Error Code 0x8007000b - What is it?
Error Code 0x8007000b has appeared on Windows operating systems from Windows 10 all the way back to Windows XP. In most cases, it occurs when there is a problem within the transaction log for the filing system within Windows.
Common symptoms include:
- Inability to install one or more updates
- Message regarding Windows Update having an unknown error
There are several different ways that you can attempt to resolve the problems that cause Error Code 0x800700b to appear on your operating system. Several of these methods are pretty easy for basic users, but others require some comfort and knowledge in working with advanced tools on your operating system.
If the methods below do not completely resolve the appearance of Error Code 0x800700b on your Windows operating system or if you are not confident in your ability to undertake these steps on your own, you may need to get in touch with a qualified computer repair professional to assist you with the error resolution process. If this error message is not resolved, you could expose your computer to other error codes such as error code 80070103.
Solution
 Error Causes
Error Causes
The primary cause for Error Code 0x800700b is that there is an issue or corrupt entry in the transaction log for the file system within Windows. This makes it impossible for Windows to complete the Windows Update process. Although the error message states that an unknown error has been encountered, it is usually fairly simple to resolve the appearance of faulty or corrupt entries in the transaction log if you follow the steps below to complete.
Further Information and Manual Repair
There are several ways that you can attempt to resolve Error Code 0x800700b manually on your Windows operating system. At least one of these methods requires some advanced knowledge or skill in using the command prompt, so if you aren’t confident in your ability to follow these steps through to completion, be sure to get in touch with a qualified computer repair technician who can help you to resolve the error.
Here are the top three methods that can be used to resolve Error Code 0x800700b on your machine:
Method One: Reset Your Transaction Log for the File System in Windows
To clear and reset the entries in your transaction log, there are a few simple steps that you should follow:
- Step One: Open up the Start menu and go into the search bar. When it opens up, type in “cmd”.
- Step Two: Right-click on the icon for the Command Prompt that opens up and selects the option to run it as an administrator.
- Step Three: In the menu that appears, enter in this command: “fsutil resource setautoreset true C:/”
- Step Four: Reboot your computer before re-attempting the download and install of the necessary update.
Method Two: Run the System Update Readiness Tool
An alternative method to resolving Error Code 0x800700b is to open and run the System Update Readiness Tool on your machine. This program runs a scan on your Windows operating system to determine whether it is ready for updates, attempting to resolve any errors it encounters along the way.
After you have scanned and run this tool, you should always take the time to restart your computer before attempting to perform the update process, so that any changes made can be successfully applied to your computer.
Method Three: Run the System File Checker Tool on Your Computer
The System File Checker is a tool for Windows that runs a basic scan for problem files and attempts to resolve them. To run this tool, follow these steps:
- Step One: From the Start menu, open up the search box, and type in “cmd,” selecting the option to run the command prompt as an administrator.
- Step Two: Type in this command and run it: “sfc /scannow”
This tool should tell you what the specific issues are so that you can resolve them. It may give you a message that the action couldn’t be performed, that corrupt files were fixed, or that corrupt files were encountered, but could not be fixed automatically.
Method Four: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise,
download and install a powerful automated tool.


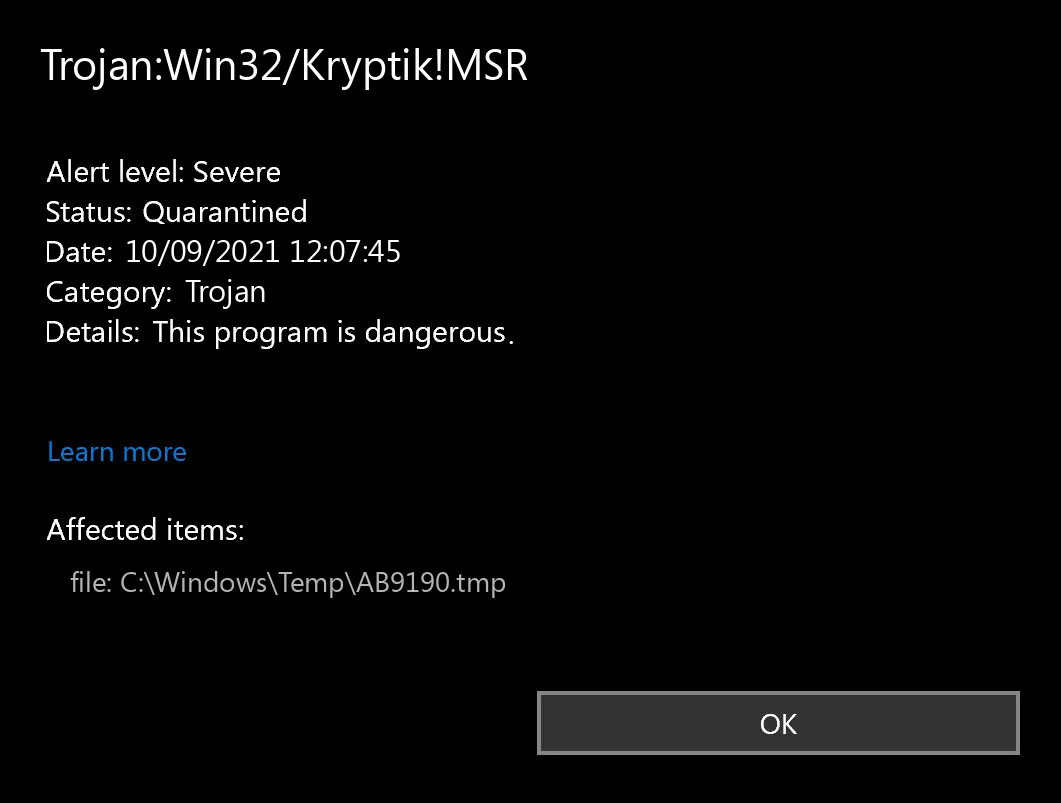 Trojan.Kryptik creates the following registry entry or registry entries:
Trojan.Kryptik creates the following registry entry or registry entries: