InboxAce is a browser extension for Google Chrome developed by Mindspark and gives users easy access to the most popular email clients with just 1 click away. This extension changes your default search engine, as well as your home page to MyWay.com. Several anti-virus scanners have marked this extension as a Browser Hijacker due to its information mining nature.
While installing this extension monitors user browsing activities. It logs the website you visit, the links you click, the products you buy, basically everything that you do in a browser. This information is later used to display unwanted targeted ads that are injected into your search results.
About Browser Hijackers
Browser hijacking means that a malicious code has power over and modified the settings of your internet browser, without your consent. Browser hijacker malware is designed for many different reasons. Typically, it will drive users to particular websites which are looking to increase their advertising campaign revenue. Many people believe that these kinds of sites are legitimate and harmless but that is incorrect. Almost every browser hijacker poses an actual threat to your online safety and it is vital to classify them under privacy risks. Browser hijackers can also permit other malicious programs without your knowledge to further damage the computer.
How to determine if your browser has been hijacked
Signs that an internet browser is hijacked include: the home page of your respective browser is changed unexpectedly; you observe new unwanted favorites or bookmarks added, usually directed to ad-filled or pornography sites; default online search engine is modified; find new toolbars which you did not add; unstoppable flurries of popup advertisements show up on your computer screen; your browser gets slow, buggy, crashes very often; Inability to navigate to particular sites, especially anti-malware and also other security software sites.
How it infects your PC
Browser hijackers might use drive-by downloads or file-sharing websites or an e-mail attachment in order to reach a targeted computer. They also come from add-on applications, also known as browser helper objects (BHO), browser extensions, or toolbars. Other times you may have unintentionally accepted a browser hijacker as part of a software bundle (usually freeware or shareware). A good example of some notorious browser hijackers includes Conduit, Anyprotect, Babylon, DefaultTab, SweetPage, Delta Search, and RocketTab, but the names are continually changing.
Browser hijackers can disrupt the user’s web surfing experience greatly, record the websites frequented by users and steal private information, cause problems in connecting to the internet, and then finally create stability problems, making applications and systems crash.
Tips on how to get rid of browser hijackers
Some types of browser hijackers can be effortlessly removed from your PC by deleting malicious software or any other recently installed freeware. But, most hijackers are extremely tenacious and need specialized applications to eliminate them. And there’s no denying the very fact that the manual repairs and removal methods could be a difficult job for a novice PC user. On top of that, there are many risks connected with tinkering around with the system registry files.
Anti-malware software is very effective with regards to picking up and eliminating browser hijackers that normal anti-virus application has overlooked. SafeBytes Anti-Malware will counter persistent browser hijackers and provide you real-time computer protection against all types of malware. In addition to anti-malware, a system optimizer program, similar to Total System Care, could help you fix Windows registry errors, get rid of unwanted toolbars, secure your online privacy, and increase overall computer performance.
Find Out How To Install Safebytes Anti-Malware On An Infected PC
Malware can cause all sorts of damage once they invade your computer, starting from stealing your personal details to deleting files on your computer system. Some malware goes to great lengths to stop you from installing anything on your computer system, particularly antivirus programs. If you’re reading this, odds are you’re stuck with a malware infection that is preventing you to download or install the Safebytes Anti-Malware program on your PC. There are a few fixes you could try to get around with this particular problem.
Remove viruses in Safe Mode
If any virus is set to run automatically when Windows starts, entering Safe Mode could very well block this attempt. Just the minimum required programs and services are loaded when you start your PC into Safe Mode. The following are the steps you have to follow to boot into the Safe Mode of your Windows XP, Vista, or 7 computers (visit Microsoft website for instructions on Windows 8 and 10 computers).
1) At power-on/startup, tap the F8 key in 1-second intervals. This will bring up the Advanced Boot Options menu.
2) Use the arrow keys to choose Safe Mode with Networking and press ENTER.
3) When you are into this mode, you should have online access once again. Now, make use of your browser normally and navigate to https://safebytes.com/products/anti-malware/ to download and install Safebytes Anti-Malware.
4) After installation, do a full scan and let the program eliminate the threats it finds.
Switch over to an alternate web browser
Some viruses may target vulnerabilities of a particular web browser that block the downloading process. If you’re not able to download the security software using Internet Explorer, this means malware could be targeting IE’s vulnerabilities. Here, you must switch to another browser such as Firefox or Chrome to download Safebytes software.
Make a bootable USB anti-virus drive
Another option is to save and operate an anti-malware program completely from a Thumb drive. Adopt these measures to run the antivirus on the affected computer.
