The Motitags toolbar browser add-on was created by Mindspark Inc. and is compatible with Internet Explorer and Mozilla Firefox. It claims to enhance users’ Internet browsing experience by enabling smileys within popular email clients such as Gmail, Yahoo!, AOL, and Outlook Live. While such added functionality may seem useful, Internet users should be aware that this browser plugin is categorized as a Browser Hijacker due to its behavior.
When installed this extension changes your default search engine, the home page, and new tab to MyWay.com, and while installed it gathers user browsing data and sends it back to Mindspark servers. This data is later used to inject additional unwanted ads into the user’s browser search results.
About Browser Hijackers
Browser hijacking is actually a type of unwanted software program, often a web browser add-on or extension, which then causes modifications in the web browser’s settings. Browser hijacker malware is developed for a number of reasons. These are generally used to force hits to a specific website, manipulating web traffic to generate ad revenue. It could seem harmless, but the majority of these websites aren’t legitimate and could pose a serious threat to your online safety. In a much worst case, your internet browser could be hi-jacked to open up your computer to a host of additional computer infections.
How one can identify a browser hijack
There are several signs of browser hijacking. Here are a few of them: the home page of your browser is changed unexpectedly; you get re-directed to websites you never intended to visit; the essential web browser settings are altered and unwanted or unsafe resources are added to the trusted websites list; discover new toolbars that you didn’t add; endless pop-up adverts show up and/or your web browser popup blocker is disabled; your browser gets sluggish, buggy, crashes frequently; you can’t navigate to certain internet pages, for example, security software related websites.
So how does a browser hijacker infect a computer?
Browser hijackers infect computers via malicious email attachments, downloaded infected files, or by going to infected sites. Many internet browser hijackings come from add-on software, i.e., toolbars, browser helper objects (BHO), or plug-ins added to browsers to provide them extra capabilities. Browser hijackers sneak into your pc in addition to free software application downloads that you unwittingly install along with the original. An example of some infamous browser hijacker includes Babylon, Anyprotect, Conduit, SweetPage, DefaultTab, RocketTab, and Delta Search, but the names are often changing.
Browser hijacking can bring about severe privacy problems and also identity theft, affect your browsing experience by taking control over outgoing traffic, drastically slows down your PC by consuming lots of resources, and result in system instability also.
Getting rid of browser hijackers
Some browser hijacking could be easily stopped by discovering and eliminating the corresponding malware program through your control panel. But, most browser hijackers are difficult to eliminate manually. No matter how much you try to eliminate it, it can return over and over. Rookie PC users should not try for the manual form of removal, since it needs thorough computer knowledge to perform fixes on the system registry and HOSTS file.
Professionals always recommend users to remove any malware including browser hijacker with an automatic removal tool, which is easier, safer, and quicker than the manual removal technique. Safebytes Anti-Malware has a state-of-the-art anti-malware engine that will help you stop browser hijacking in the first place, and clean up any existing issues.
What To Do If You Cannot Download Safebytes Anti-Malware?
Malware could potentially cause all sorts of damage once they invade your computer, starting from stealing your private details to erasing data files on your computer system. Some malware sits in between your computer and your internet connection and blocks some or all sites that you would like to visit. It might also prevent you from installing anything on your PC, particularly anti-virus programs. If you’re reading this, you probably have infected by malware that prevents you from downloading a computer security program such as Safebytes Antimalware on your PC. There are a few options you could try to get around with this particular obstacle.
Install in Safe Mode
If the malware is set to load automatically when Windows starts, entering Safe Mode could block this attempt. Only minimal required programs and services are loaded whenever you start your personal computer in Safe Mode. To start your Windows XP, Vista, or 7 computers in Safe Mode with Networking, please do as instructed below.
1) At power on/start-up, press the F8 key in 1-second intervals. This would conjure up the Advanced Boot Options menu.
2) Choose Safe Mode with Networking with arrow keys and press Enter.
3) When you are into this mode, you will have online access again. Now, get the virus removal application you want by using the web browser. To install the program, follow the directions within the setup wizard.
