The Event Viewer in the Windows operating system is used to troubleshoot any computer issues. It is one of the most useful tools that keep logs of both security and system events. It also monitors for both software and hardware problems in the computer. This tool is the only one with amazing features that maintain logs about everything that’s going on in the computer system. It keeps track of all the information to the point where going over them will take a lot of time.
Luckily, the Event Viewer tool now allows users to create custom views where you can set the filters and sort the data recorded to limit the information details to only what you’re interested in seeing. For instance, if you want to troubleshoot with one hard drive, you can just create a special custom view to display only the hard drive warnings in the security logs. This will save you hassle and time.
Take note that the logs in the Event Viewer are divided into two main categories namely the Window logs and the Application and Services logs. You can just set the filter to the logs by their event id, specific date, and many other events when you have to troubleshoot some problem in your computer. So if you are trying to troubleshoot a problem in your Windows 10 computer and you’re checking the Event Viewer, read on as this post will guide you in creating custom event views in the Event Viewer. To get started, refer to the instructions given below.
Step 1: Go to the Start menu and in the search box, type “event viewer” and then click on Event Viewer from the search results to open it.
Step 2: After opening Event Viewer, click on Custom Views located in the left pane of the window.
Step 3: Next, click on the Administrative events under the Custom View to create special log views.
Step 4: Then on the right side of the window, click on Create Custom View to open the Create Custom View window.
Step 5: There is a logged drop-down list under Filter. From there, you have the option to choose an appropriate predefined time or use a custom time range for your Custom log views.
Step 6: After that, select an appropriate event level for your custom view. You have fine entry-level options to choose from such as critical event level, error, warning, information and verbose.
- Critical – select this if you want to see the events that require your immediate attention in the custom view.
- Error – select this if you want your Event Viewer to display the events that are less critical but hints at the problems.
- Warning – select this event-level if you want to see the event with the potential problem but may not bound to happen.
- Verbose – select this if you want to see detailed information about all the events.
Step 7: After you’ve selected the event level, you now have to select how you want the events to be filtered. They can either be filtered By the log or By the source.
- By the log – you can select two options called Windows log and, Application and Service logs. The Windows logs allow you to filter the logs created during events like setup, security, applications, and system events. While the Application and Service logs filter the log created by the installed applications in your system.
- By the source – select this if you want your Custom View to search for information in event sources. It allows you to view events in detail for various applications and devices.
Note: You have the option to further customize the event logs with more filters like Event IDs, task category, keywords, User, and Computer. Using these additional filters, you can choose to filter the events in the special views by specifying event id numbers in the Event IDs, entering predefined Windows words in the Keyword, specify the user accounts in the User field, as well as choose the system from the server to maintain logs in the Computer field.
Step 8: Once you’re done customizing the log filter, click on OK to apply the changes made.
Step 9: After that, a Save Filter should be displayed in the Custom View window. Just enter the Custom View name and select the Event Viewer folder where you want to save the Custom view. The folder name should be Custom View by default. And if you want, you can also create your own folder if you want your custom views to be visible to all the system users.
Step 10: Next, check all the Users box located in the lower corner of the window and then click the OK button after you’re done.
You should now see the customized filter you just created on the left side of the window. Just click on it to check your filtered events in the center of the Event Viewer window. And for you to save the custom view logs, simply right-click on the Custom views you created and then click on Save All Events in the Custom View As from the drop-down menu. Then put a name on the file and select the appropriate location where you want to save the logs and click on the Save button. Note that the log file is saved with the “.EVTX” file extension and when you double click on it, it will open the file in the Event Viewer.
