What is 0x0000007E Error Code?
If you’ve been experiencing a 0x0000007E error code pop message on your PC frequently then you need to get it fixed before it causes serious damage to your system. 0x0000007E is a Stop error or Blue Screen of Death error code.
This error message turns your computer screen blue and locks you out of the program running on your computer. It freezes your system and hampers your ability to perform any type of task on your PC.
Solution
 Error Causes
Error Causes
Error 0x0000007E, a blue screen of death error triggers registry issues. It’s not easy to narrow down the cause of 0x0000007E as it results due to many reasons like memory overload, cluttered disk space, viral infection, malware attack, and if the hardware malfunctions.
Ignoring 0x0000007E error pop up is not wise. It is more like a warning of the serious damage that can happen to your PC if it is not fixed timely. It also leads to slowing down the system and increases boot time.
This error message exposes you to dangerous Windows PC threats like registry corruption and damage. Registry corruption can lead to system crash and failure and you may also lose all your important data saved on your PC.
Further Information and Manual Repair
Install Restoro
You don’t always have to spend hundreds of dollars to hire a technician to fix error pop-ups on your PC try using Restoro
Restoro is an advanced and multi-functional PC repair tool with a comprehensive suite of powerful features designed to resolve almost all types of PC errors in seconds including 0x0000007E error code.
It is a next-generation PC repair tool that serves as a system optimizer, anti-virus, and quality registry cleaner. Its built-in intuitive technology enables Restoro to scan, identify and repair the ultimate cause of the error code 0x0000007E in just a few seconds.
Eventually, it spares you from the hassle of finding the root cause of the 0x0000007E error message and then selecting a tool specifically designed to resolve only that particular cause with limited features. This highly functional PC error tool is the answer for all your registry issues.
By running Restoro on your PC, you can fix the 0x0000007E BSOD error code and avoid registry corruption.
Why Restoro?
The smart registry cleaner utility embedded in this tool enables it to scan for registry errors and clear up disk space accumulated by junk files, internet temporary files, invalid entries, and other types of unnecessary files taking up a good chunk of your disk space.
This clutter also slows down your PC performance as it requires more power than it has to run the system because of the excess load on the RAM.
However, by wiping out the clutter with this helper, you can optimize the speed of your PC and see a significant difference in its performance.
Restoro backup feature enables you to create backup files for safety purposes. Furthermore, it has several other built-in value-adding features like privacy error utility and system stability utility for enhanced functionality.
To resolve the error code 0x0000007E in seconds, all you need to do is download and install Restoro on your system and run it to scan for errors. In a few seconds, you will see a scanning report with comprehensive details of the types of PC damages.
To fix the issue right away, create backups and click ‘fix’ to resolve. In just a few clicks you can repair your PC.
Download Restoro Today!


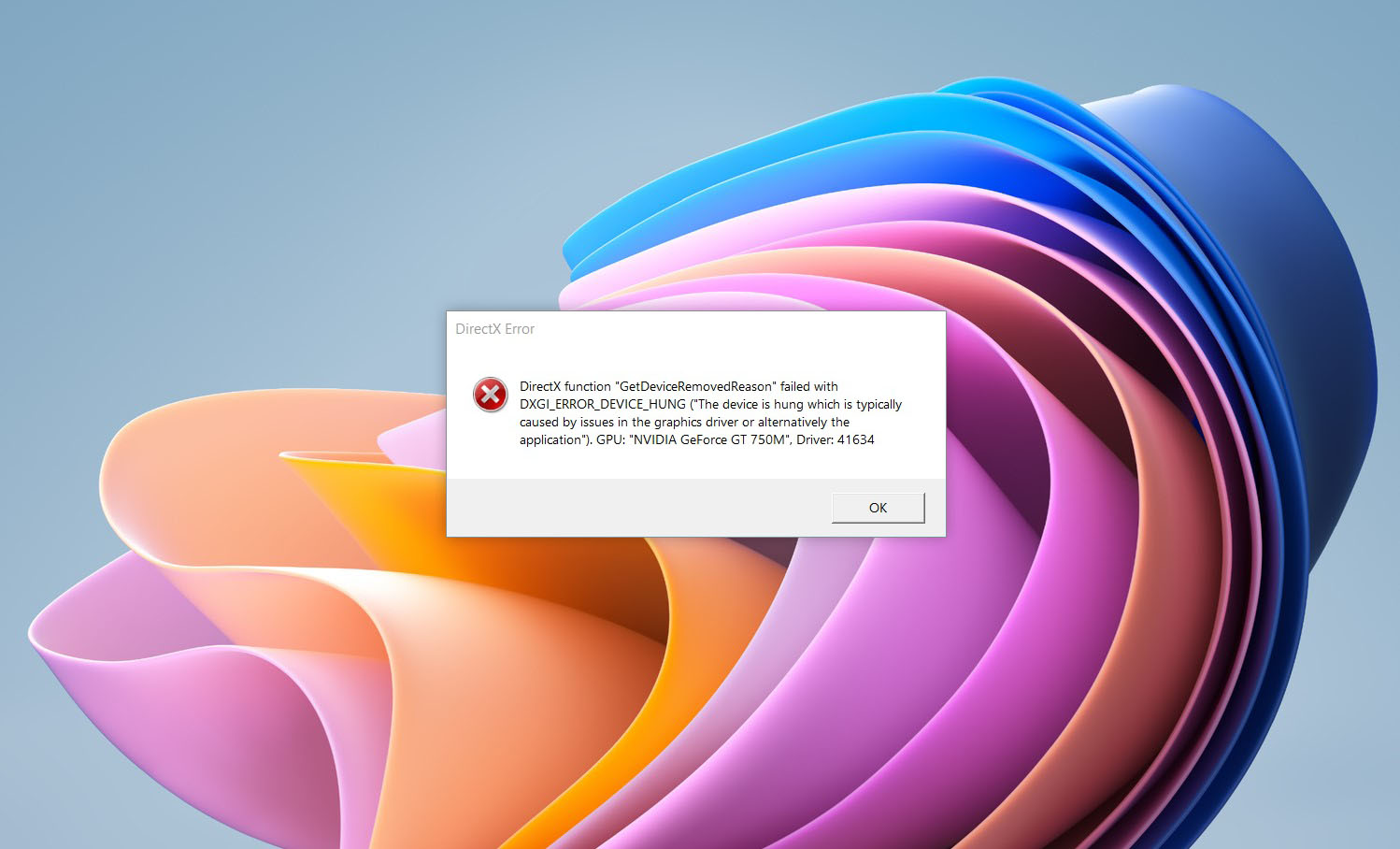 If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
If you are one of the gamers affected by this error, fear not because we have a solution for you. Follow provided fix guide in order to correct this error and get back to gaming asap.
 The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.
The console itself is coming in cylindrical shape powered by Intel CPU and ASUS GPU of the unknown chipset. It has Seagate Baraccuda 1TB SSD and it is VR-ready. The console will have raytracing and will be 4K ready.
 Update Windows 11
Update Windows 11