Error Code 0x8024001e - What is it?
Error Code 0x8024001e is most commonly associated with the installation of apps from the Windows store, although versions of the error have been present in multiple versions of the Windows operating system. At its most basic level, the error says that a program has not been installed, even after the installation wizard has run through to completion.
Common symptoms include:
- Inability to open or run apps downloaded from the Windows store
- The error message reads, “Something happened and this app couldn’t be installed. Please try again.”
The solutions to Error Code 0x8024001e are somewhat complex, so it is a good idea to get in touch with a computer repair professional if you do not feel confident in your ability to follow the steps below to complete. However, most users should be able to follow the steps below and achieve the desired results.
Solution
 Error Causes
Error Causes
There are a couple of different causes that can lead to the appearance of Error Code 0x8024001e. In some cases, extraneous data left in the app cache can cause the problem. In other cases, particular processes may need to be manually reset to clear the problem. Last, but not least, unresolved updates may lead to Error Code 0x8024001e causing issues with downloaded and installed apps from the Windows Store.
Further Information and Manual Repair
There are three primary methods to address the appearance of Error Code 0x8024001e. These should work for all users, regardless of the specific cause for their machine. The methods below do require some advanced skills in computing, so be sure to contact a Windows repair technician if you have trouble following the instructions below.
Here are the top ways to repair Error Code 0x8024001e on Windows 10:
Method One: Clear the App Cache and Use Power User Options
In many cases, simply clearing your app cache can resolve the errors that pop up when you are downloading, installing, or updating any apps that have come from the Windows store. This method may not perfectly resolve the problem every time, but it is a step that should always be done before any others.
Next, open up the Power User options by pressing both the Windows key and the X key at the same time. Choose “Command Prompt (Admin)” from the options that appear. Then type in the commands into the prompt, one at a time:
- net stop wuauserv
- cd/windows
- rename SoftwareDistribution SoftwareDistribution.bck
- net start wuauserv
Restart your computer after these changes have been made so that all changes can take effect. You may be able to access the desired programs and apps after this is complete.
Method Two: Run Your Registry Repair Tools
Sometimes, the best way to repair Error Code 0x8024001e is to simply open up the Window Registry tools and run the repair process. This will scan your registry for any errant entries, corrupted entries, or missing entries, repairing them automatically as the device is able to do. This process may take some time to complete, so plan accordingly.
After this process is complete, it is always a good idea to restart your computer to apply any changes that have been made. Reattempt to install or run the program in question one this is done.
Method Three: Run Windows Updates as Necessary
Last, open up the Windows Update tools to check to see if any of your programs need to be updated or if your operating system needs to be updated. Install each of the updates, restarting your computer after the entire process has been completed so that they can fully take effect on your machine. You should be able to run the programs that had caused problems once this is complete.
It is important to keep up-to-date on your system and program updates to avoid future errors in installations and downloads from the Windows store.
In most cases, using the steps above should allow you to use the apps that you’ve downloaded from the Windows store without Error Code 0x8024001e popping back up. If the problem persists or if you have not been able to follow the steps listed above to remedy the error, it is a good idea to contact a qualified professional who is experienced in working with Windows 10 errors.
Method Four: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.


 Razer had some strange dives into stuff not really aimed at gamers and the gaming community overall like its Zephir smart mask and now it is venturing into the area of smartwatches teaming up with Fossil. I am not clear if this initiative was set in motion by Razer or Fossil and I really do not know why limited production numbers. Officially named RAZER X FOSSIL GEN 6 SMARTWATCH, this watch comes with the official following text on Razer's page:
Razer had some strange dives into stuff not really aimed at gamers and the gaming community overall like its Zephir smart mask and now it is venturing into the area of smartwatches teaming up with Fossil. I am not clear if this initiative was set in motion by Razer or Fossil and I really do not know why limited production numbers. Officially named RAZER X FOSSIL GEN 6 SMARTWATCH, this watch comes with the official following text on Razer's page:
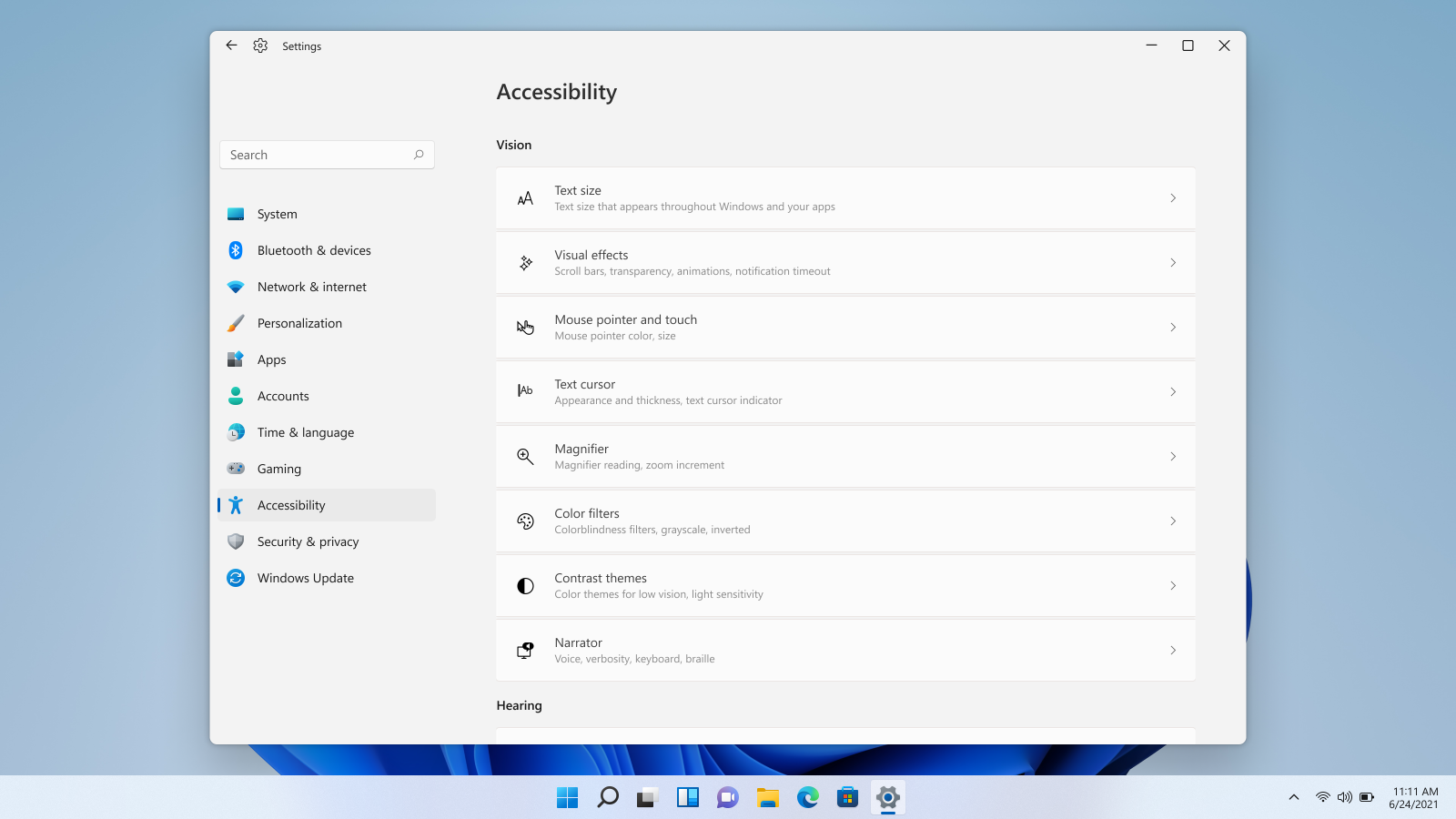 Windows 11 provides several different ways to make your cursor stand out and be easier to spot inside it. You can make the mouse pointer larger, invert it, or change its color.
Windows 11 provides several different ways to make your cursor stand out and be easier to spot inside it. You can make the mouse pointer larger, invert it, or change its color.
 History of Commodore
History of Commodore With sales booming and the early reliability issues with the hardware addressed, software for the C64 began to grow in size and ambition during 1984. This growth shifted to the primary focus of most US game developers. The two holdouts were Sierra, who largely skipped over the C64 in favor of Apple and PC compatible machines, and Broderbund, who was heavily invested in educational software and developed primarily around the Apple II. In the North American market, the disk format had become nearly universal while cassette and cartridge-based software all but disappeared. So most US-developed games by this point grew large enough to require multi-loading.
At a mid-1984 conference of game developers and experts at Origins Game Fair, Dan Bunten, Sid Meier, and a representative of Avalon Hill said that they were developing games for the C64 first as the most promising market. By 1985, games were an estimated 60 to 70% of Commodore 64 software. Over 35% of SSI's 1986 sales were for the C64, ten points higher than for the Apple II.
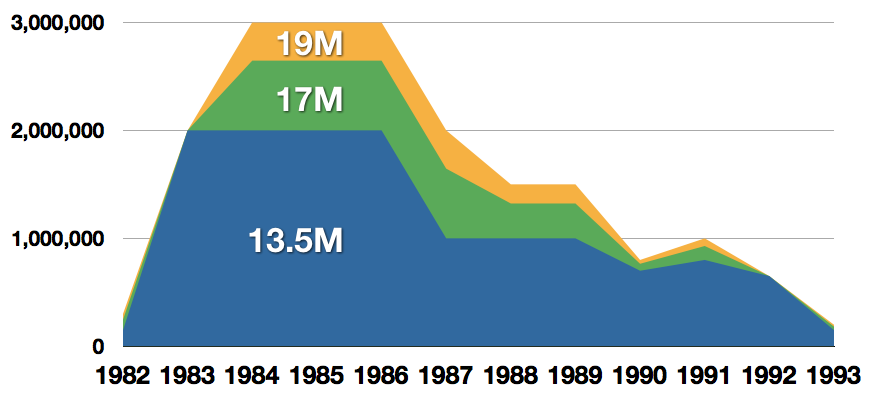
Everything was great for Commodore but the industry was moving forward and by the year 1988, PC compatible computers were stated to be the largest and fastest-growing home entertainment systems pushing C64 on to second place. Also, Nintendo’s gaming system has started to take hold in the world with amazing 7 million systems sold in 1988 only.
By the year 1991, many developers exited the gaming market for Commodore 64 home computer system and its popularity started to fall due to lack of software and not so many hardware changes.
With sales booming and the early reliability issues with the hardware addressed, software for the C64 began to grow in size and ambition during 1984. This growth shifted to the primary focus of most US game developers. The two holdouts were Sierra, who largely skipped over the C64 in favor of Apple and PC compatible machines, and Broderbund, who was heavily invested in educational software and developed primarily around the Apple II. In the North American market, the disk format had become nearly universal while cassette and cartridge-based software all but disappeared. So most US-developed games by this point grew large enough to require multi-loading.
At a mid-1984 conference of game developers and experts at Origins Game Fair, Dan Bunten, Sid Meier, and a representative of Avalon Hill said that they were developing games for the C64 first as the most promising market. By 1985, games were an estimated 60 to 70% of Commodore 64 software. Over 35% of SSI's 1986 sales were for the C64, ten points higher than for the Apple II.
Everything was great for Commodore but the industry was moving forward and by the year 1988, PC compatible computers were stated to be the largest and fastest-growing home entertainment systems pushing C64 on to second place. Also, Nintendo’s gaming system has started to take hold in the world with amazing 7 million systems sold in 1988 only.
By the year 1991, many developers exited the gaming market for Commodore 64 home computer system and its popularity started to fall due to lack of software and not so many hardware changes.
 Commodore announced that the C64 would be finally discontinued in 1995.
However, only one month later in April 1994, the company filed for bankruptcy. When Commodore went bankrupt, all production on their inventory, including the C64, was discontinued, thus ending the C64's 11 and a half year production.
Commodore announced that the C64 would be finally discontinued in 1995.
However, only one month later in April 1994, the company filed for bankruptcy. When Commodore went bankrupt, all production on their inventory, including the C64, was discontinued, thus ending the C64's 11 and a half year production.
 Zak McKracken and the Alien Mindbenders
Zak McKracken and the Alien Mindbenders
 If you are not keen on spending money for reliving and checking games or software of C64 here are some links to help you to at least experience part of it completely free.
Commodore 64
If you are not keen on spending money for reliving and checking games or software of C64 here are some links to help you to at least experience part of it completely free.
Commodore 64 