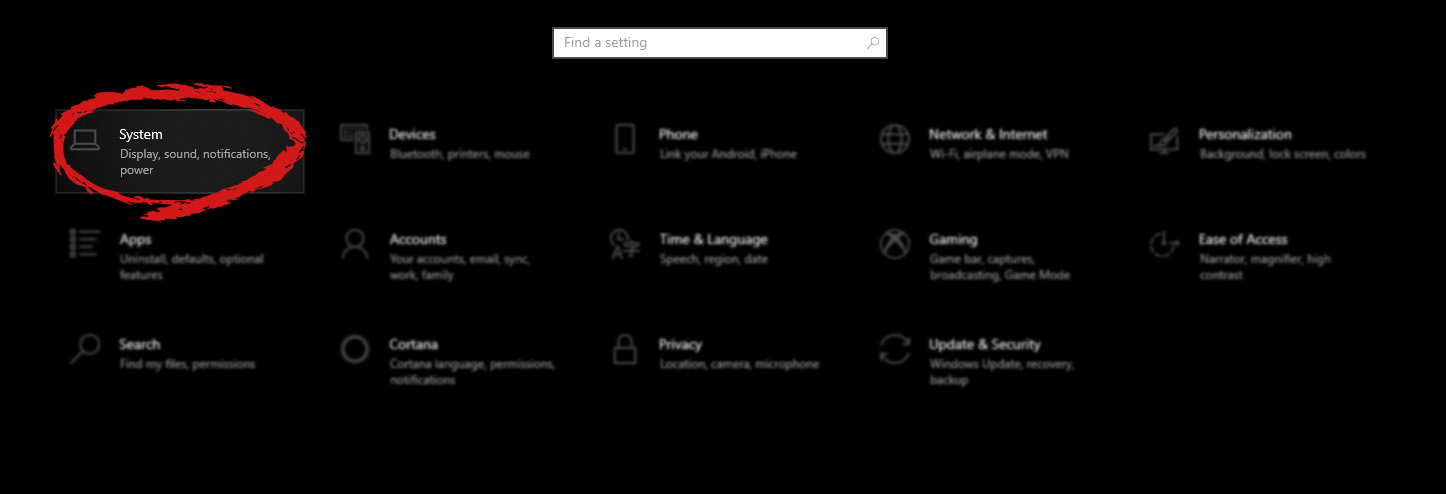
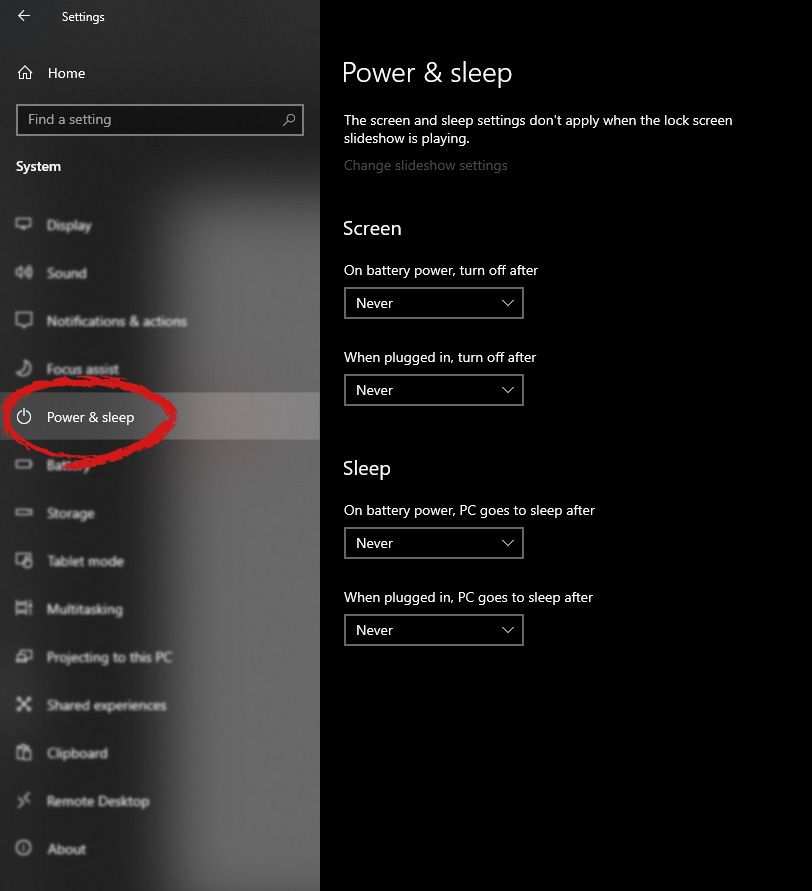

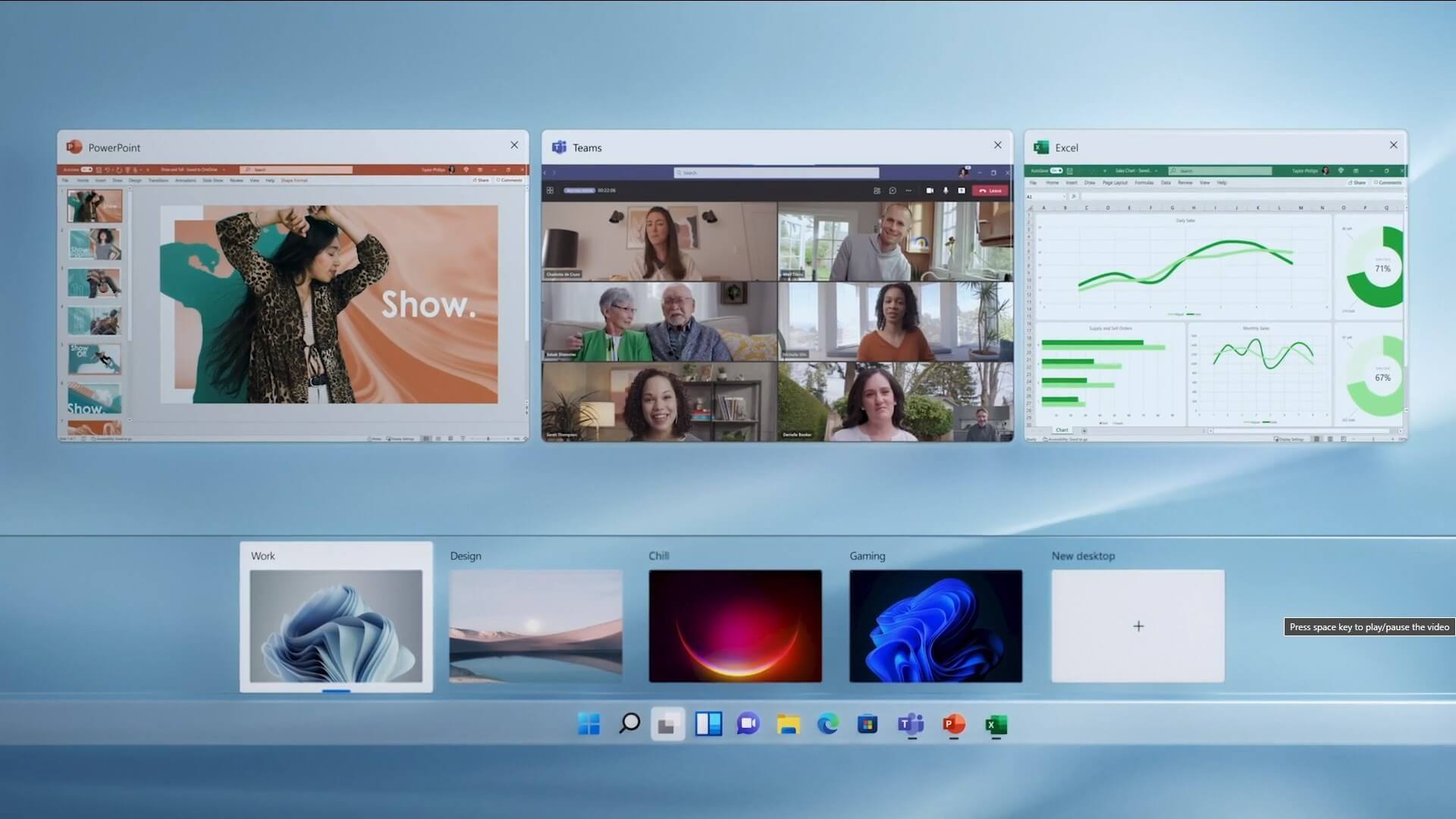 The feature that was originally planned for now scrapped Windows 10X is included in Windows 11. You will be able to customize your Virtual desktop with different wallpapers for each screen.
In order to fully customize your virtual desktops with different wallpapers follow this easy step-by-step guide.
The feature that was originally planned for now scrapped Windows 10X is included in Windows 11. You will be able to customize your Virtual desktop with different wallpapers for each screen.
In order to fully customize your virtual desktops with different wallpapers follow this easy step-by-step guide.

 With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
With its Rift model, Oculus set itself as a big player in VR. Now the company is slowly bowing out of the dedicated, tethered VR headset with its latest Quest 2 designed to primarily be a standalone headset.
In case you do not know, tethered headset means that the headset itself is connected to your PC and is using its power to drive your VR experience.
Now technical specifications of Quest 2 are pretty OK and it can drive stuff pretty decently and if you want you can purchase the dedicated cable to connect it to your PC for the full experience of games requiring more capable hardware.
Oculus Quest 2 is the cheapest headset on this list and with its stable performance, is highly recommended.
 Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
Although the headset itself is nothing revolutionary or special its controllers are. They can track individual finger movements, making games (that take advantage of them) much more immersive than the standard trigger grips on other controllers.
The Index's higher refresh rate makes for smoother action, as well, which is another nice bonus. If you already have an HTC Vive or Vive Cosmos Elite, and their base stations (not the regular Cosmos), you can buy only the controllers.
 The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
The PlayStation VR is compelling thanks to Sony backing its development, plus the PlayStation 4's affordability and availability compared with gaming PCs. All you need is the headset, a PlayStation 4, and a PlayStation Camera (now included with most PlayStation VR bundles).
Not really the best of the bunch but still one of the top ones for console gaming. Sony is working on a new PlayStation VR system for the PlayStation 5, with redesigned controllers. The new headset hasn't been revealed yet, but the company has released a preview of the new controllers.
 HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
HP headset is one which you get if you want the best image quality in VR headset, sadly controllers did not follow the same quality of headset itself. But this is still a pretty decent headset overall and worth the purchase.
 HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price.
HTC's Vive Cosmos is the upgraded version of the Vive. It features a higher resolution and replaces the external base stations with outward-facing cameras for motion tracking. It's a comprehensive package for whole-room VR.
HTC recently released the Vive Pro 2, a high-end VR headset targeting both enterprise users and consumers. This new headset features a 2,448-by-2,448 resolution display for each eye, making it the highest-resolution headset currently available. It's also more expensive than the Cosmos Elite.
Sadly one thing that is bringing this headset down is the price. 