Error Code 0x803f7001 – What is it?
Error code 0x803f7001 results when users fail to update their Windows operating system. This often occurs when they seek to update from Windows 8 or 8.1 to Windows 10. Users will be able to identify error code 0x803f7001 because of the following common symptoms which occur:
- Inability to upgrade your Windows operating system to Windows 10
- Message box with error code 0x803f7001
Solution
 Error Causes
Error Causes
The causes for error code 0x803f7001 are usually associated with the use of an unlicensed version of Windows 8 when upgrading to Windows 10. In such cases, the error code occurs when there is no valid Windows license or product key on your device.
Further Information and Manual Repair
To fix error code 0x803f7001, users may not necessarily need technical knowledge or the help of a Windows repair technician. Usually, the process is simple and can be resolved with the use of a valid product key. However, if users have trouble implementing the instructions found in the manual repair methods listed below, contact a Windows repair specialist for help or use an automated tool that provides the best solutions for problems like error code 0x803f7001.
Method One: Use a Valid Product Key
A product key is a 25-character code that enables users to activate their Windows operating system. To successfully activate your operating system and resolve error code 0x803f7001, enter the product key in the correct order. Once you have a valid product key in your possession, begin to resolve the error code by following the instructions below:
- Step one: Click the Start button then select Settings
- Step two: Select Update & security then Activation
- Step three: Click the Change product key
- Step four: Type in your valid product key. (Ensure you include the 25 characters of your product key in the correct order.)
Once you type in the valid product key, you should be able to successfully upgrade to the latest version of Windows. However, this method is only effective if the error code 0x803f7001 on your device is caused by issues related to the product key.
If the error code reappears after attempting manual repair method one, move to the next manual method suggested below.
Method Two: Reinstall Genuine Version of Windows 8
This method is crucial for you to perform if method one was not successful. Begin the reinstallation process by ensuring you have a genuine version of Windows 8. After reinstalling this version of your Windows operating system, attempt to upgrade to Windows 10 by following the instructions below:
- Step one: Type Settings in the search box near the Start button or click the Start button and select Settings
- Step two: After clicking Settings, select Update & Security
- Step three: Select Windows Update then the Check for updates tab
- Step four: Activate Windows 10 update
If this method is successful, you will no longer see error code 0x803f7001 pop up in a message box. You will also be able to access Windows 10, and all the benefits it provides users, on your device.
Method Three: Install an Automated Tool
Automated tools help PC users eliminate common issues such as Windows error codes. To address or rectify error codes like error code 0x803f7001 download a powerful automated tool on your machine. This tool enables users to access quick solutions. It also scans for and corrects issues that may result in error codes or poor PC performance.


 Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
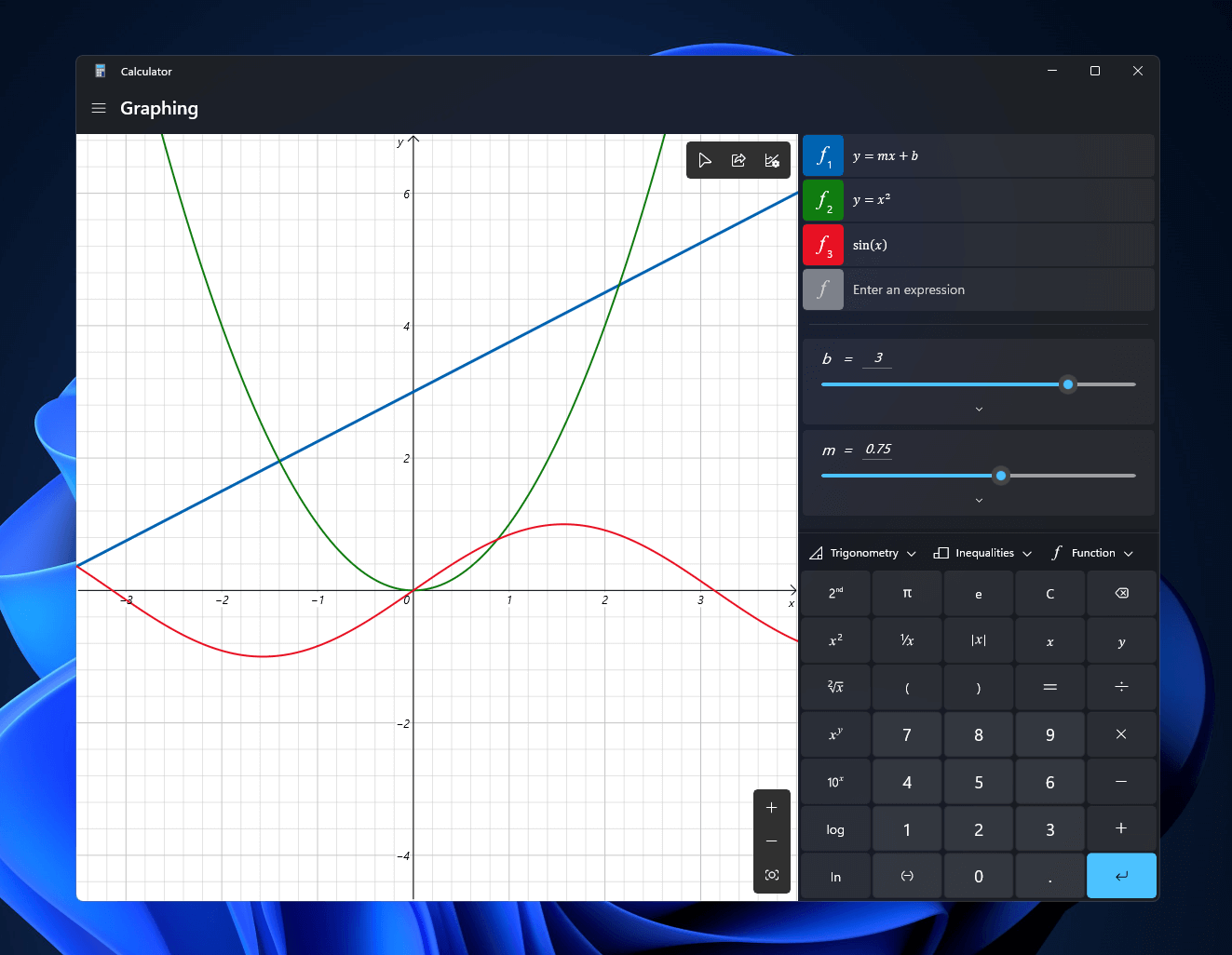
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
Windows 11 will bring some old applications in new looks and some will get additional features as well. One of the old apps that will get new stuff is a calculator.
The calculator was always a way to go application for quick calculations but Microsoft aims to expand on that and make the calculator a little more useful.
The first thing that you will notice is the calculator look, the calculator has now an application theme setting that allows you to change the look of the application. It comes in standard and professional mode as usual but this time calculator will come with features that will enable it to handle some programming and engineering tasks.
The new calculator features a full graphing mode that lets you visually analyze a graph to identify key features. It also packs a deep converter that can switch between more than 100 units and currencies.
 Speaking of old players of old Diablo 2, they can transfer their old characters into remaster and continue playing them within this new great HD environment. There are some steps and requirements but we are here to help and transferred characters will bring full stash, inventory, and equipped items with them.
Speaking of old players of old Diablo 2, they can transfer their old characters into remaster and continue playing them within this new great HD environment. There are some steps and requirements but we are here to help and transferred characters will bring full stash, inventory, and equipped items with them.
