AudioToAudio is a browser extension for Google Chrome developed by Mindspark Inc. This extension allows users easy access to popular audio converting websites.
When installed, it changes the default search engine, home page, and new tab to MyWay.com. While active AudioToAudio gathers user browsing activities such as, but not limited to: visited websites, clicked links, search queries. This data is later used/sold by the Mindspark ad network to better target ads.
While browsing the internet with this extension enabled, you will see additional injected ads, sponsored content (such as links to web pages, banner ads, affiliate shop links, etc), and even pop-up ads from time to time if the regular ads are blocked.
AudioToAudio has been marked as a Browser Hijacker by several anti-virus applications and is marked for removal by most of them.
About Browser Hijackers
Browser hijacking is a form of unwanted software, commonly a web browser add-on or extension, which causes modifications in web browser’s settings. They are created to interfere with browser functions for various purposes. Typically, hijackers are developed for the benefit of cyber hackers often through revenue generation from forced ad clicks and website visits. However, it isn’t that innocent. Your online safety is compromised and it is also extremely annoying. Some browser hijackers are programmed to make particular modifications beyond the browsers, like changing entries in the computer registry and letting other malware further damage your computer.
How to determine if your browser has been hijacked
When your web browser is hijacked, the following might happen:
1. your web browser’s homepage is suddenly different
2. you get re-directed to sites you never meant to visit
3. The default search page of the web browser is changed
4. discover new toolbars that you simply did not add
5. you see numerous ads pop up on the web browsers or computer screen
6. webpages load slowly and often incomplete
7. Inability to navigate to certain websites, especially antivirus and also other computer security software sites.
How they infect computers
There are many ways your computer or laptop can become infected with a browser hijacker. They usually arrive by way of spam email, via file-sharing networks, or by a drive-by-download. They can also be deployed via the installation of an internet browser toolbar, extension, or add-on. A browser hijacker could also come bundled up with some free software that you unknowingly download and install the browser hijack, compromising your PC security. Some of the most well-known hijackers are AudioToAudio, Babylon Toolbar, Conduit Search, OneWebSearch, Sweet Page, and CoolWebSearch.
Removing browser hijackers
Some hijackers could be removed by just uninstalling the related freeware or add-ons through the Add or Remove Programs in the Microsoft Windows Control Panel. But, the majority of hijackers are quite tenacious and require specialized applications to eliminate them. Novice computer users shouldn’t ever attempt the manual form of removal, as it requires thorough computer knowledge to carry out repairs on the computer registry and HOSTS file.
Browser hijackers can be effectively removed by installing and running anti-malware software on the affected PC. Safebytes Anti-Malware has a sophisticated anti-malware engine to help you prevent browser hijacking in the first place, and mop up any existing issues. In addition to anti-malware, a system optimizer tool, similar to Total System Care, could help you resolve Windows registry errors, eliminate unwanted toolbars, secure online privacy, and increase overall computer performance.
How To Get Rid Of Malware That Is Preventing Anti-Malware Installation?
All malware is bad, but certain types of malware do more damage to your computer than others. Some malware types alter internet browser settings by including a proxy server or change the PC’s DNS settings. In these cases, you will be unable to visit some or all internet sites, and thus not able to download or install the required security software to remove the malware. If you are reading this article, you probably have got affected by malware that prevents you from installing a computer security program like Safebytes Anti-Malware. There are a few actions you can take to get around this problem.
Install in Safe Mode
In Safe Mode, you are able to modify Windows settings, un-install or install some applications, and remove hard-to-delete viruses and malware. In the event the malware is blocking access to the internet and affecting your PC, running it in Safe Mode allows you to download anti-malware and run a diagnostic scan whilst limiting possible damage. In order to enter into Safe Mode or Safe Mode with Networking, press the F8 key while the PC is starting up or run MSCONFIG and locate the “Safe Boot” options in the “Boot” tab. Once you are in Safe Mode, you can attempt to download and install your anti-malware software without the hindrance of the malicious software. Now, you can actually run the antivirus scan to remove computer viruses and malware without any interference from another application.