4) Right after the software is installed, allow the scan run to eliminate viruses and other threats automatically.
Use an alternate web browser to download security software
Malicious code could exploit vulnerabilities on a particular internet browser and block access to all anti-virus software sites. The most effective way to avoid this issue is to choose a web browser that is renowned for its security features. Firefox contains built-in Malware and Phishing Protection to keep you safe online.
Install security software on a USB drive
To effectively eliminate the malware, you need to approach the problem of installing an anti-virus software program on the infected PC from a different angle. Follow these steps to run the antivirus on the affected computer.
1) Download Safebytes Anti-Malware or Microsoft Windows Defender Offline onto a virus-free computer system.
2) Plug the pen drive into the uninfected computer.
3) Double click on the downloaded file to open the installation wizard.
4) Choose the USB stick as the destination for saving the software file. Follow the instructions on the screen to finish up the installation process.
5) Disconnect the flash drive. You may now use this portable anti-malware on the infected computer.
6) Double-click the anti-malware program EXE file on the USB flash drive.
7) Run Full System Scan to detect and get rid of all sorts of malware.
Benefits and Features of SafeBytes Security Suite
To protect your laptop or computer from many different internet-based threats, it is very important to install an anti-malware program on your PC. However, with so many anti-malware companies in the marketplace, nowadays it’s difficult to decide which one you should obtain for your laptop. A few are very good ones, some are ok types, and some are simply just fake anti-malware applications that could damage your computer themselves! When looking for an anti-malware program, pick one which gives reliable, efficient, and total protection against all known viruses and malware. One of the highly recommended software by industry analysts is SafeBytes Anti-Malware, a popular security application for Microsoft Windows.
Safebytes is one of the well-established computer solutions companies, which provide this complete anti-malware software. Using its cutting-edge technology, this application can assist you to eliminate multiples types of malware such as viruses, PUPs, trojans, worms, ransomware, adware, and browser hijackers.
SafeBytes possesses a variety of wonderful features that can help you protect your laptop or computer from malware attack and damage. Below are some typical features found in this application:
World-class AntiMalware Protection: Built upon a greatly acclaimed anti-virus engine, this malware removal application can find and remove numerous stubborn malware threats like browser hijackers, PUPs, and ransomware that other typical anti-virus applications will miss.
Real-time Threat Response: SafeBytes gives complete and real-time security for your computer. They’re extremely effective in screening and getting rid of numerous threats since they’re regularly improved with the latest updates and alerts.
“Fast Scan” Features: Safebytes Anti-Malware, using its enhanced scanning engine, provides ultra-fast scanning which can quickly target any active online threat.
Website Filtering: Through its unique safety ranking, SafeBytes notifies you whether a site is safe or not to visit it. This will ensure that you’re always certain of your online safety when browsing the internet.
Light-weight: The program is lightweight and can run silently in the background, and will not have an effect on your PC efficiency.
24/7 Premium Support: SafeBytes provides you with 24/7 technical support, automatic maintenance, and software upgrades for the best user experience.
Simply put, SafeBytes has developed a meaningful anti-malware solution that is aimed to protect you against various malware. Malware issues can become a thing of the past when you put this tool to use. So if you’re seeking the very best malware removal application out there, and when you don’t mind shelling out a few bucks for it, go for SafeBytes Anti-Malware.
Technical Details and Manual Removal (Advanced Users)
If you wish to manually remove Motitags without using an automated tool, it may be possible to do so by removing the application from the Windows Add/Remove Programs menu, or in cases of browser extensions, going to the browsers AddOn/Extension manager and removing it. Additionally, it is advised to factory reset your web browser to its default state to fix corrupt settings.
Finally, check your hard drive for all of the following and clean your computer registry manually to get rid of leftover application entries after uninstalls. Please remember that only advanced users should try to manually edit the system files simply because removing any single vital registry entry leads to a serious issue or even a PC crash. Moreover, certain malicious programs have the capability to defend against its removal. Carrying out this in Safe Mode is recommended.
Folders:
C:\Program Files\Motitags_94
C:\Program Files\Motitags_94EI
C:\Users\(username)\AppData\Local\Motitags_94
C:\Users\(username)\AppData\LocalLow\Motitags_94
C:\Users\(username)\AppData\LocalLow\Motitags_94EI
C:\Users\(username)\AppData\Roaming\Mozilla\Firefox\Profiles\g75s8p2u.default\extensionsffxtbr-bs@Motitags_94.com
C:\Users\(username)\AppData\Roaming\Mozilla\Firefox\Profiles\g75s8p2u.default\extensionsffxtbr@Motitags_94.com
C:\Users\(username)\AppData\Roaming\Mozilla\Firefox\Profiles\g75s8p2u.default\Motitags_94
Files:
Search and Delete:
94auxstb.dll
94auxstb64.dll
94bar.dll
94barsvc.exe
94bprtct.dll
94brmon.exe
94brmon64.exe
94brstub.dll
94brstub64.dll
94datact.dll
94dlghk.dll
94dlghk64.dll
94feedmg.dll
94highin.exe
94hkstub.dll
94htmlmu.dll
94httpct.dll
94idle.dll
94ieovr.dll
94medint.exe
94mlbtn.dll
94Plugin.dll
94radio.dll
94regfft.dll
94reghk.dll
94regiet.dll
94script.dll
94skin.dll
94skplay.exe
94SrcAs.dll
94SrchMn.exe
94srchmr.dll
94tpinst.dll
AppIntegrator64.exe
AppIntegratorStub64.dll
BOOTSTRAP.JS
chromeffxtbr.jar
CHROME.MANIFEST
CREXT.DLL
CrExtP94.exe
DPNMNGR.DLL
EXEMANAGER.DLL
FF-NativeMessagingDispatcher.dll
Hpg64.dll
INSTALL.RDF
installKeys.js
LOGO.BMP
NP94Stub.dll
T8EPMSUP.DLL
T8EXTEX.DLL
T8EXTPEX.DLL
T8HTML.DLL
T8RES.DLL
T8TICKER.DLL
UNIFIEDLOGGING.DLL
VERIFY.DLL
94EIPlug.dll
94EZSETP.dll
NP94EISb.dll
Registry:
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Value: Motitags_94 Browser Plugin Loader Data: 94brmon.exe
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Value: Motitags Search Scope Monitor Data: C:\PROGRA~1\MOTITA~2\bar.binsrchmn.exe” /m=2 /w /h
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Value: Motitags Home Page Guard 32 bit Data: C:\PROGRA~1\MOTITA~2\bar.bin\AppIntegrator.exe
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Value: Motitags EPM Support Data: C:\PROGRA~1\MOTITA~2\bar.binmedint.exe” T8EPMSUP.DLL,S
Key HKCU\Software\AppDataLow\Software\Motitags_94
Key HKLM\SOFTWARE\Motitags_94
Key HKLM\SOFTWARE\MozillaPlugins\@Motitags_94.com/Plugin
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Motitags_94bar Uninstall Firefox
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\6df8a038-1b03-41eb-a92b-0e82de08ee4a
Key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\598f4e85-2ee6-43a8-bf43-c75c82b925fe
