If you are trying to install or reinstall a program on your Windows 10 computer but encountered an error instead that says, “Fatal error, Installation fails, Installation ended prematurely because of an error”, then you’ve come to the right place as this post will guide you how you can fix it.
This kind of error is most likely caused by some files that may have been left behind by the previous installation of the program. Each time a program is uninstalled, it leaves behind its files and if the uninstallation process wasn’t completed properly, then it would result in errors like the
“Fatal error, Installation fails, Installation ended prematurely because of an error”.
Moreover, this kind of error is a generic one that can also occur with any software reinstallation or installation. And to fix this error, there are several suggestions you must check out. You can try to install or reinstall the program in a Clean Boot State or restart the Windows Installer Service. You could also try to re-register the Windows Installer Service or re-register the VBScript.dll file.
It is possible that there are some third-party applications in your computer that are preventing the program from getting installed and to isolate this possibility, you need to boot your computer in a Clean Boot State and then try installing the program again. Putting your computer in this state can help you identify which program is the culprit and thus isolates the problem. In a Clean Boot state, your computer will start using only the pre-selected minimal set of drivers and startup programs. Note that you have to disable and enable one process at a time.
The next thing you can do to fix the problem is to restart the Windows Installer Service. To do this, follow these steps:
You may have to re-register the vbscript.dll file using the regsvr32.exe before you can successfully install the program and fix the error. The Regsvr32 tool is a command-line utility that can be used to register and un-register the OLE controls like DLL and ActiveX (OCX) control in the Windows operating system. Follow the steps below to use it.

 Error Causes
Error Causes Error Causes
Error Causes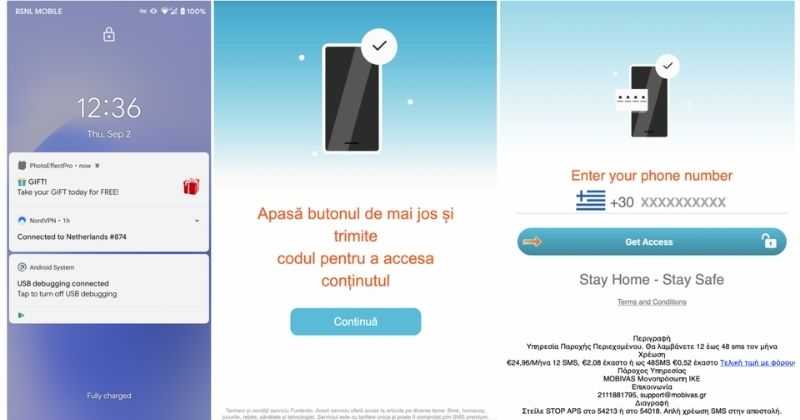 According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
According to Zimperium zLabs, this malware that was recently detected has been doing its scams and attacks even in November of 2020 and has thus far accumulated hundreds of thousands of dollars in its scam.
On the surface it looks very harmless, asking for typical permissions like internet access, calls, and other related needed functions, and then it waits. After few months the real attack happens when users get charged with premium service they never subscribed to in the first place.
‘HTMLayout.dll cannot be loaded to properly start GUI. Therefore process cannot continue’, ‘Htmlayout.dll not found’, ‘The file htmlayout.dll is missing’,and so on, then your system may be exposed to serious privacy and security threats.
 Error Causes
Error Causes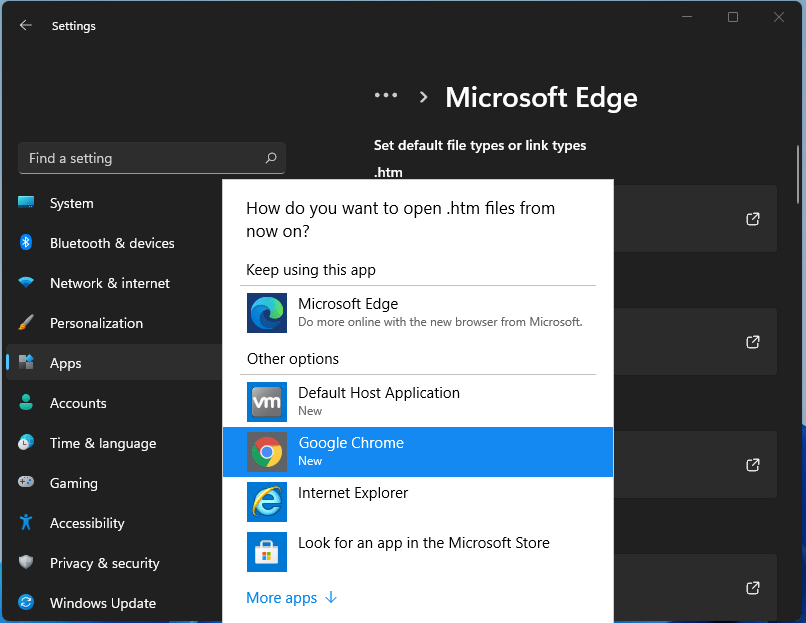 For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required.
For anyone who is not aware, when Windows 11 was released if you wanted to switch to another browser you had to go into the settings app and choose the default browser for different types of file extensions like HTML, HTM, PDF for opening on the web, etc. Of course, this was completely unnecessary and it was not well received by users. So after some time, Microsoft backpedaled to standard one click, choose your default browser solution that existed in the previous version of Windows OS.
Altho sometimes Microsoft knows how to irritate its users base, it is good to know that they can also listen and fix things that are required. ‘Error Message: Error 118 (net::ERR_CONNECTION_TIMED_OUT): The operation timed out.’
 Error Causes
Error Causes