Switch over to a different web browser
Malicious code could exploit vulnerabilities in a particular internet browser and block access to all anti-virus software websites. If you suspect that your Internet Explorer happens to be hijacked by a computer virus or otherwise compromised by cybercriminals, the best plan of action would be to switch to an alternate browser like Chrome, Firefox, or Safari to download your favorite computer security program – Safebytes Anti-Malware.
Install and run antivirus from your Thumb drive
Here’s another solution which is creating a portable USB anti-virus software package that can scan your computer for malicious software without needing installation. Adopt these measures to use a USB drive to fix your infected computer system.
1) Download Safebytes Anti-Malware or MS Windows Defender Offline onto a virus-free computer system.
2) Mount the USB drive on the same computer.
3) Double-click the executable file to run the installation wizard.
4) Choose the USB flash drive as the destination for saving the file. Do as instructed on the screen to finish up the installation process.
5) Transfer the USB drive from the uninfected PC to the infected computer.
6) Double-click the EXE file to open the Safebytes tool from the thumb drive.
7) Run Full System Scan to detect and clean-up up all types of malware.
Protect Your PC and Privacy With SafeBytes Anti-Malware
If you’re looking to install an anti-malware application for your computer, there are several tools in the market to consider but you should not trust blindly anyone, irrespective of whether it is paid or free software. A few of them do a good job in removing malware threats while many will damage your computer by themselves. When searching for an antivirus tool, purchase one that offers reliable, efficient, and complete protection against all known viruses and malware. When considering commercial anti-malware software options, most people choose popular brands, like SafeBytes, and are very happy with them.
Safebytes is among the well-established computer solutions companies, which provide this all-inclusive anti-malware application. Through its cutting-edge technology, this software will help you protect your PC against infections brought on by various kinds of malware and other threats, including spyware, adware, computer viruses, worms, trojan horses, keyloggers, potentially unwanted program (PUPs), and ransomware.
SafeBytes anti-malware takes computer protection to a whole new level with its advanced features. Here are a few of the good ones:
Robust, Anti-malware Protection: Safebytes is built on the very best virus engine within the industry. These engines can find and eliminate threats even during the early phases of a malware outbreak.
Real-Time Protection: Malware programs trying to enter the computer are identified and stopped as and when detected by the SafeBytes real-time protection shields. This software will constantly monitor your PC for any suspicious activity and updates itself regularly to keep abreast of the constantly changing threat scenarios.
Internet Security: Safebytes assigns all websites a unique safety rating that helps you to get an idea of whether the webpage you’re going to visit is safe to browse or known to be a phishing site.
Lightweight: SafeBytes is a lightweight application. It uses up a really small amount of processing power as it works in the background so you’re free to use your Windows-based computer the way you want.
Premium Support: For any technical problems or product guidance, you may get 24/7 professional assistance via chat and e-mail.
Overall, SafeBytes Anti-Malware is a solid program since it has loads of features and could detect and eliminate any potential threats. You now may realize that this tool does more than just scan and eliminate threats from your computer. So when you want advanced forms of protection features & threat detections, purchasing SafeBytes Anti-Malware will be well worth the money!
Technical Details and Manual Removal (Advanced Users)
If you’d like to carry out the removal of AudioToAudio manually rather than utilizing an automated software tool, you can follow these simple steps: Go to the Windows Control Panel, click on the “Add/Remove Programs” and there, select the offending application to uninstall. In case of suspicious versions of web browser plugins, you can easily get rid of them through your browser’s extension manager. You may also want to reset your home page and search engine providers, as well as clear your browser cache and cookies.
If you decide to manually delete the system files and registry entries, utilize the following checklist to ensure that you know exactly what files to remove before undertaking any actions. However, this can be a tricky task and only computer professionals could carry it out safely. In addition, some malware is capable of replicating or preventing deletion. It is recommended that you do the removal procedure in Safe Mode.
For more information and manual removal instructions visit www.ErrorTools.com
Download Safebytes Anti-Malware: https://errortools.com/download/safebytes-anti-malware/
AudioToAudio is a browser extension for Google Chrome developed by Mindspark Inc. This extension allows users easy access to popular audio converting websites.
When installed, it changes the default search engine, home page, and new tab to MyWay.com. While active AudioToAudio gathers user browsing activities such as, but not limited to: visited websites, clicked links, search queries. This data is later used/sold by the Mindspark ad network to better target ads.
While browsing the internet with this extension enabled, you will see additional injected ads, sponsored content (such as links to web pages, banner ads, affiliate shop links, etc), and even pop-up ads from time to time if the regular ads are blocked.
AudioToAudio has been marked as a Browser Hijacker by several anti-virus applications and is marked for removal by most of them.


 The first thing that would pop into my mind is that I have lost tons of work and that something in my hardware has gone very wrong and it is dead. Luckily that is not the case and this error means that due to Windows update drivers were not properly transferred due to some compatibility issues, maybe it was a corrupt update file, etc. Of course, the reason could be hardware malfunction as well, but if everything was working fine before the update, it is a software issue, and I must say it is a common one and fixable. Please keep reading this guide in order to fix the Device not migrated error.
The first thing that would pop into my mind is that I have lost tons of work and that something in my hardware has gone very wrong and it is dead. Luckily that is not the case and this error means that due to Windows update drivers were not properly transferred due to some compatibility issues, maybe it was a corrupt update file, etc. Of course, the reason could be hardware malfunction as well, but if everything was working fine before the update, it is a software issue, and I must say it is a common one and fixable. Please keep reading this guide in order to fix the Device not migrated error.
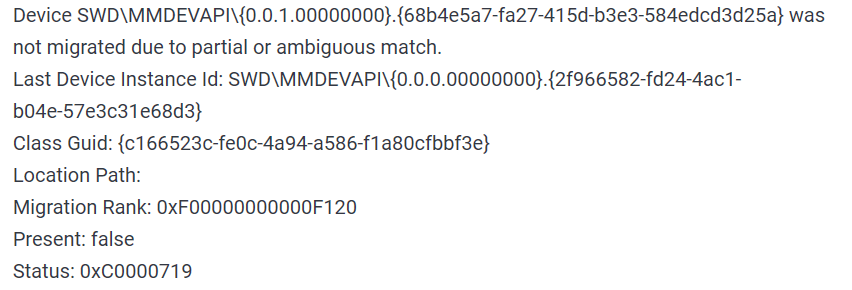
 Find device inside device manager, right-click on it, and choose properties. Go to the events tab and make sure that the device has migration issues.
Find device inside device manager, right-click on it, and choose properties. Go to the events tab and make sure that the device has migration issues.
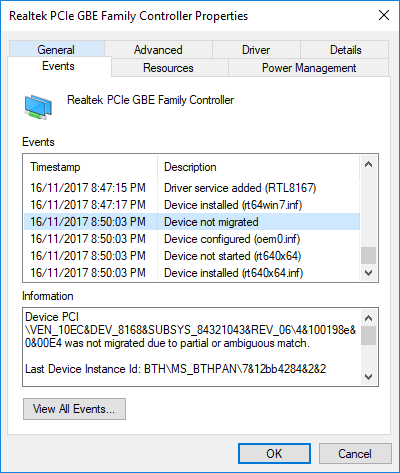 You have now 3 options for updating the driver, you can do it manually, automatically, or with the driver installer. We will cover all 3 options so you choose which one best suits you.
OPTION 1: Manually.
Close the Properties tab, go to the device manufacturer website and download the latest driver, if there are no drivers there, the only executable installer for the device skip this step and try the other 2. After you have downloaded the driver package from the website, right-click on the device and choose update driver.
You have now 3 options for updating the driver, you can do it manually, automatically, or with the driver installer. We will cover all 3 options so you choose which one best suits you.
OPTION 1: Manually.
Close the Properties tab, go to the device manufacturer website and download the latest driver, if there are no drivers there, the only executable installer for the device skip this step and try the other 2. After you have downloaded the driver package from the website, right-click on the device and choose update driver.
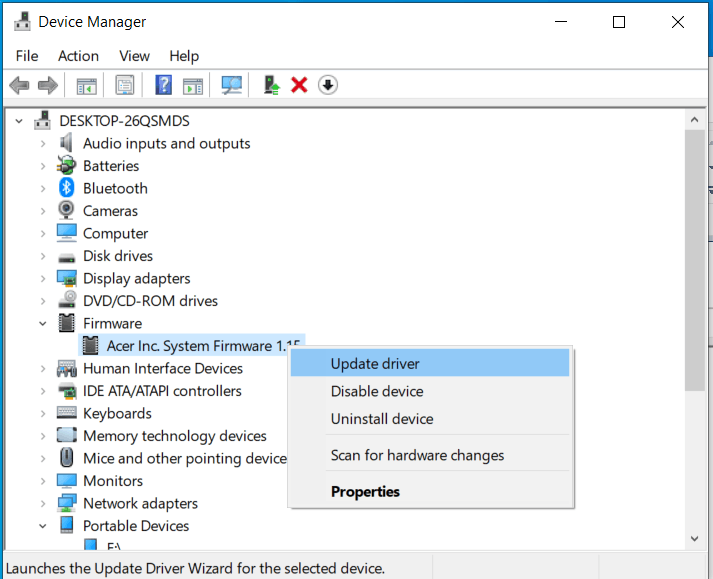 Now navigate to the folder where you have downloaded your driver package and update the driver. Reboot your system.
OPTION 2: Automatic update.
Close the Properties tab, right-click on the device and choose to uninstall.
Now navigate to the folder where you have downloaded your driver package and update the driver. Reboot your system.
OPTION 2: Automatic update.
Close the Properties tab, right-click on the device and choose to uninstall.
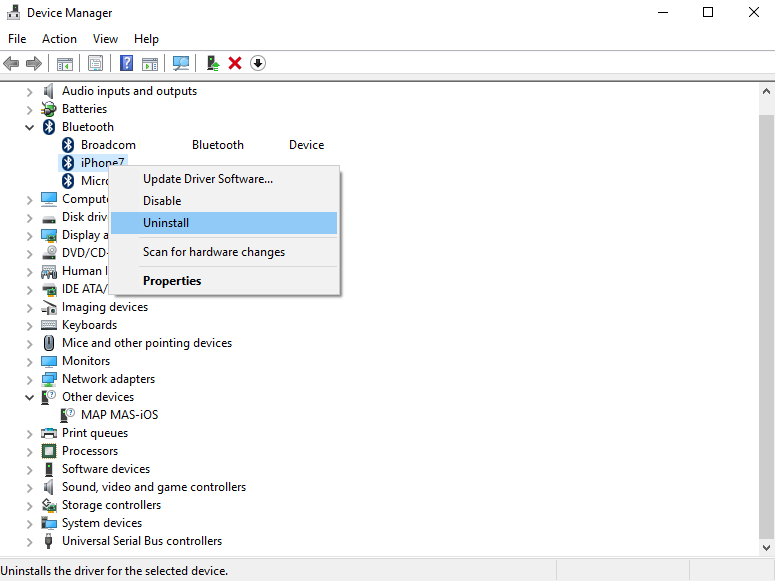 Once the device is uninstalled, restart your system, and Windows will automatically search and install the latest driver for the device.
OPTION 3: Via driver installer.
If you have downloaded .EXE or executable driver installer from device manufacturers web site try installing it, if the installation fails, try using compatibility mode for the installer. Navigate where the installer is located, right-click on it, and choose properties. Go to compatibility TAB and try installing it with administrator privileges in Windows 8 mode.
