Raptor Lake, a new and upcoming Intel 13th generation CPU will break the 6GHz barrier for the first time ever in normal working mode, overclocked mode in Intel words will go as high as 8GHz. CPU will be 15% faster than Alder lake in single-threaded tasks and a stunning 41% faster in multi-threaded workloads.
The current world record for overclocking is 8.72GHz done with AMD FX-8370 and Intel is aiming at breaking that record with Raptor Lake, of course, this kind of extreme overclocking will require some top-of-the-line nitrogen cooling systems.

Raptor Lake will run on the current LGA 1700 socket, so you will not need to buy another motherboard for CPU and they will also be manufactured on a 10nm process which means that you will need to take care of cooling and power supply if they really go over 6GHz.
Mid-range Intel Core i5-13600K processor will come with 14 cores inside and 20 threads running at a maximum P-core frequency of 5.1GHz, while Core i7-13700K will have 16 cores and 24 threads and run on 5.3GHz max P-core frequency. Best i9-13900K will come packed with 24 cores, 8 of them will be P-cores, and the rest 16 are E-cores, and 32 threads. It will reach 5.4GHz frequency but it was stated it can go to 5.8GHz with Thermal Velocity Boost.
After this statement, we can clearly see that the 6GHz breaker CPU will probably be an i9 special KS variant. In other words, specially tested and picked existing i9 running at higher speeds as was with Alder Lake as well where normal i9-12900K ran at 5.2GHz while i9-12900KS was running at 5.5GHz.
 When File Explorer opens go to VIEW > OPTIONS. Inside options select “Show hidden files, folders, and drives”, uncheck “Hide protected operating system files (Recommended)”, and click APPLY > OK
When File Explorer opens go to VIEW > OPTIONS. Inside options select “Show hidden files, folders, and drives”, uncheck “Hide protected operating system files (Recommended)”, and click APPLY > OK In the command prompt type in the following: rd /s /q C:\$Recycle.bin
In the command prompt type in the following: rd /s /q C:\$Recycle.bin



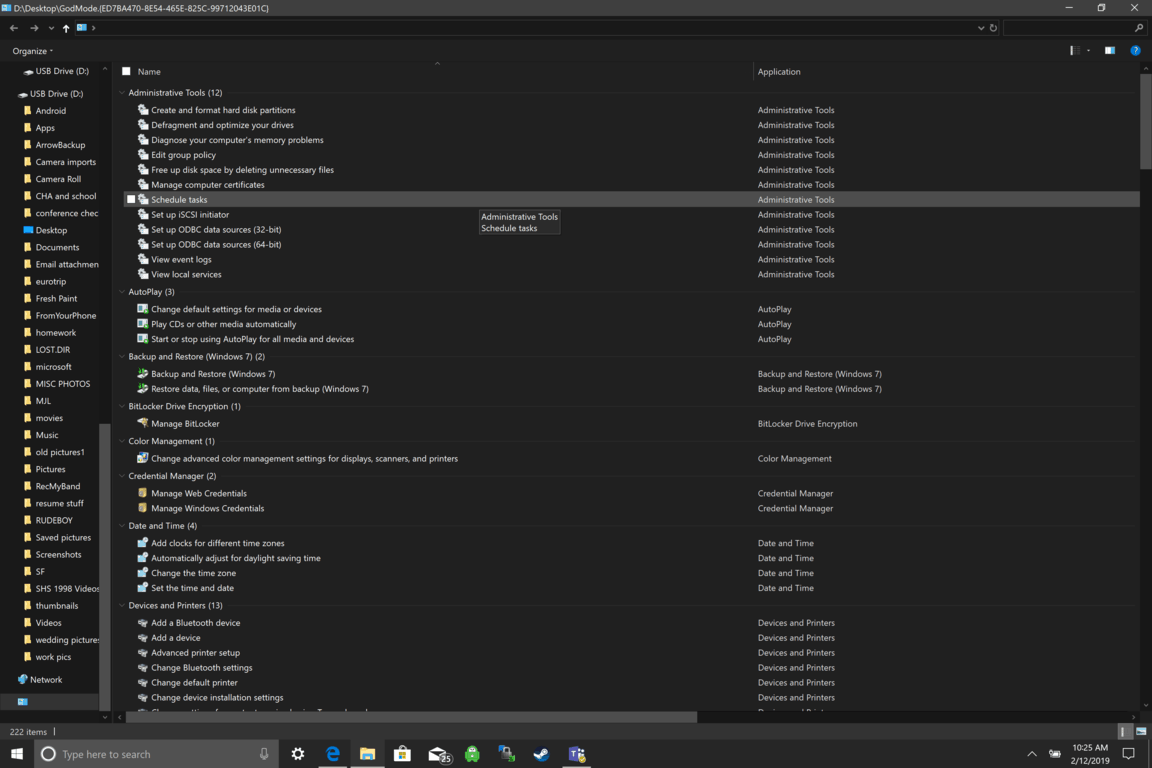 Like in Windows 10, Windows 11 will also support God mode to be enabled and used. For those readers that do know what God mode is, let me explain it in simple terms. God mode is the icon on the desktop that once clicked will open and let you adjust every option in the control panel and some hidden features for Windows inside one application.
There are a lot of advantages to having this one-click fast access to features, especially if you are a power user. Luckily creating such an awesome icon and enabling God mode is very easy to accomplish, all you have to do is:
Like in Windows 10, Windows 11 will also support God mode to be enabled and used. For those readers that do know what God mode is, let me explain it in simple terms. God mode is the icon on the desktop that once clicked will open and let you adjust every option in the control panel and some hidden features for Windows inside one application.
There are a lot of advantages to having this one-click fast access to features, especially if you are a power user. Luckily creating such an awesome icon and enabling God mode is very easy to accomplish, all you have to do is:
