Error Code 0x80070032 - What is it?
Error Code 0x80070032 is a command that most often relates to codes or commands that have not been entered correctly or do not apply to the given program. It can also appear when mail folders in Windows Mail are not able to sync in the way that they should between the local device and the servers owned by Microsoft.
Common symptoms include:
- Inability to access your emails
- Emails not syncing between devices correctly
- Inability to use certain commands in certain programs
The primary methods used to address Error Code 0x80070032 are fairly basic and easy to complete. Most users should be able to complete these methods on their own and they do not require a lot of time to do. However, if you don’t feel like you have the experience, skills, or knowledge necessary to complete the steps listed below, consider getting in touch with a qualified Windows repair technician to assist you.
Solution
 Error Causes
Error Causes
The two main causes for Error Code 0x80070032 are commands entered into programs that cannot be completed or are incompatible with the program at hand and folders in Windows Mail that cannot sync properly.
Further Information and Manual Repair
There are three basic methods that users can try in order to resolve Error Code 0x80070032 on their machine. These are fairly simple and easy to complete. However, if the methods below aren’t successful in resolving the error code or if you do not feel confident in your ability to use them, get in touch with a certified Windows repair professional to assist you.
If you believe that you are seeing the error due to entering a command that didn’t work, use Method One first. If you believe it is due to a mail syncing error, use Methods Two or Three.
Here are the top methods for addressing Error Code 0x80070032:
Method One: Reinstall the Program in Question
If you believe that you are experiencing Error Code 0x80070032 because of a command that you have entered, the best solution is to reinstall the program in which you were entering the command. You may also want to try updating your program, if able, before reinstalling it. Remember to restart the computer before reattempting to enter in the command that caused the error.
Method Two: Download and Install Windows System Updates
For many users, Error Code 0x80070032 appears because of a bug in one of the versions of Windows 10. If you believe that this is the case, open up your Windows Updates and check to see if there are any updates that you can install.
For users who are only seeing Error Code 0x80070032 because of the bug mentioned above, Windows released an update that should address the error code on its own. If your computer is fully updated, the error may be resolved on its own. Always remember to restart your computer after installing updates so that the necessary changes can take effect.
Method Three: Change Your Windows Mail to Local Access
If the above methods did not resolve the problem successfully, you can switch to local access to your Windows Mail, rather than relying on Microsoft access. To do so, complete the following steps:
- Go into your Windows settings and click on the option for “Accounts.”
- Select the account that you wish to access and choose the option to sign in using a local account.
- Enter your password to verify local access.
- Add in your user name, password, and password hint.
- Sign out of the local account to finish.
Once this is done, you can switch back to your Microsoft account, which should reset your syncing ability. Follow these steps to switch back:
- Go back into your settings, selecting “Accounts” and choosing the proper account.
- Change the option to sign in with a Microsoft account.
- Enter your password, then your username and password again.
- Select “Switch” to change back to the Microsoft account.
Method Four: Use An Automated Tool
If you wish to always have at your disposal a utility tool to fix these Windows 10 and other related issues when they do arise, download and install a powerful automated tool.