Once the device is uninstalled, restart your system, and Windows will automatically search and install the latest driver for the device.
OPTION 3: Via driver installer.
If you have downloaded .EXE or executable driver installer from device manufacturers web site try installing it, if the installation fails, try using compatibility mode for the installer. Navigate where the installer is located, right-click on it, and choose properties. Go to compatibility TAB and try installing it with administrator privileges in Windows 8 mode.
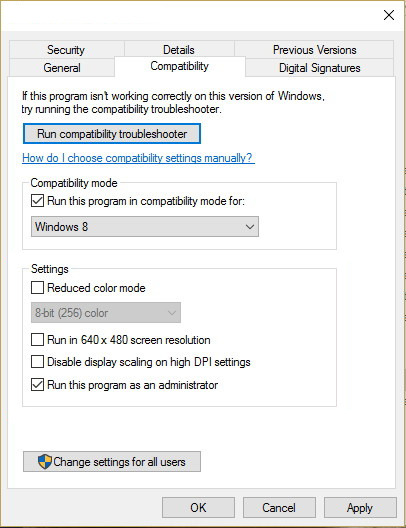 Reboot your system after this step.
This should solve the issues, however, if the issue still persists, follow the next steps.
Reboot your system after this step.
This should solve the issues, however, if the issue still persists, follow the next steps.