Error Code 38 – What is it?
Error Code 38 is a device driver error that users encounter on any Windows 2000 operating system and its following versions.
It occurs when the peripheral device that you connect to your PC cannot be accessed due to an inability of the Windows system to acknowledge the driver as a previous record of the driver being loaded is found in its memory.
It is a common error that users come across and appears on your PC with the following message:
“Windows cannot load the device driver for this hardware because a previous instance of the device driver is still in memory. (Code 38)”
Solution
 Error Causes
Error Causes
Error Code 38 is prompted when incomplete program files are left in the Windows system which damage or corrupt its files. There are various factors that contribute to this, some of which are:
- An incomplete program installation
- An incomplete program uninstallation
- Hardware is not removed properly
- System recovery from viruses
- An improper system shut down
The above triggers are very likely to create incomplete files within the Windows registry thereby leading to its damage and corruption.
This is especially true in the case of your PC when it has recovered from viruses when using anti-virus software. The anti-virus in its effort to remove the virus also could remove the files which contain them thereby increasing the risk of the error code.
These damaged files can severely impact the health of your PC and are imperative to fix it immediately to prevent further problems.
Further Information and Manual Repair
Although this error code may pose serious problems for your PC, thankfully, it is very similar to other PC driver errors and thus is an easy one to get rid of. Here are various methods that you can use to get your PC running smoothly again.
Method 1 – Restart your PC
The easiest method you can use to solve your PC error code is to simply restart your PC. It may be that the error prompted upon connecting the device you have connected is merely a temporary problem, and upon restart, will resume functioning smoothly.Method 2 – Run the Troubleshooting Wizard
If restarting your PC does not help, you will have to find the exact nature of the problem by running the troubleshooting wizard for the device and then address the problem accordingly. To do this, proceed with the following steps:
- Run Device Manager on your PC
- Click on the program under the installed programs that is creating problems for you
- Click on the ‘General’ Tab
- Click ‘Troubleshoot’
- Upon opening, the Troubleshooting Wizard will ask a series of questions regarding the error. Answer the questions and follow its directions for solving the error code.
After following the directions of the Troubleshooting wizard, make sure to restart your PC for the changes to take effect. Now check if your device is still causing problems.
Method 3 – Use System Restore
If the error persists, you can use system restore to eliminate the problem. Here is how to do so:
- Log in using an Administrator account
- Click ‘Start’ button and select All Programs > Accessories > System Tools > System Restore
- Click ‘Restore my computer to an earlier time’ and click ‘Next’
- Select the last Windows to restore point from the ‘On this list, click a restore point’ list, and click ‘Next’
- Click ‘Next’ on the confirmation window to proceed
- Restart your PC after restoration is complete
By restoring the system via a last saved system checkpoint, you can obtain undamaged Windows system files that can help resolve the error code.
Method 4 – Manually uninstall and reinstall the device driver
If using system restore does not work either, you may have to resort to manually uninstalling and then reinstalling the device driver causing the problem.
This would be necessary since the remaining incomplete files due to a partial removal or installation of programs are responsible for the error code. By uninstalling and reinstalling the device driver program, it would lead to the completion of the files.
You can do this by firstly logging in as Administrator and opening Device Manager. Select the device that is causing the problem and double click it; make sure that the peripheral is connected properly to the PC.
Upon opening, click on the ‘Driver’ tab and then select ‘Update Driver’. Make sure to refer to the system documentation that you received with your PC or computer to check for the motherboard details and driver specifics.
Method 5 – Use software to automatically download the driver
Manually uninstalling and reinstalling the driver will do the trick; however, it may be time-consuming especially when you would have to resort to your hardware user manual.
Using a program such as DriverFIX can save you a lot of time and frustration in having your device to work properly on your computer.
DriverFIX, with its user-friendly approach to help you fix your PC issues, comes with an integrated database that detects which drivers you need to reconfigure within just a few seconds and downloads it automatically.
It further ensures that your drivers are installed in their entirety leaving no room for any incomplete files to remain that create Error Code 38, or any other driver-related errors for that matter.