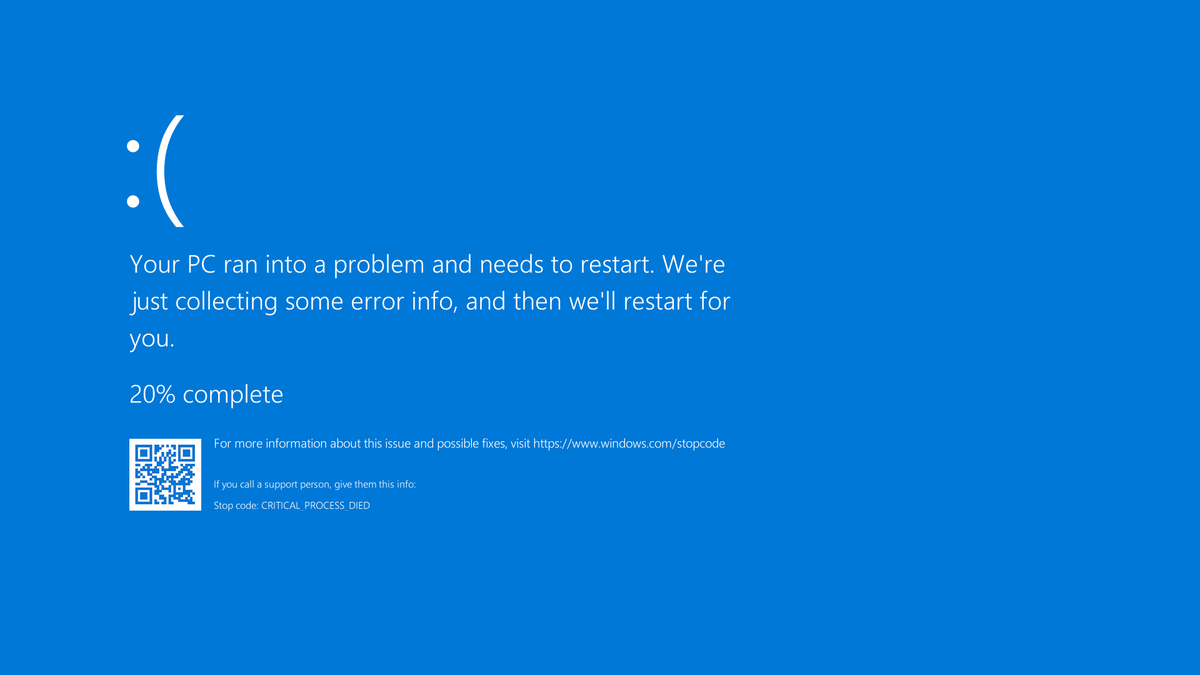 A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
A stop error or exception error commonly called the blue screen of death (BSoD) or blue screen, is an error screen displayed on Windows computers following a fatal system error. It indicates a system crash, in which the operating system has reached a condition where it can no longer operate safely. This is caused by many different problems, such as a general hardware failure or a crucial process terminating unexpectedly.
 On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update.
On Windows 10 systems, a Black Screen of Death can be caused by an unfinished Windows Update. It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
It is a diagnostic screen with a white type on a pink background. Pink Screen is mainly seen when the VMkernel of an ESX/ESXi host experiences a critical error, becomes inoperative, and terminates any virtual machines that are running. It is not fatal and generally considered more of a developer testing issue. When encountered, it can be fixed quickly by following the simple action of pressing and holding your computer’s power button to shut down the device.
 The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers).
The Microsoft Windows 10 Operating System Brown Screen of Death is an on-screen fatal error notification with bug check codes which is seen when a computer crashes due to graphics hardware or software-related problems (failing graphics drivers). It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
It affects the functioning of a browser, particularly Mozilla Firefox. The Yellow Screen of Death makes the appearance with a weird buzzing sound in the background when the XML parser refuses to process an XML document causing a parsing error and a weird buzzing sound. The issue persists unless the computer is manually rebooted.
 Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.