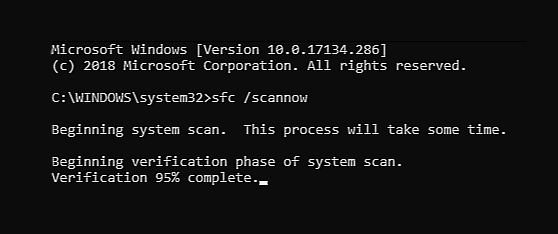 The scanning process and repair of files will take around 15 min. Leave it to finish completely, do not restart, work on the computer or shut it down while the process is active, and only after it is finished reboot your system.
The scanning process and repair of files will take around 15 min. Leave it to finish completely, do not restart, work on the computer or shut it down while the process is active, and only after it is finished reboot your system. Go to the Windows update tab and click on DOWNLOAD or click on check for updates for the latest Windows fix.
Go to the Windows update tab and click on DOWNLOAD or click on check for updates for the latest Windows fix.
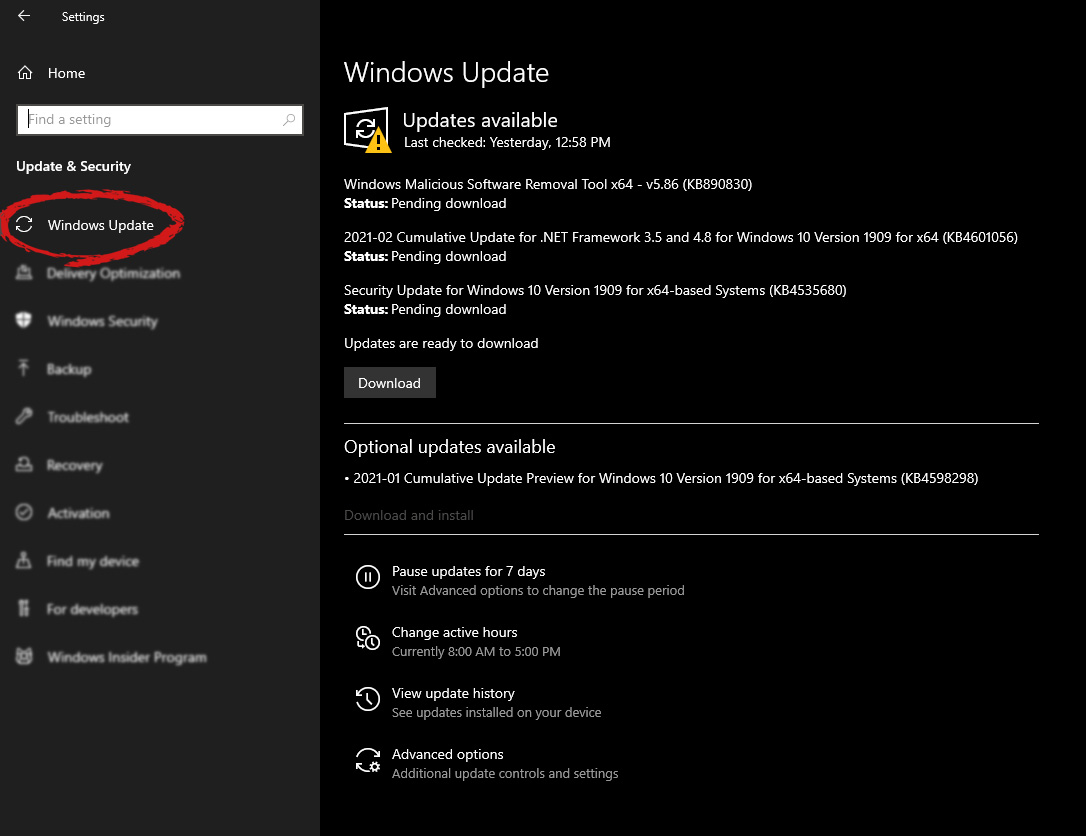
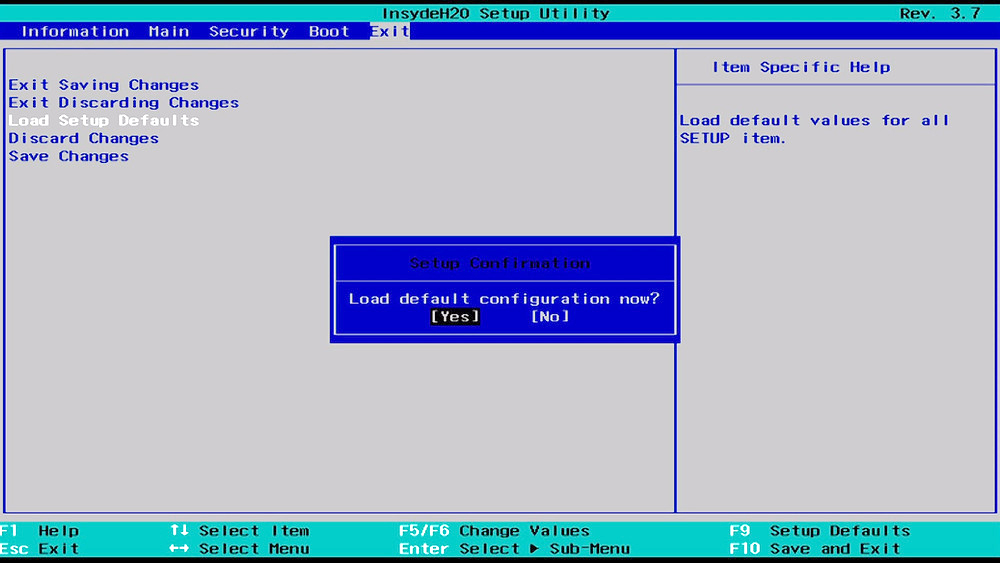
 In the run dialog, type control panel and press enter to enter control panel, locate recovery and click on it.
In the run dialog, type control panel and press enter to enter control panel, locate recovery and click on it.
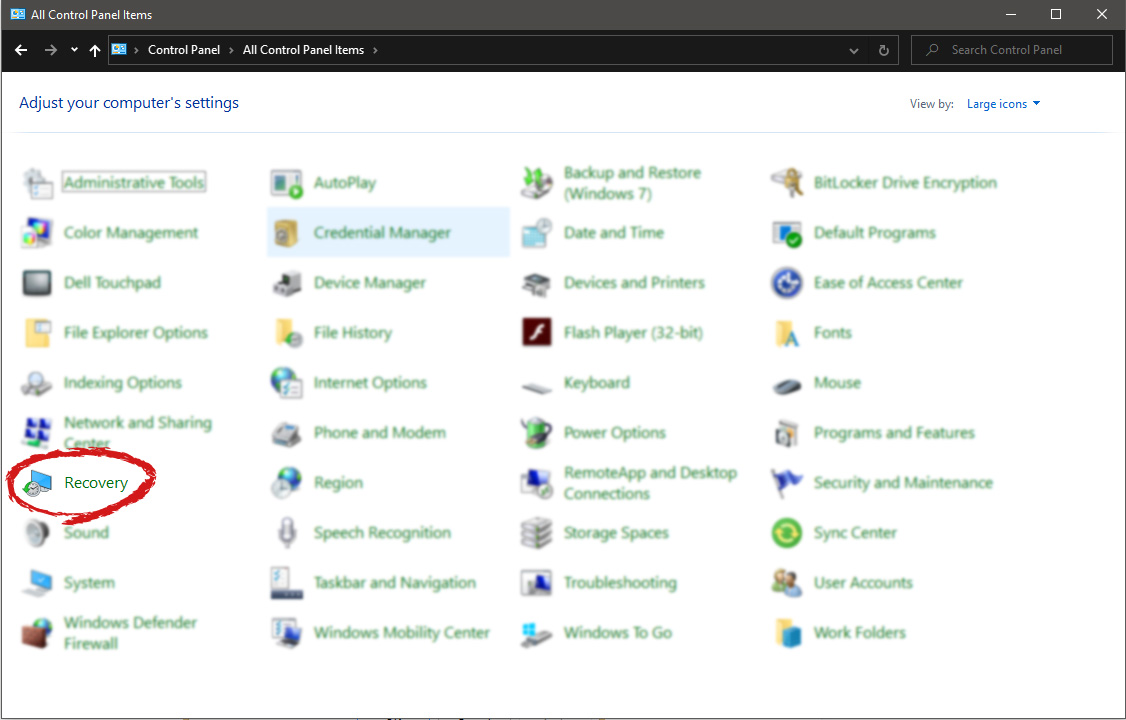 Inside the recovery screen click on Open System Restore.
Inside the recovery screen click on Open System Restore.
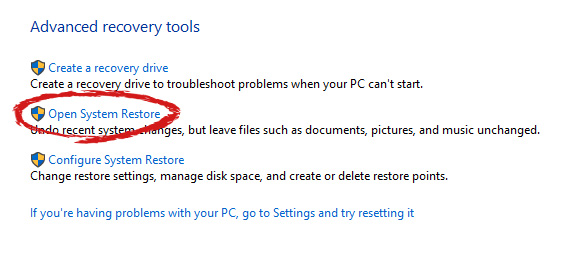 Choose a date when everything was working in order, the best bet is the date before Windows update and roll it back.
Choose a date when everything was working in order, the best bet is the date before Windows update and roll it back.
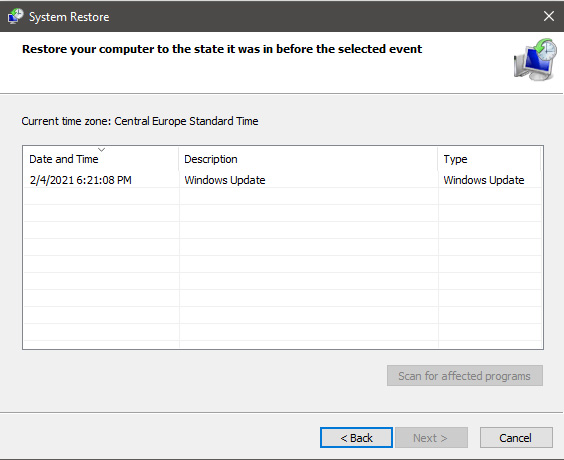 Click on date, and then on next.
Click on date, and then on next.