Key HKLM\SOFTWARE\Classes\Motitags_94.ToolbarProtector.1
Key HKLM\SOFTWARE\Classes\Motitags_94.ToolbarProtector
Key HKLM\SOFTWARE\Classes\Motitags_94.ThirdPartyInstaller.1
Key HKLM\SOFTWARE\Classes\Motitags_94.ThirdPartyInstaller
Key HKLM\SOFTWARE\Classes\Motitags_94.SettingsPlugin.1
Key HKLM\SOFTWARE\Classes\Motitags_94.SettingsPlugin
Key HKLM\SOFTWARE\Classes\Motitags_94.ScriptButton.1
Key HKLM\SOFTWARE\Classes\Motitags_94.ScriptButton
Key HKLM\SOFTWARE\Classes\Motitags_94.RadioSettings.1
Key HKLM\SOFTWARE\Classes\Motitags_94.RadioSettings
Key HKLM\SOFTWARE\Classes\Motitags_94.Radio.1
Key HKLM\SOFTWARE\Classes\Motitags_94.Radio
Key HKLM\SOFTWARE\Classes\Motitags_94.PseudoTransparentPlugin.1
Key HKLM\SOFTWARE\Classes\Motitags_94.PseudoTransparentPlugin
Key HKLM\SOFTWARE\Classes\Motitags_94.MultipleButton.1
Key HKLM\SOFTWARE\Classes\Motitags_94.MultipleButton
Key HKLM\SOFTWARE\Classes\Motitags_94.HTMLPanel.1
Key HKLM\SOFTWARE\Classes\Motitags_94.HTMLPanel
Key HKLM\SOFTWARE\Classes\Motitags_94.HTMLMenu.1
Key HKLM\SOFTWARE\Classes\Motitags_94.HTMLMenu
Key HKLM\SOFTWARE\Classes\Motitags_94.FeedManager.1
Key HKLM\SOFTWARE\Classes\Motitags_94.FeedManager



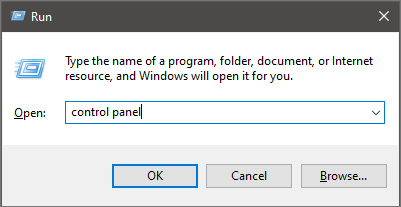 Once you are in the control panel, switch your view to large icons and locate Indexing options.
Once you are in the control panel, switch your view to large icons and locate Indexing options.
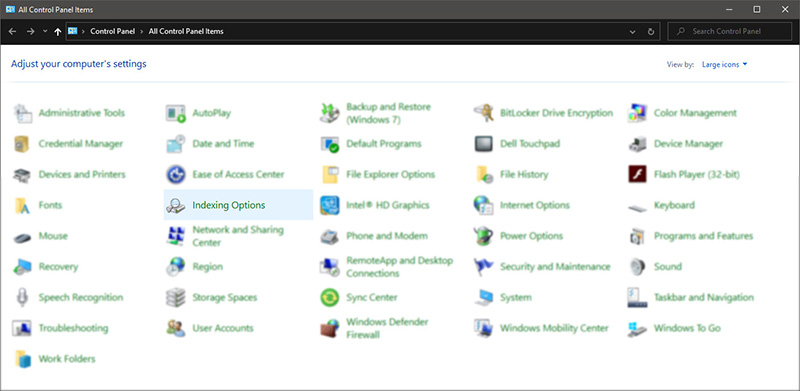 Inside indexing options, click on advanced.
Inside indexing options, click on advanced.
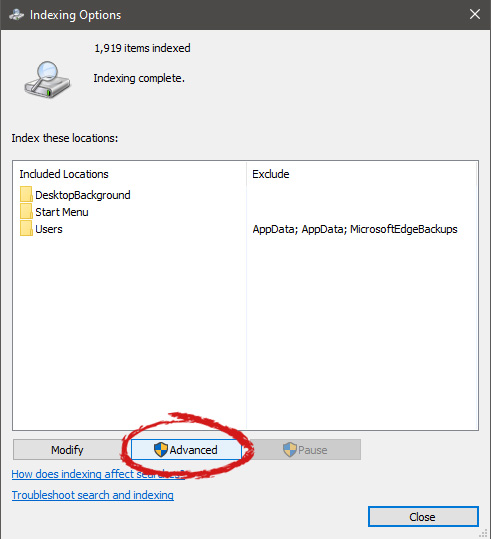 In advanced options click on the rebuild and confirm.
In advanced options click on the rebuild and confirm.
 Leave your computer to finish and your searches should be working fine now.
Leave your computer to finish and your searches should be working fine now. 







 Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend
Skinning of applications is not new to PC users, but did you knew you could skin Steam?
With skin, you can customize the UI and style of the client to what you want making it more personal and to your liking. First thing is to find the skin that you would like to install. There are a lot of sites where you could find custom made Steam skins but we would recommend 