It also has the added advantage of being able to backup and restores your files should there be the slightest possibility of system file damage. DriverFIX is the answer to fixing your PC error codes accurately and quickly.
Click here to download DriverFIX to fix Error Code 38 quickly and effectively!

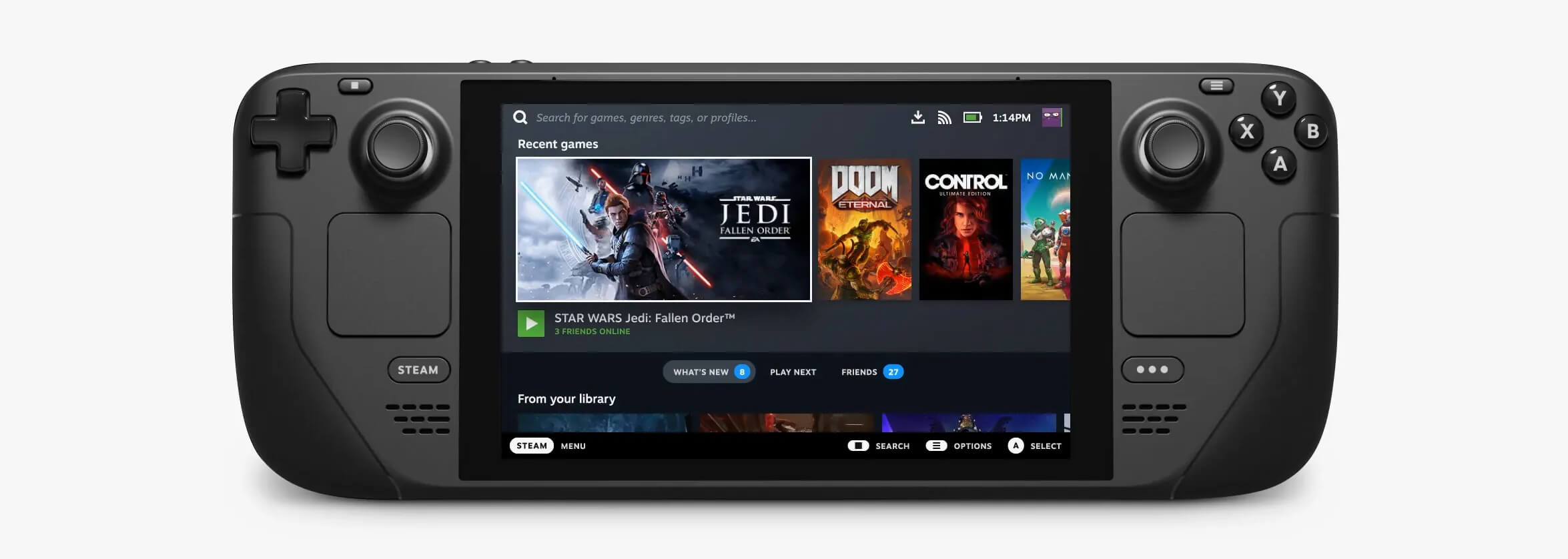 Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11.
Valve has officially announced that Steam Deck will be compatible with Windows 11 despite TPM 2.0 Microsoft requirements.
From the beginning, Deck was announced like a mini handheld PC device. Powered with new Steam OS 3.0 based on Linux. However, besides out-of-the-box OS it was also stated that Deck will be a personal device meaning that other PC-based operating systems could be installed on it and even run your typical applications in it.
Since Microsoft announced Windows 11 hardware requirements, specifically the TPM 2.0 requirement many users voiced concern that Steam Deck will not be able to connect to Windows 11
TPM 2.0 is something that Microsoft requires for every internal and hardware component that is to connect on a Windows 11 device. This is to ensure that only trusted devices would be included in the array of a PC setup and avoid any problems like malicious hardware injecting software into a system.
This would also minimize the compromise Windows would have, as unverified or untrusted devices connect to a Windows PC.
However, Valve and AMD are ensuring us that Deck will not have any issue connecting to a PC running Windows 11 or even if you wish to transform Deck itself into a Device running Windows 11. 