1) On a clean computer, install Safebytes Anti-Malware.
2) Plug the Thumb drive into the clean computer.
3) Double click on the exe file to open the installation wizard.
4) When asked, select the location of the USB drive as the place where you would like to put the software files. Follow activation instructions.
5) Unplug the pen drive. You may now utilize this portable anti-virus on the affected computer system.
6) Double click the EXE file to open the Safebytes tool right from the pen drive.
7) Simply click “Scan Now” to run a complete scan on the affected computer for viruses.
A Look at the Best AntiMalware Program
If you are looking to download the anti-malware program for your PC, there are various tools in the market to consider but you just cannot trust blindly anyone, irrespective of whether it is paid or free program. Some are very good ones, some are ok types, and some are just bogus anti-malware programs that could ruin your computer themselves! You should select one that is dependable, practical, and has a strong reputation for its malware source protection. When considering commercial antimalware tool options, many people select well-known brands, such as SafeBytes, and they are quite happy with it.
SafeBytes is a powerful, real-time anti-malware application that is designed to assist the typical computer end user in safeguarding their computer from malicious internet threats. When you have installed this software, SafeByte's state-of-the-art protection system will make sure that no viruses or malware can seep through your personal computer.
SafeBytes anti-malware takes PC protection to a totally new level with its enhanced features. Here are some of the features you will like in SafeBytes.
World-class AntiMalware Protection: Built on a greatly acclaimed anti-virus engine, this malware removal application can detect and remove numerous obstinate malware threats like browser hijackers, PUPs, and ransomware that other typical antivirus programs will miss.
Active Protection: SafeBytes gives you round-the-clock protection for your computer limiting malware intrusions instantly. This software will constantly keep track of your computer for suspicious activity and updates itself continuously to keep abreast of the constantly changing threat landscape.
Extremely Speed Scanning: SafeBytes’s virus scan engine is one of the fastest and most efficient in the industry. Its targeted scanning highly increases the catch rate for malware that is embedded in various computer files.
Safe Web Browsing: SafeBytes checks and gives a unique safety rating to each and every website you visit and block access to web pages known to be phishing sites, thus protecting you from identity theft, or known to contain malicious software.
Light-weight: SafeBytes gives total protection from online threats at a fraction of the CPU load because of its advanced detection engine and algorithms.
Premium Support: Skilled technicians are at your disposal 24/7! They will promptly resolve any technical issues you might be experiencing with your security software.
On the whole, SafeBytes Anti-Malware is a solid program as it has lots of features and could detect and remove any potential threats. You can rest assured that your PC will be protected in real-time as soon as you put this tool to use. You will get the very best all-around protection for the money you spend on SafeBytes anti-malware subscription, there is no doubt about it.
Technical Details and Manual Removal (Advanced Users)
If you’d like to manually get rid of InboxAce without the use of an automated tool, it may be actually possible to do so by removing the program from the Microsoft Windows Add/Remove Programs menu, or in cases of web browser plug-ins, going to the browsers AddOn/Extension manager and removing it. It is also highly recommended to factory reset your browser settings to their default state.
If you choose to manually delete the system files and registry entries, utilize the following list to ensure that you know precisely what files to remove before executing any actions. But bear in mind, this can be a tricky task and only computer professionals could accomplish it safely. Also, certain malware is capable of replicating itself or preventing deletion. You’re urged to do this process in Safe Mode.