Commonly the Windows 10 red screen is caused due to the hardware error, particularly if you overclock your Windows PC/laptop. Despite this, sometimes the red screen of death is also caused by outdated or incompatible drivers or due to BIOS issues.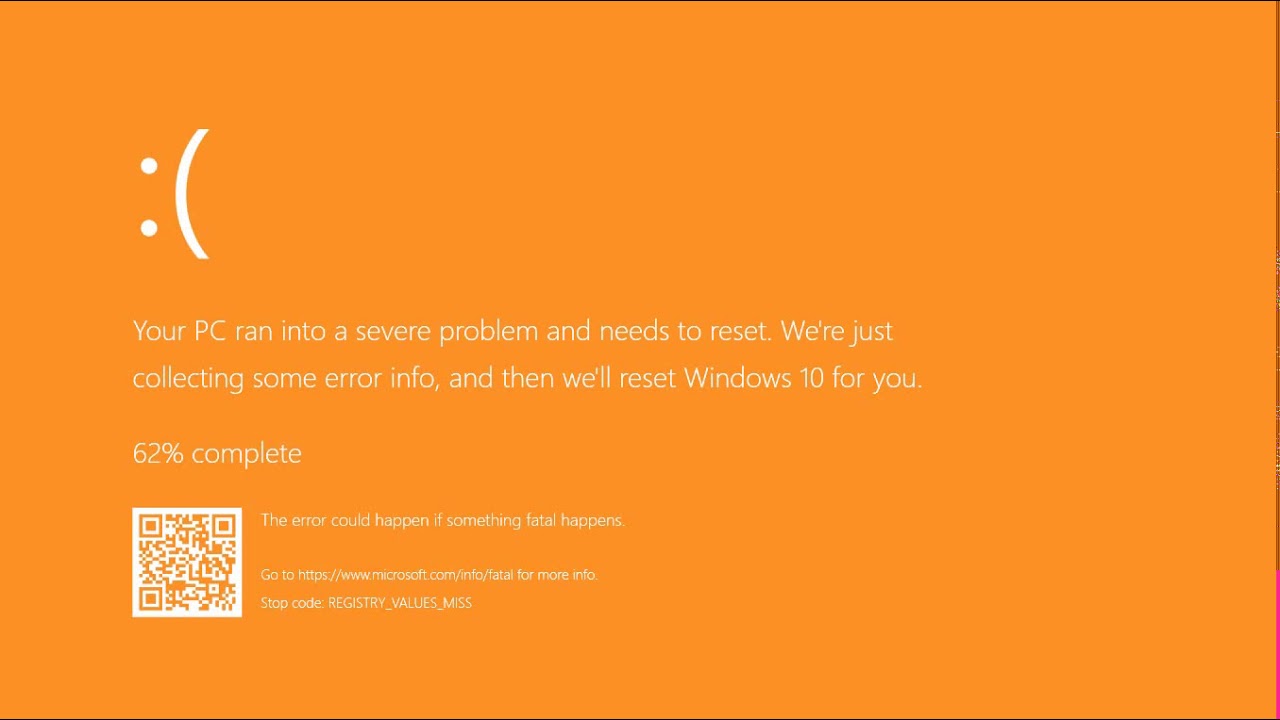 The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
The Orange Screen of Death on Windows occurs due to fatal hardware errors. Multiple reasons have been reported for the Orange Screen of Death. Some had this issue when watching a YouTube video, some were not able to boot into Windows. It can even occur when waking up from Sleep.
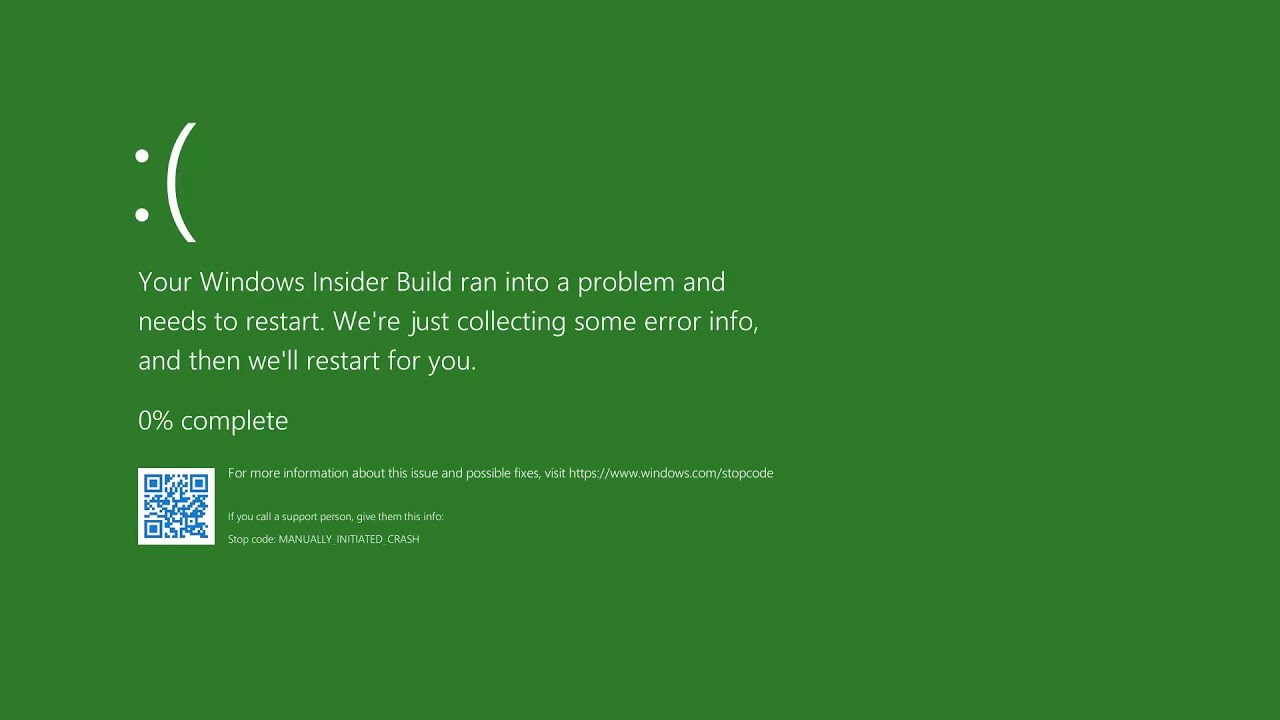 The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10.
The green screen of death only appears when you're running an Insider Preview version of Windows 10. It's the same as the blue screen of death, and it will show the same error messages. ... If you see a green screen of death (GSOD) on your PC, that's a sign you're using an Insider Preview build of Windows 10. The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware.
The White Screen on Windows is also an error where the screen of the computer just turns white and freezes. There can be several things that can cause the white screen to appear on the Windows laptop monitor. But the main issue could be because of malfunctioning of the graphics hardware. 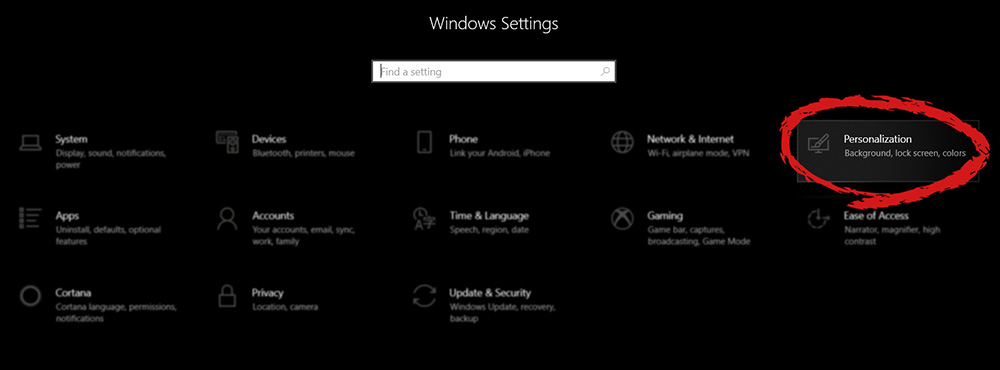 Under personalization options click on START.
Under personalization options click on START.
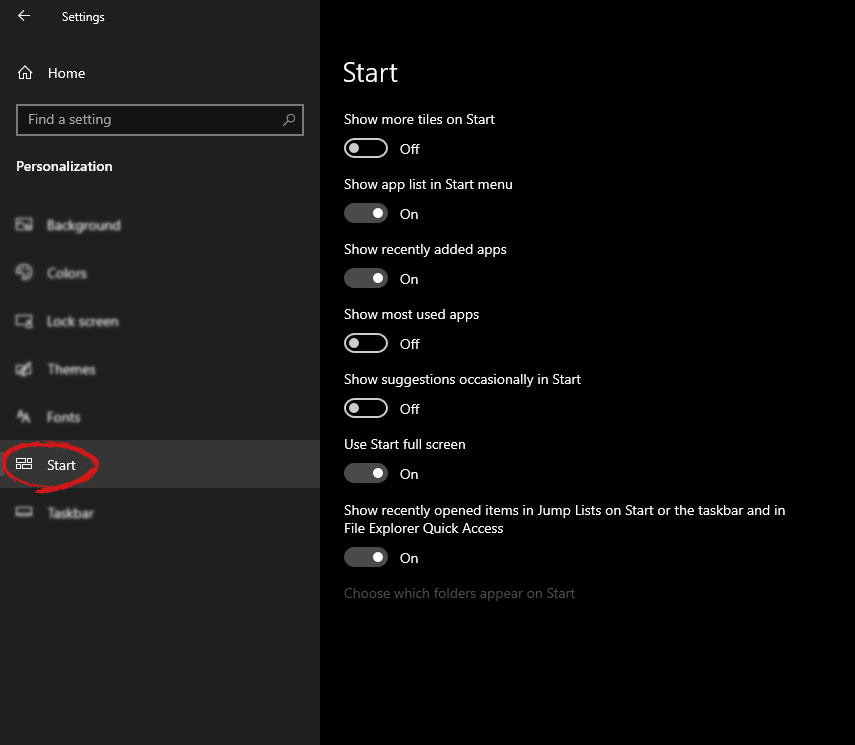 And then on the right part click on the button under Use Start full screen to turn it ON
And then on the right part click on the button under Use Start full screen to turn it ON
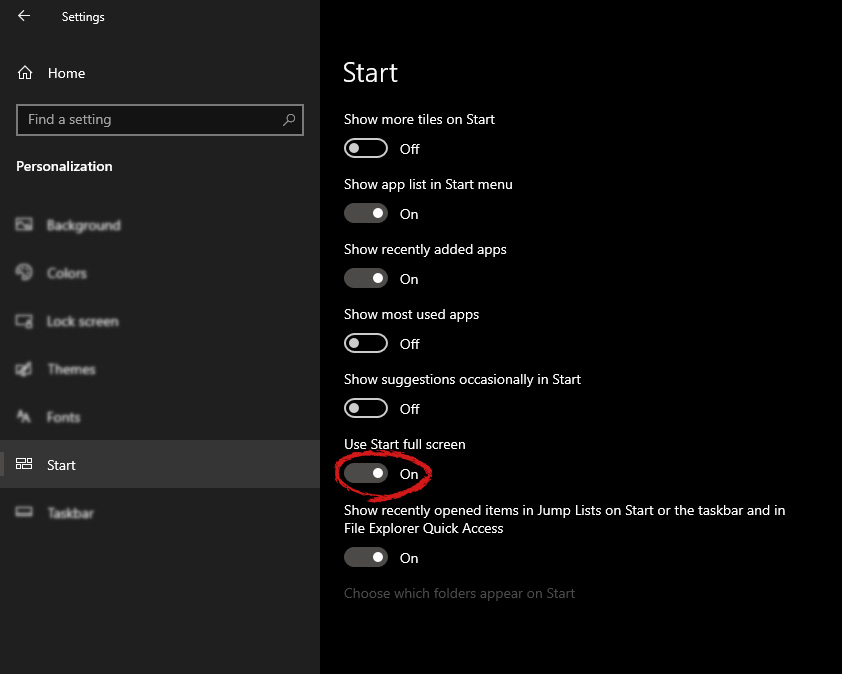 That's it, your start menu is now full screen.
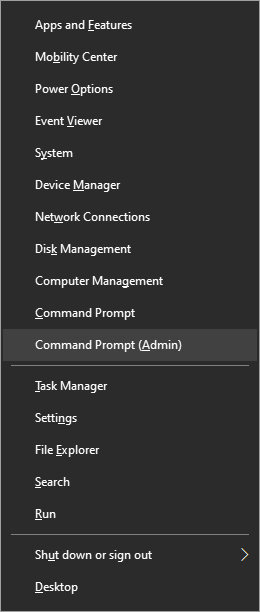
That's it, your start menu is now full screen.  Click on command prompt (admin)
Click on command prompt (admin)
 Type in command prompt following:
Type in command prompt following:
 Windows 11 has some cool animations including fading effects which make working in it feels nice and futuristic but the cost of this is that there is a slight delay to certain actions performed. If you want the snap fast feature in Windows 11 and do not care about this eye candy there is an easy way to turn animations off inside it.
Windows 11 has some cool animations including fading effects which make working in it feels nice and futuristic but the cost of this is that there is a slight delay to certain actions performed. If you want the snap fast feature in Windows 11 and do not care about this eye candy there is an easy way to turn animations off inside it.
