Error Code 0x80070004 on Windows 10 – What Is It?
Some users trying to upgrade from Windows 7 or Windows 8/8.1 reported experiencing installation rollback with error code 0x80070004. This error normally appears when the Computer Name is set to names that can’t be used for the computer. It’s also possible this error occurs if users or program files folder were redirected to a different partition.
Solution
 Error Causes
Error Causes
The Error code 0x80070004 on Windows 10 is normally caused if any of the following were used as the Computer Name and the user tried to upgrade to Windows 10:
- System (or SYSTEM)
- SELF
- LOCAL
- Network
Failure to fix this error message might result in others, including
error code 0xc0000001.
Further Information and Manual Repair
If you don’t solve this error, you won’t be able to upgrade from Windows 7 or Windows 8/8.1 to Windows 10. Note that this error will continuously bring you back to the original OS unless fixed.
Please note that if you’re not confident in doing these steps, you might want to consider seeking the help of an expert or using an automated tool that will help fix this.
Here are a few methods to try.
Method 1: Check and Change the Computer Name
The most common cause of this error is if your computer uses any of the following reserved names:
- LOCAL
- System (or SYSTEM)
- Network
- SELF
These reserved names are not meant to be used as computer names. If this is what your computer uses and you try to upgrade to Windows 10, you will surely get this error. Check your computer name and if you see any of the reserved names, change it right away.
Changing Computer Name in Windows 8.1
If you’re trying to upgrade from Windows 8.1, you can change the name of the computer by following these steps:
- Step 1: Open the Start menu then simply type “rename computer”. After that, choose “Rename this computer”
- Step 2: A dialog box will open. Just click the “Change” button
- Step 3: A new dialog box will open. Type the new name. Click Apply then Ok.
Changing Computer Name in Windows 7
If you’re trying to upgrade from Windows, you can follow the steps below to change the name of your computer.
- Step 1: Go to the Start menu then on the Computer section, right-click the mouse and choose “Properties”.
- Step 2: A new dialog box will appear. Go to “Computer name, domain, and workgroup settings” then click “Change settings”. In case you’re asked for administrative access, make sure to grant it.
- Step 3: Find the “Computer Name” tab then click “Change”
- Step 4: Change the computer name and click Ok.
Method 2: Fix the “Users” directory issue
If the first method doesn't work, it probably means the computer name isn’t the cause of this error. Another reason why users experience Error code 0x80070004 when upgrading to Windows 10 is if the “Users” directory was relocated. So, when you try upgrading to Windows 10, the installer wasn’t able to find the user profiles on the “%systemdrive%”, where the current operating system is installed.
If you changed or moved any of the Users, Program Data, or Program Files folders, this will cause the error. Before you upgrade to Windows 10, you might be required to reset or reinstall your current operating system (Windows 7 or Windows 8.1).
If you haven’t made any changes or haven’t moved any of the mentioned folders, there’s a great chance that your users' profiles are corrupted. You can also reinstall your current operating system. However, you might want to check for the corrupter user profile first. To do this, follow the steps below:
- Step 1: Go to the Start menu and type System
- Step 2: Click System then go to the Advanced tab
- Step 3: Go to Settings, which you’ll find under User Profiles
On the Users Profiles, make a copy of all the accounts somewhere. Sign out from the current user account then try logging in back using the accounts you’ve copied. For each account, you get an error, delete it. However, make sure that you don’t delete the UpdateUser and Administrator account ever.
After this is done, try upgrading your operating system to windows 10 again.
Method 3: Try a trusted and secured Automated Tool
If the above methods still not useful, you might want to rely on an automated tool. Find a secured and trusted tool. It will help fix this issue.
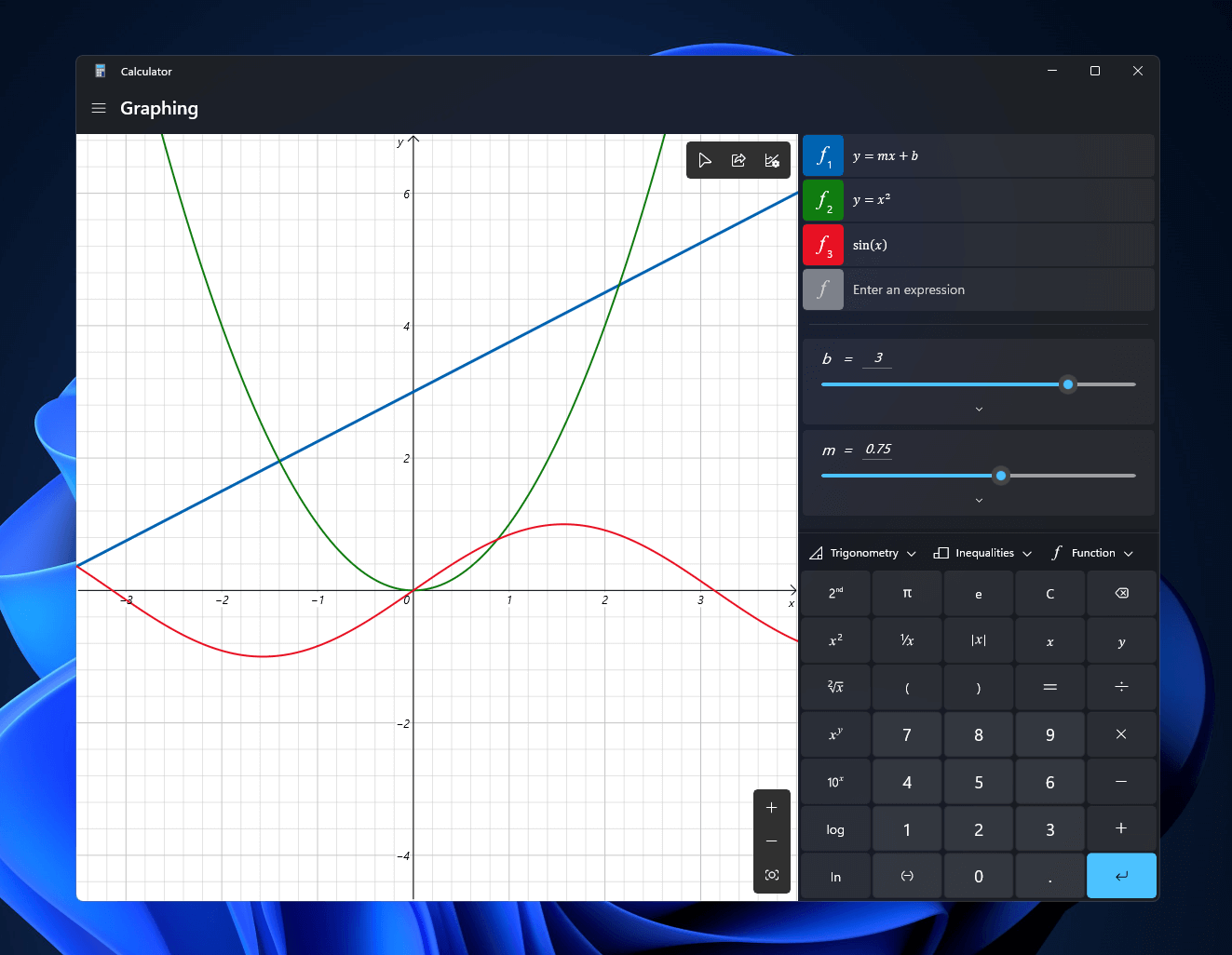 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.


