To get rid of any browser hijacker out of your computer, you could download this particular top-notch malware removal application – SafeBytes Anti-Malware. Together with anti-malware, a PC optimizer software, similar to Total System Care, could help you correct Windows registry errors, remove unwanted toolbars, secure your internet privacy, and stabilize programs installed on your computer.
Find Out How To Install Safebytes Anti-Malware On An Infected Computer system
All malware is bad and the consequences of the damage will vary based on the specific type of malicious software. Certain malware goes to great lengths to stop you from downloading or installing anything on your computer system, particularly anti-virus programs. If you are reading this, you probably have infected by a virus that stops you from installing a security program like Safebytes Anti-Malware. Follow the instructions below to remove malware through alternative methods.
Install in Safe Mode with Networking
Safe Mode is a unique, simplified version of Windows where just essential services are loaded to counteract malware and other problematic programs from loading. In case the malicious software is set to load immediately when the PC boots, switching to this mode could prevent it from doing so. To boot into Safe Mode, hit “F8” key on the keyboard right before Windows logo screen appears; Or right after normal Windows boot up, run MSCONFIG, look over Safe Boot under Boot tab, and then click Apply. Once you are in Safe Mode, you can try to install your anti-malware application without the hindrance of the malware. After installation, run the malware scanner to eliminate standard infections.
Download the anti-malware program in a different internet browser
Some malware only targets particular internet browsers. If this is your case, employ another browser as it might circumvent the computer virus. In case you suspect that your Internet Explorer happens to be hijacked by a computer virus or otherwise compromised by online hackers, the most effective course of action is to switch over to a different web browser such as Mozilla Firefox, Google Chrome, or Apple Safari to download your favorite security application – Safebytes Anti-Malware.
Make a bootable USB anti-virus drive
Another solution is to save and run an anti-malware software program entirely from a Thumb drive. To run antivirus from a thumb drive, follow these simple steps:
1) On a clean computer, install Safebytes Anti-Malware.
2) Plug the USB drive into the clean computer.
3) Double-click the Setup icon of the anti-malware software to run the Installation Wizard.
4) Select the drive letter of the pen drive as the location when the wizard asks you where you would like to install the anti-virus. Follow the onscreen instructions to finish the installation.
5) Now, insert the USB drive into the corrupted PC.
6) Run the Safebytes Anti-malware directly from the pen drive by double-clicking the icon.
7) Simply click “Scan Now” to run a complete scan on the affected computer for malware.
SafeBytes Anti-Malware Features
To protect your laptop or computer from various internet-based threats, it’s important to install anti-malware software on your personal computer. However, with countless numbers antimalware companies out there, these days it is hard to decide which one you should buy for your laptop. Some of them do a great job in eliminating malware threats while some will damage your PC by themselves. You must be careful not to pick the wrong product, especially if you buy a paid application. On the list of strongly recommended software by industry leaders is SafeBytes Anti-Malware, the most dependable program for Microsoft Windows.
SafeBytes anti-malware is a trustworthy tool that not only secures your PC permanently but is also quite user-friendly for people of all skill levels. Once you’ve got installed this application, SafeByte's sophisticated protection system will ensure that no viruses or malware can seep through your PC.
SafeBytes anti-malware provides an array of enhanced features that sets it aside from all others. Some of them are listed as below:
Real-Time Protection: SafeBytes gives you round-the-clock protection for your PC limiting malware intrusions in real-time. This utility will constantly monitor your computer for suspicious activity and updates itself continuously to keep abreast of the constantly changing threat landscape.
Most effective AntiMalware Protection: Built on a greatly acclaimed anti-virus engine, this malware removal application can find and get rid of numerous stubborn malware threats such as browser hijackers, potentially unwanted programs, and ransomware that other common anti-virus applications will miss.
Website Filtering: Safebytes allots all websites a unique safety score that helps you to have an idea of whether the webpage you’re just about to visit is safe to browse or known to be a phishing site.
Fast Multi-threaded Scanning: Safebytes Anti-Malware, with its advanced scanning engine, offers extremely fast scanning which can promptly target any active online threat.
Low CPU/Memory Usage: SafeBytes is well known for its low influence on processing power and great detection rate of various threats. It operates silently and efficiently in the background so you’re free to utilize your PC at full power all of the time.
24/7 Customer Service: For any technical concerns or product assistance, you could get 24/7 professional assistance through chat and email.
Put simply, SafeBytes has created a meaningful anti-malware solution that is aimed to protect you against all manner of malware. You now may understand that this particular software does more than just scan and eliminate threats from your PC. So if you’re searching for the absolute best malware removal application out there, and when you don’t mind shelling out a few bucks for it, opt for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
To eliminate Nectar Toolbar manually, go to the Add or Remove programs list in the Windows Control Panel and choose the program you want to remove. For browser extensions, go to your web browser’s Addon/Extension manager and select the add-on you want to remove or disable. You’ll probably also want to reset your internet browser to its default settings.
Finally, check your hard disk for all of the following and clean your computer registry manually to get rid of leftover application entries after uninstallation. But bear in mind, this can be a tough task and only computer professionals can perform safely. In addition, certain malicious programs have the capability to defend against its removal. Completing this task in Safe Mode is suggested.
Files:
C:\Program Files (x86)\Nectar Toolbar
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\AimiaPoints.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\AimiaPointsAct.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\AimiaToolbar.css
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ArrowDown.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ArrowRight.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ArrowUp.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\arrow_refresh.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\background.html
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\background.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\basis.xml
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\BrowserTweak.css
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\btn-background-grey.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\CanCollect.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\CanCollectAct.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\closeIcon.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\cog.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\Collecting.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\CollectingAct.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\computer_delete.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\eShopsMenu.html
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\eShopsMenu.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\help.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\HelpMenu.html
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\HelpMenu.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\icon-128.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\icon-16.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\icon-48.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\icons.bmp
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\icons.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ie7vista.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ie7xp.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\ie8bg.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\IE8GuardWorkaround.exe
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\info.txt
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\InstIcon.ico
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\jquery-1.7.2.min.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\jquery.placeholder.min.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\JSON.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\main.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\menu.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\nectar-icon-32×32.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\PIE.htc
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\PIE.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\SearchHist.html
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\SearchHist.js
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\search_glass.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\separator.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\separator_arrows.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\TbCommonUtils.dll
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\tbcore3.dll
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\TbHelper2.exe
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\tbhelperU.dll
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\uninstall.exe
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\UninstIcon.ico
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\update.exe
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\version.txt
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\Yahoo.ico
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\yahoo.png
C:\Program Files (x86)\Nectar Toolbar\tbunsg7A.tmp\your_logo.png
Registry:
HKEY_CURRENT_USER\Software376694984709702142491016734454
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run 13376694984709702142491016734454
 With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
 Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
 The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
 HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
 HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price.
HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price. 



 Probably tired of even trying to hide it, Steam has released that this year's big Steam Winter sale is officially starting on December 22nd, 2021, and closing on January 5th, 2022. So if you have someone to buy a gift or just want to drop a few great games in your library at a low price this is the time when you should do it.
Probably tired of even trying to hide it, Steam has released that this year's big Steam Winter sale is officially starting on December 22nd, 2021, and closing on January 5th, 2022. So if you have someone to buy a gift or just want to drop a few great games in your library at a low price this is the time when you should do it.  Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11.
Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11. 