Files:
Search and Delete:
1gauxstb.dll
1gbar.dll
1gbarsvc.exe
1gbprtct.dll
1gbrmon.exe
1gbrstub.dll
1gdatact.dll
1gdlghk.dll
1gdyn.dll
1gfeedmg.dll
1ghighin.exe
1ghkstub.dll
1ghtmlmu.dll
1ghttpct.dll
1gidle.dll
1gieovr.dll
1gimpipe.exe
1gmedint.exe
1gmlbtn.dll
1gmsg.dll
1gPlugin.dll
1gradio.dll
1gregfft.dll
1greghk.dll
1gregiet.dll
1gscript.dll
1gskin.dll
1gsknlcr.dll
1gskplay.exe
1gSrcAs.dll
1gSrchMn.exe
1gtpinst.dll
1guabtn.dll
AppIntegrator64.exe
AppIntegratorStub64.dll
BOOTSTRAP.JS
chromegffxtbr.jar
CHROME.MANIFEST
CREXT.DLL
CrExtP1g.exe
DPNMNGR.DLL
EXEMANAGER.DLL
Hpg64.dll
INSTALL.RDF
installKeys.js
LOGO.BMP
NP1gStub.dll
T8EXTEX.DLL
T8EXTPEX.DLL
T8HTML.DLL
T8RES.DLL
T8TICKER.DLL
VERIFY.DLL
s_pid.dat
1gEIPlug.dll
1gEZSETP.dll
NP1gEISb.dll
000653A1.exe
Folders:
%APPDATA%\InboxAce_1g\
%PROGRAMFILES%\InboxAce_1g\
%PROGRAMFILES%\InboxAce_1gEI\
Registry:
Key HKLM\SOFTWARE\Classes\InboxAce_1g.DynamicBarButton
Key HKLM\SOFTWARE\Classes\InboxAce_1g.DynamicBarButton\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.DynamicBarButton\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.DynamicBarButton.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.DynamicBarButton.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.FeedManager
Key HKLM\SOFTWARE\Classes\InboxAce_1g.FeedManager\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.FeedManager\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.FeedManager.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.FeedManager.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLMenu
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLMenu\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLMenu\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLMenu.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLMenu.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLPanel
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLPanel\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLPanel\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLPanel.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.HTMLPanel.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.MultipleButton
Key HKLM\SOFTWARE\Classes\InboxAce_1g.MultipleButton\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.MultipleButton\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.MultipleButton.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.MultipleButton.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.PseudoTransparentPlugin
Key HKLM\SOFTWARE\Classes\InboxAce_1g.PseudoTransparentPlugin\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.PseudoTransparentPlugin\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.PseudoTransparentPlugin.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.PseudoTransparentPlugin.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.Radio
Key HKLM\SOFTWARE\Classes\InboxAce_1g.Radio\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.Radio\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.Radio.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.Radio.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.RadioSettings
Key HKLM\SOFTWARE\Classes\InboxAce_1g.RadioSettings\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.RadioSettings\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.RadioSettings.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.RadioSettings.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ScriptButton
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ScriptButton\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ScriptButton\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ScriptButton.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ScriptButton.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SettingsPlugin
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SettingsPlugin\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SettingsPlugin\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SettingsPlugin.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SettingsPlugin.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncher
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncher\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncher\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncher.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncher.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncherSettings
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncherSettings\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncherSettings\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncherSettings.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.SkinLauncherSettings.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ThirdPartyInstaller
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ThirdPartyInstaller\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ThirdPartyInstaller\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ThirdPartyInstaller.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ThirdPartyInstaller.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ToolbarProtector
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ToolbarProtector\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ToolbarProtector\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ToolbarProtector.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.ToolbarProtector.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.UrlAlertButton
Key HKLM\SOFTWARE\Classes\InboxAce_1g.UrlAlertButton\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.UrlAlertButton\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.UrlAlertButton.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.UrlAlertButton.1\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.XMLSessionPlugin
Key HKLM\SOFTWARE\Classes\InboxAce_1g.XMLSessionPlugin\CLSID
Key HKLM\SOFTWARE\Classes\InboxAce_1g.XMLSessionPlugin\CurVer
Key HKLM\SOFTWARE\Classes\InboxAce_1g.XMLSessionPlugin.1
Key HKLM\SOFTWARE\Classes\InboxAce_1g.XMLSessionPlugin.1\CLSID
Key HKLM\SOFTWARE\MozillaPlugins\@InboxAce_1g.com/Plugin
Key HKLM\SOFTWARE\InboxAce_1g
Key HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_INBOXACE_1GSERVICE
Key HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_INBOXACE_1GSERVICE%#MANIFEST#%00
Key HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_INBOXACE_1GSERVICE%#MANIFEST#%00\Control
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService\Security
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService\Enum
Key HKCU\Software\InboxAce_1g
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ Value: InboxAce Search Scope Monitor Data: C:\PROGRA~1\INBOXA~2\bar.bingsrchmn.exe /m=2 /w /h
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ Value: InboxAce_1g Browser Plugin Loader Data: C:\PROGRA~1\INBOXA~2\bar.bingbrmon.exe00\Control
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService\Security
Key HKLM\SYSTEM\CurrentControlSet\Services\InboxAce_1gService\Enum
Key HKCU\Software\InboxAce_1g
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ Value: InboxAce Search Scope Monitor Data: C:\PROGRA~1\INBOXA~2\bar.bingsrchmn.exe /m=2 /w /h
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ Value: InboxAce_1g Browser Plugin Loader Data: C:\PROGRA~1\INBOXA~2\bar.bingbrmon.exe



 Following are proven solutions that will resolve the issue and provide you with a working device.
Following are proven solutions that will resolve the issue and provide you with a working device.

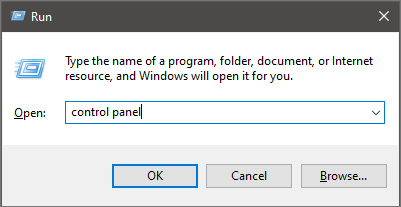 Once you are in the control panel, switch your view to large icons and locate Indexing options.
Once you are in the control panel, switch your view to large icons and locate Indexing options.
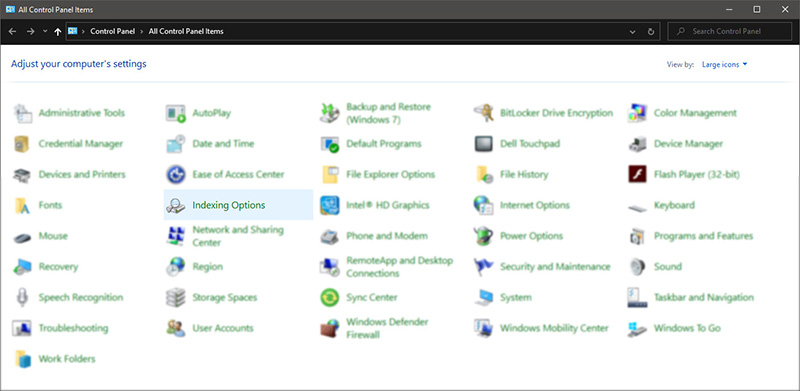 Inside indexing options, click on advanced.
Inside indexing options, click on advanced.
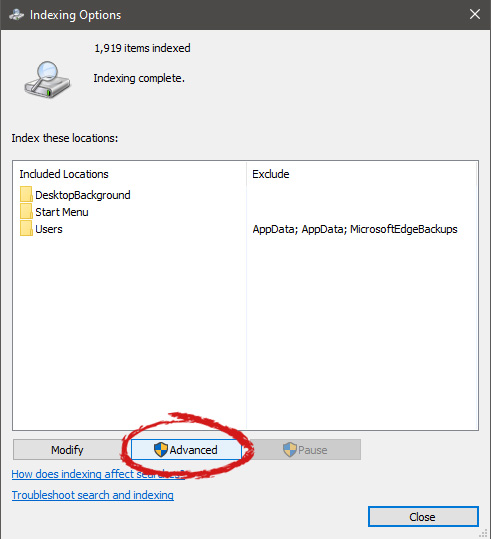 In advanced options click on the rebuild and confirm.
In advanced options click on the rebuild and confirm.
 Leave your computer to finish and your searches should be working fine now.
Leave your computer to finish and your searches should be working fine now.  This is the second large game company acquisition by Microsoft, Acquiring Bethesda first and a big hit to Sony since Xbox will now have more games in its catalog and as exclusives.
Of course, the sale has to go through the standard closing conditions and completion of regulatory review and Activision Blizzard’s shareholder approval before it’s finalized. Assuming that all goes well, the deal is slated to be completed during the fiscal year 2023, which is July 1, 2022, through June 30, 2023.
This is the second large game company acquisition by Microsoft, Acquiring Bethesda first and a big hit to Sony since Xbox will now have more games in its catalog and as exclusives.
Of course, the sale has to go through the standard closing conditions and completion of regulatory review and Activision Blizzard’s shareholder approval before it’s finalized. Assuming that all goes well, the deal is slated to be completed during the fiscal year 2023, which is July 1, 2022, through June 30, 2023.  Intel says that the remedy to the issue for these games is the scroll lock fix which can be done so by enabling Legacy Game Compatibility mode from the BIOS of your motherboard. When running the said games, you can press scroll lock to park the E-cores on Intel's Alder Lake Desktop CPUs to get rid of DRM issues.
Certain motherboard manufacturers such as MSI and Gigabyte have made this even easier through software tools with which you don't have to access the BIOS. All you need to do is select a button in the tool which works on both Windows 11 and Windows 10 operating systems and you will enable compatibility mode.
Intel says that the remedy to the issue for these games is the scroll lock fix which can be done so by enabling Legacy Game Compatibility mode from the BIOS of your motherboard. When running the said games, you can press scroll lock to park the E-cores on Intel's Alder Lake Desktop CPUs to get rid of DRM issues.
Certain motherboard manufacturers such as MSI and Gigabyte have made this even easier through software tools with which you don't have to access the BIOS. All you need to do is select a button in the tool which works on both Windows 11 and Windows 10 operating systems and you will enable compatibility mode. 